ezre
pythonEXE
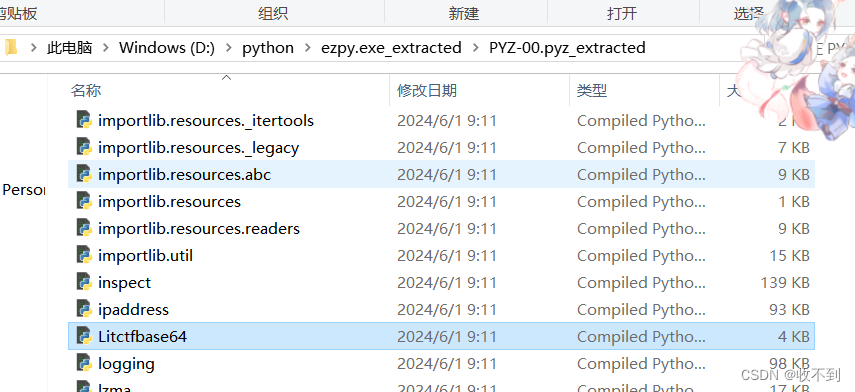
附件拖到和pyins。。。一个目录下
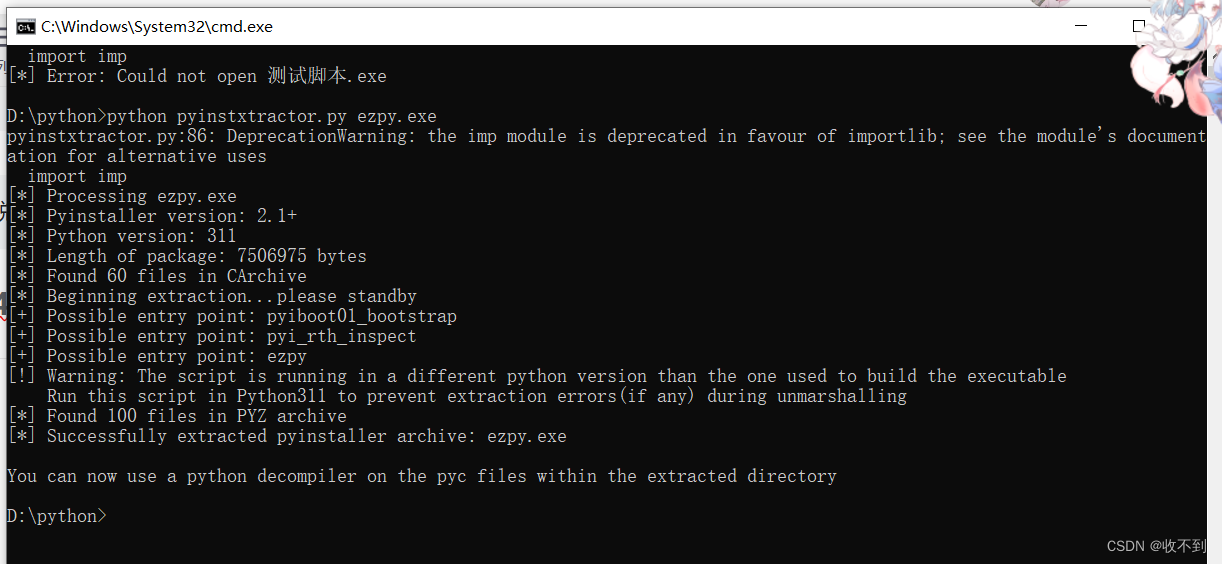
找到ezpy加后缀pyc
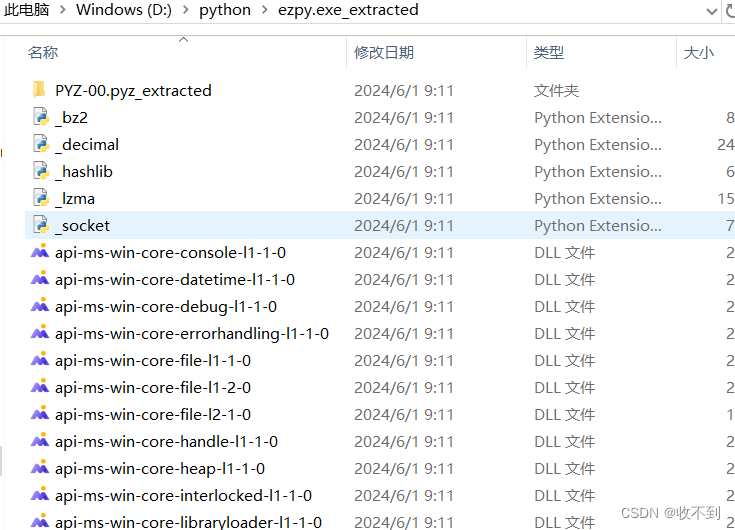
在第一个文件里找一个文件看字节戳,复制
打开ezre
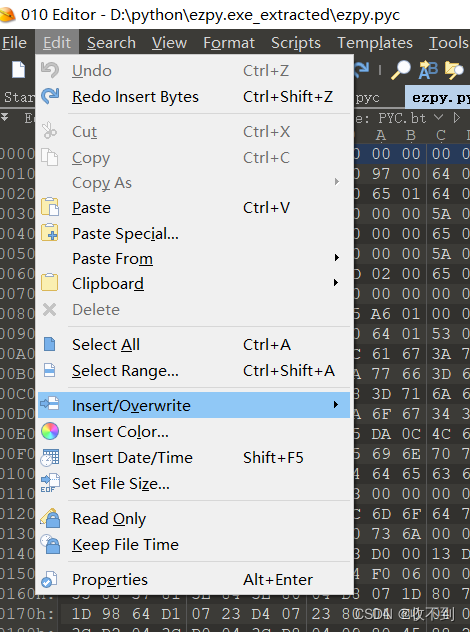

把ezpy 加上.pyc
然后执行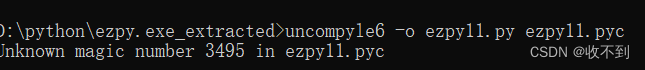
python3.11的用不了,去在线网站,用不了啊
使用pycdc工具,严格来说无法还原为python文件,但能看到其源代码
将pycdc.exe文件跟要还原的pyc文件放入同一个文件夹,在命令行输入命令可以在命令行显示pyc文件内的python源代码pycdc ea_py.pyc
如果想要保存到一个文件中:pycdc.exe xxx.pyc > 1.txt
先用在线网站吧
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 3.11
import Litctfbase64
flag = input('flag:')
flag = Litctfbase64.b64decode(flag)
if flag == 'X=3o4hx=0EZwf=mMv13gX=3o4hx=qje2ZjtgZQmEKXZog4==':
