使用keytool 管理证书
在JAVA平台中,keytool是提供给技术人员进行证书管理的工具。关于它的使用,笔者将从实际应用的角度讲三点:1.如何构建独立的CA认证体系; 2.生成证书并提交CA认证,最终合成tomcat可用的SSL证书;3.证书格式的转换;
1.如何构建独立的CA认证体系
要构建独立CA认证体系,我们需要先生成一个作为ROOTCA的根证书,并内置到客户端的浏览器中。
以命名该ROOTCA为 YUAN_ROOTCA,并建立中间证书颁发机构 YUANLANGCHAO为例:
step1
[root@oracle model]# keytool -genkeypair -keyalg RSA -alias YUAN_ROOTCA -keystore YUANCA.jks -storepass yuan123456 -startdate 2015/09/20 -validity 3650
What is your first and last name?
[Unknown]: YUAN_ROOTCA
What is the name of your organizational unit?
[Unknown]: YUAN
What is the name of your organization?
[Unknown]: YUAN_HOME
What is the name of your City or Locality?
[Unknown]: SHANGHAI
What is the name of your State or Province?
[Unknown]: SHANGHAI
What is the two-letter country code for this unit?
[Unknown]: CN
Is CN=YUAN_ROOTCA, OU=YUAN, O=YUAN_HOME, L=SHANGHAI, ST=SHANGHAI, C=CN correct?
[no]: Y
Enter key password for <YUAN_ROOTCA>
(RETURN if same as keystore password):
[root@oracle model]# keytool -list -rfc -alias YUAN_ROOTCA -keystore YUANCA.jks -storepass yuan123456
Alias name: YUAN_ROOTCA
Creation date: Sep 22, 2015
Entry type: PrivateKeyEntry
Certificate chain length: 1
Certificate[1]:
-----BEGIN CERTIFICATE-----
MIIDdzCCAl+gAwIBAgIEHjF9GjANBgkqhkiG9w0BAQsFADBsMQswCQYDVQQGEwJDTjERMA8GA1UE
CBMIU0hBTkdIQUkxETAPBgNVBAcTCFNIQU5HSEFJMRIwEAYDVQQKDAlZVUFOX0hPTUUxDTALBgNV
BAsTBFlVQU4xFDASBgNVBAMMC1lVQU5fUk9PVENBMB4XDTE1MDkyMDE5MjIxMVoXDTI1MDkxNzE5
