1 为用户创建JWT RSA256证书
利用postman工具发送restfull请求
请求地址:http://${konghost}:8001/consumers/${consumerId}/jwt
1.1 添加header内容
[{
"key"
:
"Content-Type"
,
"value"
:
"application/x-www-form-urlencoded"
}]
|
1.2 利用openssl命令生成RSA 私钥和公钥
1.2.1 生成私钥
ssh-keygen -t rsa -b 4096 -f jwtRS256.key
# Don't add passphrase, 不需要设置密码
1.2.2 利用私钥生成公钥
openssl rsa -in jwtRS256.key -pubout -outform PEM -out jwtRS256.key.pub
1.2.3 查看私钥是否生成成功
cat jwtRS256.key
#查看公钥钥是否生成成功
cat jwtRS256.key.pub
1.2.4 将公钥粘贴复制出来
如下是我复制出来的内容:
-----BEGIN PUBLIC KEY-----
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEArrGzztq8tDH43gk9qqvl
NuUPZJAc2lHq5pCmYaQGoSRfq0VE5DkoYyHs+tdxC0o3fjOkJnhz3CM5+3nKwqRE
UFcMb2Pg0kVktFjApd8B0Qa6LKnE8uX815XOwS9K7JXLAem5gaAZBVUs73Q+UsNk
if1ImiYM415A2PPMeT3rnOWcZ62bqUjAr8LgTt1Lli9s6aDZ070/LFpJVhk45sZK
90KalpEy+8q7U+QiXX8LAq/K+nkZhXqmZ5R3OPabmM2e5kcvg8HtJs+DVYsfGTS8
di/3bh2DjTId/H7NNhV2B4XtcNR7mq8bQocseOGLbQBQekrVPOwjJCgd6EByzVbZ
ojGE5juMb+OFTmFqHJlsfY64EalLG0eZfNqDc/6O38oTSunAIlMwYtEA9YD2VT8D
ecWaNKsMX/vPo/ON4dWqltKrQyp7nkITIpqbL8dzujaMMyVXqoLGtSF6XDNOd1ay
Qj/B2r6xZKxmYm9I05vV3MQpxi6XkN+r09jLsS4FaCBgNVZ7qBS2TEXfYdPXHrcR
AM2piRqiIIcr6vp3p6J5Y5D9dEhObIFw1a0bp/gSLcAr9Ds+9cHv5Ov1fRRhZDeZ
NX4xztrKgsqSTJNCLeZOYtvp2zAk08Fnn484ZWRimuJOgYKx0LubR0107PwAvih2
2JEbA3AfD7iWYpAXVYkNtl0CAwEAAQ==
-----END PUBLIC KEY-----
|
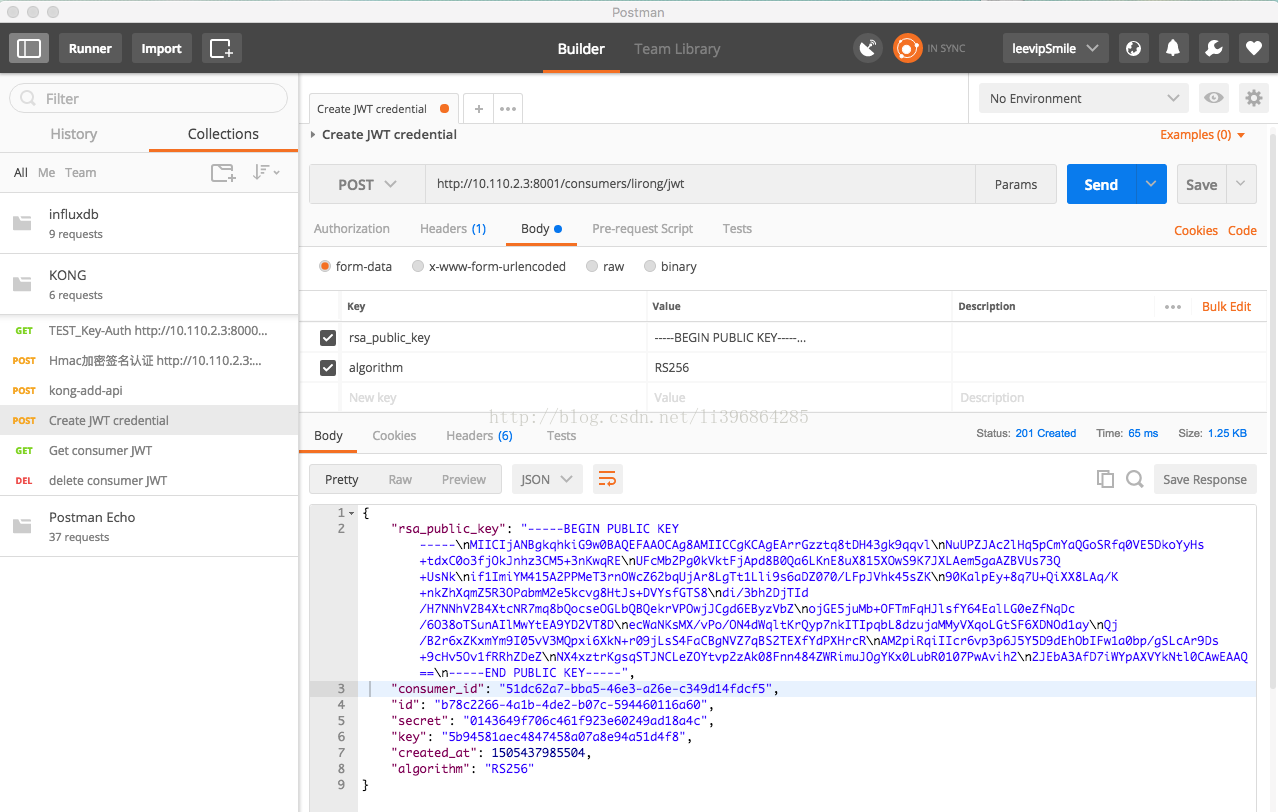
1.3 填写restful form-data body正文
添加参数:
rsa_public_key: 填写上一步1.2.4复制出来的公钥
algorithm: 填写RS256
1.4 最后点击发送
POST方式发送请求。成功后的截图如下:
curl -X POST \
http:
//10
.110.2.3:8001
/consumers/netBank/jwt
\
-H
'cache-control: no-cache'
\
-H
'content-type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW'
\
-H
'postman-token: ec74888f-26b2-95a2-5aa9-ffbd7b0b9336'