print('win')
return None
print('no')然后卡在这里了
导入了自定义库
在这个路径下
学习学习
然后同理丢到在线网站反编译
心情好的时候装一下pycdc

base64变表
import base64
import string
str1 = "X=3o4hx=0EZwf=mMv13gX=3o4hx=qje2ZjtgZQmEKXZog4=="
string1 = "8kuWYm=1JiUPs7DT4x+X5tcqZKfGvA0gFLB6y3QbV2rNOlRdMwnEohjzSe9/HIa-"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
print (base64.b64decode(str1.translate(str.maketrans(string1,string2))))
#b'LitCTF{61happy_LitCTF_nice_base64}\x01\x86'编码喵
base64换表
shift F12直接看字符串即可
import base64
import string
str1 = "tgL0q1rgEZaZmdm0zwq4lweYzgeTngfHnI1ImMm5ltaXywnLowuYnJmWmx0="
string1 = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
print(base64.b64decode(str1.translate(str.maketrans(string1, string2))))
#LitCTF{03034ed8-a2da-4aa6-b2c9-01ace9e26301}hello_upx

ESP脱壳定律---不会
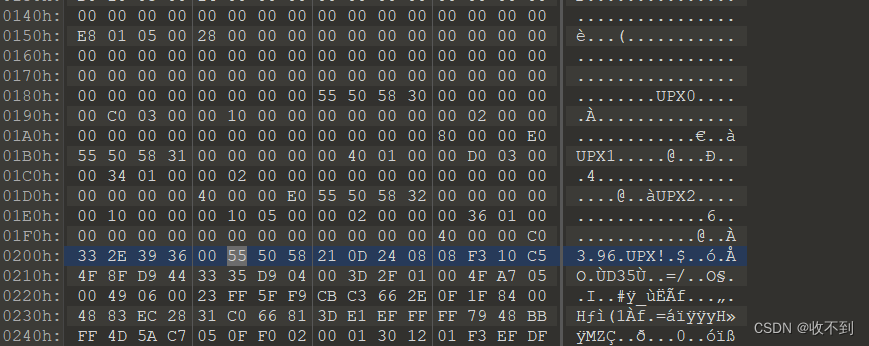
刚刚一个叹号那个没修改,一共修改四处
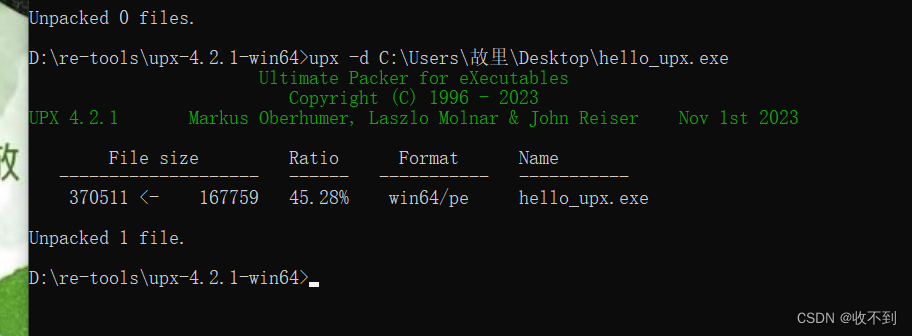
64位打开
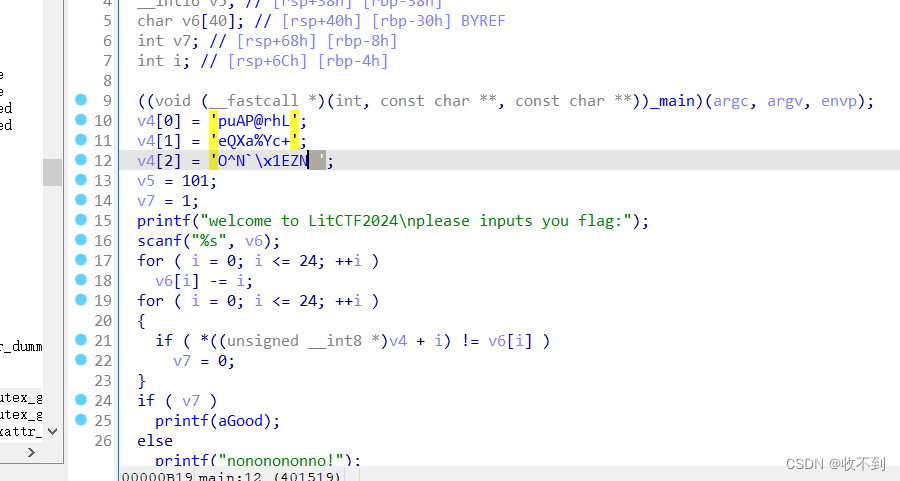
脚本
#include<stdio.h>
#include<string.h>
int main()
{
int i,j;
char ch;
char v6[40];//flag
//unsigned char v4[]="puAP@rhLeQXa%Yc+O^N`\x1EZN";
unsigned char v4[]="Lhr@PAup+cY%aXQe NZ\x1E`N^O";
int v5 = 101;
int v7 = 1;
int len;
char flag[40];
printf("welcome to LitCTF2024\nplease inputs you flag:\n");
for ( i = 0; i <= 24; ++i )
{
for(j=32;j<128;j++)
if ( (char)j-i == *((unsigned char*)v4 + i) )
