Wireshark is a popular network packet capture and analysis tool. It is previously named as Ethereal. Wireshark captures packets from a different type of interfaces and prints them as a floating list to the screen. It also provides detailed information about a specific packet. Wireshark can also read already captured packets in different formats like cap , pcap etc.
Wireshark是一种流行的网络数据包捕获和分析工具。 它以前被称为Ethereal。 Wireshark捕获来自不同类型接口的数据包,并将它们作为浮动列表打印到屏幕。 它还提供有关特定数据包的详细信息。 Wireshark还可以读取不同格式的已捕获数据包,例如cap , pcap等。
下载并安装 (Download and Install)
Wireshark is supported by a lot of platforms. Let’s install
许多平台都支持Wireshark。 让我们安装
视窗:(Windows:)
For Windows operating system we need to download the wireshark installation file from the official web site. The latest version of Wireshark can be downloaded from the following link.
对于Windows操作系统,我们需要从官方网站下载wireshark安装文件。 可以从以下链接下载最新版本的Wireshark。
https://www.wireshark.org/#download
https://www.wireshark.org/#download
Windows provides a different type of installers like 32 bit, 64 bit, portable. If we do not have required privileges to install application we can use portable Wireshark which do not needs installation.
Windows提供了不同类型的安装程序,例如32位,64位,便携式。 如果我们没有安装应用程序所需的特权,则可以使用不需要安装的便携式Wireshark。
Ubuntu,Debian,Mint: (Ubuntu, Debian, Mint:)
Ubuntu, Debian, Mint and other deb based distributions provide Wireshark from their official repositories. Just issue the following command to install Wireshark.
Ubuntu,Debian,Mint和其他基于deb的发行版从其官方存储库中提供了Wireshark。 只需发出以下命令来安装Wireshark。
$ sudo apt install wireshark-qt
Fedora,CentOS,RedHat: (Fedora, CentOS, RedHat:)
Fedora, CentOS, and RedHat provide Wireshark package in their repositories too. In order to install Wireshark in Fedora, CentOS and RedHat issue following command.
Fedora,CentOS和RedHat也在其存储库中提供Wireshark软件包。 为了在Fedora中安装Wireshark,CentOS和RedHat发出以下命令。
$ sudo yum install wireshark-qt
选择接口和捕获数据包 (Select Interface and Capture Packets)
One of the fundamental operation with Wireshark is selecting an interface to capture network packets. When we open Wireshark we will see the following screen. Available interfaces are listed with their name current network traffic on that interface is shown with a simple graph.
Wireshark的基本操作之一是选择一个接口来捕获网络数据包。 当我们打开Wireshark时,我们将看到以下屏幕。 可用接口以其名称列出,该接口上的当前网络流量以简单图形显示。
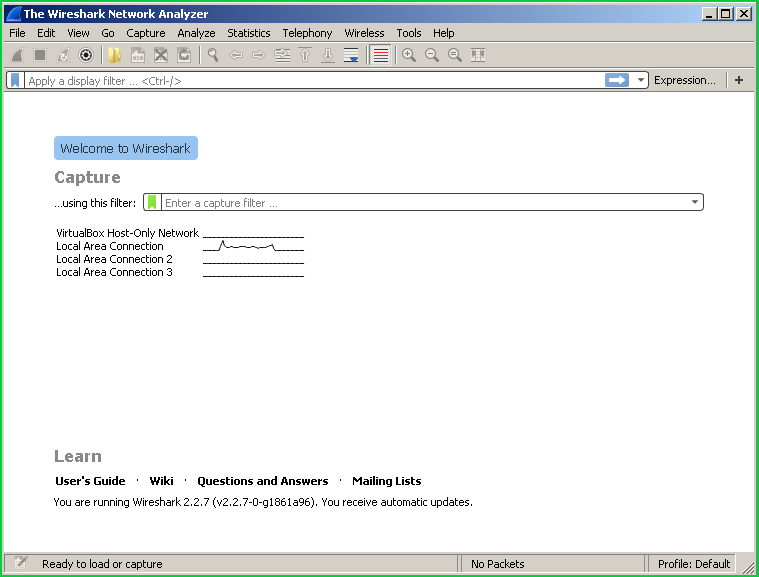
Here we will see that namedLocal Area Connection interface has some network traffic. By the way, Wireshark can listen to USB interfaces too.