\
-F 'rsa_public_key=-----BEGIN PUBLIC KEY-----
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEArrGzztq8tDH43gk9qqvl
NuUPZJAc2lHq5pCmYaQGoSRfq0VE5DkoYyHs+tdxC0o3fjOkJnhz3CM5+3nKwqRE
UFcMb2Pg0kVktFjApd8B0Qa6LKnE8uX815XOwS9K7JXLAem5gaAZBVUs73Q+UsNk
if1ImiYM415A2PPMeT3rnOWcZ62bqUjAr8LgTt1Lli9s6aDZ070
/LFpJVhk45sZK
90KalpEy+8q7U+QiXX8LAq
/K
+nkZhXqmZ5R3OPabmM2e5kcvg8HtJs+DVYsfGTS8
di
/3bh2DjTId/H7NNhV2B4XtcNR7mq8bQocseOGLbQBQekrVPOwjJCgd6EByzVbZ
ojGE5juMb+OFTmFqHJlsfY64EalLG0eZfNqDc
/6O38oTSunAIlMwYtEA9YD2VT8D
ecWaNKsMX
/vPo/ON4dWqltKrQyp7nkITIpqbL8dzujaMMyVXqoLGtSF6XDNOd1ay
Qj
/B2r6xZKxmYm9I05vV3MQpxi6XkN
+r09jLsS4FaCBgNVZ7qBS2TEXfYdPXHrcR
AM2piRqiIIcr6vp3p6J5Y5D9dEhObIFw1a0bp
/gSLcAr9Ds
+9cHv5Ov1fRRhZDeZ
NX4xztrKgsqSTJNCLeZOYtvp2zAk08Fnn484ZWRimuJOgYKx0LubR0107PwAvih2
2JEbA3AfD7iWYpAXVYkNtl0CAwEAAQ==
-----END PUBLIC KEY-----' \
-F algorithm=RS256
|
2 模拟客户端调用
2.1 RSA256加解密概述
JWT 规范按如下内容组合签名串:
base64UrlEncode(header) +"."+ base64UrlEncode(payload)+"."+SHA256RSA.sign(header+payload, privateKey)
并将生成的加密串(headerBase64UrlEncodeString.payloadBase64UrlEncodeString.sha256RSASignatureString)
最终通过"." 号拼接。
2.2 准备加密签名信息
需要提前准备好:私钥,公钥,header,payload,签名算法。
2.2.1私钥
-----BEGIN RSA PRIVATE KEY-----
MIIJKgIBAAKCAgEArrGzztq8tDH43gk9qqvlNuUPZJAc2lHq5pCmYaQGoSRfq0VE
5DkoYyHs+tdxC0o3fjOkJnhz3CM5+3nKwqREUFcMb2Pg0kVktFjApd8B0Qa6LKnE
8uX815XOwS9K7JXLAem5gaAZBVUs73Q+UsNkif1ImiYM415A2PPMeT3rnOWcZ62b
qUjAr8LgTt1Lli9s6aDZ070/LFpJVhk45sZK90KalpEy+8q7U+QiXX8LAq/K+nkZ
hXqmZ5R3OPabmM2e5kcvg8HtJs+DVYsfGTS8di/3bh2DjTId/H7NNhV2B4XtcNR7
mq8bQocseOGLbQBQekrVPOwjJCgd6EByzVbZojGE5juMb+OFTmFqHJlsfY64EalL
G0eZfNqDc/6O38oTSunAIlMwYtEA9YD2VT8DecWaNKsMX/vPo/ON4dWqltKrQyp7