MjIxMVowbDELMAkGA1UEBhMCQ04xETAPBgNVBAgTCFNIQU5HSEFJMREwDwYDVQQHEwhTSEFOR0hB
STESMBAGA1UECgwJWVVBTl9IT01FMQ0wCwYDVQQLEwRZVUFOMRQwEgYDVQQDDAtZVUFOX1JPT1RD
QTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAISGfoPZ+GGVq67hdKXL+2WuVvKi6acv
6haEzAvX4atBRCPQPM156Wc288LEAvniW+Re29xxdKjH2GLRvkQ0XMwtO7eNExOLbICD3ZorPSmO
JiWfRj3V/mqKO53xAKPgr55ySxs9kDFBB1uYCEgWJd4qHBuzoi5rrBo0nCEVz4tbeT9lgkKxHsy/
fR6pt2Pl5EkbuVCiJBlr0j38Uw9cu19+B2TKMibBNhh90ZmgW4WTAzNzqs+lENiZOGzEUl0OL5SH
7UxKKpDDpqrRgC+6tjMMAXAkvN7LkP+7r7iX+B7myYjGYyeYCj/yY7F/Mm7o5McqyklmilvOwNNj
bkhpsxUCAwEAAaMhMB8wHQYDVR0OBBYEFKCyP52ihWWzOuLZvDLZ0K2duWv/MA0GCSqGSIb3DQEB
CwUAA4IBAQA65f6cqcv/S4Bg6WxY8lfUo9mNk+2NKeoC0h5qvgKf+45aJ0ygIbimkpvxgdabPyOl
BK4nsrp+PA0j952G5DEzCmwyzhlxvGgcAMvTW7RlQbxiogiSW+LMh2LEAYVhitYEPyHe/fYA+31H
bI7GMLzPa8vzAldcxCw44RL3K7MUUQ2drWcgwbKhkldovyBVzzGx+iVN4L4bDf/L1JumOLXN+Nsc
H6kmeeeqavr6KLfyCZ46aca50UgRM1/HmQEso5BLKTmE39u4nGj109iehiJZ8so39rgQObkAO1W4
0Wbn7d7WfTKqxziK8TM2nDcPz76/p/guqspJXaqfl0OBTG4j
-----END CERTIFICATE-----
[root@oracle model]# keytool -exportcert -alias YUAN_ROOTCA -keystore YUANCA.jks -storepass yuan123456 -file YUAN_ROOTCA.cer
Certificate stored in file <YUAN_ROOTCA.cer>step2
我们需要将生成的YUAN_CAROOT.cer导入到客户端 受信任的根证书颁发机构 中,以在WindowsServer 2012R2上安装证书为例:
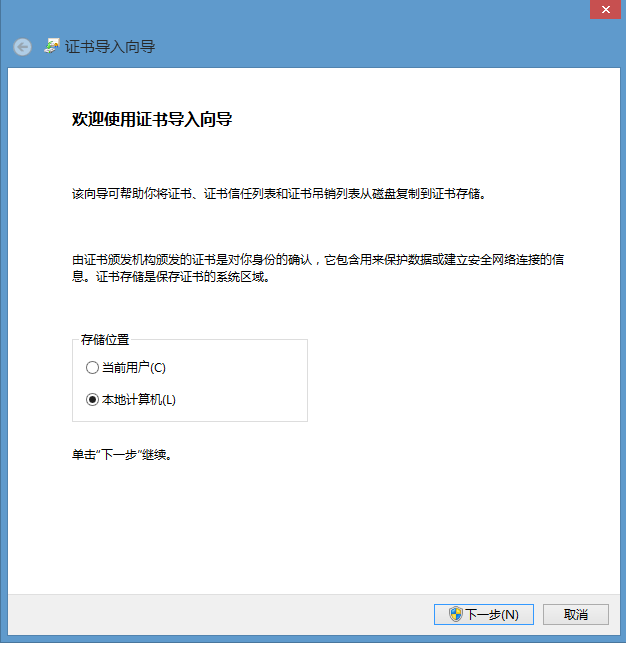
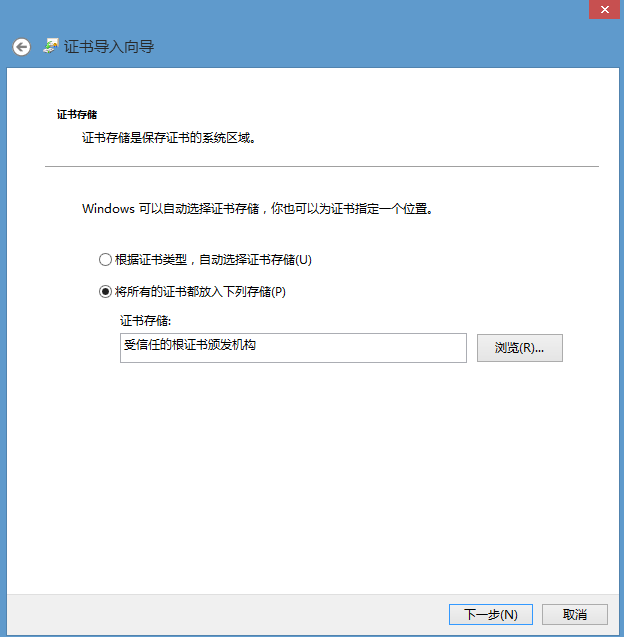
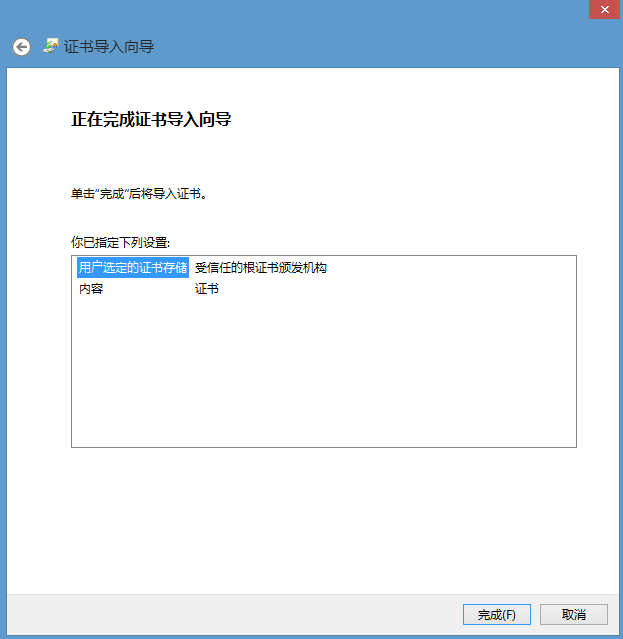
