linux打开端口
Before we learn about opening a port on Linux, let’s understand what network ports are. A port is a communication endpoint. Within an operating system, a port allows the data packets specific processes or network services.
在学习在Linux上打开端口之前,让我们了解什么是网络端口。 端口是通信端点。 在操作系统内,端口允许数据包特定的进程或网络服务。
Typically, ports identify a specific network service assigned to them. This can be changed by manually configuring the service to use a different port, but in general, the defaults can be used.
通常,端口标识分配给它们的特定网络服务。 可以通过手动将服务配置为使用其他端口来更改此设置,但是通常可以使用默认值。
The first 1024 ports (Ports 0-1023) are referred to as well-known port numbers and are reserved for the most commonly used services include SSH (port 22), HTTP and HTTPS (port 80 and 443), etc. Port numbers above 1024 are referred to as ephemeral ports.
前1024个端口(端口0-1023 )称为众所周知的端口号,并保留用于最常用的服务,包括SSH(端口22),HTTP和HTTPS(端口80和443)等。上面的端口号1024被称为临时端口 。
Among ephemeral ports, Port numbers 1024-49151 are called the Registered/User Ports. The rest of the ports, 49152-65535 are called as Dynamic/Private Ports.
在临时端口中,端口号1024-49151称为已注册/用户端口。 其余端口49152-65535被称为动态/专用端口。
In this tutorial, we will show how we can open an ephemeral port on Linux, since the most common services use the well-known ports.
在本教程中,我们将展示如何在Linux上打开临时端口,因为最常用的服务使用众所周知的端口。
列出所有打开的端口 (List all open ports)
Before opening a port on Linux, let us first check the list of all open ports, and choose an ephemeral port to open from that list.
在Linux上打开端口之前,让我们首先检查所有打开的端口的列表,然后从该列表中选择一个临时端口打开。
We can use the netstat command to list all open ports, including those of TCP, UDP, which are the most common protocols for packet transmission in the network layer.
我们可以使用netstat命令列出所有打开的端口,包括TCP , UDP的端口 ,它们是网络层中用于数据包传输的最常见协议。
NOTE: If your distribution doesn’t have netstat, it is not a problem. You can use the ss command to display open ports via listening sockets.
注意 :如果您的发行版没有netstat ,那不是问题。 您可以使用ss命令通过侦听套接字显示打开的端口。
netstat -lntu
This will print all listening sockets (-l) along with the port number (-n), with TCP ports (-t) and UDP ports (-u) also listed in the output.
这将打印所有侦听套接字( -l )以及端口号 ( -n ),并且输出中还将列出TCP端口( -t )和UDP端口( -u )。

Just to ensure that we are getting consistent outputs, let’s verify this using the ss command to list listening sockets with an open port.
为了确保我们获得一致的输出,让我们使用ss命令来验证这一点,以列出具有开放端口的侦听套接字。
ss -lntu
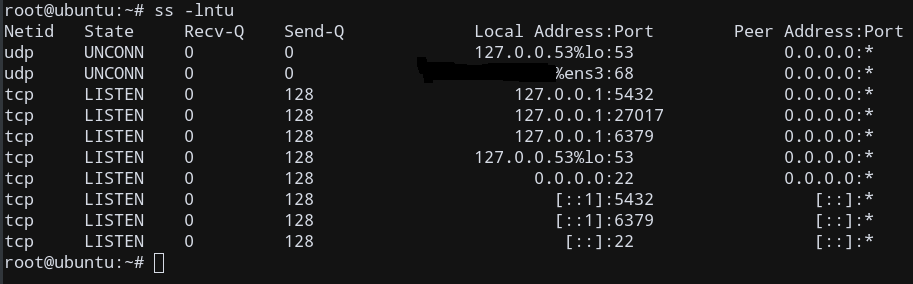
This gives more or less the same open ports as netstat, so we are good to go!
这提供了几乎与netstat相同的开放端口,所以我们很高兴!
在Linux上打开端口以允许TCP连接 (Opening a port on Linux to Allow TCP Connections)
Let’s open a closed port and make it listen to TCP Connections, for the sake of this example.
就本例而言,我们打开一个封闭的端口并使其侦听TCP连接。
Since port 4000 is not being used in my system, I choose to open port 4000. If that port is not open in your system, feel free to choose another closed port. Just make sure that it’s greater than 1023!
由于系统中未使用端口4000 ,因此我选择打开端口4000 。 如果您的系统中该端口未打开,请随时选择另一个关闭的端口。 只要确保它大于1023即可 !
Again, just to make sure, let’s ensure that port 4000 is not used, using the netstat or the ss command.
