最近电脑一直蓝屏,一直在找问题,但是没有按照正确的思路来分析处理。
大致步骤这里写一下:
1.出现蓝屏,重启看Windows日志
2.找到事件描述
3.安装Debugging Tools分析.dmp文件,找到蓝屏错误
4.百度蓝屏解决方法,询问专业人士
这是我的蓝屏错误代码
KERNEL_SEURITY_CHECK_FAILURE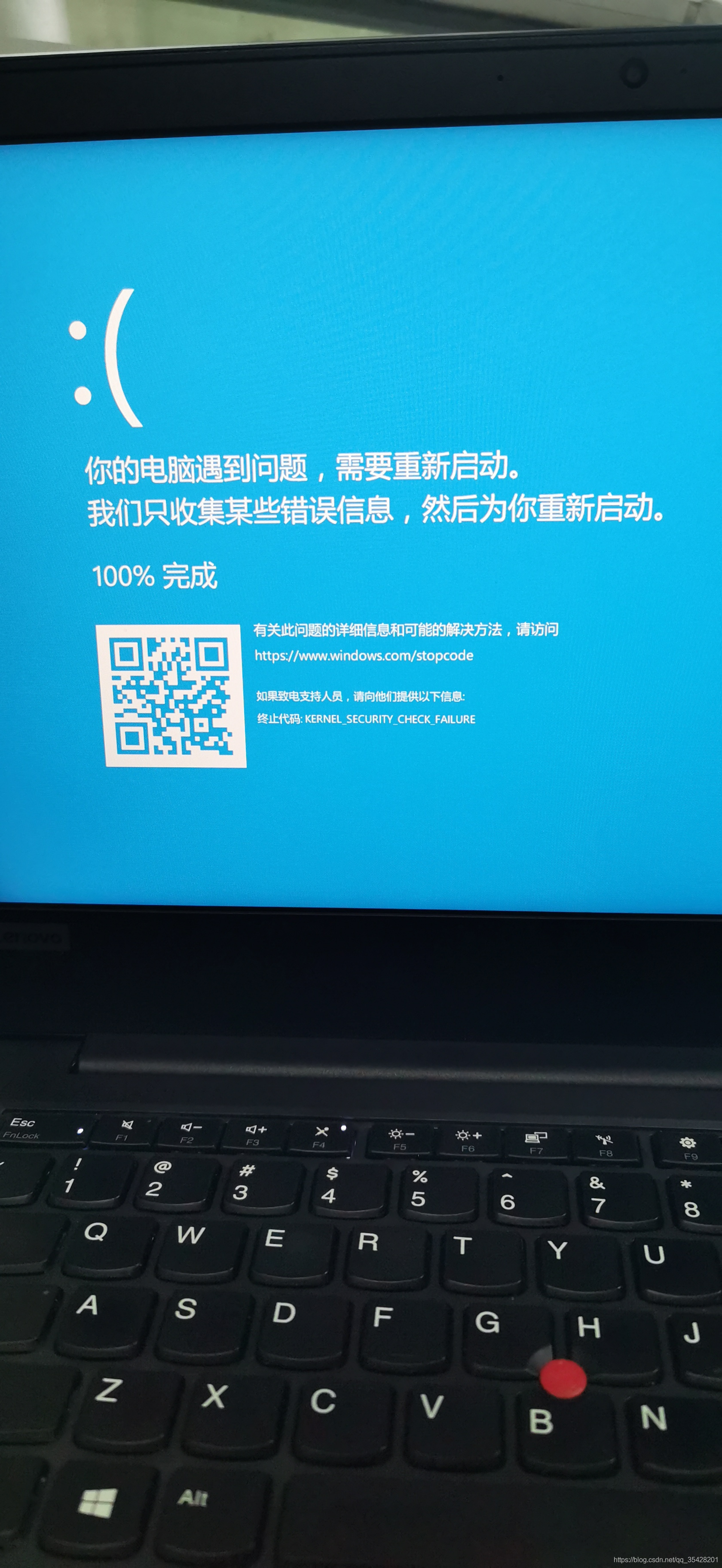
Windows事件查看器里也没有准确的导致蓝屏失败的原因

下载Debugging Tools for Windows 查看导致蓝屏根因。Debugging Tools for Windows下载链接。

Microsoft (R) Windows Debugger Version 10.0.18362.1 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [D:\Desktop\11\101219-51031-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 18362 MP (8 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff805`63c00000 PsLoadedModuleList = 0xfffff805`64046490
Debug session time: Sat Oct 12 09:47:39.711 2019 (UTC + 8:00)
System Uptime: 0 days 1:01:03.824
Loading Kernel Symbols
...............................................................
................................................................
................................................................
.................
Loading User Symbols
Loading unloaded module list
.............