{
flag[i]=j;
}
}
puts(flag);
/*for(i=0;i<40;i++)
{
printf("%c",v4[i]);
}
*/
return 0;
} ezrc4
64 open
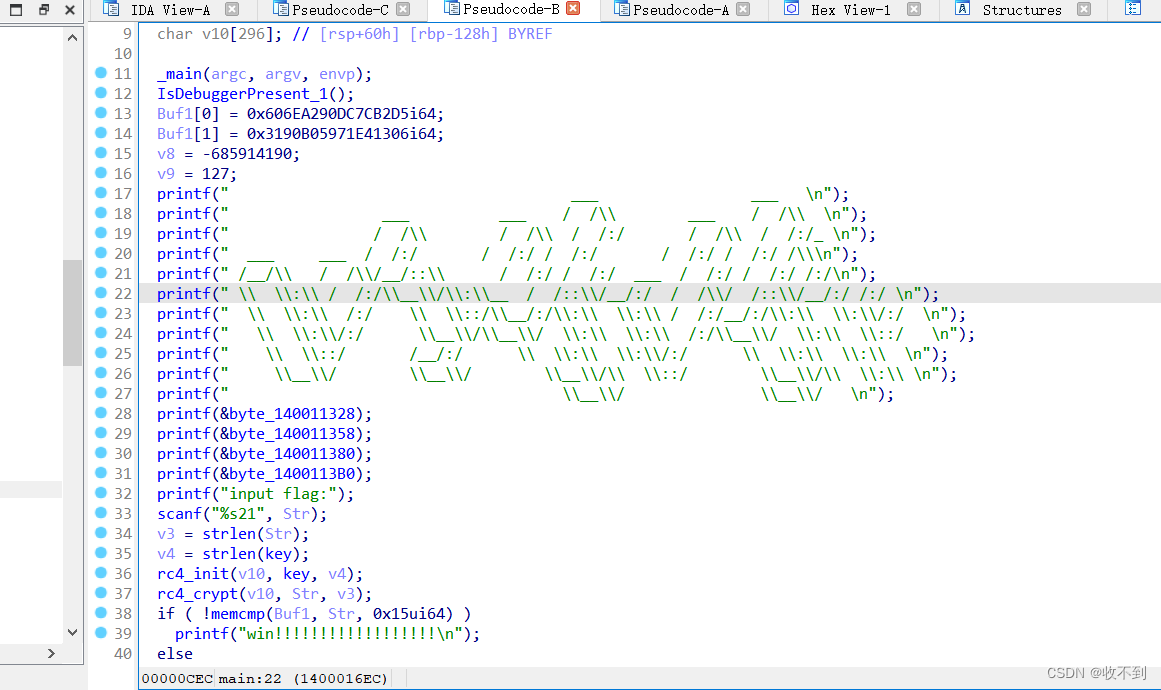
IDA数据存储的问题吧,读数据的时候注意一下,后面是v8v9的数据, 不加的话不完整,反编译的一点小问题,maybe
Buf1[0] = 0x606EA290DC7CB2D5i64;
Buf1[1] = 0x3190B05971E41306i64;v8 = 0xD71DC7B2;
v9 = 0x7F;
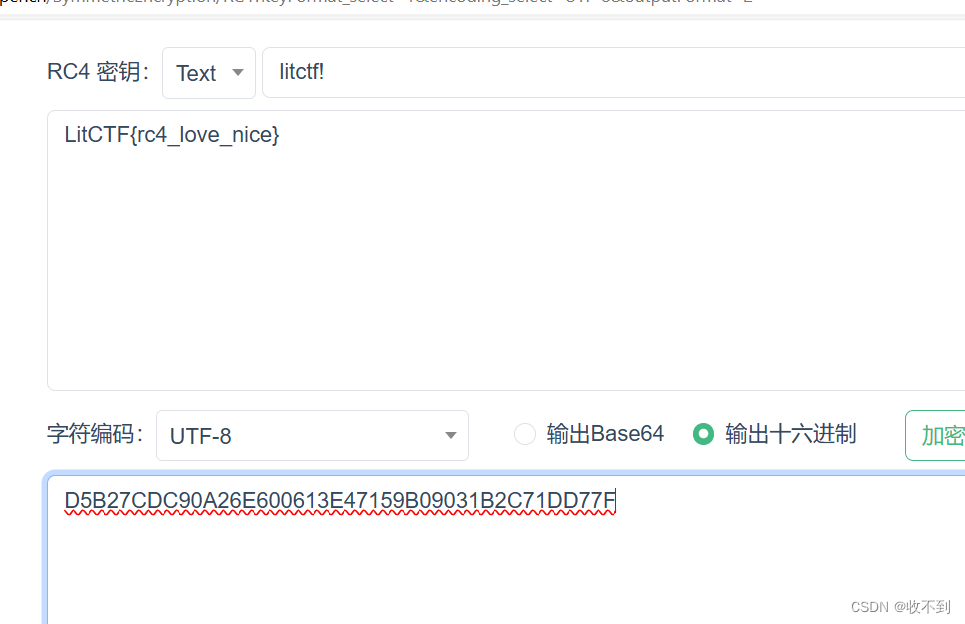
D5B27CDC90A26E600613E47159B09031B2C71DD77F
key:fenkey?

Crtl X 交叉引用
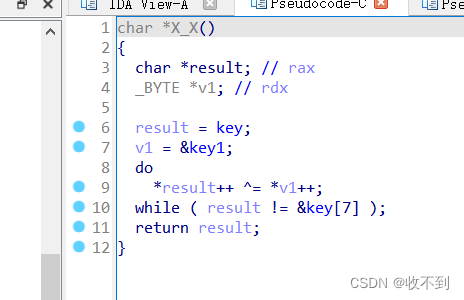
拿到真正的key
#include<stdio.h>
int main()
{
int i,j;
char key[]="fenkey?";
char key1[7]={0x0A, 0x0C, 0x1A, 0x08, 0x11, 0x1F, 0x1E};
for(i=0;i<7;i++)
{
key[i]=key[i]^key1[i];
}
puts(key);
//litctf!