再次,只是要确保,请使用netstat或ss命令确保未使用端口4000。
netstat -na | grep :4000
ss -na | grep :4000
The output must remain blank, thus verifying that it is not currently used, so that we can add the port rules manually to the system iptables firewall.
输出必须保持空白,从而验证它当前未被使用,以便我们可以将端口规则手动添加到系统iptables防火墙 。
对于Ubuntu用户和基于ufw防火墙的系统 (For Ubuntu Users and ufw firewall based Systems)
Ubuntu has a firewall called ufw, which takes care of these rules for ports and connections, instead of the old iptables firewall. If you are a Ubuntu user, you can directly open the port using ufw
Ubuntu有一个名为ufw的防火墙,它负责处理端口和连接的这些规则,而不是旧的iptables防火墙。 如果您是Ubuntu用户,则可以使用ufw直接打开ufw
sudo ufw allow 4000
You can skip the next few steps, and directly test your newly opened port!
您可以跳过接下来的几个步骤,直接测试您新打开的端口!
对于CentOS和基于Firewalld的系统 (For CentOS and firewalld based Systems)
For these types of systems, if you have firewalld as your primary firewall, it is recommended that you use the firewall-cmd to update your firewall rules, instead of the old iptables firewall.
对于这些类型的系统,如果已将firewalld为主防火墙,则建议您使用firewall-cmd来更新防火墙规则,而不是旧的iptables防火墙。
firewall-cmd --add-port=4000/tcp
NOTE: This will reset the firewalld rules to default on a reboot, so if you want to modify this setting permanently, add the --permanent flag to the command.
注:这将在重新引导时将firewalld规则重置为默认值,因此,如果您要永久修改此设置,请在命令中添加--permanent标志。
firewall-cmd --add-port=4000/tcp --permanent
You can skip the next few steps, and directly test your newly opened port!
您可以跳过接下来的几个步骤,直接测试您新打开的端口!
对于其他Linux发行版 (For Other Linux Distributions)
So let’s add this new port to our system iptables rules, using the iptables command.
因此,让我们使用iptables命令将此新端口添加到系统iptables规则中。
If this command is not yet installed, get it using your package manager.
如果尚未安装此命令,请使用软件包管理器获取它。
iptables -A INPUT -p tcp --dport 4000 -j ACCEPT
This sets the firewall to append (-A) the new rule to accept input packets via protocol (-p) TCP where the destination port (--dport) is 4000, and specifies the target jump (-j) rule as ACCEPT.
这将防火墙设置为附加新规则( -A ),以通过协议( -p ) TCP接受输入数据包,其中目标端口 ( --dport )为4000 ,并将目标跳转 ( -j )规则指定为ACCEPT 。
To update the firewall rules, restart the iptables service.
要更新防火墙规则,请重新启动iptables服务。
sudo service iptables restart
OR using systemctl if you have it.
或使用systemctl如果有)。
sudo systemctl restart iptables
测试新打开的端口的TCP连接 (Test the newly opened port for TCP Connections)
Now that we have successfully opened a new TCP port (Port 4000 in my case), let’s test it out.
现在我们已经成功打开了一个新的TCP端口(在我的情况下为Port 4000),让我们对其进行测试。
First, we will start netcat (nc) and listen on port 4000, while sending the output of ls to any connected client. So after a client has opened a TCP connection on port 4000, they will receive the output of ls.
首先,我们将启动netcat( nc )并侦听端口4000,同时将ls的输出发送到任何已连接的客户端。 因此,客户端在端口4000上打开TCP连接后,他们将收到ls的输出。
ls | nc -l -p 4000
This makes netcat listen on port 4000. Leave this session alone for now.
这使得netcat在端口4000上进行侦听。暂时不进行此会话。
Open another terminal session on the same machine.
在同一台计算机上打开另一个终端会话。
Since I’ve opened a TCP port, I’ll use telnet to check for TCP Connectivity. If the command doesn’t exists, again, install it using your package manager.
由于打开了TCP端口,因此我将使用telnet来检查TCP连接。 如果该命令不存在,请再次使用程序包管理器进行安装。
Format for telnet:
telnet的格式:
telnet [hostname/IP address] [port number]
So input your server IP and the port number, which is 4000 in my case, and run this command.
因此,输入您的服务器IP和端口号(在我的情况下为4000) ,然后运行此命令。
telnet localhost 4000
This tries to open a TCP connection on localhost on port 4000.
这会尝试在端口4000的localhost上打开TCP连接。
You’ll get an output similar to this, indicating that a connection has been established with the listening program (nc).