For analysis of this file, run !analyze -v
4: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KERNEL_SECURITY_CHECK_FAILURE (139)
A kernel component has corrupted a critical data structure. The corruption
could potentially allow a malicious user to gain control of this machine.
Arguments:
Arg1: 0000000000000003, A LIST_ENTRY has been corrupted (i.e. double remove).
Arg2: ffffb58476316930, Address of the trap frame for the exception that caused the bugcheck
Arg3: ffffb58476316888, Address of the exception record for the exception that caused the bugcheck
Arg4: 0000000000000000, Reserved
Debugging Details:
------------------
*** WARNING: Unable to verify timestamp for topsecpf.sys
KEY_VALUES_STRING: 1
PROCESSES_ANALYSIS: 1
SERVICE_ANALYSIS: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 18362.1.amd64fre.19h1_release.190318-1202
SYSTEM_MANUFACTURER: LENOVO
SYSTEM_PRODUCT_NAME: 20N8002XCD
SYSTEM_SKU: LENOVO_MT_20N8_BU_SMB_FM_ThinkPad E490
SYSTEM_VERSION: ThinkPad E490
BIOS_VENDOR: LENOVO
BIOS_VERSION: R0YET35W (1.18 )
BIOS_DATE: 09/06/2019
BASEBOARD_MANUFACTURER: LENOVO
DUMP_TYPE: 2
BUGCHECK_P1: 3
BUGCHECK_P2: ffffb58476316930
BUGCHECK_P3: ffffb58476316888
BUGCHECK_P4: 0
TRAP_FRAME: ffffb58476316930 -- (.trap 0xffffb58476316930)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000001 rbx=0000000000000000 rcx=0000000000000003
rdx=ffff930d5b99d7e0 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80563e45d1d rsp=ffffb58476316ac0 rbp=fffff8056d877350
r8=fffff8056d877350 r9=0000000000000000 r10=fffff8056d872ca4
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up di pl nz na pe nc
nt!ExInterlockedInsertTailList+0x13ea0d:
fffff805`63e45d1d cd29 int 29h
Resetting default scope
EXCEPTION_RECORD: ffffb58476316888 -- (.exr 0xffffb58476316888)
ExceptionAddress: fffff80563e45d1d (nt!ExInterlockedInsertTailList+0x000000000013ea0d)
ExceptionCode: c0000409 (Security check failure or stack buffer overrun)
ExceptionFlags: 00000001
NumberParameters: 1
Parameter[0]: 0000000000000003
Subcode: 0x3 FAST_FAIL_CORRUPT_LIST_ENTRY
CPU_COUNT: 8
CPU_MHZ: 708
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 8e
CPU_STEPPING: c
CPU_MICROCODE: 6,8e,c,0 (F,M,S,R) SIG: B8'00000000 (cache) B8'00000000 (init)
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
BUGCHECK_STR: 0x139
PROCESS_NAME: eNSP_VBoxServer.exe
CURRENT_IRQL: 0
DEFAULT_BUCKET_ID: FAIL_FAST_CORRUPT_LIST_ENTRY
ERROR_CODE: (NTSTATUS) 0xc0000409 - <Unable to get error code text>
EXCEPTION_CODE: (NTSTATUS) 0xc0000409 - <Unable to get error code text>
EXCEPTION_CODE_STR: c0000409
EXCEPTION_PARAMETER1: 0000000000000003
ANALYSIS_SESSION_HOST: GJHE_THINKPAD
ANALYSIS_SESSION_TIME: 10-14-2019 09:01:05.0748
ANALYSIS_VERSION: 10.0.18362.1 amd64fre
LAST_CONTROL_TRANSFER: from fffff80563dd1ae9 to fffff80563dbfcc0
STACK_TEXT:
ffffb584`76316608 fffff805`63dd1ae9 : 00000000`00000139 00000000`00000003 ffffb584`76316930 ffffb584`76316888 : nt!KeBugCheckEx
ffffb584`76316610 fffff805`63dd1f10 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiBugCheckDispatch+0x69
ffffb584`76316750 fffff805`63dd02a5 : ffff930d`7750ebc8 00000000`00000000 ffff930d`7657bdd0 ffff930d`74c999e0 : nt!KiFastFailDispatch+0xd0
ffffb584`76316930 fffff805`63e45d1d : ffff930d`7657bdd0 fffff805`000002af ffff930d`5b99d7e0 fffff805`6d877360 : nt!KiRaiseSecurityCheckFailure+0x325
