dir 显示当前目录文件,ls -al 显示包括隐藏文件(同win2K的 dir)
pwd 查询当前所在的目录位置
cd cd ..回到上一层目录,注意cd 与..之间有空格。cd /返回到根目录。
cat 文件名 查看文件内容
cat >abc.txt 往abc.txt文件中写上内容。
more 文件名 以一页一页的方式显示一个文本文件。
cp 复制文件
mv 移动文件
rm 文件名 删除文件,rm -a 目录名删除目录及子目录
rm -r 强制删除目录
mkdir 目录名 建立目录
rmdir 删除子目录,目录内没有文档。
chmod 设定档案或目录的存取权限
grep 在档案中查找字符串
diff 档案文件比较
find 档案搜寻
date 现在的日期、时间
who 查询目前和你使用同一台机器的人以及Login时间地点
w 查询目前上机者的详细资料
whoami 查看自己的帐号名称
groups 查看某人的Group
passwd 更改密码
history 查看自己下过的命令
ps 显示进程状态
net-tools: => 如果 ifconfig 找不到 需要安装
kill 停止某进程 kill -9 1234(进程ID)
关闭某个端口
步骤:1. netstat -anp | grep 8082 查找对应进程,tcp6 0 0 :::8082 :::* LISTEN 2718/java
2. 然后执行 kill -9 2718
gcc 黑客通常用它来编译C语言写的文件
su 权限转换为指定使用者
telnet IP telnet连接对方主机(同win2K),当出现bash$时就说明连接成功。
ftp ftp连接上某服务器(同win2K)
sudo passwd root 修改root的密码或者警用开启root
su root 切换到root用户
LINUX基本使用
ifconfig -a 查看没有被载入的网卡
ifconfig eth1 up 激活网卡
dhclient eht1 自动获取IP
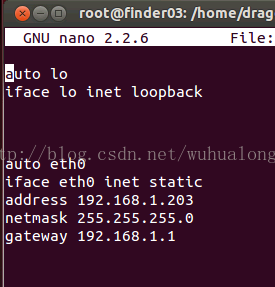
nano /etc/network/interfaces 网卡信息文件
ifconfig eth1 192.168.0.222 netmask 255.255.255.0 设置IP地址掩码 ==》设置临时IP
route add default gw 192.168.0.254 设置网关
nano /etc/resolv.conf nameserver 192.168.4.4 修改DNS GOOGLE提供 DNS1 8.8.8.8
=========centos 静态ip设置======
vi /etc/sysconfig/network => GATEWAY=192.168.0.1
修改 BOOTPROTO="static"
添加 NETMASK IPADDR DNS1
NETMASK=255.255.255.0
IPADDR=192.168.0.108
DNS1=218.4.4.4
vi /etc/resolv.conf 输入 nameserver 218.4.4.4 上网设置
service network restart 或者 ifdown 网卡名称 ifup..
apt-get install language-selector 安装中文输入法
进入System -> Administrator ->Language Support
安装和卸载
安装软件 apt-get install softname1 softname2 softname3……
卸载软件 apt-get remove softname1 softname2 softname3……
卸载并清除配置 apt-get remove --purge softname1
更新软件信息数据库 apt-get update
进行系统升级 apt-get upgrade
搜索软件包 apt-cache search softname1 softname2 softname3……
安装deb软件包 dpkg -i xxx.deb
删除软件包 dpkg -r xxx.deb
连同配置文件一起删除 dpkg -r --purge xxx.deb
查看软件包信息 dpkg -info xxx.deb
查看文件拷贝详情 dpkg -L xxx.deb
查看系统中已安装软件包信息 dpkg -l
重新配置软件包 dpkg-reconfigure xxx
探测扫描工具:
dnsenum, dnsmap , maltego
traceroute (ICMP+ECHO)
tcptraceroute(SYN+ACK) -- 推荐 tcptraceroute www.finderbao.com,
ping (ICMP) , fping (ICMP), genlist (ICMP)- 只列出在线主机
arping ( 直连)
hping3(可以TCP 、UDP 强大 但是复杂http://www.hping.org/)
nbtscan(扫描网段对应的主机,网卡地址等 nbtscan -r 192.168.1.1-110)
nping (允许发送TCP,UDP,ICMP,ARP 比较hping3好操作)
=> nping -c 1 --tcp -p 80 --flag SYN www.finderbao.com 返回 SYN+ACK
=>nping -c 1 --tcp -p 80 --flag ACK www.finderbao.com 服务器返回 R 还没有建立TCP
=> nping -c 1 --udp -p 80 www.finderbao.com (port unreachable)
onesixtyone(破解路由密码) => ./onesixtyone -c dict.txt 192.168.1.1
protos(路由协议探测) =>./protos -v -i eth1 -d 192.168.1.103
root@bt:/pentest/enumeration/irpas# ./protos -v -i eth1 -d 192.168.1.103
192.168.1.103 is alive
TARGET 192.168.1.103
Running in verbose mode
Afterscan delay is 3
running in fast scan - pause every 1 probes
continuing scan afterwards for 3 secs
supported protocols will be reported
you supplied the target(s) 192.168.1.103
Scanning 192.168.1.103
>>>>>>>>> RESULTS >>>>>>>>>>
192.168.1.103 may be running (did not negate):