return 0;
} 解密RC4 加密/解密 - 锤子在线工具 (toolhelper.cn)
盯帧珍珠
PS打开逐帧看即可

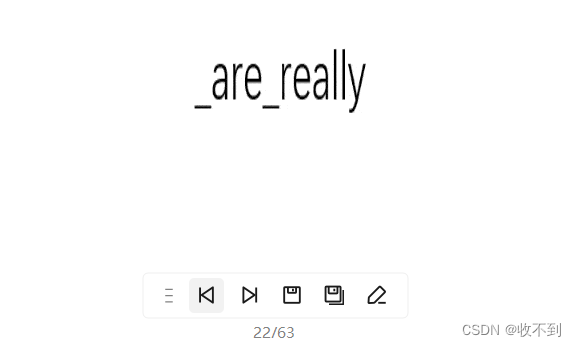

舔到最后应有尽有
我以为她的flag藏在这一堆ex的文字里面。。。
base64隐写
脚本,把a换掉即可
def base64_stego(str):
base64_list = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789"
temp = ''
if str.count('=') == 2:
a = len(bin(base64_list.find(str[-3]) & 0xf).replace('0b', ''))
if a == 3:
temp += "0"
elif a == 2:
temp += "00"
elif a == 1:
temp += "000"
temp += bin(base64_list.find(str[-3]) & 0xf).replace('0b', '')
print(temp)
elif str.count('=') == 1:
a = len(bin(base64_list.find(str[-3]) & 0x3).replace('0b', ''))
if a == 3:
temp += "0"
elif a == 2:
temp += "00"
elif a == 1:
temp += "000"