在这里,我们将看到命名的Local Area Connection接口具有一些网络流量。 顺便说一下,Wireshark也可以监听USB接口。
We double click on andLocal Area Connection this will start network capture on this interface and a new screen will be opened where the network packets flow.
双击并单击“ Local Area Connection这将在此接口上开始网络捕获,并在网络数据包流向的位置打开一个新屏幕。
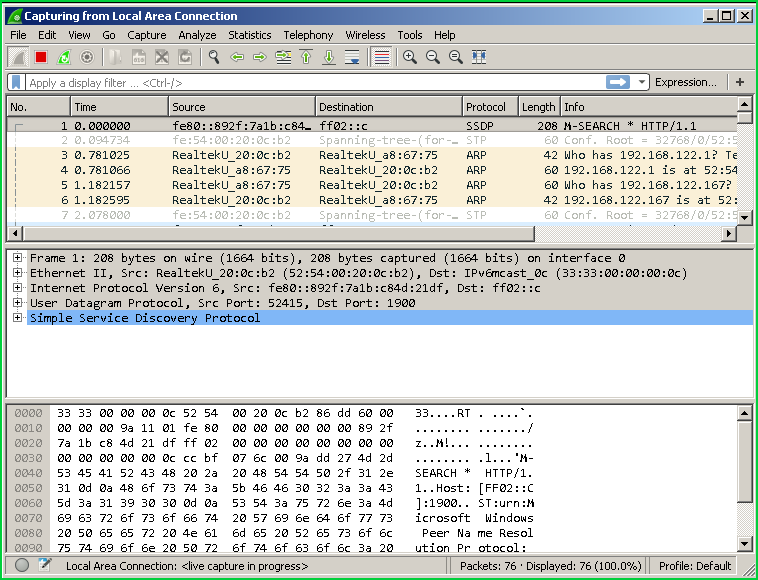
显示特定的数据包详细信息(Show Specific Packet Details)
We generally look at some specific packets to analyze. We can locate the packet we want in a simple way from the right side of the packet flow list and click on the packet. This will show detailed packet information in the middle section where Frame, Ethernet, IP, TCP/UDP, and Application layer information provided. In the lowest and third section, we will see application layer data in hex format.
我们通常查看一些特定的数据包进行分析。 我们可以从数据包流列表的右侧以简单的方式找到所需的数据包,然后单击该数据包。 这将在中间部分显示详细的数据包信息,其中提供了帧,以太网,IP,TCP / UDP和应用程序层信息。 在最低和第三部分,我们将以十六进制格式查看应用程序层数据。
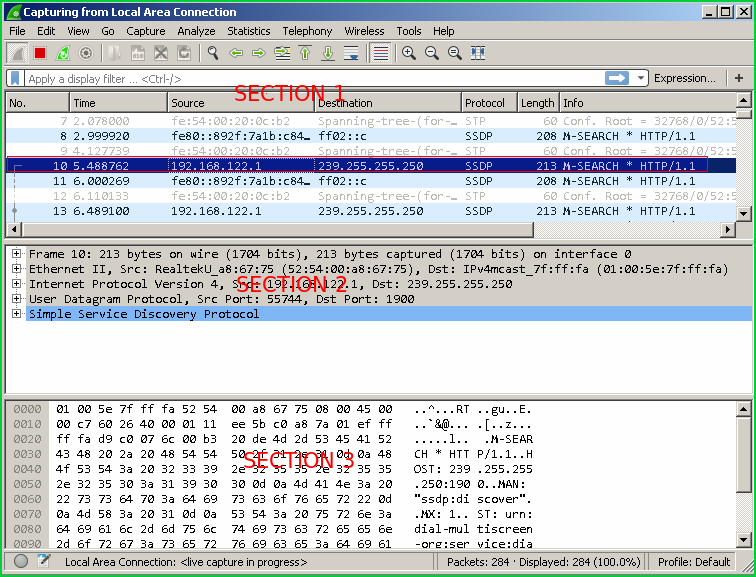
过滤捕获的数据包(Filter Captured Packets)
In a busy network, there will be a lot of packets flying around. This will make to look some packets one by one very hard job. Wireshark has very powerful filtering features. We can filter captured packets according to a protocol like IP, TCP, UDP, IP address, Source address destination address, TCP port, mac address, DNS packet, SNMP packet etc. There are a lot of them. We will simply look most popular of them. We can get the whole list of supported filter expressions by clicking buttonExpression on the left up corner. We can see the filter textbox and buttonExpression.