nkITIpqbL8dzujaMMyVXqoLGtSF6XDNOd1ayQj/B2r6xZKxmYm9I05vV3MQpxi6X
kN+r09jLsS4FaCBgNVZ7qBS2TEXfYdPXHrcRAM2piRqiIIcr6vp3p6J5Y5D9dEhO
bIFw1a0bp/gSLcAr9Ds+9cHv5Ov1fRRhZDeZNX4xztrKgsqSTJNCLeZOYtvp2zAk
08Fnn484ZWRimuJOgYKx0LubR0107PwAvih22JEbA3AfD7iWYpAXVYkNtl0CAwEA
AQKCAgAe4XjYiyAqdl742QdWoTZOouU6sKL5ENwGT/GpdvZZC/YBb6hC87uo8nlS
yjzIcyEmJPjSeB56/pskUh4+lA0jao/fLPe0E+I+YyYC7E4E5jyI4qXXDkLI1UmM
KtECy2PsfaV2PZfOsoTT+2d8999Q6T4pSaqjkqjB8S7nC8QXoxsn1K+cmCi/qSI/
rqzK6q1FC1MWM/Dz5S3rk1/Uo57i4Jo1HYu2qNq+dKiCgI+wtOSbrEaPquO5kawV
nLpao5aAPHswvlouryYXPBWOPh1GgyopA/yaPA7C8KNT+S05HTqg5F7JNEUMWJrK
74vXA+Q2Cf5x24hGvvSydpoUpFKqJ3O33jPchKZkkUk6XSdp4HG4Sn727ovVruVu
Oy18w9MvzKCEm3fPH/ySmXJGLLuISEi8p0iVrHuuyD10bNw41EnkYbxC2fy/tzw/
gj47G9wCc2c4Sq8hxmBvTppzeHKVQddc1cLtm+CCyPVzFknIZx1dP5GC3te9aqky
3v5li2RfzeuxsFt8zItk2HLAU7m4nB6ubu3g6dA9Oy8pW2/7Vv9GgvUTGUoPvB2m
vAqTrdmvjbSCV3402jaFVqjSe8nSob7m/32+6DXu70QZZ7gPi54GH9uhEMKHLsx5
OYalCHyV50fnlco8Fr5bxARxAKEyLjoaBATKEA0NEQ+UOT7uPQKCAQEA1Y4SktpU
JGgG+ZFwC9SXG+SNy235uek0LbR/2OR0toHLaPGNDBY/mpcZHFQMogmHrKDQd91P
fKvBlhGErL4lgu6AEaVI6rI3ztAlDmVu01kMmmGAtv9wXfbF6S28Rp4BFzpdVB0S
X4xhaOdYhjTBELkChAqp1wdEZOZ9NMJx/VPJ7Dfyp8kw56hk1vm0IOcsuGvB8qbI
9xPxGKfTl3QS9cPBKmWzItU7gQLV2GseURA8EiVUFT18GNyvuftJE1rN0YlDvtMl
he3ZDGdW0OCvo5GoKkWU27gd4VT4RkIRjuvbykCgOd/OX2FO+m4S12n4KpDnR8N6
C5egFlBiqchUXwKCAQEA0WpYfTEQnsP6W87INfWdfFCjIUFxx0IDGIgKNYm3Fcd3
8y1EEdDTsCIp3d0jRKixVW7AuM1qljlmwNTC7yV2DRjqhvqxZOk+UzrRIDaBFSBn
rV/tx/2Hr5l4eqjORI9BhkwqSFsDrnQp9hb3hYMVoFp1uswizL631pHAPp6tLO2L
hCyD0Lykv2roqVhZlUGevjb7VkqWWUnTwSSaxmwpZ+ETydZLI5TtoXh2VlZMyhkP
ChiMN8RHXBI/xSutTaXVkzZZVj4+k1t7Y5vH826k+WuVpZk4ZFXm/T+M5NpomKtn
6qbpXAQLGw6tnuzIVEADs/wxuOFF4pRE3uzn8A/OwwKCAQEAv3cfg/anlfSGvF7+
