声明
本文章中所有内容仅供学习交流使用,不用于其他任何目的,抓包内容、敏感网址、数据接口等均已做脱敏处理,严禁用于商业用途和非法用途,否则由此产生的一切后果均与作者无关!
逆向分析
部分python代码
cp = execjs.compile(open('tiktok.js','r',encoding='utf-8').read())
result = cp.call('decrypt',base64.b64encode(response.content).decode("utf-8"))
data = {
"aid": 1988,
"service": "",
"union": False,
"unionHost": "",
"needFid": False,
"fid": "",
"migrate_priority": 0
}
data = json.dumps(data, separators=(',', ':'))
response = requests.post(url, headers=headers, cookies=cookies, data=data)
print(response.cookies)
wss = create_connection(header=headers, url=url)
cp = execjs.compile(open('tiktok.js','r',encoding='utf-8').read())
result = cp.call('decrypt',base64.b64encode(response.content).decode("utf-8"))
data = {
"aid": 1988,
"service": "",
"union": False,
"unionHost": "",
"needFid": False,
"fid": "",
"migrate_priority": 0
}
data = json.dumps(data, separators=(',', ':'))
response = requests.post(url, headers=headers, cookies=cookies, data=data)
print(response.cookies)
wss = create_connection(header=headers, url=url)
结果
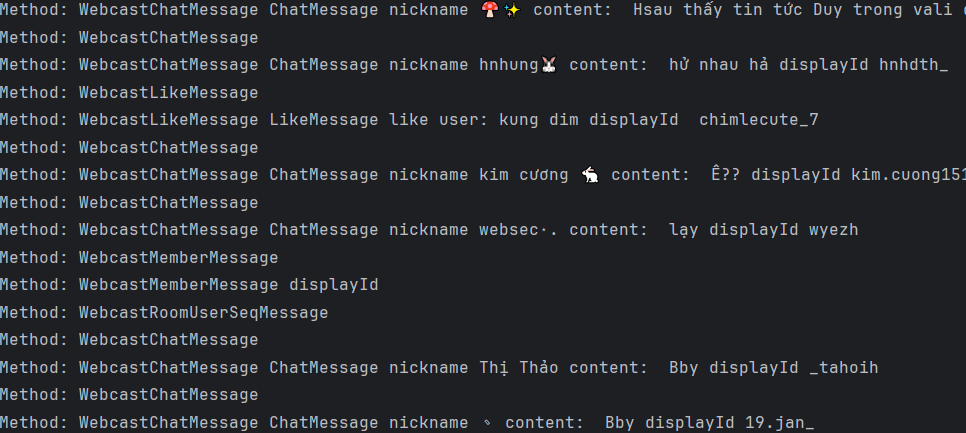
总结
1.出于安全考虑,本章未提供完整流程,调试环节省略较多,只提供大致思路,具体细节要你自己还原,相信你也能调试出来。






















 2233
2233

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