在繁忙的网络中,将有很多数据包在飞来飞去。 这将使查找某些数据包变得非常困难。 Wireshark具有非常强大的过滤功能。 我们可以根据协议过滤捕获的数据包,例如IP,TCP,UDP,IP地址,源地址目标地址,TCP端口,mac地址,DNS数据包,SNMP数据包等。它们很多。 我们只会看起来其中最受欢迎。 通过单击左上角的“ Expression ”按钮,可以获取支持的过滤器表达式的完整列表。 我们可以看到过滤器文本框和按钮Expression 。
List of supported expressions. As we can see there are a lot of protocols like.
支持的表达式列表。 我们可以看到有很多类似的协议。
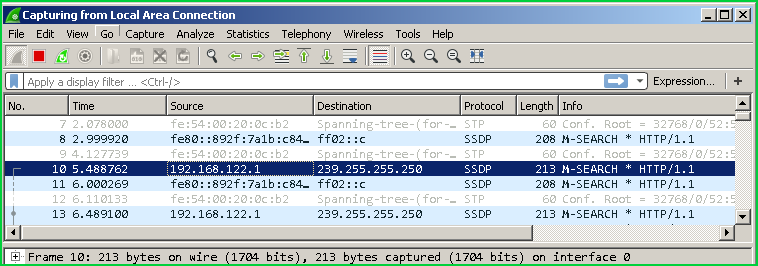
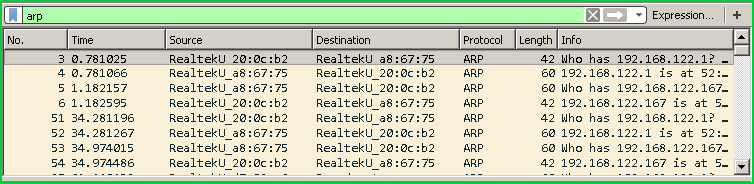
过滤ARP数据包 (Filter ARP Packets)
In this example we will filter ARP packets and section or the packet list only provides ARP protocol packets. We will only use arp in the filter box.
在此示例中,我们将过滤ARP数据包,而section或数据包列表仅提供ARP协议数据包。 我们将仅在过滤器框中使用arp 。
arp
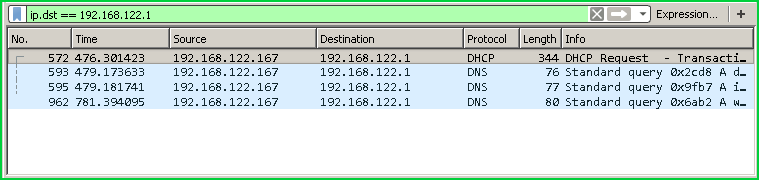
根据目标IP地址过滤(Filter According To Destination IP Address)
Another popular usage is filtering packet those have specified destination IP address. In this example, we will filter and only show those packets which have a destination IP address is 192.168.122.ip.
另一种流行的用法是过滤具有指定目标IP地址的数据包。 在此示例中,我们将过滤并仅显示目标IP地址为192.168.122.ip.那些数据包。
ip.dst == 192.168.122.1
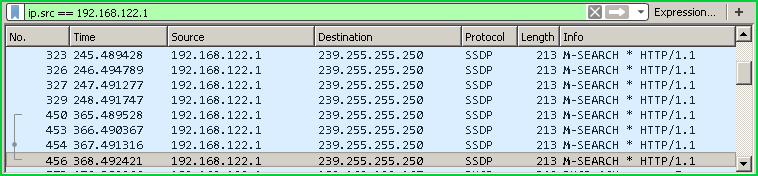
根据源IP地址过滤(Filter According To Source IP Address)
We can also filter according to source IP address too. In this example, we will filter IP source address 192.168.122.1
我们也可以根据源IP地址进行过滤。 在此示例中,我们将过滤IP源地址192.168.122.1
ip.src == 192.168.122.1
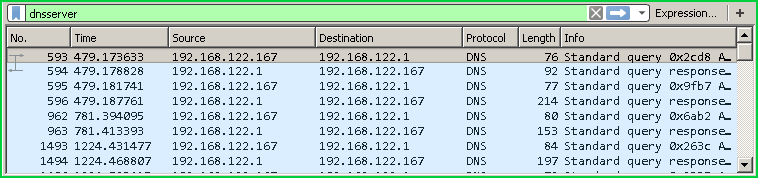
过滤DNS数据包(Filter DNS Packets)
We can filter DNS packets with keyworddnsserver like below.