/DxgNqvVzVwOl/ZTx96a+VTqp277dl2LPhj8cZei9dkNcoHk2IteHPmY+IftiqSu
NUpNy3QV8rwkAfhDPPM1JhEfKfIe8JMWmfuvPS+xBXzx3sZu5+p2HqHqBSyRcUJq
BflqV5nofYYp/BYR5f0YqKLlHGFxGo6WyoQBitFZh7xdGVrqp3ZFb07Fw3Bnqtld
Rd7V2O7nUyHXWBWhwetO2zg++CL8GLDLEDgN+SRzkOWRAP9apNDSolYgwFEdVpeY
KLIqBxbilPPJoK0UbSCHcEZwA5nHdzA1922HU9CkxLbHwcbKry83jQnfdGE/MIJl
0x8/NQKCAQEA0Bev1L9Dt7AggMgq1Mu7cYOjhnFEwW7MKr1L/8VYJBExFXjekiGD
qRtZpPiQijJi/PTwFvMwPhTOEUGabw83jm465mQIkLDhWM0yb6MZg8fOnk6btsYs
5YZIXQKO7Tu5Ld1TitC+CMWvyLUrwwTuIYiiQjuFPRUrEtGESfVdOi7WG0Isvegm
gXuXtGdxpUoulu+Fs0qsug8Nl3hrQE7MmkfjZQZHZhUgSPquBL7+0TgzZKHd+7BU
BJ6xtZjgPi9S2lUAUx3JCp62LtXmy/QfhSWt738gtTtTLEXRGLwbgdGZkmfHrcLq
0jk0t56stmNiCqDJO+DGlA8nnKmnFDpxBwKCAQEAmV7d77sNH85vG1qEDT+RWyfv
NOZDofZMZSHbH5kLgfMJMccsrIGTAsvu0doceZukAJVv0wjjdTL/JOk8AzK9wo9F
RebHNoLKpGXpoD8LC4wO1PIYPdc3jzOgmtyNPQsp83sIasUzJpKrV9sAdEvBllgt
X7SAvAUyrh7PkOJDFOR1IAY8DGhxNmMZzuC3gMDsTCGasg0VWS5YBym9dI83CsL6
mdORAxOVsMVhxkkCnCFisxp1ufruqg7y0/18zeM2mhkOmWGmZ+t4SWaBcp41GAZb
cPytKQu2RD6optpJL8U2pQrZZJDYy/qNNGH2tOeXN/6wQBzd3gf19qxWJMpwfg==
-----END RSA PRIVATE KEY-----
|
2.2.2 公钥
-----BEGIN PUBLIC KEY-----
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEArrGzztq8tDH43gk9qqvl
NuUPZJAc2lHq5pCmYaQGoSRfq0VE5DkoYyHs+tdxC0o3fjOkJnhz3CM5+3nKwqRE
UFcMb2Pg0kVktFjApd8B0Qa6LKnE8uX815XOwS9K7JXLAem5gaAZBVUs73Q+UsNk
if1ImiYM415A2PPMeT3rnOWcZ62bqUjAr8LgTt1Lli9s6aDZ070/LFpJVhk45sZK
90KalpEy+8q7U+QiXX8LAq/K+nkZhXqmZ5R3OPabmM2e5kcvg8HtJs+DVYsfGTS8
di/3bh2DjTId/H7NNhV2B4XtcNR7mq8bQocseOGLbQBQekrVPOwjJCgd6EByzVbZ
ojGE5juMb+OFTmFqHJlsfY64EalLG0eZfNqDc/6O38oTSunAIlMwYtEA9YD2VT8D
ecWaNKsMX/vPo/ON4dWqltKrQyp7nkITIpqbL8dzujaMMyVXqoLGtSF6XDNOd1ay
Qj/B2r6xZKxmYm9I05vV3MQpxi6XkN+r09jLsS4FaCBgNVZ7qBS2TEXfYdPXHrcR