step3
生成YUANLANGCHAO的证书,并发出颁发请求,由YUAN_ROOTCA进行签名认证并指定证书中的基本约束赋予有限于3级的CA权限:
[root@oracle model]# keytool -genkeypair -keyalg RSA -alias YUANLANGCHAO -keystore YUANLANGCHAO.jks -storepass yuanlc123456 -startdate 2015/09/20 -validity 3650
What is your first and last name?
[Unknown]: YUANLANGCHAO
What is the name of your organizational unit?
[Unknown]: YUANLANGCHAO
What is the name of your organization?
[Unknown]: YUAN
What is the name of your City or Locality?
[Unknown]: SHANGHAI
What is the name of your State or Province?
[Unknown]: SHANGHAI
What is the two-letter country code for this unit?
[Unknown]: CN
Is CN=YUANLANGCHAO, OU=YUANLANGCHAO, O=YUAN, L=SHANGHAI, ST=SHANGHAI, C=CN correct?
[no]: Y
Enter key password for <YUANLANGCHAO>
(RETURN if same as keystore password):
[root@oracle model]# keytool -certreq -alias YUANLANGCHAO -keystore YUANLANGCHAO.jks -storepass yuanlc123456 > YUANLANGCHAO.csr
[root@oracle model]# cat YUANLANGCHAO.csr
-----BEGIN NEW CERTIFICATE REQUEST-----
MIIC5TCCAc0CAQAwcDELMAkGA1UEBhMCQ04xETAPBgNVBAgTCFNIQU5HSEFJMREwDwYDVQQHEwhT
SEFOR0hBSTENMAsGA1UEChMEWVVBTjEVMBMGA1UECxMMWVVBTkxBTkdDSEFPMRUwEwYDVQQDEwxZ
VUFOTEFOR0NIQU8wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCieng4vabG7lqylVzL
gGUVaTReuVWNlur/s7jl2HRUchOtp2ItTqEM++ZxqMnh6KvzTglmYk6pxLDRBbDeH5Da6N+tw7aw
Gm48VcCHjMJcGJIS007I2KvdumyOK8tNvCJ6BaM6SxkYHCfdTavZTy9FFl/2lS4IBvIXqMNQWc9J
