
浏览器 ssh隧道
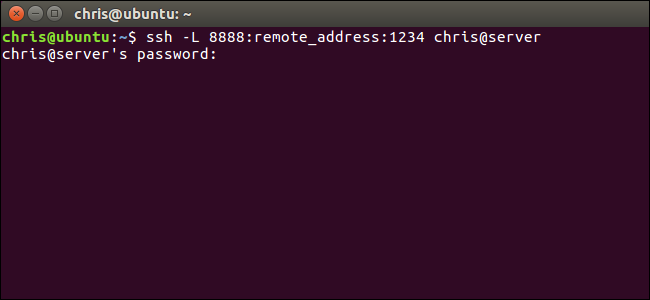
An SSH client connects to a Secure Shell server, which allows you to run terminal commands as if you were sitting in front of another computer. But an SSH client also allows you to “tunnel” a port between your local system and a remote SSH server.
SSH客户端连接到Secure Shell服务器 ,该服务器使您可以像坐在其他计算机前一样运行终端命令。 但是,SSH客户端还允许您“隧道”本地系统和远程SSH服务器之间的端口。
There are three different types of SSH tunneling, and they’re all used for different purposes. Each involves using an SSH server to redirect traffic from one network port to another. The traffic is sent over the encrypted SSH connection, so it can’t be monitored or modified in transit.
共有三种不同类型的SSH隧道,它们都用于不同的目的。 每一种都涉及使用SSH服务器将流量从一个网络端口重定向到另一个网络端口。 流量是通过加密的SSH连接发送的,因此在传输过程中无法对其进行监视或修改。
You can do this with the ssh command included on Linux, macOS, and other UNIX-like operating systems. On Windows, which doesn’t include a built-in ssh command, we recommend the free tool PuTTY to connect to SSH servers. It supports SSH tunneling, too.
您可以使用Linux,macOS和其他类似UNIX的操作系统上包含的ssh命令来执行此操作。 在不包含内置ssh命令的Windows上,我们建议使用免费工具PuTTY连接到SSH服务器。 它也支持SSH隧道。
本地端口转发:使远程资源可在本地系统上访问 (Local Port Forwarding: Make Remote Resources Accessible on Your Local System)
“Local port forwarding” allows you to access local network resources that aren’t exposed to the Internet. For example, let’s say you want to access a database server at your office from your home. For security reasons, that database server is only configured to accept connections from the local office network. But if you have access to an SSH server at the office, and that SSH server allows connections from outside the office network, then you can connect to that SSH server from home and access the database server as if you were in the office. This is often the case, as it’s easier to secure a single SSH server against attacks than to secure a variety of different network resources.
“本地端口转发”使您可以访问未暴露给Internet的本地网络资源。 例如,假设您要在家中访问办公室中的数据库服务器。 出于安全原因,该数据库服务器仅配置为接受来自本地办公室网络的连接。 但是,如果您可以访问办公室中的SSH服务器,并且该SSH服务器允许来自办公室网络外部的连接,则可以在家中连接到该SSH服务器并像访问办公室一样访问数据库服务器。 通常是这样,因为保护单个SSH服务器免受攻击要比保护各种不同的网络资源更容易。
To do this, you establish an SSH connection with the SSH server and tell the client to forward traffic from a specific port from your local PC—for example, port 1234—to the address of the database’s server and its port on the office network. So, when you attempt to access the database server at port 1234 your current PC, “localhost”, that traffic is automatically “tunneled” over the SSH connection and sent to the database server. The SSH server sits in the middle, forwarding traffic back and forth. You can use any command line or graphical tool to access the database server as if it was running on your local PC.