ICMP IGMP ST TCP IGP NVP-II ARGUS XNET UDP DCN-MEAS PRM TRUNK-1 LEAF-1 RDP ISO-TP4 MFE-NSP SEP IDPR IDPR-CMTP IL IPv6 IPv6-Frag RSVP MHRP ESP AH NARP TLSP IPv6-ICMP IPv6-Opts CFTP SAT-EXPAK RVD 68 VISA CPNX WSN BR-SAT-MON WB-MON ISO-IP SECURE-VMTP TTP DGP EIGRP Sprite-RPC MTP IPIP ETHERIP 99PrivEncr IFMP PIM SCPS A/N SNP IPX-in-IP L2TP IATP SRP SMP PTP FIRE CRUDP IPLT PIPE FC 135 137 139 141 143 145 148 150 152 154 156 158 160 162 164 166 168 170 172 174 176 178 180 182 184 186 188 190 193 195 197 199 201 203 205 207 209 211 213 215 217 219 221 223 225 228 230 232 235 237 239 241 243 246 248 250 252 254 p0f (监听SYN, 判断操作系统类型 效果不行,没有测试成功, 被动检测) => p0f
xprobe2 (主动OS指纹探测) => xprobe2 ip|host 我自己的win7的 他探测结果是xp的
root@bt:~# xprobe2 www.baidu.com
Xprobe-ng v.2.1 Copyright (c) 2002-2009 fyodor@o0o.nu, ofir@sys-security.com, meder@o0o.nu
[+] Target is www.baidu.com
[+] Loading modules.
[+] Following modules are loaded:
[x] ping:icmp_ping - ICMP echo discovery module
[x] ping:tcp_ping - TCP-based ping discovery module
[x] ping:udp_ping - UDP-based ping discovery module
[x] infogather:ttl_calc - TCP and UDP based TTL distance calculation
[x] infogather:portscan - TCP and UDP PortScanner
[x] fingerprint:icmp_echo - ICMP Echo request fingerprinting module
[x] fingerprint:icmp_tstamp - ICMP Timestamp request fingerprinting module
[x] fingerprint:icmp_amask - ICMP Address mask request fingerprinting module
[x] fingerprint:icmp_info - ICMP Information request fingerprinting module
[x] fingerprint:icmp_port_unreach - ICMP port unreachable fingerprinting module
[x] fingerprint:tcp_hshake - TCP Handshake fingerprinting module
[x] fingerprint:tcp_rst - TCP RST fingerprinting module
[x] app:smb - SMB fingerprinting module
[x] app:snmp - SNMPv2c fingerprinting module
[x] app:ftp - FTP fingerprinting tests
[x] app:http - HTTP fingerprinting tests
[+] 16 modules registered
[+] Initializing scan engine
[+] Running scan engine
fingerprint:icmp_tstamp has not enough data
Executing ping:icmp_ping
Executing fingerprint:icmp_port_unreach
Executing fingerprint:icmp_echo
Executing fingerprint:tcp_rst
fingerprint:tcp_hshake has not enough data
Executing fingerprint:icmp_amask
Executing fingerprint:icmp_tstamp
Executing fingerprint:icmp_info
Executing app:snmp
app:smb has not enough data
ping:tcp_ping has not enough data
ping:udp_ping has not enough data
infogather:ttl_calc has not enough data
Executing infogather:portscan
Executing app:ftp
Executing app:http
[+] Primary Network guess:
[+] Host 119.75.217.56 Running OS: "Apple Mac OS X 10.5" (Guess probability: 93%)
[+] Other guesses:
[+] Host 119.75.217.56 Running OS: "AIX 4.3.3" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "HP JetDirect ROM L.20.07 EEPROM L.20.24" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "FreeBSD 5.2.1" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "FreeBSD 5.3" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "FreeBSD 5.4" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "FreeBSD 4.6.2" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "FreeBSD 4.6" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "FreeBSD 4.5" (Guess probability: 86%)