9mZ69VMU6WOqQKwwtkLDNMeinDRlclWNVGYha357evKG/wah+jYWFZyWrpUzzRBsuRdWFXaZOY7M
vChnRCHrHm4U1ZI4O3eKNLH2XXxI5QhSnqdo7PH3bvPO0uDPaiqEXSZ2xxMAQdvkb5qxNz3Ew+ob
HHlZXjoT3suxEAcZQ1rDAgMBAAGgMDAuBgkqhkiG9w0BCQ4xITAfMB0GA1UdDgQWBBTl7AqKfViO
Ek25QFPfKHeMmUveUDANBgkqhkiG9w0BAQsFAAOCAQEAesBRXkf/hlY9BwYOGgvK57d1w9IuKhev
B5VI0d26JkjdxtkYxjvR3ZRnkL4VLqWTTO8x3a3tDgFu92fkyzsUWgoKzaXyfzGo/jU02z+j1ajj
GA4R5NGTOt5YoPN3Q1L7Du7FkFcfc01Rvi/AdlbMds5hvE8/pAhXNa8+GTk0JjHC8KTkfTm5jPRI
en+dlWLg7kDvWNWImYmKoIDf+wjQMMj1MD7o7fPFZCXNvJ7KDdnZ5lPlpDt1iU42snEEKwXI8rhd
SRS5HYk9m/um6foCOeZOgrCVF1VknU0ADHoygQjusTP4qOn0N2IBd6QROuo0vYGYi7TuY5pLhqM/
rPGHjQ==
-----END NEW CERTIFICATE REQUEST-----
[root@oracle model]# keytool -gencert -alias YUAN_ROOTCA -keystore YUANCA.jks -storepass yuan123456 -infile YUANLANGCHAO.csr -outfile YUANLANGCHAO.cer -startdate 2015/09/20 -validity 3650 -ext BC=ca:true,pathlen:3
[root@oracle model]# keytool -importcert -file YUAN_ROOTCA.cer -alias chain_root -keystore YUANLANGCHAO.jks -storepass yuanlc123456
Owner: CN=YUAN_ROOTCA, OU=YUAN, O=YUAN_HOME, L=SHANGHAI, ST=SHANGHAI, C=CN
Issuer: CN=YUAN_ROOTCA, OU=YUAN, O=YUAN_HOME, L=SHANGHAI, ST=SHANGHAI, C=CN
Serial number: 1e317d1a
Valid from: Sun Sep 20 15:22:11 EDT 2015 until: Wed Sep 17 15:22:11 EDT 2025
Certificate fingerprints:
MD5: 67:09:36:53:72:D8:53:E8:62:8B:59:C9:B4:8F:15:87
SHA1: 10:FD:15:41:0C:14:9A:95:AB:7E:63:D4:A9:25:36:5A:AD:41:17:0E