为此,您需要与SSH服务器建立SSH连接,并告诉客户端将流量从本地PC的特定端口(例如端口1234)转发到数据库服务器的地址及其办公室网络上的端口。 因此,当您尝试访问当前PC的端口1234上的数据库服务器“ localhost”时,该流量会通过SSH连接自动“隧道化”并发送到数据库服务器。 SSH服务器位于中间,来回转发流量。 您可以使用任何命令行或图形工具来访问数据库服务器,就像它在本地PC上运行一样。
To use local forwarding, connect to the SSH server normally, but also supply the -L argument. The syntax is:
要使用本地转发,请正常连接到SSH服务器,但还要提供-L参数。 语法为:
ssh -L local_port:remote_address:remote_port username@server.com
For example, let’s say the database server at your office is located at 192.168.1.111 on the office network. You have access to the office’s SSH server at ssh.youroffice.com , and your user account on the SSH server is bob . In that case, your command would look like this:
例如,假设您办公室的数据库服务器位于办公室网络上的192.168.1.111。 您可以通过ssh.youroffice.com访问办公室的SSH服务器,并且您在SSH服务器上的用户帐户是bob 。 在这种情况下,您的命令将如下所示:
ssh -L 8888:192.168.1.111:1234 bob@ssh.youroffice.com
After running that command, you’d be able to access the database server at port 8888 at localhost. So, if the database server offered web access, you could plug http://localhost:8888 into your web browser to access it. If you had a command line tool that needs the network address of a database, you’d point it at localhost:8888. All traffic sent to port 8888 on your PC will be tunneled to 192.168.1.111:1234 on your office network.
运行该命令后,您将能够在本地主机的8888端口访问数据库服务器。 因此,如果数据库服务器提供了Web访问,则可以将http:// localhost:8888插入Web浏览器以对其进行访问。 如果您有需要数据库网络地址的命令行工具,则将其指向localhost:8888。 发送到PC上端口8888的所有流量都将通过隧道传输到办公室网络上的192.168.1.111:1234。
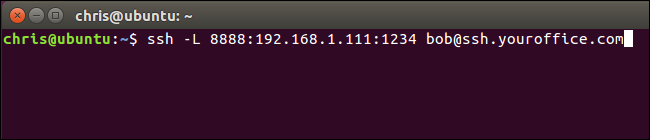
It’s a little more confusing if you want to connect to a server application running on the same system as the SSH server itself. For example, let’s say you have an SSH server running at port 22 on your office computer, but you also have a database server running at port 1234 on the same system at the same address. You want to access the database server from home, but the system is only accepting SSH connections on port 22 and its firewall doesn’t allow any other external connections.
如果您想连接到与SSH服务器本身在同一系统上运行的服务器应用程序,那会更加令人困惑。 例如,假设您在办公室计算机的端口22上运行了SSH服务器,但是在同一地址的同一系统上的数据库端口1234上也运行了数据库服务器。 您想从家里访问数据库服务器,但是系统仅在端口22上接受SSH连接,并且其防火墙不允许任何其他外部连接。
In this case, you could run a command like the following one:
在这种情况下,您可以运行以下命令:
ssh -L 8888:localhost:1234 bob@ssh.youroffice.com
When you attempt to access the database server at port 8888 on your current PC, the traffic will be sent over the SSH connection. When it arrives on the system running the SSH server, the SSH server will send it to port 1234 on “localhost”, which is the same PC running the SSH server itself. So the “localhost” in the command above means “localhost” from the perspective of the remote server.
当您尝试访问当前PC上端口8888上的数据库服务器时,流量将通过SSH连接发送。 当它到达运行SSH服务器的系统时,SSH服务器会将其发送到“ localhost”上的端口1234,该端口与运行SSH服务器本身的PC相同。 因此,从远程服务器的角度来看,以上命令中的“ localhost”表示“ localhost”。
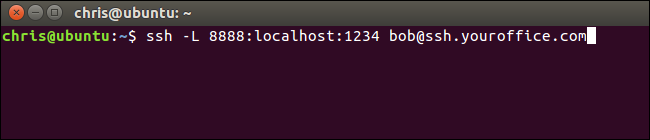
To do this in the PuTTY application on Windows, select Connection > SSH > Tunnels. Select the “Local” option. For “Source Port”, enter the local port. For “Destination”, enter the destination address and port in the form remote_address:remote_port.