AM2piRqiIIcr6vp3p6J5Y5D9dEhObIFw1a0bp/gSLcAr9Ds+9cHv5Ov1fRRhZDeZ
NX4xztrKgsqSTJNCLeZOYtvp2zAk08Fnn484ZWRimuJOgYKx0LubR0107PwAvih2
2JEbA3AfD7iWYpAXVYkNtl0CAwEAAQ==
-----END PUBLIC KEY-----
|
2.2.3 header内容
{
"alg"
:
"RS256"
,
"typ"
:
"JWT"
}
|
2.2.4 payload内容
{
"iss"
:
"e9d24e5d802743b8822d8e0e6e7e64bf"
,
"exp"
: 1506457076
}
|
2.2.5 签名算法
增加pom依赖
<
dependency
>
<
groupId
>io.jsonwebtoken</
groupId
>
<
artifactId
>jjwt</
artifactId
>
<
version
>0.7.0</
version
>
</
dependency
>
|
编写签名算法
import
io.jsonwebtoken.Jwts;
import
io.jsonwebtoken.SignatureAlgorithm;
import
lombok.extern.slf4j.Slf4j;
import
java.security.*;
import
java.security.spec.PKCS8EncodedKeySpec;
import
java.text.SimpleDateFormat;
import
java.util.Base64;
@Slf4j
public
class
SHA256RSA {
public
static
final
String strPk =
"-----BEGIN RSA PRIVATE KEY-----\n"
+
"MIIJKgIBAAKCAgEArrGzztq8tDH43gk9qqvlNuUPZJAc2lHq5pCmYaQGoSRfq0VE\n"
+
"5DkoYyHs+tdxC0o3fjOkJnhz3CM5+3nKwqREUFcMb2Pg0kVktFjApd8B0Qa6LKnE\n"
+
"8uX815XOwS9K7JXLAem5gaAZBVUs73Q+UsNkif1ImiYM415A2PPMeT3rnOWcZ62b\n"
+
"qUjAr8LgTt1Lli9s6aDZ070/LFpJVhk45sZK90KalpEy+8q7U+QiXX8LAq/K+nkZ\n"
+
"hXqmZ5R3OPabmM2e5kcvg8HtJs+DVYsfGTS8di/3bh2DjTId/H7NNhV2B4XtcNR7\n"
+
"mq8bQocseOGLbQBQekrVPOwjJCgd6EByzVbZojGE5juMb+OFTmFqHJlsfY64EalL\n"
+
"G0eZfNqDc/6O38oTSunAIlMwYtEA9YD2VT8DecWaNKsMX/vPo/ON4dWqltKrQyp7\n"
+
"nkITIpqbL8dzujaMMyVXqoLGtSF6XDNOd1ayQj/B2r6xZKxmYm9I05vV3MQpxi6X\n"
+
"kN+r09jLsS4FaCBgNVZ7qBS2TEXfYdPXHrcRAM2piRqiIIcr6vp3p6J5Y5D9dEhO\n"
+
"bIFw1a0bp/gSLcAr9Ds+9cHv5Ov1fRRhZDeZNX4xztrKgsqSTJNCLeZOYtvp2zAk\n"
+
"08Fnn484ZWRimuJOgYKx0LubR0107PwAvih22JEbA3AfD7iWYpAXVYkNtl0CAwEA\n"
+
"AQKCAgAe4XjYiyAqdl742QdWoTZOouU6sKL5ENwGT/GpdvZZC/YBb6hC87uo8nlS\n"