SHA256: 42:B8:1E:A6:A9:A6:DA:22:B5:8B:25:5A:97:44:E2:D6:C1:40:48:06:62:8C:FB:8D:89:88:B7:88:8A:34:83:A6
Signature algorithm name: SHA256withRSA
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: A0 B2 3F 9D A2 85 65 B3 3A E2 D9 BC 32 D9 D0 AD ..?...e.:...2...
0010: 9D B9 6B FF ..k.
]
]
Trust this certificate? [no]: y
Certificate was added to keystore
[root@oracle model]# keytool -importcert -file YUANLANGCHAO.cer -alias YUANLANGCHAO -keystore YUANLANGCHAO.jks -storepass yuanlc123456
Certificate reply was installed in keystore
其中 keytool -importcert -file YUAN_ROOTCA.cer -alias chain_root -keystore YUANLANGCHAO.jks -storepass yuanlc123456 这一步是不能省的,如果漏掉的话 在执行 keytool -importcert -file YUANLANGCHAO.cer -alias YUANLANGCHAO -keystore YUANLANGCHAO.jks -storepass yuanlc123456 时会报”无法从回复中建立证书链“的错误。
step4
YUANLANGCHAO 作为中间级CA其证书也是需要内置到浏览器中的,步骤与step2中类似,只不过
需要选择
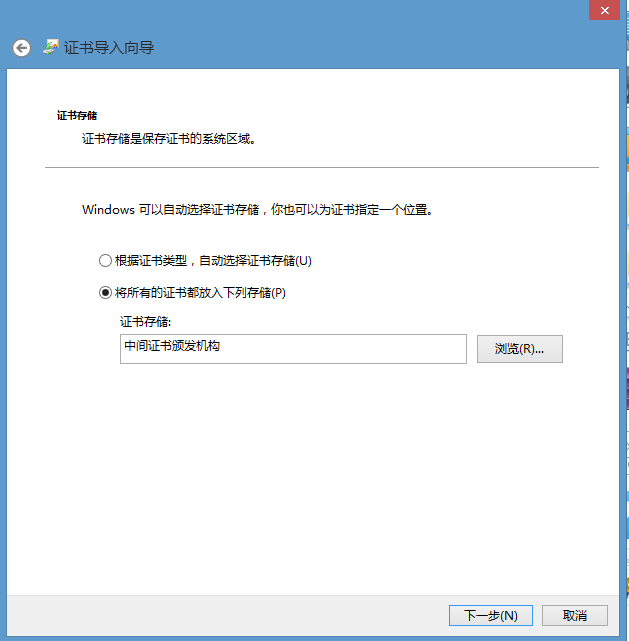
最后效果是
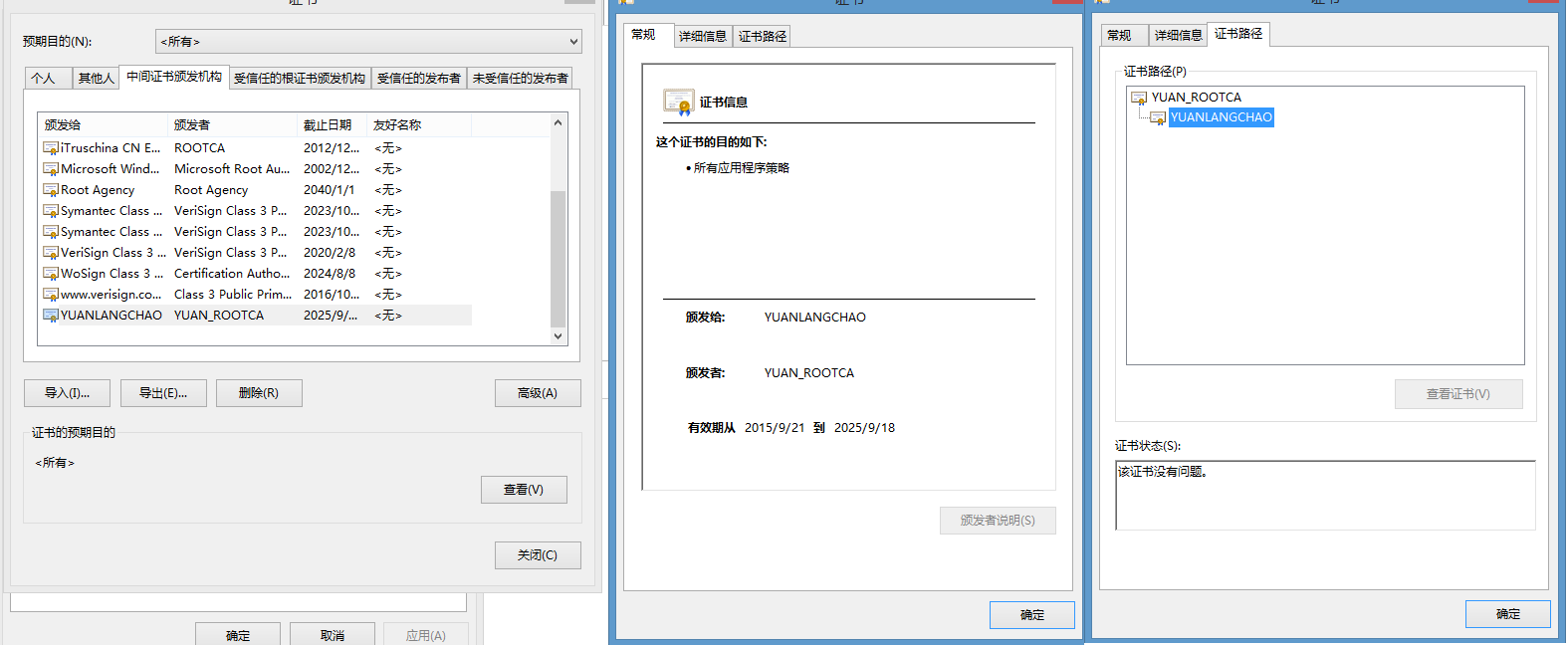
这个时候我们已经形成了CA的从属关系,YUAN_ROOTCA颁发给YUANGLANGCHAO,则YUANGLANGCHAO上级路径便是YUAN_ROOT这个因为我们在导入证书回复的时候已经导入了YUAN_ROOTCA的证书,所以keytool会自动帮我们建好证书链。
需要注意的是作为CA的证书一般是不用到具体服务器站点的。
下面我们将使用 中间CA YUANLANGCHAO为具体的站点颁发证书。
2.生成证书并提交CA认证,最终合成tomcat可用的SSL证书
以为个人网站www.yuanlangchao.com申请证书为例
step 1
[root@oracle model]# keytool -genkeypair -keyalg RSA -alias server -keystore www.yuanlangchao.jks -storepass yuanlangchao -startdate 2015/09/20 -validity 3650
What is your first and last name?