[+] Host 119.75.217.56 Running OS: "FreeBSD 4.4" (Guess probability: 86%)
[+] Cleaning up scan engine
[+] Modules deinitialized
[+] Execution completed.autoscan(图形化端口扫描),不行
netifera(可以扫描可以抓包还能探测SNMP简单密钥)
nmap(黑客必备 -- 强烈推荐 速度快 , OS探测,扫描,追踪)
=>nmap -v -n -sP 192.168.0.1-255 (ICMP 扫描)
=>nmap -v -n -A 192.168.0.1-255 (扫描OS,服务, 端口,端口对应的应用)
amap(服务探测-扫描端口上运行的应用) 有时测试结果还不如 nmap
httprint (也是发送包去探测,然后匹配,有一个singnatrue.txt文件字典匹配) 注意是在web目录下 。菜单有问题
=>root@bt:/pentest/enumeration/web/httprint/linux# ./httprint -h www.i201314.net -s signatures.txt 没有扫描到
httsquash(和httpprint类似,感觉下效果比httprint好点)
root@bt:/pentest/scanners/httsquash# ./httsquash -r www.i201314.net
FOUND: 222.73.204.180 80
HTTP/1.1 302 Redirect
Date: Mon, 09 Jul 2012 09:41:33 GMT
Content-Length: 152
Content-Type: text/html
Location: http://web.idccdns.cn/noa.htm
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NETike-scan(IKE扫描工具,IPC SEC策略探测)
root@bt:~# ike-scan -M -v 192.168.0.1
DEBUG: pkt len=336 bytes, bandwidth=56000 bps, int=52000 us
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
--- Pass 1 of 3 completed
--- Pass 2 of 3 completed
--- Pass 3 of 3 completed
sslscan (策略探测,算法 证书)
root@bt:~# sslscan 192.168.0.117
_
___ ___| |___ ___ __ _ _ __
/ __/ __| / __|/ __/ _` | '_ \
\__ \__ \ \__ \ (_| (_| | | | |
|___/___/_|___/\___\__,_|_| |_|
Version 1.8.2
http://www.titania.co.uk
Copyright Ian Ventura-Whiting 2009
Testing SSL server 192.168.0.117 on port 443
Supported Server Cipher(s):
Rejected SSLv2 168 bits DES-CBC3-MD5
Rejected SSLv2 56 bits DES-CBC-MD5
Rejected SSLv2 40 bits EXP-RC2-CBC-MD5
Rejected SSLv2 128 bits RC2-CBC-MD5
Rejected SSLv2 40 bits EXP-RC4-MD5
Rejected SSLv2 128 bits RC4-MD5
Rejected SSLv3 256 bits ADH-AES256-SHA
Rejected SSLv3 256 bits DHE-RSA-AES256-SHA
Rejected SSLv3 256 bits DHE-DSS-AES256-SHA
Accepted SSLv3 256 bits AES256-SHA
Rejected SSLv3 128 bits ADH-AES128-SHA
Rejected SSLv3 128 bits DHE-RSA-AES128-SHA
Rejected SSLv3 128 bits DHE-DSS-AES128-SHA
Accepted SSLv3 128 bits AES128-SHA
Rejected SSLv3 168 bits ADH-DES-CBC3-SHA
Rejected SSLv3 56 bits ADH-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-ADH-DES-CBC-SHA
Rejected SSLv3 128 bits ADH-RC4-MD5
Rejected SSLv3 40 bits EXP-ADH-RC4-MD5
Rejected SSLv3 168 bits EDH-RSA-DES-CBC3-SHA
Rejected SSLv3 56 bits EDH-RSA-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-EDH-RSA-DES-CBC-SHA
Rejected SSLv3 168 bits EDH-DSS-DES-CBC3-SHA
Rejected SSLv3 56 bits EDH-DSS-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-EDH-DSS-DES-CBC-SHA
Accepted SSLv3 168 bits DES-CBC3-SHA
Rejected SSLv3 56 bits DES-CBC-SHA
Rejected SSLv3 40 bits EXP-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-RC2-CBC-MD5
Rejected SSLv3 128 bits RC4-SHA
Rejected SSLv3 128 bits RC4-MD5
Rejected SSLv3 40 bits EXP-RC4-MD5
Rejected SSLv3 0 bits NULL-SHA