要在Windows的PuTTY应用程序中执行此操作,请选择“连接”>“ SSH”>“隧道”。 选择“本地”选项。 对于“源端口”,输入本地端口。 对于“目标”,以remote_address:remote_port的形式输入目标地址和端口。
For example, if you wanted to set up the same SSH tunnel as above, you’d enter 8888 as the source port and localhost:1234 as the destination. Click “Add” afterwards and then click “Open” to open the SSH connection. You will also need to enter the address and port of the SSH server itself on the main “Session” screen before connecting, of course.
例如,如果您要设置与上述相同的SSH隧道,则将输入8888作为源端口,并输入localhost:1234作为目标端口。 然后单击“添加”,然后单击“打开”以打开SSH连接。 当然,在连接之前,您还需要在“会话”主屏幕上输入SSH服务器本身的地址和端口。
远程端口转发:使本地资源在远程系统上可访问 (Remote Port Forwarding: Make Local Resources Accessible on a Remote System)
“Remote port forwarding” is the opposite of local forwarding, and isn’t used as frequently. It allows you to make a resource on your local PC available on the SSH server. For example, let’s say you’re running a web server on the local PC you’re sitting in front of. But your PC is behind a firewall that doesn’t allow incoming traffic to the server software.
“远程端口转发”与本地转发相反,并且不经常使用。 它允许您使本地PC上的资源在SSH服务器上可用。 例如,假设您正在前面的本地PC上运行Web服务器。 但是您的PC位于防火墙之后,该防火墙不允许进入服务器软件的流量。
Assuming you can access a remote SSH server, you can connect to that SSH server and use remote port forwarding. Your SSH client will tell the server to forward a specific port—say, port 1234—on the SSH server to a specific address and port on your current PC or local network. When someone accesses the port 1234 on the SSH server, that traffic will automatically be “tunneled” over the SSH connection. Anyone with access to the SSH server will be able to access the web server running on your PC. This is effectively a way to tunnel through firewalls.
假设您可以访问远程SSH服务器,则可以连接到该SSH服务器并使用远程端口转发。 您的SSH客户端将告诉服务器将SSH服务器上的特定端口(例如,端口1234)转发到当前PC或本地网络上的特定地址和端口。 当某人访问SSH服务器上的端口1234时,该流量将通过SSH连接自动“隧道化”。 有权访问SSH服务器的任何人都可以访问您PC上运行的Web服务器。 这实际上是穿越防火墙的一种方式。
To use remote forwarding, use the ssh command with the -R argument. The syntax is largely the same as with local forwarding:
要使用远程转发,请将ssh命令与-R参数一起使用。 语法与本地转发的语法基本相同:
ssh -R remote_port:local_address:local_port username@server.com
Let’s say you want to make a server application listening at port 1234 on your local PC available at port 8888 on the remote SSH server. The SSH server’s address is ssh.youroffice.com and your username on the SSH server is bob. You’d run the following command:
假设您要使一个服务器应用程序侦听本地PC上的端口1234,该应用程序在远程SSH服务器上的端口8888上可用。 SSH服务器的地址是ssh.youroffice.com而您在SSH服务器上的用户名是bob 。 您将运行以下命令:
ssh -R 8888:localhost:1234 bob@ssh.youroffice.com
Someone could then connect to the SSH server at port 8888 and that connection would be tunneled to the server application running at port 1234 on the local PC you established the connection from.
然后,某人可以通过端口8888连接到SSH服务器,并且该连接将通过隧道建立到从其建立连接的本地PC上的端口1234运行的服务器应用程序。
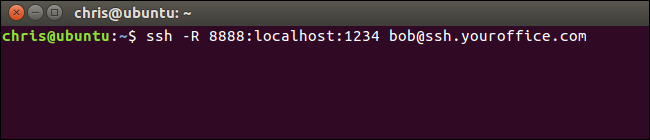
To do this in PuTTY on Windows, select Connection > SSH > Tunnels. Select the “Remote” option. For “Source Port”, enter the remote port. For “Destination”, enter the destination address and port in the form local_address:local_port.