ffffb584`76316ac0 fffff805`6d872d14 : ffff930d`7657bdd0 ffffb584`76316bc9 ffff930d`61fddf10 ffff930d`7657bea3 : nt!ExInterlockedInsertTailList+0x13ea0d
ffffb584`76316af0 ffff930d`7657bdd0 : ffffb584`76316bc9 ffff930d`61fddf10 ffff930d`7657bea3 ffff930d`7657bea3 : topsecpf+0x2d14
ffffb584`76316af8 ffffb584`76316bc9 : ffff930d`61fddf10 ffff930d`7657bea3 ffff930d`7657bea3 fffff805`63c47079 : 0xffff930d`7657bdd0
ffffb584`76316b00 ffff930d`61fddf10 : ffff930d`7657bea3 ffff930d`7657bea3 fffff805`63c47079 ffff930d`7657bdd0 : 0xffffb584`76316bc9
ffffb584`76316b08 ffff930d`7657bea3 : ffff930d`7657bea3 fffff805`63c47079 ffff930d`7657bdd0 ffff930d`61fdddc0 : 0xffff930d`61fddf10
ffffb584`76316b10 ffff930d`7657bea3 : fffff805`63c47079 ffff930d`7657bdd0 ffff930d`61fdddc0 00000000`00000000 : 0xffff930d`7657bea3
ffffb584`76316b18 fffff805`63c47079 : ffff930d`7657bdd0 ffff930d`61fdddc0 00000000`00000000 00000000`656c6946 : 0xffff930d`7657bea3
ffffb584`76316b20 fffff805`63c46f47 : ffff930d`00000000 ffffcd0e`4e33f302 ffff930d`7071f260 00000000`c000000d : nt!IopfCompleteRequest+0x119
ffffb584`76316c30 fffff805`6d825391 : ffff930d`61fcc960 ffff930d`7689b9e0 ffff930d`61fcc8a0 00000000`00000000 : nt!IofCompleteRequest+0x17
ffffb584`76316c60 fffff805`63c31819 : 00000000`00000000 00000000`00000000 ffff930d`74f3cdf0 fffff805`641e7680 : tdx!TdxTdiDispatchCreate+0x431
ffffb584`76316cf0 fffff805`6d872eb6 : ffff930d`00000000 ffff930d`7657bea0 ffffb584`763170d0 ffff930d`5b99d7e0 : nt!IofCallDriver+0x59
ffffb584`76316d30 ffff930d`00000000 : ffff930d`7657bea0 ffffb584`763170d0 ffff930d`5b99d7e0 ffff930d`7657bf30 : topsecpf+0x2eb6
ffffb584`76316d38 ffff930d`7657bea0 : ffffb584`763170d0 ffff930d`5b99d7e0 ffff930d`7657bf30 ffff930d`7657bdd0 : 0xffff930d`00000000
ffffb584`76316d40 ffffb584`763170d0 : ffff930d`5b99d7e0 ffff930d`7657bf30 ffff930d`7657bdd0 ffff930d`64207e00 : 0xffff930d`7657bea0
ffffb584`76316d48 ffff930d`5b99d7e0 : ffff930d`7657bf30 ffff930d`7657bdd0 ffff930d`64207e00 fffff805`6d87126d : 0xffffb584`763170d0
ffffb584`76316d50 ffff930d`7657bf30 : ffff930d`7657bdd0 ffff930d`64207e00 fffff805`6d87126d ffff930d`7657bee8 : 0xffff930d`5b99d7e0
ffffb584`76316d58 ffff930d`7657bdd0 : ffff930d`64207e00 fffff805`6d87126d ffff930d`7657bee8 ffff930d`7657bdd0 : 0xffff930d`7657bf30
ffffb584`76316d60 ffff930d`64207e00 : fffff805`6d87126d ffff930d`7657bee8 ffff930d`7657bdd0 ffff930d`7657bdd0 : 0xffff930d`7657bdd0
ffffb584`76316d68 fffff805`6d87126d : ffff930d`7657bee8 ffff930d`7657bdd0 ffff930d`7657bdd0 fffff805`641e2bb0 : 0xffff930d`64207e00
ffffb584`76316d70 ffff930d`7657bee8 : ffff930d`7657bdd0 ffff930d`7657bdd0 fffff805`641e2bb0 ffff930d`61fddf10 : topsecpf+0x126d
ffffb584`76316d78 ffff930d`7657bdd0 : ffff930d`7657bdd0 fffff805`641e2bb0 ffff930d`61fddf10 fffff805`6d871739 : 0xffff930d`7657bee8
ffffb584`76316d80 ffff930d`7657bdd0 : fffff805`641e2bb0 ffff930d`61fddf10 fffff805`6d871739 ffff930d`61fdddc0 : 0xffff930d`7657bdd0
ffffb584`76316d88 fffff805`641e2bb0 : ffff930d`61fddf10 fffff805`6d871739 ffff930d`61fdddc0 ffff930d`7657bee8 : 0xffff930d`7657bdd0
ffffb584`76316d90 fffff805`641e3e1b : ffffb584`763170d0 fffff805`641e3704 ffffb584`76317040 ffff930d`768c32f0 : nt!IopAllocRealFileObject+0x190