+
"yjzIcyEmJPjSeB56/pskUh4+lA0jao/fLPe0E+I+YyYC7E4E5jyI4qXXDkLI1UmM\n"
+
"KtECy2PsfaV2PZfOsoTT+2d8999Q6T4pSaqjkqjB8S7nC8QXoxsn1K+cmCi/qSI/\n"
+
"rqzK6q1FC1MWM/Dz5S3rk1/Uo57i4Jo1HYu2qNq+dKiCgI+wtOSbrEaPquO5kawV\n"
+
"nLpao5aAPHswvlouryYXPBWOPh1GgyopA/yaPA7C8KNT+S05HTqg5F7JNEUMWJrK\n"
+
"74vXA+Q2Cf5x24hGvvSydpoUpFKqJ3O33jPchKZkkUk6XSdp4HG4Sn727ovVruVu\n"
+
"Oy18w9MvzKCEm3fPH/ySmXJGLLuISEi8p0iVrHuuyD10bNw41EnkYbxC2fy/tzw/\n"
+
"gj47G9wCc2c4Sq8hxmBvTppzeHKVQddc1cLtm+CCyPVzFknIZx1dP5GC3te9aqky\n"
+
"3v5li2RfzeuxsFt8zItk2HLAU7m4nB6ubu3g6dA9Oy8pW2/7Vv9GgvUTGUoPvB2m\n"
+
"vAqTrdmvjbSCV3402jaFVqjSe8nSob7m/32+6DXu70QZZ7gPi54GH9uhEMKHLsx5\n"
+
"OYalCHyV50fnlco8Fr5bxARxAKEyLjoaBATKEA0NEQ+UOT7uPQKCAQEA1Y4SktpU\n"
+
"JGgG+ZFwC9SXG+SNy235uek0LbR/2OR0toHLaPGNDBY/mpcZHFQMogmHrKDQd91P\n"
+
"fKvBlhGErL4lgu6AEaVI6rI3ztAlDmVu01kMmmGAtv9wXfbF6S28Rp4BFzpdVB0S\n"
+
"X4xhaOdYhjTBELkChAqp1wdEZOZ9NMJx/VPJ7Dfyp8kw56hk1vm0IOcsuGvB8qbI\n"
+
"9xPxGKfTl3QS9cPBKmWzItU7gQLV2GseURA8EiVUFT18GNyvuftJE1rN0YlDvtMl\n"
+
"he3ZDGdW0OCvo5GoKkWU27gd4VT4RkIRjuvbykCgOd/OX2FO+m4S12n4KpDnR8N6\n"
+
"C5egFlBiqchUXwKCAQEA0WpYfTEQnsP6W87INfWdfFCjIUFxx0IDGIgKNYm3Fcd3\n"
+
"8y1EEdDTsCIp3d0jRKixVW7AuM1qljlmwNTC7yV2DRjqhvqxZOk+UzrRIDaBFSBn\n"
+
"rV/tx/2Hr5l4eqjORI9BhkwqSFsDrnQp9hb3hYMVoFp1uswizL631pHAPp6tLO2L\n"
+
"hCyD0Lykv2roqVhZlUGevjb7VkqWWUnTwSSaxmwpZ+ETydZLI5TtoXh2VlZMyhkP\n"
+
"ChiMN8RHXBI/xSutTaXVkzZZVj4+k1t7Y5vH826k+WuVpZk4ZFXm/T+M5NpomKtn\n"
+
"6qbpXAQLGw6tnuzIVEADs/wxuOFF4pRE3uzn8A/OwwKCAQEAv3cfg/anlfSGvF7+\n"
+
"/DxgNqvVzVwOl/ZTx96a+VTqp277dl2LPhj8cZei9dkNcoHk2IteHPmY+IftiqSu\n"
+
"NUpNy3QV8rwkAfhDPPM1JhEfKfIe8JMWmfuvPS+xBXzx3sZu5+p2HqHqBSyRcUJq\n"
+
"BflqV5nofYYp/BYR5f0YqKLlHGFxGo6WyoQBitFZh7xdGVrqp3ZFb07Fw3Bnqtld\n"