temp += bin(base64_list.find(str[-3]) & 0x3).replace('0b', '')
print(temp)
return temp
a = ["55y85YmN6YeN5aSN55qE6aOO5pmvLG==",
"5riQ5riQ5qih57OK5LqG57qm5a6aLO==",
"5pif56m65LiL5rWB5rWq55qE5L2gLH==",
"5LuN54S256eY5a+G55qE6Led56a7LA==",
"5rip5bqm5raI5aSx55qE556s6Ze0LH==",
"5peg5rOV6Kem5pG455qE5piO5aSpLF==",
"5rKh5pyJ5byV5Yqb55qE5LiW55WMLG==",
"5rKh5pyJ6ISa5Y2w55qE5YWJ5bm0LD==",
"6L+Y5Zyo562J552A5L2g5Ye6546wLH==",
"5pel5pel5aSc5aSc6Ieq6L2s55qE6KGM5pifLE==",
"5Yiw5aSE6YGu5ruh5Yir5Lq655qE6IOM5b2xLG==",
"6K6p6aOO5ZC55pWj5re35Lmx55qE5ZG85ZC4LG==",
"5b+r5b+r5riF6YaSfn==",
"6Z2Z6Z2Z54Wn5Lqu5Y6f5p2l55qE6Ieq5bexLL==",
"5aSp56m65rSS5ruh5b+954S255qE5YWJ5piOLE==",