我们可以使用关键字dnsserver过滤DNS数据包,如下所示。
dnsserver
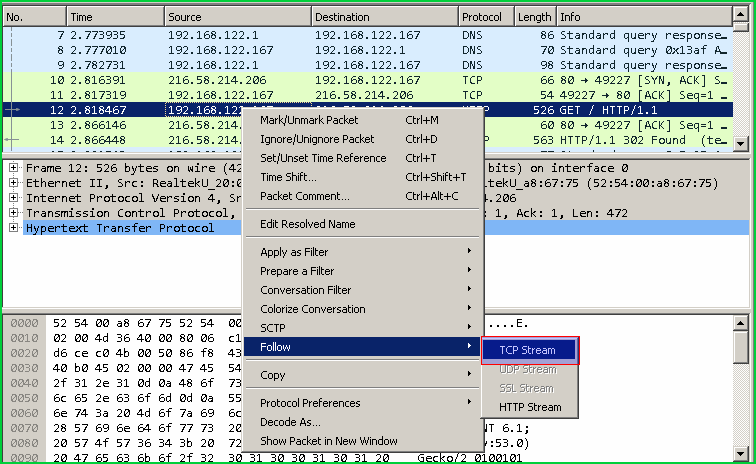
关注TCP流(Follow TCP Stream)
During a regular web page load or request, there will be some round trip to download data. If we need to inspect the whole request and response traffic we need to filter multiple packets. We can accomplish this by filtering according to a TCP session or TCP stream. It is called Follow TCP Stream .
在常规的网页加载或请求期间,将有一些往返下载数据。 如果我们需要检查整个请求和响应流量,则需要过滤多个数据包。 我们可以通过根据TCP会话或TCP流进行过滤来完成此操作。 它称为“ Follow TCP Stream 。
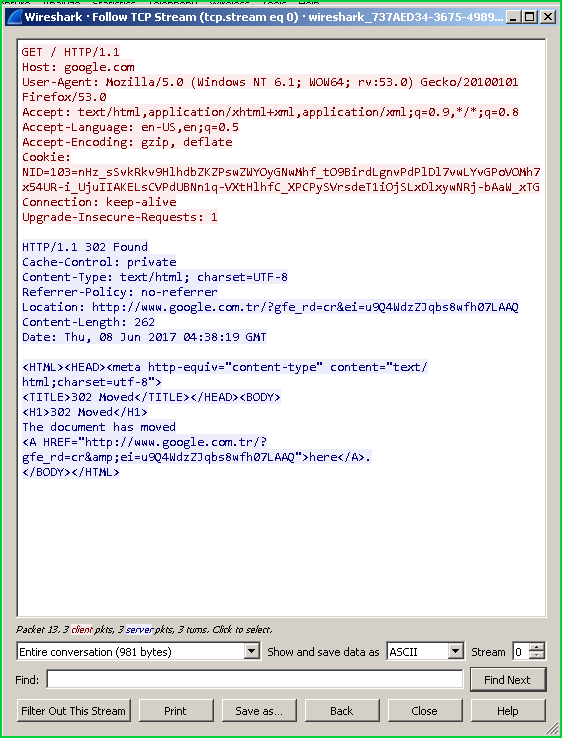
This will provide the following screen which provides the whole HTTP request and response session. We can also search these with bottomFind.
这将提供以下屏幕,其中提供了整个HTTP请求和响应会话。 我们也可以使用底部的Find搜索这些。
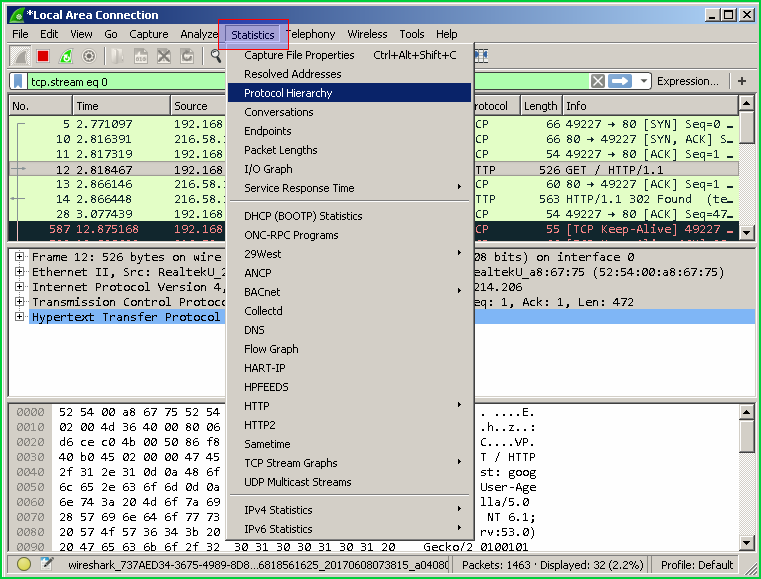
封包统计 (Packet Statistics)
One of the best features is the packet statistics. We can get a lot of different type of statistics with the menuStatistics from up. We can get the following statistical information.
