原题:
Shoulder-surfing is the behavior of intentionally and stealthily watching the screen of another person’s
electronic device, such as laptop computer or mobile phone. Since mobile devices prevail, it is getting
serious to steal personal information by shoulder-surfing.
Suppose that we have a smart phone. If we touch the screen keyboard directly to enter the password,
this is very vulnerable since a shoulder-surfer easily knows what we have typed. So it is desirable to
conceal the input information to discourage shoulder-surfers around us. Let me explain one way to do
this.
You are given a 6 × 5 grid. Each column can be considered the visible part of a wheel. So you can
easily rotate each column wheel independently to make password characters visible. In this problem,
we assume that each wheel contains the 26 upper letters of English alphabet.
See the following Figure 1.
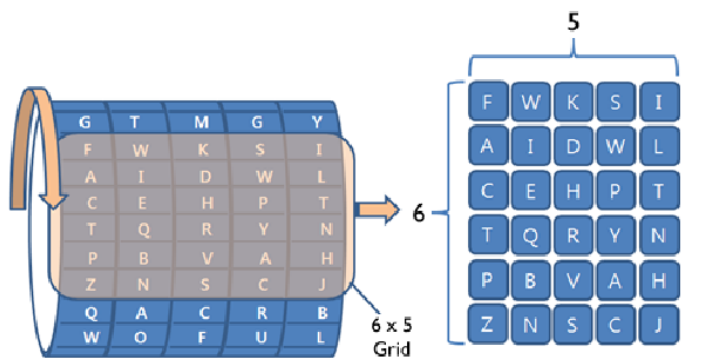
Figure 1. 6 × 5 window clips a valid grid representation for a password.
Assume that we have a length-5 password such as p 1 p 2 p 3 p 4 p 5 . In order to pass the authentication
procedure, we should construct a configuration of grid space where each p i appears in the i-th column
of the grid. In that situation we say that the user password is accepted.
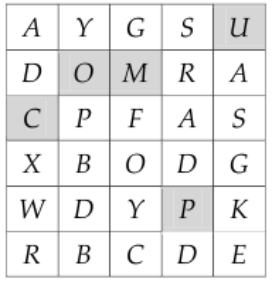
Figure 2. A valid grid
representation for password
‘COMPU’.
Let me start with one example. Suppose that our password was set ‘COMPU’. If we construct the grid as shown in Figure 2 on next page, then the authentication is successfully processed. In this password system, the position of each password character in each column is meaningless. If each of the 5 characters in p 1 p 2 p 3 p 4 p 5 appears in the corresponding column, that can be considered the correct password. So there are many grid configurations allowing one password. Note that the sequence of letters on each wheel is randomly determined for each trial and for each column. In practice, the user is able to rotate each column and press “Enter” key, so a should-surfer cannot perceive the password
by observing the 6 × 5 grid since there are too many password candidates. In this 6 × 5 grid space, maximally 6 5 = 7,776 cases are possible. This is the basic idea of the proposed password system
against shoulder-surfers.Unfortunately there is a problem. If a shoulder-surfer can observe more than two grid plate configurations for a person, then the shoulder-surfer can reduce the searching space and guess the correct password. Even though it is not easy to stealthily observe other’s more than once, this is one weakness of implicit grid passwords.Let me show one example with two observed configurations for a grid password. The user password is ‘COMPU’, but ‘DPMAG’ is also one candidate password derived from the following configuration.
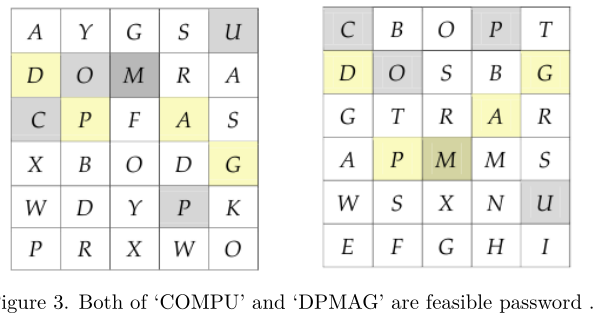
You are given two configurations of grid password from a shoulder-surfer. Suppose that you have
succeeded to stealthily record snapshots of the target person’s device (e.g. smart phone). Then your
next task is to reconstruct all possible passwords from these two snapshots. Since there are lots of
password candidates, you are asked for the k-th password among all candidates in lexicographical
order. In Figure 3, let us show the first 5 valid password. The first 5 valid passwords are ‘ABGAG’ ,
‘ABGAS’, ‘ABGAU’, ‘ABGPG’ and ‘ABGPS’.