"55y85Lit5Y+q6KaB57ua54OC55qE5aSp6ZmFLG==",
"5YaN6aOe6KGMIW==",
"5oiR5YuH5pWi5Zyw5oqs6LW35aS0LM==",
"55yL552A6Iyr6Iyr55qE5a6H5a6ZLH==",
"5aSa5bCR5pyq55+l55qE5pif55CDLJ==",
"5pyJ5rKh5pyJ6YCa5ZCR5pyq5p2l6Lev5Y+jLD==",
"5Lqy54ix55qE5LyZ5Ly0LB==",
"6K6p5oiR5Lus5LiA6LW354K554eDLG==",
"5YuH5rCU5ZKM5L+h5b+1LO==",
"5Zyo6YGl6L+c55qE5aSp6L65LG==",
"6ZO25rKz6L6557yYLH==",
"5pyJ5LiA54mH56We5aWH55qE5b2p6Jm55rW3LC==",
"5ZKM5oiR5LiA6LW35YaS6ZmpLB==",
"6aOe5ZCR5Y+m5LiA5Liq5LiW55WMLC==",
"5Zyo6YGl6L+c55qE5aSp6L65LB==",
"6ZO25rKz6L6557yYLC==",
"5pyJ5LiA54mH56We5aWH55qE5b2p6Jm55rW3LB==",
"5ZKM5oiR5LiA6LW35YaS6ZmpLH==",
"6aOe5ZCR5Y+m5LiA5Liq5LiW55WMLN==",
"c3VwZXIgbWFnaWMgd29ybGR+fg=="]