最好的功能之一是数据包统计信息。 通过向上菜单“ Statistics信息”,我们可以获得许多不同类型的统计信息。 我们可以获得以下统计信息。
- Endpoints 终点
- HTTPHTTP
- IP 知识产权
- Ethernet乙太网路
- PRotocol HierarchyPRotocol层次结构
停止捕捉(Stop Capturing)
We can stop capturing network packets with Wireshark with the red button in the toolbar menu.
我们可以使用工具栏菜单中的红色按钮停止使用Wireshark捕获网络数据包。
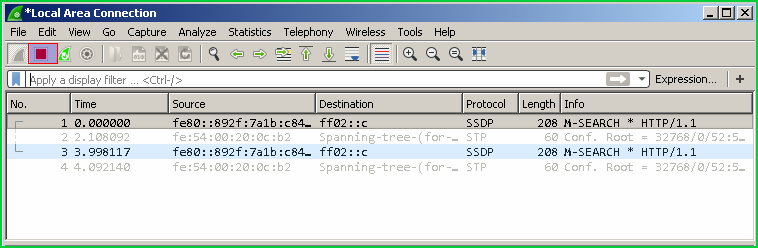
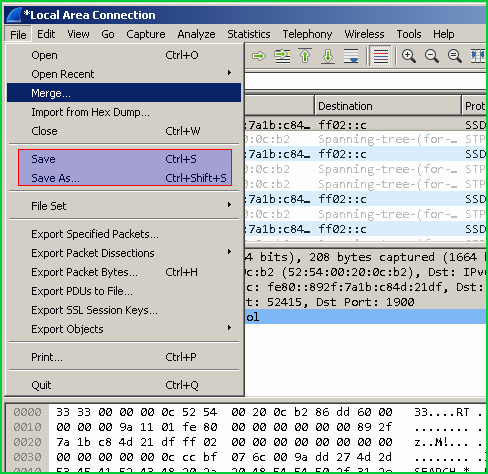
保存捕获的数据包 (Save Captured Packets)
We can save captured files. In order to save we firstly stop live packet capture. Then from the menuFile and save or Save as menus.
我们可以保存捕获的文件。 为了保存,我们首先停止实时数据包捕获。 然后从菜单File并save或Save as菜单。
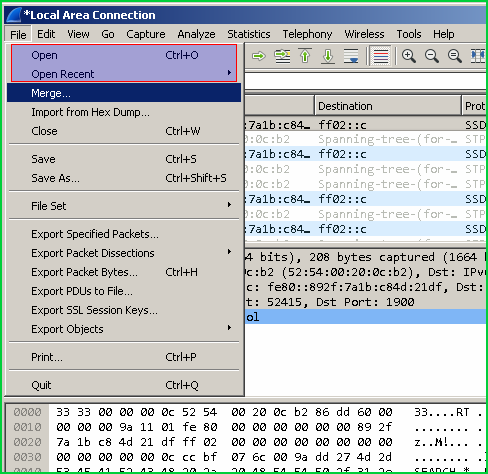
打开Cap,Pcap等捕获文件(Open Capture Files Like Cap , Pcap)
We can open already saved a different type of capture formats like cap, pcap ,ngcap etc. from File menu. We can also open recently opened capture files.
我们可以从File菜单中打开已经保存的不同类型的捕获格式,例如cap,pcap,ngcap等。 我们还可以打开最近打开的捕获文件。
翻译自: https://www.poftut.com/wireshark-capture-filter-inspect-network-packets/





















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








