本文记录 Kali Linux 2018.1 学习使用和渗透测试的详细过程,教程为安全牛课堂里的《Kali Linux 渗透测试》课程
- Nikto 简单使用
- Nikto-interactive(交互方式)
- 设置使用 cookie 自动登录扫描
- 使用 LibWhisker 中对 IDS 的躲避技术
1. Nikto 简单使用
-
安装并更新
安装并更新官网:https://cirt.net/Nikto-Installing_and_Updating
git clone https://github.com/sullo/nikto.git Nikto2 # 之后,nikto.pl 将会在Nikto2/program/目录(也可以在文档目录中找到)。 # 保持Nikto更新只需转到您的仓库中的目录并键入: git pull -
列出插件
root@kali:~# nikto -list-plugins Plugin: cgi CGI - Enumerates possible CGI directories. Written by Sullo, Copyright (C) 2008 CIRT Inc. Plugin: cookies HTTP Cookie Internal IP - Looks for internal IP addresses in cookies returned from an HTTP request. Written by Sullo, Copyright (C) 2010 CIRT Inc. Plugin: report_csv CSV reports - Produces a CSV report. Written by Tautology, Copyright (C) 2008 CIRT Inc. -
基本扫描
# 指定主机 root@kali:~# nikto -host 172.16.10.133 root@kali:~ nikto -host http://172.16.10.133/dvwa - Nikto v2.1.6 --------------------------------------------------------------- + Target IP: 172.16.10.133 + Target Hostname: 172.16.10.133 + Target Port: 80 + Start Time: 2018-03-04 07:15:51 (GMT-5) -------------------------------------------------------------- + Server: Apache/2.2.8 (Ubuntu) DAV/2 + Cookie PHPSESSID created without the httponly flag + Cookie security created without the httponly flag + Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10 # 指定主机和端口 root@kali:~# nikto -host www.baidu.com -port 443 -ssl - Nikto v2.1.6 --------------------------------------------------------------- + Target IP: 103.235.46.39 + Target Hostname: www.baidu.com + Target Port: 443 --------------------------------------------------------------- + SSL Info: Subject: /C=CN/ST=beijing/L=beijing/O=BeiJing Baidu Netcom Science Technology Co., Ltd/OU=service operation department./CN=baidu.com Ciphers: ECDHE-RSA-AES128-GCM-SHA256 Issuer: /C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec Class 3 Secure Server CA - G4 + Start Time: 2018-03-04 07:19:06 (GMT-5) -------------------------------------------------------------- + Server: BWS/1.1 + Cookie BAIDUID created without the secure flag + Cookie BAIDUID created without the httponly flag # 指定端口 root@kali:~# nikto -host 172.16.10.133:80 - Nikto v2.1.6 -------------------------------------------------------- + Target IP: 172.16.10.133 + Target Hostname: 172.16.10.133 + Target Port: 80 + Start Time: 2018-03-04 07:24:53 (GMT-5) ------------------------------------------------------- + Server: Apache/2.2.8 (Ubuntu) DAV/2 + Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Uncommon header 'tcn' found, with contents: list + Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php + Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. + Web Server returns a valid response with junk HTTP methods, this may cause false positives. # 将结果保存到文件 root@kali:~# nikto -host 172.16.10.133 -port 80 -output host133.txt - Nikto v2.1.6/2.1.5 + Target Host: 172.16.10.133 + Target Port: 80 + GET Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10 + GET The anti-clickjacking X-Frame-Options header is not present. + GET The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + GET The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a di fferent fashion to the MIME type + GET Uncommon header 'tcn' found, with contents: list + GET Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http:// www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php + HXNGYMEH Web Server returns a valid response with junk HTTP methods, this may cause false positives. + OSVDB-877: TRACE HTTP TRACE method is active, suggesting the host is vulnerable to XST + GET /phpinfo.php?VARIABLE=<script>alert('Vulnerable')</script>: Output from the phpinfo() function was found. + OSVDB-3268: GET /doc/: Directory indexing found. # 批量扫描 root@kali:~# vim hostscan.txt root@kali:~# cat hostscan.txt 172.16.10.138:80 172.16.10.133 http://172.16.10.133/dvwa:80 root@kali:~# nikto -host hostscan.txt - Nikto v2.1.6 --------------------------------------------------------------- + Target IP: 172.16.10.138 + Target Hostname: 172.16.10.138 + Target Port: 80 + Start Time: 2018-03-04 07:50:31 (GMT-5) ----------------------------------------------------------------- + Server: Apache/2.2.22 (Ubuntu) ---------------------------------------------------------------- + Target IP: 172.16.10.133 + Target Hostname: 172.16.10.133 + Target Port: 80 + Start Time: 2018-03-04 07:51:37 (GMT-5) ----------------------------------------------------------------- + Server: Apache/2.2.8 (Ubuntu) DAV/2 + 3 host(s) tested # 将 nmap 发现的主机进行扫描 root@kali:~# nmap -p80 172.16.10.0/24 -oG - | nikto -host - ------------------------------------------------- + nmap Input Queued: 172.16.10.133:80 + nmap Input Queued: 172.16.10.138:80 + Target IP: 172.16.10.138 + Target Hostname: 172.16.10.138 + Target Port: 80 + Start Time: 2018-03-04 07:54:40 (GMT-5) -------------------------------------------------- ------------------------------------------------- + Target IP: 172.16.10.133 + Target Hostname: 172.16.10.133 + Target Port: 80 + Start Time: 2018-03-04 07:55:13 (GMT-5) --------------------------------------------------- -------------------------------------------------- + 2 host(s) tested # 使用本地设置的 VPN 代理 root@kali:~# nikto -host 172.16.10.133 -useproxy http://localhost:8087 - Nikto v2.1.6 ------------------------------------------------------- + Target IP: 61.135.169.125 + Target Hostname: www.baidu.com + Target Port: 443 ----------------------------------------------------
2. Nikto-interactive(交互方式)
-
在扫描的过程中敲下按键,即可打开开关
• Space – report current scan status • v – verbose mode on/off • d – debug mode on/off • e – error reporting on/off • p – progress reporting on/off • r – redirect display on/off • c – cookie display on/off • a – auth display on/off • q – quit • N – next host • P - Pause -
演示