def cut(obj, sec):
return [obj[i:i + sec] for i in range(0, len(obj), sec)]
flag = ''
print(len(a))
for i in range(len(a)):
flag += base64_stego(a[i])
flagg = cut(flag, 8)
flag = ''
print(flagg)
ff = [1] * 100
for i in range(len(flagg)):
ff[i] = int(flagg[i], 2)
flag += (chr(ff[i]))
print(flag)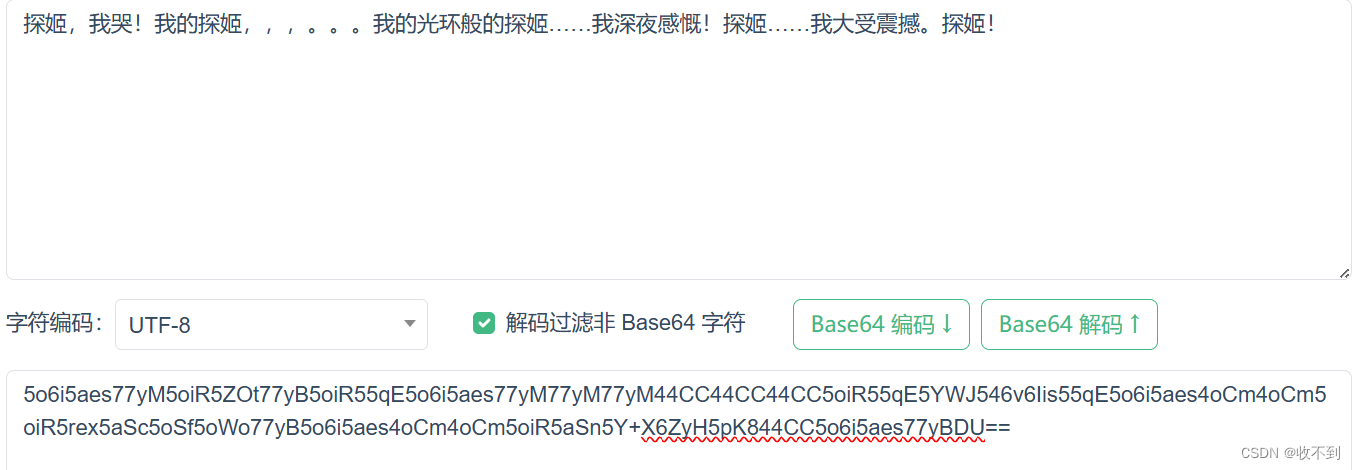
啊这、、、、、、、、
第二个
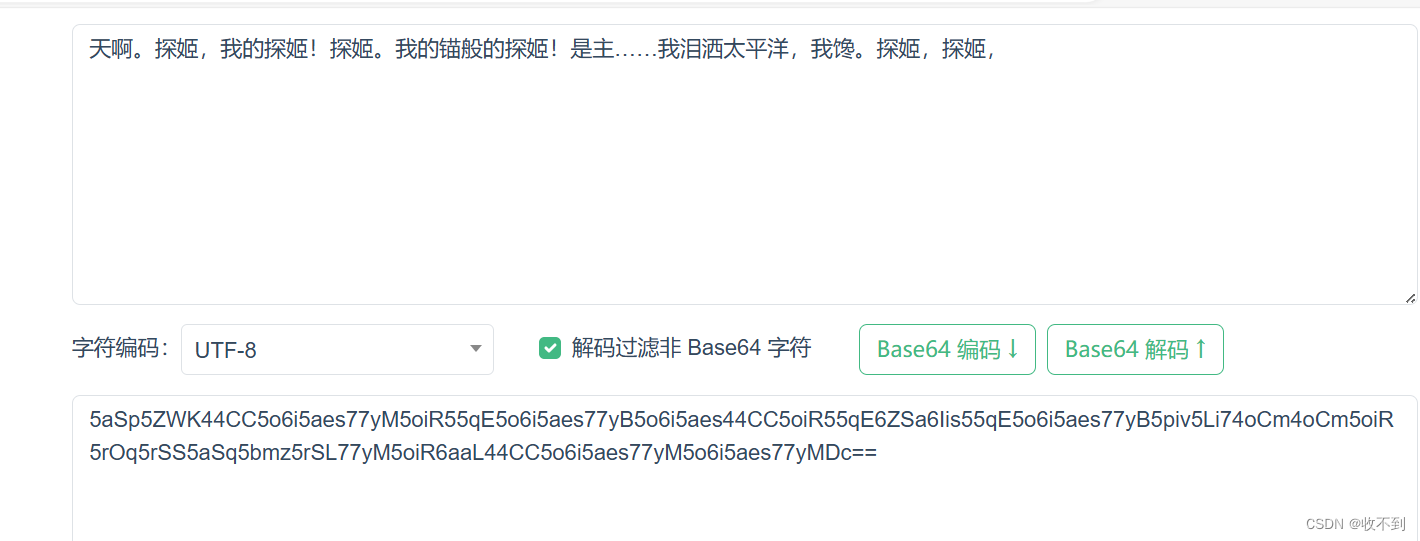
333
 44
44

5555
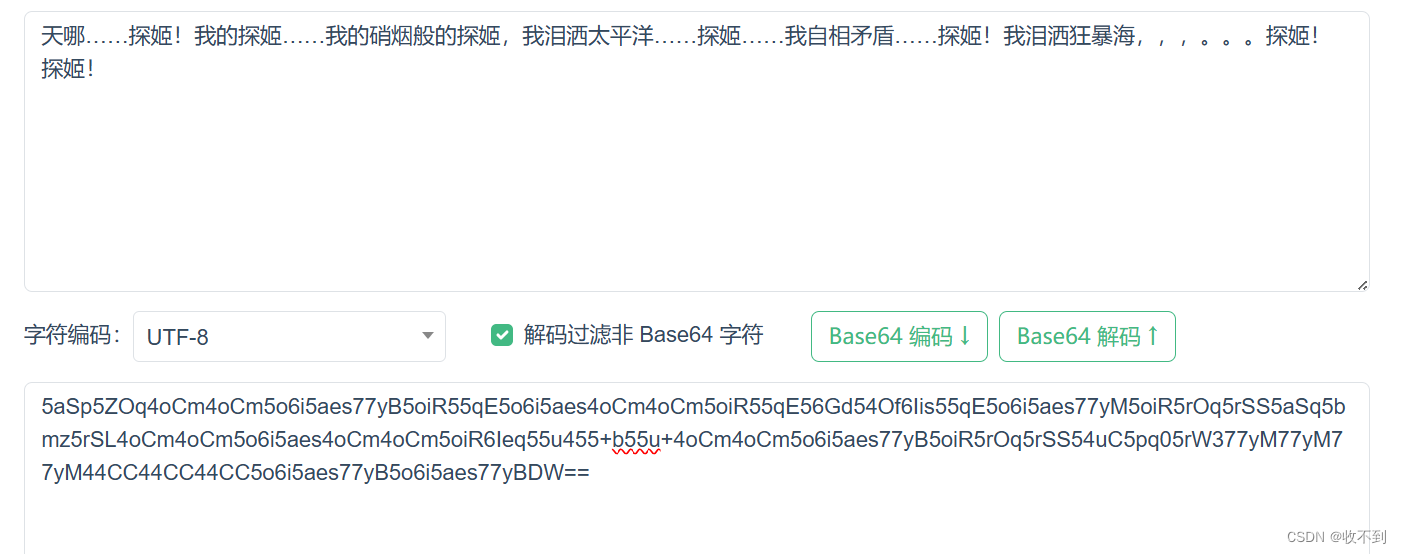
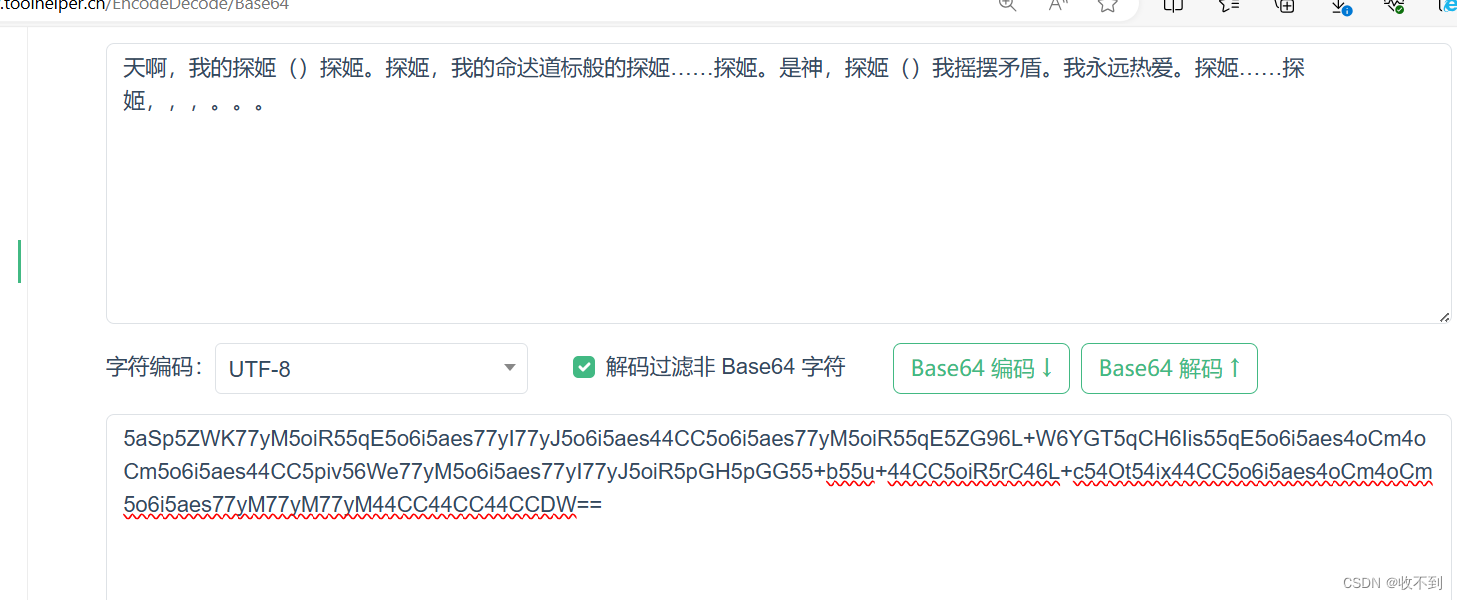
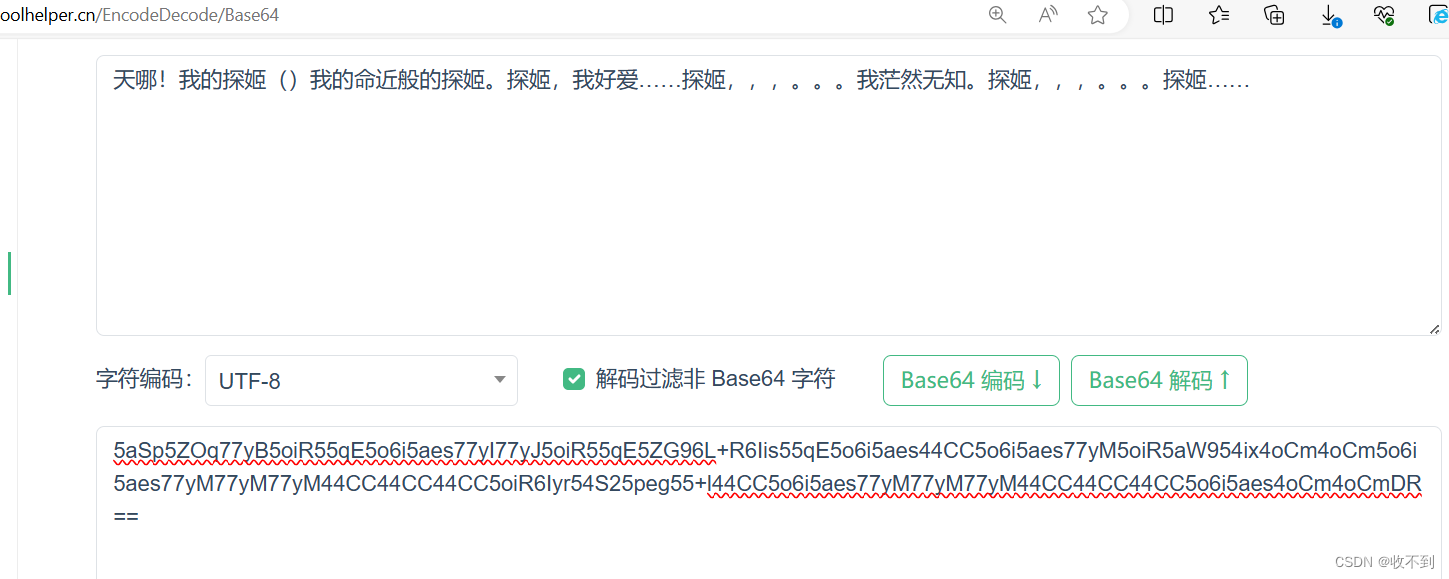
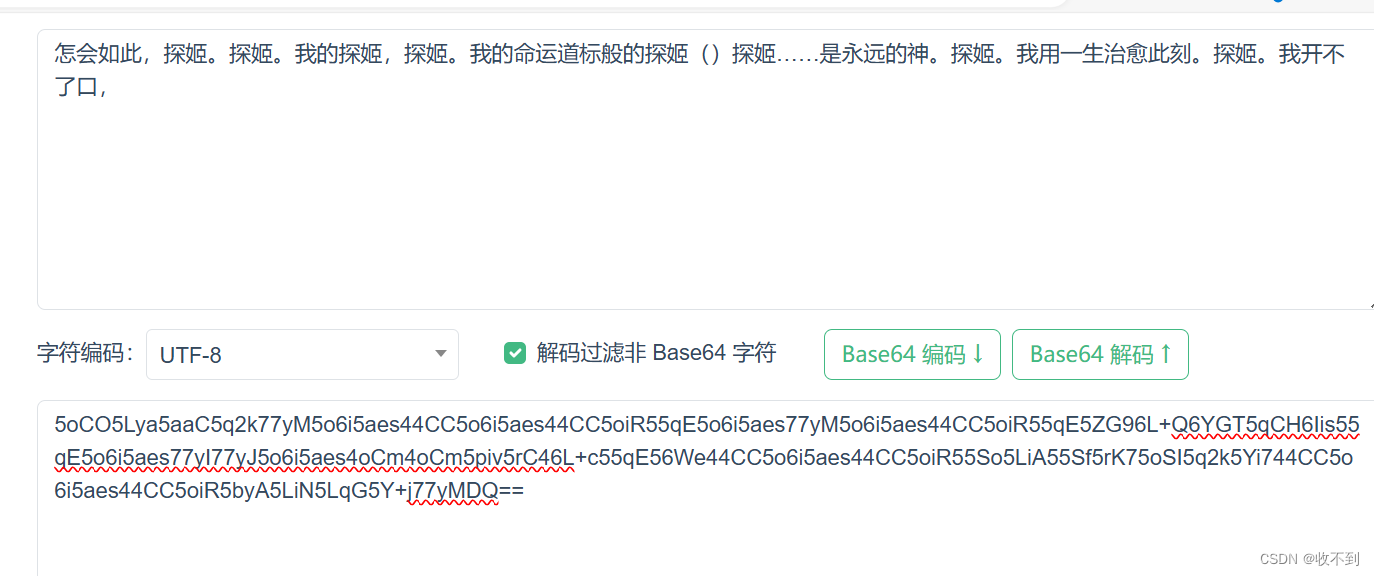




















 3865
3865

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