[Unknown]: www.yuanlangchao.com
What is the name of your organizational unit?
[Unknown]: YUANLANGCHAO
What is the name of your organization?
[Unknown]: YUAN
What is the name of your City or Locality?
[Unknown]: shanghai
What is the name of your State or Province?
[Unknown]: shanghai
What is the two-letter country code for this unit?
[Unknown]: cn
Is CN=www.yuanlangchao.com, OU=YUANLANGCHAO, O=YUAN, L=shanghai, ST=shanghai, C=cn correct?
[no]: y
Enter key password for <server>
(RETURN if same as keystore password):
[root@oracle model]# keytool -certreq -alias server -keystore www.yuanlangchao.jks -storepass yuanlangchao > www.yuanlangchao.com.csr
[root@oracle model]# cat www.yuanlangchao.com.csr
-----BEGIN NEW CERTIFICATE REQUEST-----
MIIC7TCCAdUCAQAweDELMAkGA1UEBhMCY24xETAPBgNVBAgTCHNoYW5naGFpMREwDwYDVQQHEwhz
aGFuZ2hhaTENMAsGA1UEChMEWVVBTjEVMBMGA1UECxMMWVVBTkxBTkdDSEFPMR0wGwYDVQQDExR3
d3cueXVhbmxhbmdjaGFvLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAI/zAR3B
JAajSxvC4bqAwGrBq9EwFLUDQukugXjGX/YlzFilTUp0NibEycJ5udTARNEi12FDV9BhdxXYmCO+
KgPTYjM9l94DFCob15FV9wKxLyn4vQezpyNGqLsN6aSihFGZwmCIihkvLPUg7aCC3xKmS8LLXhGe
rlKIIbMM5CSZPCysQPiuq6s7MGBVzmwxzUO6CJS5EbQ9Rf3vDUwxJ1/N+ZSlmkoNbjQSIBLMMKBp
rC+CVVwqQL5QFlScciD+Me4t047mmEixRVJudpiQcyIh4itwbzAcBQwaZbnsnh2Jc+EDPel8+keS
3HykBsYKeRi5yS2uFavJi+cMp1H3PNUCAwEAAaAwMC4GCSqGSIb3DQEJDjEhMB8wHQYDVR0OBBYE
FO33W9/Kt68tVGd2cdSbnWM1PoC3MA0GCSqGSIb3DQEBCwUAA4IBAQA8z/GS5n87Xw/+ngF8idML
ZgtxfxqZ4DRZxwYqittxfEP4F2c3DZedMEPnWnPtz8Ge81oivmNH34gT2I8FupRYn3tmPAFcel5i
7Q+Ub2Kg5bRTFuHviWYFDH2TA6sP5k404dKVbZ31ESMvWm+qEAzwTJ6bLceW1ikuHHMSc8jkfj9u
syp4lJz2beI6ur/ejBY9JmoB1JYkXFFKIk6H+YvKNydvfhPYIhq+EF3iF/0f8lIOA4BqAVNAa/T9
EjZTd6H/14duaqSkgYDPlMOKc86ntSjqyczm3VAioe8Rrzn8J6TAdrXMrMPOCu85Hb1A0ZoMqwwi
aC4B8OdM5aoimsTW
-----END NEW CERTIFICATE REQUEST-----
[root@oracle model]# keytool -gencert -alias YUANLANGCHAO -keystore YUANLANGCHAO.jks -storepass yuanlc123456 -infile www.yuanlangchao.com.csr -outfile www.yuanlangchao.cer -startdate 2015/09/20 -validity 3650
[root@oracle model]# keytool -importcert -file YUAN_ROOTCA.cer -alias chainroot -keystore www.yuanlangchao.jks -storepass yuanlangchao