要在Windows的PuTTY中执行此操作,请选择“连接”>“ SSH”>“隧道”。 选择“远程”选项。 对于“源端口”,输入远程端口。 对于“目标”,以local_address:local_port的形式输入目标地址和端口。
For example, if you wanted to set up the example above, you’d enter 8888 as the source port and localhost:1234 as the destination. Click “Add” afterwards and then click “Open” to open the SSH connection. You will also need to enter the address and port of the SSH server itself on the main “Session” screen before connecting, of course.
例如,如果要设置上面的示例,则输入8888作为源端口,输入localhost:1234作为目标端口。 然后单击“添加”,然后单击“打开”以打开SSH连接。 当然,在连接之前,您还需要在“会话”主屏幕上输入SSH服务器本身的地址和端口。
People could then connect to port 8888 on the SSH server and their traffic would be tunneled to port 1234 on your local system.
人们随后可以连接到SSH服务器上的端口8888,他们的流量将通过隧道传输到本地系统上的端口1234。
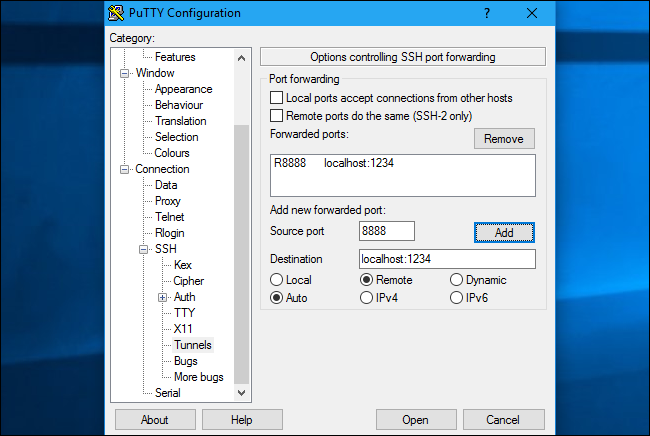
By default, the remote SSH server will only listen to connections from the same host. In other words, only people on the same system as the SSH server itself will be able to connect. This is for security reasons. You’ll need to enable the “GatewayPorts” option in sshd_config on the remote SSH server if you want to override this behavior.
默认情况下,远程SSH服务器将仅侦听来自同一主机的连接。 换句话说,只有与SSH服务器本身位于同一系统上的人才能连接。 这是出于安全原因。 如果要覆盖此行为,则需要在远程SSH服务器上的sshd_config中启用“ GatewayPorts”选项。
动态端口转发:使用SSH服务器作为代理 (Dynamic Port Forwarding: Use Your SSH Server as a Proxy)
There’s also “dynamic port forwarding”, which works similarly to a proxy or VPN. The SSH client will create a SOCKS proxy you can configure applications to use. All the traffic sent through the proxy would be sent through the SSH server. This is similar to local forwarding—it takes local traffic sent to a specific port on your PC and sends it over the SSH connection to a remote location.
还有“动态端口转发”,其功能类似于代理或VPN。 SSH客户端将创建一个SOCKS代理,您可以配置要使用的应用程序。 通过代理发送的所有流量都将通过SSH服务器发送。 这类似于本地转发-将本地流量发送到PC上的特定端口,并通过SSH连接将其发送到远程位置。
For example, let’s say you’re using a public Wi-Fi network. You want to browse securely without being snooped on. If you have access to an SSH server at home, you could connect to it and use dynamic port forwarding. The SSH client will create a SOCKS proxy on your PC. All traffic sent to that proxy will be sent over the SSH server connection. No one monitoring the public Wi-Fi network will be able to monitor your browsing or censor the websites you can access. From the perspective of any websites you visit, it will be as if you were sitting in front of your PC at home. This also means you could use this trick to access US-only websites while outside of the USA—assuming you have access to an SSH server in the USA, of course.