您将获得类似于此的输出,表明已与侦听程序( nc )建立了连接。
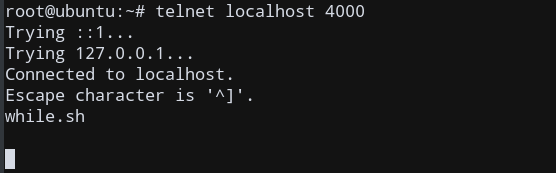
As you can see, the output of ls (while.sh in my case) has also been sent to the client, indicating a successful TCP Connection!
如您所见, ls (在我的情况下为while.sh )的输出也已发送到客户端,表明TCP连接成功!
To show you that the port is indeed open, we can use nmap to check this.
为了告诉您端口确实是开放的,我们可以使用nmap进行检查。
nmap localhost -p 4000

Indeed, our port has been opened! We have successfully opened a new port on our Linux system!
确实,我们的港口已经开放! 我们已经在Linux系统上成功打开了一个新端口!
NOTE: nmap only lists opened ports which have a currently listening application. If you don’t use any listening application such as netcat, this will display the port 4000 as closed, since there isn’t any application listening on that port currently. Similarly, telnet won’t work either, since it also needs a listening application to bind to. This is the reason why nc is such a useful tool. This simulates such environments in a simple command.
注意 : nmap仅列出具有当前监听应用程序的已打开端口。 如果您不使用任何监听应用程序(例如netcat),则会将端口4000显示为已关闭,因为当前没有任何应用程序在该端口上进行监听。 同样,telnet也不起作用,因为它还需要绑定监听应用程序。 这就是nc如此有用的工具的原因。 这在一个简单的命令中模拟了这种环境。
But this is only temporary, as the changes will be reset every time we reboot the system.
但这只是暂时的,因为更改将在每次重新引导系统时重置。
每次重启后都需要更新规则 (Need to update rules after every reboot)
The approach presented in this article will only temporarily update the firewall rules until the system shuts down/reboots. So similar steps must be repeated to open the same port again after a restart.
本文介绍的方法只会临时更新防火墙规则,直到系统关闭/重新启动为止。 因此,必须重复类似的步骤才能在重新启动后再次打开同一端口。
对于ufw防火墙 (For ufw Firewall)
The ufw rules are not reset on reboot, so if you’re a Ubuntu user, you need not worry about this part!
ufw规则不会在重启时重置,因此,如果您是Ubuntu用户,则不必担心这部分!
This is because it is integrated into the boot process and the kernel saves the firewall rules using ufw, via appropriate config files.
这是因为它已集成到引导过程中,并且内核使用ufw通过适当的配置文件保存了防火墙规则。
对于防火墙 (For firewalld)
As mentioned earlier, firewalld also suffers from the same problem, but this can be avoided by appending a --permananent flag to the initial command, when opening a port or setting any other rule.
如前所述, firewalld也存在相同的问题,但是在打开端口或设置任何其他规则时,可以通过在初始命令后附加--permananent标志来避免此问题。
For example, you can open the TCP Port 4000 permanently using the below command:
例如,您可以使用以下命令永久打开TCP端口4000 :
firewall-cmd --zone=public --add-port=400/tcp --permanent
对于iptables (For iptables)
For the iptables firewall, although this inconvenience cannot be avoided, we could minimize the hassle.
对于iptables防火墙,尽管无法避免这种不便,但我们可以将麻烦降到最低。
We can save the iptables rules to a config file, such as /etc/iptables.conf.
我们可以将iptables规则保存到配置文件中,例如/etc/iptables.conf 。
sudo iptables-save | sudo tee -a /etc/iptables.conf
We can then retrieve it from the config file after we reboot, using the below command:
重新启动后,我们可以使用以下命令从配置文件中检索它:
sudo iptables-restore < /etc/iptables.conf
Now, the iptables rules are now updated, and our ports are opened again!
现在, iptables规则现在已更新,我们的端口再次打开!
结论 (Conclusion)
In this tutorial, we showed you how you could open a new port on Linux and set it up for incoming connections.
在本教程中,我们向您展示了如何在Linux上打开新端口并将其设置为传入连接。
翻译自: https://www.journaldev.com/34113/opening-a-port-on-linux
linux打开端口







 本文详细介绍了在Linux系统中打开端口的过程,包括理解网络端口的概念,使用netstat和ss命令查看已打开的端口,以及如何通过iptables、ufw和firewalld防火墙规则在Ubuntu、CentOS和其他Linux发行版上打开新的端口。
本文详细介绍了在Linux系统中打开端口的过程,包括理解网络端口的概念,使用netstat和ss命令查看已打开的端口,以及如何通过iptables、ufw和firewalld防火墙规则在Ubuntu、CentOS和其他Linux发行版上打开新的端口。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