The number k is given in each test case differently. If there does not exist a k-th password since k
is larger than the number of all possible passwords, then you should print ‘NO’ in the output.
Input
Your program is to read from standard input. The input consists of T test cases. The number of test
cases T is given in the first line of the input. The first line of each test case contains one integer, K,
the order of the password you should find. Note that 1 ≤ K ≤ 7,777. Next the following 6 lines show
the 6 rows of the first grid and another 6 lines represent the 6 rows of the second grid.
Output
Your program is to write to standard output. Print exactly the k-th password (including ‘NO’) in one
line for each test case.
The following shows sample input and output for three test cases.
Sample Input
3
1
AYGSU
DOMRA
CPFAS
XBODG
WDYPK
PRXWO
CBOPT
DOSBG
GTRAR
APMMS
WSXNU
EFGHI
5
AYGSU
DOMRA
CPFAS
XBODG
WDYPK
PRXWO
CBOPT
DOSBG
GTRAR
APMMS
WSXNU
EFGHI
64
FGHIJ
EFGHI
DEFGH
CDEFG
BCDEF
ABCDE
WBXDY
UWYXZ
XXZFG
YYFYH
EZWZI
ZGHIJ
Sample Output
ABGAG
ABGPS
NO
中文:
给出两个6行5列的字母矩阵,一个密码满足:密码的第i个字母在两个字母矩阵的第i列均出现。然后找出字典序为k的密码,如果不存在输出NO。
#include<bits/stdc++.h>
using namespace std;
char s1[6][5],s2[6][5],ss[6][5];
bool marka[27],markb[27];
int tot[6];
int cnt[5];
int main()
{
ios::sync_with_stdio(false);
int t,k;
cin>>t;
while(t--)
{
cin>>k;
k--;
for(int i=0;i<6;i++)
cin>>s1[i];
for(int i=0;i<6;i++)
cin>>s2[i];
memset(tot,0,sizeof(tot));
memset(cnt,0,sizeof(cnt));
for(int i=0;i<5;i++)
{
memset(marka,false,sizeof(marka));
memset(markb,false,sizeof(markb));
for(int j=0;j<6;j++)
marka[s1[j][i]-'A']=true;
for(int j=0;j<6;j++)
markb[s2[j][i]-'A']=true;
for(int j=0;j<26;j++)
if(marka[j]&&markb[j])
ss[i][cnt[i]++]='A'+j;
}
tot[5]=1;
for(int i=4;i>=0;i--)
tot[i]=cnt[i]*tot[i+1];
if(k>=tot[0])
{
cout<<"NO"<<endl;
continue;
}
for(int i=0;i<5;i++)
{
int j=k/tot[i+1];
cout<<ss[i][j];
k=k%tot[i+1];
}
cout<<endl;
}
return 0;
}
解答:
这题真是又臭又长-_-!!!
编译器换成了C++14,不知道是因为编译器优化做的好还是什么原因,自己跑了n多数据都没问题,一提交就RE。后来参考别人代码,改成用C语言的字符串就过了。
紫书上的例题,思路很简单,暴力可以,用数学公式算也很简单。首先把两侧对应列都出现的字母都挑出来,然后考虑每一列到后面的列可以有多少种组合,然后,用k值去除以当前列的元素个数即为选中的字母(自己在纸上写两下就知道了)





















 744
744











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