root@kali:~# nikto -host https://www.baidu.com - Nikto v2.1.6 --------------------------------------------------- + Target IP: 61.135.169.121 + Target Hostname: www.baidu.com + Target Port: 443 --------------------------------------------------- v- STATUS: Completed 70 requests (~1% complete, 18.0 minutes left): currently in plugin 'Guess authentication' - STATUS: Running average: 10 requests: 0.1569 sec. V:Sun Mar 4 08:17:26 2018 - 302 for GET: /VVdEgbpJ.axd V:Sun Mar 4 08:17:26 2018 - Testing error for file: /VVdEgbpJ.pl V:Sun Mar 4 08:17:26 2018 - 302 for GET: /VVdEgbpJ.pl e+ Entry '/homepage/' in robots.txt returned a non-forbidden or redirect HTTP code (302) + Entry '/s?/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/shifen/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/homepage/' in robots.txt returned a non-forbidden or redirect HTTP code (302) + Entry '/s?/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/shifen/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
3. 设置使用 cookie 自动登录扫描
配置文件位置: /etc/nikto.conf
-
配置文件默认使用 Nikto 的 User Agent,更改为 IE8 或其他
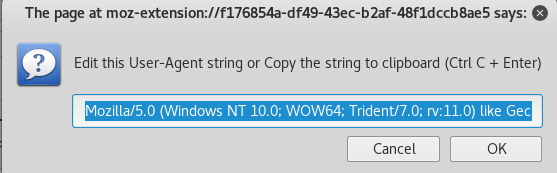
root@kali:~# vim /etc/nikto.conf #USERAGENT=Mozilla/5.00 (Nikto/@VERSION) (Evasions:@EVASIONS) (Test:@TESTID) USERAGENT=Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.0; Trident/4.0) # 17行 # 更换为 IE8:单击 User-Agent-Swicher,选择并复制其中的UA值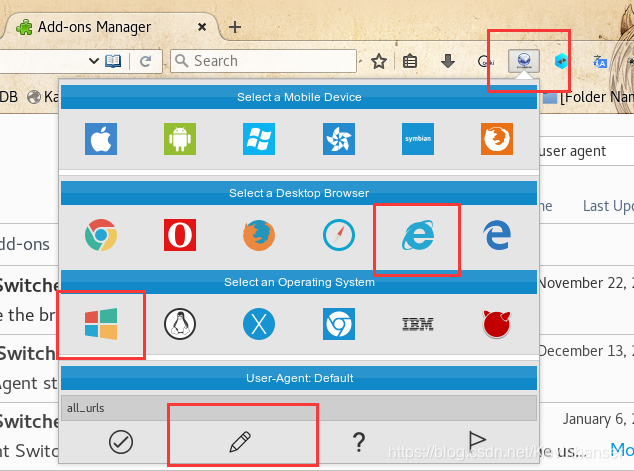
-
配置默认 cookie
# "cookie1"="cookie value";"cookie2"="cookie val" STATIC-COOKIE="PHPSESSID"="31ce7cd539ed93f182d7881460fe0def";"security"="high" # 57行 -
使用修改过配置文件的 nikto 进行扫描,扫描过程中按 d 进行 debug 模式,进行验证配置信息
root@kali:~# nikto -host http://172.16.10.133/dvwa -port 80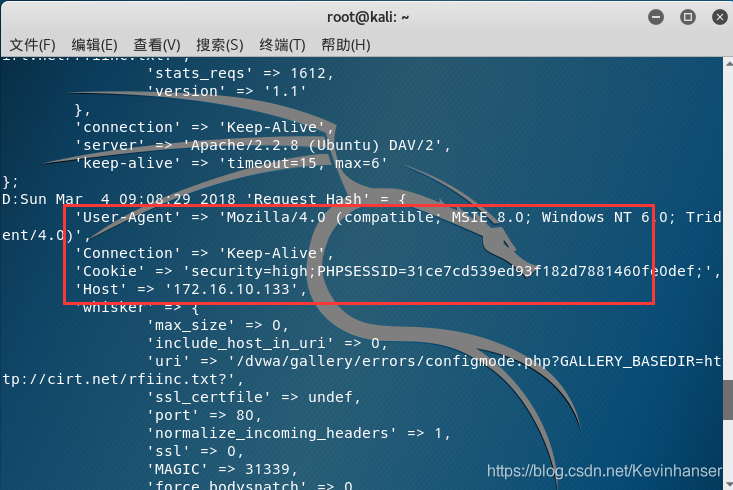
###4. 使用 LibWhisker 中对 IDS 的躲避技术
# -evasion
Specify the LibWhisker IDS evasion technique to use (see the LibWhisker docs for detailed information on
these). Use the reference number to specify the type, multiple may be used:
1 - Random URI encoding (non-UTF8)
2 - Directory self-reference (/./)
3 - Premature URL ending
4 - Prepend long random string
5 - Fake parameter
6 - TAB as request spacer
7 - Change the case of the URL
8 - Use Windows directory separator (\)
# -evasion 使用 LibWhisker 中对 IDS 的躲避技术,可使用以下几种类型
• 1 随机 URL 编码(非 UTF-8 方式)
• 2 自然选择路径 (/./)
• 3 过早的结束URL
• 4 优先考虑长随机字符串
• 5 参数欺骗
• 6 使用 TAB 作为命令的分隔符
• 7 使用变化的 URL
• 8 使用 windows 路径风额度 "\"
root@kali:~# nikto -host http://172.16.10.133/dvwa -evasion 167
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 172.16.10.133
+ Target Hostname: 172.16.10.133
+ Target Port: 80
+ Using Encoding: Random URI encoding (non-UTF8)
+ Using Encoding: TAB as request spacer
+ Using Encoding: Change the case of the URL
+ Start Time: 2018-03-04 09:17:54 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ 7534 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2018-03-04 09:18:17 (GMT-5) (23 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested





















 2419
2419











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