Rejected SSLv3 0 bits NULL-MD5
Rejected TLSv1 256 bits ADH-AES256-SHA
Rejected TLSv1 256 bits DHE-RSA-AES256-SHA
Rejected TLSv1 256 bits DHE-DSS-AES256-SHA
Accepted TLSv1 256 bits AES256-SHA
Rejected TLSv1 128 bits ADH-AES128-SHA
Rejected TLSv1 128 bits DHE-RSA-AES128-SHA
Rejected TLSv1 128 bits DHE-DSS-AES128-SHA
Accepted TLSv1 128 bits AES128-SHA
Rejected TLSv1 168 bits ADH-DES-CBC3-SHA
Rejected TLSv1 56 bits ADH-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-ADH-DES-CBC-SHA
Rejected TLSv1 128 bits ADH-RC4-MD5
Rejected TLSv1 40 bits EXP-ADH-RC4-MD5
Rejected TLSv1 168 bits EDH-RSA-DES-CBC3-SHA
Rejected TLSv1 56 bits EDH-RSA-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-EDH-RSA-DES-CBC-SHA
Rejected TLSv1 168 bits EDH-DSS-DES-CBC3-SHA
Rejected TLSv1 56 bits EDH-DSS-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-EDH-DSS-DES-CBC-SHA
Accepted TLSv1 168 bits DES-CBC3-SHA
Rejected TLSv1 56 bits DES-CBC-SHA
Rejected TLSv1 40 bits EXP-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-RC2-CBC-MD5
Rejected TLSv1 128 bits RC4-SHA
Rejected TLSv1 128 bits RC4-MD5
Rejected TLSv1 40 bits EXP-RC4-MD5
Rejected TLSv1 0 bits NULL-SHA
Rejected TLSv1 0 bits NULL-MD5
Prefered Server Cipher(s):
SSLv3 256 bits AES256-SHA
TLSv1 256 bits AES256-SHA
SSL Certificate:
Version: 2
Serial Number: -4294967295
Signature Algorithm: sha1WithRSAEncryption
Issuer: /C=US/L=Palo Alto/OU=VMware/CN=VMware/emailAddress=none@vmware.com
Not valid before: May 23 04:57:27 2012 GMT
Not valid after: May 23 04:57:27 2013 GMT
Subject: /C=US/L=Palo Alto/OU=VMware/CN=VMware/emailAddress=none@vmware.com
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Modulus (2048 bit):
00:db:a1:4e:a9:52:30:64:b9:33:4e:e8:fc:69:6b:
c7:73:e0:98:cd:44:13:ce:9f:11:3a:25:99:3e:83:
16:2a:8c:2e:f8:c3:af:47:30:93:18:15:9d:42:ea:
19:4b:03:4f:11:80:48:e4:ad:d8:23:51:b8:6c:67:
3b:2b:a4:bf:ed:2e:da:29:dc:56:9c:70:23:f6:46:
51:36:fd:34:ae:27:d3:b8:6c:db:0d:af:15:0b:90:
10:91:05:bf:99:f5:97:70:dc:24:f5:27:fb:7a:e4:
73:48:56:02:0e:85:ea:bb:e5:52:30:e9:14:c1:42:
77:1b:2b:e1:f5:b0:a4:4d:8d:76:5e:3d:e9:d6:2d:
1e:58:28:4f:9b:28:36:8d:05:a0:0f:1e:e9:4c:1a:
06:19:70:da:93:7c:f8:4a:74:59:d0:da:9e:22:84:
14:0c:bb:8b:32:2c:7c:36:f2:89:ca:28:55:67:c7:
6e:85:f0:7a:e4:58:78:a1:92:dc:6c:4f:35:a0:01:
86:54:58:21:90:ad:70:c5:e6:f1:3c:ab:c8:ee:e2:
4c:76:02:db:ac:db:a6:28:77:78:f0:4a:26:86:ea:
e1:3d:3d:a5:94:5e:8d:2e:7a:ca:9b:5e:93:11:49:
e7:0c:07:01:59:f7:3a:4e:b6:12:b9:6a:75:ee:94:
84:69
Exponent: 65537 (0x10001)
X509v3 Extensions:
X509v3 Subject Key Identifier:
DD:9B:78:41:36:8A:0B:0A:F0:B8:51:94:9E:D8:AF:4B:B9:5D:B9:CF
X509v3 Authority Key Identifier:
keyid:DD:9B:78:41:36:8A:0B:0A:F0:B8:51:94:9E:D8:AF:4B:B9:5D:B9:CF
DirName:/C=US/L=Palo Alto/OU=VMware/CN=VMware/emailAddress=none@vmware.com
serial:D4:BB:98:2F:2C:2D:AB:21
X509v3 Basic Constraints:
CA:TRUE
Verify Certificate:
self signed certificate





















 7825
7825











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