Owner: CN=YUAN_ROOTCA, OU=YUAN, O=YUAN_HOME, L=SHANGHAI, ST=SHANGHAI, C=CN
Issuer: CN=YUAN_ROOTCA, OU=YUAN, O=YUAN_HOME, L=SHANGHAI, ST=SHANGHAI, C=CN
Serial number: 1e317d1a
Valid from: Sun Sep 20 15:22:11 EDT 2015 until: Wed Sep 17 15:22:11 EDT 2025
Certificate fingerprints:
MD5: 67:09:36:53:72:D8:53:E8:62:8B:59:C9:B4:8F:15:87
SHA1: 10:FD:15:41:0C:14:9A:95:AB:7E:63:D4:A9:25:36:5A:AD:41:17:0E
SHA256: 42:B8:1E:A6:A9:A6:DA:22:B5:8B:25:5A:97:44:E2:D6:C1:40:48:06:62:8C:FB:8D:89:88:B7:88:8A:34:83:A6
Signature algorithm name: SHA256withRSA
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: A0 B2 3F 9D A2 85 65 B3 3A E2 D9 BC 32 D9 D0 AD ..?...e.:...2...
0010: 9D B9 6B FF ..k.
]
]
Trust this certificate? [no]: y
Certificate was added to keystore
[root@oracle model]# keytool -importcert -file YUANLANGCHAO.cer -alias chainmdile -keystore www.yuanlangchao.jks -storepass yuanlangchao
Certificate was added to keystore
[root@oracle model]# keytool -importcert -file www.yuanlangchao.cer -alias server -keystore www.yuanlangchao.jks -storepass yuanlangchao
Certificate reply was installed in keystore
此时 www.yuanlangchao.jks文件便可以为服务器端的tomcat使用了。
3.证书格式的转换
JAVA平台的keytool工具已经满足了在JAVA平台中使用证书的所有需要。但生成的JKS证书并不可以在windows等其他平台直接使用。这个时候我们需要对JKS格式的证书惊醒格式转换。keytool支持从JKS转换到PKCS12,然后可以利用openssl对PKCS12证书进行提取公钥、私钥以及制作证书链等操作来满足不同平台对同一认证证书的使用。
下面介绍使用keytool进行格转换的方法:
以将www.yuanlangchao.jks转换为www.yuanlangchao.p12为例:
[root@oracle model]# keytool -importkeystore -srckeystore www.yuanlangchao.jks -destkeystore www.yuanlangchao.p12 -srcstoretype JKS -deststoretype PKCS12 -srcstorepass yuanlangchao -deststorepass yuanlangchao -srcalias server -destalias server我们便可得到 www.yuanlangchao.p12文件
当然从 PKCS12转换为JKS格式 只需要将上面的命令反过来即可。
keytool工具支持PKCS12与JKS之间相互转换,还是很方便并且经常被用到的。比如说如果你需要对只有包含公钥的证书 及私钥来生成一个 java平台可用的jks文件的话,则需要先通过openssl先生成 pkcs12格式的文件,然后再使用keytool转换为jks格式的文件。这在不同平台证书的转换中可以很好的衔接。这在介绍openssl工具使用时会讲到。目前版本的tomcat支持不指定证书库的存储类型直接使用pkcs12格式的证书。






















 348
348

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