例如,假设您正在使用公共Wi-Fi网络。 您想安全浏览而不被窥探 。 如果您在家中可以访问SSH服务器,则可以连接到该服务器并使用动态端口转发。 SSH客户端将在您的PC上创建一个SOCKS代理。 发送到该代理的所有流量都将通过SSH服务器连接发送。 没有人监视公共Wi-Fi网络将能够监视您的浏览或审查您可以访问的网站。 从您访问的任何网站的角度来看,就好像您坐在家里的PC前面一样。 这也意味着您可以使用此技巧在美国境外访问仅限美国的网站-当然,假设您可以访问美国的SSH服务器。
As an another example, you may want to access a media server application you have on your home network. For security reasons, you may only have an SSH server exposed to the Internet. You don’t allow incoming connections from the Internet to your media server application. You could set up dynamic port forwarding, configure a web browser to use the SOCKS proxy, and then access servers running on your home network through the web browser as if you were sitting in front of your SSH system at home. For example, if your media server is located at port 192.168.1.123 on your home network, you could plug the address 192.168.1.123 into any application using the SOCKS proxy and you’d access the media server as if you were on your home network.
作为另一个示例,您可能要访问家庭网络上的媒体服务器应用程序。 出于安全原因,您可能只将SSH服务器公开给Internet。 您不允许从Internet到媒体服务器应用程序的传入连接。 您可以设置动态端口转发,将Web浏览器配置为使用SOCKS代理,然后通过Web浏览器访问在家庭网络上运行的服务器,就像坐在家里的SSH系统之前一样。 例如,如果您的媒体服务器位于家庭网络上的端口192.168.1.123上,则可以使用SOCKS代理将地址192.168.1.123插入任何应用程序中,就像访问家庭网络一样访问媒体服务器。
To use dynamic forwarding, run the ssh command with the -D argument, like so:
要使用动态转发,请使用-D参数运行ssh命令,如下所示:
ssh -D local_port username@server.com
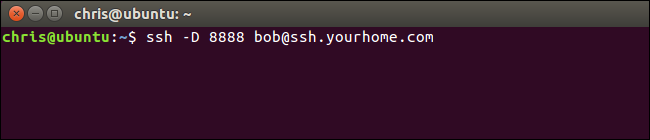
For example, let’s say you have access to an SSH server at ssh.yourhome.com and your username on the SSH server is bob . You want to use dynamic forwarding to open a SOCKS proxy at port 8888 on the current PC. You’d run the following command:
例如,假设您可以访问ssh.yourhome.com上的SSH服务器,并且您在SSH服务器上的用户名是bob 。 您要使用动态转发在当前PC的端口8888上打开SOCKS代理。 您将运行以下命令:
ssh -D 8888 bob@ssh.yourhome.com
You could then configure a web browser or another application to use your local IP address (127.0.01) and port 8888. All traffic from that application would be redirected through the tunnel.
然后,您可以配置Web浏览器或其他应用程序以使用本地IP地址(127.0.01)和端口8888。来自该应用程序的所有流量都将通过隧道重定向。
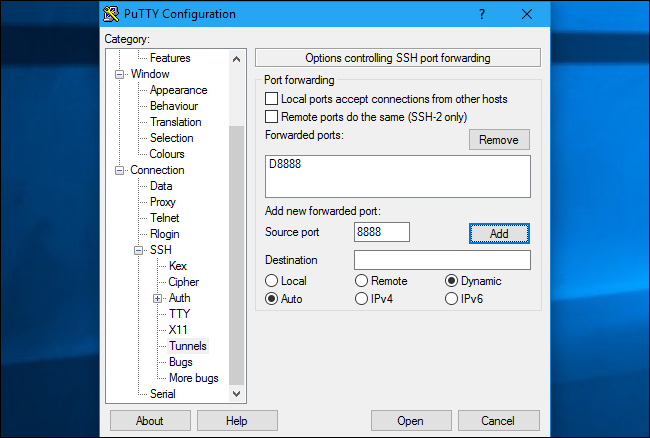
To do this in PuTTY on Windows, select Connection > SSH > Tunnels. Select the “Dynamic” option. For “Source Port”, enter the local port.