ffffb584`76316e60 fffff805`641eadef : ffff930d`64207e00 ffff930d`64207d04 ffff930d`760689e0 ffffcd0e`38c0d100 : nt!IopParseDevice+0x62b
ffffb584`76316fd0 fffff805`641e9251 : ffff930d`76068900 ffffb584`76317218 00000000`00000240 ffff930d`5bf134e0 : nt!ObpLookupObjectName+0x78f
ffffb584`76317190 fffff805`6422dd50 : 00000000`00000001 ffffb584`76317490 00000000`00000000 00000000`00000000 : nt!ObOpenObjectByNameEx+0x201
ffffb584`763172d0 fffff805`6422c18a : ffff930d`7071f308 ffff930d`c0100000 ffffb584`76317490 ffffb584`76317480 : nt!IopCreateFile+0x820
ffffb584`76317370 fffff805`6d961a4e : ffff930d`7071f260 ffff930d`6fa97080 ffff930d`6fa97080 fffff805`6d934f5a : nt!IoCreateFile+0x8a
ffffb584`76317400 fffff805`6d94c1f3 : ffff930d`7695a6d0 00000000`00000002 ffff930d`7695a6d0 00000000`00000000 : afd!AfdCreateConnection+0x13df2
ffffb584`76317530 fffff805`6d957bfd : ffff930d`73798dc0 00000000`00000080 ffff930d`7695a6d0 ffff930d`64711e30 : afd!AfdSuperConnect+0x343
ffffb584`763176f0 fffff805`63c31819 : ffff930d`73798dc0 00000000`00000000 00000000`00000003 00000000`0000001a : afd!AfdDispatchDeviceControl+0x7d
ffffb584`76317720 fffff805`641e7215 : ffff930d`73798dc0 00000000`00000000 ffff930d`73798dc0 00000000`00000000 : nt!IofCallDriver+0x59
ffffb584`76317760 fffff805`641e7020 : 00000000`00000000 00000000`00000000 ffff930d`7750e9e0 ffffb584`76317a80 : nt!IopSynchronousServiceTail+0x1a5
ffffb584`76317800 fffff805`641e63f6 : 00000000`00000000 00000000`00000000 00000000`00000001 00000000`05866cac : nt!IopXxxControlFile+0xc10
ffffb584`76317920 fffff805`63dd1515 : ffffffff`fd9da600 00000000`08c6e9f8 00738708`00000000 00000000`01312d00 : nt!NtDeviceIoControlFile+0x56
ffffb584`76317990 00000000`77a61cbc : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x25
00000000`08c6f308 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x77a61cbc
THREAD_SHA1_HASH_MOD_FUNC: a48cec2c1706e3ad230e97a390f54db35c9c53a0
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 4c15f7931c0d7078a2c4627ec0ce89c23100fe46
THREAD_SHA1_HASH_MOD: fd8940a1bff1b3d26f255ce1483333934620b317
FOLLOWUP_IP:
topsecpf+2d14
fffff805`6d872d14 4885f6 test rsi,rsi
FAULT_INSTR_CODE: 74f68548
SYMBOL_STACK_INDEX: 5
SYMBOL_NAME: topsecpf+2d14
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: topsecpf
IMAGE_NAME: topsecpf.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4d6da0f2
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 2d14
FAILURE_BUCKET_ID: 0x139_3_CORRUPT_LIST_ENTRY_topsecpf!unknown_function
BUCKET_ID: 0x139_3_CORRUPT_LIST_ENTRY_topsecpf!unknown_function
PRIMARY_PROBLEM_CLASS: 0x139_3_CORRUPT_LIST_ENTRY_topsecpf!unknown_function
TARGET_TIME: 2019-10-12T01:47:39.000Z
OSBUILD: 18362
OSSERVICEPACK: 295
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 1998-05-31 05:12:57
BUILDDATESTAMP_STR: 190318-1202
BUILDLAB_STR: 19h1_release
BUILDOSVER_STR: 10.0.18362.1.amd64fre.19h1_release.190318-1202
ANALYSIS_SESSION_ELAPSED_TIME: 6afe
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:0x139_3_corrupt_list_entry_topsecpf!unknown_function
FAILURE_ID_HASH: {7d6915eb-8c8b-b32e-d4d4-a1676df73917}
Followup: MachineOwner
---------
找到原因:topsecpf驱动问题,“topsec”是安全厂商天融信,最近确实是装了天融信的SSL VPN客户端。
删掉继续测试,系统运行正常,未出现蓝屏,问题解决。






















 8278
8278











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