要在Windows的PuTTY中执行此操作,请选择“连接”>“ SSH”>“隧道”。 选择“动态”选项。 对于“源端口”,输入本地端口。
For example, if you wanted to create a SOCKS proxy on port 8888, you’d enter 8888 as the source port. Click “Add” afterwards and then click “Open” to open the SSH connection. You will also need to enter the address and port of the SSH server itself on the main “Session” screen before connecting, of course.
例如,如果要在端口8888上创建SOCKS代理,则需要输入8888作为源端口。 然后单击“添加”,然后单击“打开”以打开SSH连接。 当然,在连接之前,您还需要在“会话”主屏幕上输入SSH服务器本身的地址和端口。
You could then configure an application to access the SOCKS proxy on your local PC (that is, IP address 127.0.0.1, which points to your local PC) and specify the correct port.
然后,您可以配置一个应用程序以访问本地PC上的SOCKS代理(即IP地址127.0.0.1,它指向本地PC)并指定正确的端口。
For example, you can configure Firefox to use the SOCKS proxy. This is particularly useful because Firefox can have its own proxy settings and doesn’t have to use system-wide proxy settings. Firefox will send its traffic through the SSH tunnel, while other applications will use your Internet connection normally.
例如,您可以将Firefox配置为使用SOCKS代理 。 这特别有用,因为Firefox可以具有自己的代理设置,而不必使用系统范围的代理设置。 Firefox将通过SSH隧道发送其流量,而其他应用程序将正常使用您的Internet连接。
When doing this in Firefox, select “Manual proxy configuration”, enter “127.0.0.1” into the SOCKS host box, and enter the dynamic port into the “Port” box. Leave the HTTP Proxy, SSL Proxy, and FTP Proxy boxes empty.
在Firefox中执行此操作时,选择“手动代理配置”,在SOCKS主机框中输入“ 127.0.0.1”,然后在“端口”框中输入动态端口。 将“ HTTP代理”,“ SSL代理”和“ FTP代理”框保留为空。
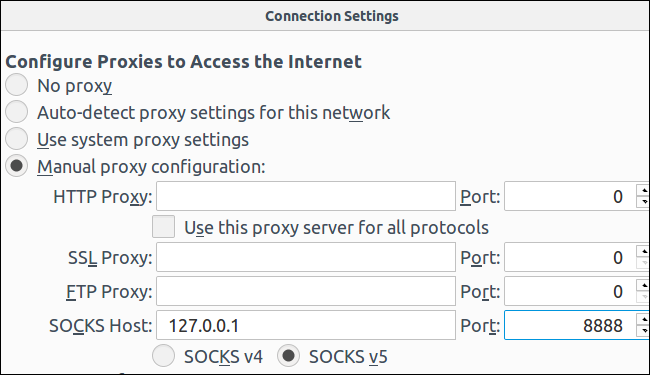
The tunnel will remain active and open for as long as you have the SSH session connection open. When you end your SSH session and disconnect from a server, the tunnel will also be closed. Just reconnect with the appropriate command (or the appropriate options in PuTTY) to reopen the tunnel.
只要您打开SSH会话连接,隧道就将保持活动状态并保持打开状态。 当您结束SSH会话并与服务器断开连接时,隧道也将关闭。 只需使用适当的命令(或PuTTY中的适当选项)重新连接即可重新打开隧道。
翻译自: https://www.howtogeek.com/168145/how-to-use-ssh-tunneling/
浏览器 ssh隧道





















 1536
1536











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