+
"Rd7V2O7nUyHXWBWhwetO2zg++CL8GLDLEDgN+SRzkOWRAP9apNDSolYgwFEdVpeY\n"
+
"KLIqBxbilPPJoK0UbSCHcEZwA5nHdzA1922HU9CkxLbHwcbKry83jQnfdGE/MIJl\n"
+
"0x8/NQKCAQEA0Bev1L9Dt7AggMgq1Mu7cYOjhnFEwW7MKr1L/8VYJBExFXjekiGD\n"
+
"qRtZpPiQijJi/PTwFvMwPhTOEUGabw83jm465mQIkLDhWM0yb6MZg8fOnk6btsYs\n"
+
"5YZIXQKO7Tu5Ld1TitC+CMWvyLUrwwTuIYiiQjuFPRUrEtGESfVdOi7WG0Isvegm\n"
+
"gXuXtGdxpUoulu+Fs0qsug8Nl3hrQE7MmkfjZQZHZhUgSPquBL7+0TgzZKHd+7BU\n"
+
"BJ6xtZjgPi9S2lUAUx3JCp62LtXmy/QfhSWt738gtTtTLEXRGLwbgdGZkmfHrcLq\n"
+
"0jk0t56stmNiCqDJO+DGlA8nnKmnFDpxBwKCAQEAmV7d77sNH85vG1qEDT+RWyfv\n"
+
"NOZDofZMZSHbH5kLgfMJMccsrIGTAsvu0doceZukAJVv0wjjdTL/JOk8AzK9wo9F\n"
+
"RebHNoLKpGXpoD8LC4wO1PIYPdc3jzOgmtyNPQsp83sIasUzJpKrV9sAdEvBllgt\n"
+
"X7SAvAUyrh7PkOJDFOR1IAY8DGhxNmMZzuC3gMDsTCGasg0VWS5YBym9dI83CsL6\n"
+
"mdORAxOVsMVhxkkCnCFisxp1ufruqg7y0/18zeM2mhkOmWGmZ+t4SWaBcp41GAZb\n"
+
"cPytKQu2RD6optpJL8U2pQrZZJDYy/qNNGH2tOeXN/6wQBzd3gf19qxWJMpwfg==\n"
+
"-----END RSA PRIVATE KEY-----"
;
private
static
final
String pkcs8PrivateKey =
"-----BEGIN PRIVATE KEY-----\n"
+
"MIIJRAIBADANBgkqhkiG9w0BAQEFAASCCS4wggkqAgEAAoICAQCusbPO2ry0Mfje\n"
+
"CT2qq+U25Q9kkBzaUermkKZhpAahJF+rRUTkOShjIez613ELSjd+M6QmeHPcIzn7\n"
+
"ecrCpERQVwxvY+DSRWS0WMCl3wHRBrosqcTy5fzXlc7BL0rslcsB6bmBoBkFVSzv\n"
+
"dD5Sw2SJ/UiaJgzjXkDY88x5Peuc5ZxnrZupSMCvwuBO3UuWL2zpoNnTvT8sWklW\n"
+
"GTjmxkr3QpqWkTL7yrtT5CJdfwsCr8r6eRmFeqZnlHc49puYzZ7mRy+Dwe0mz4NV\n"
+
"ix8ZNLx2L/duHYONMh38fs02FXYHhe1w1HuarxtChyx44YttAFB6StU87CMkKB3o\n"
+
"QHLNVtmiMYTmO4xv44VOYWocmWx9jrgRqUsbR5l82oNz/o7fyhNK6cAiUzBi0QD1\n"
+
"gPZVPwN5xZo0qwxf+8+j843h1aqW0qtDKnueQhMimpsvx3O6NowzJVeqgsa1IXpc\n"
+
"M053VrJCP8HavrFkrGZib0jTm9XcxCnGLpeQ36vT2MuxLgVoIGA1VnuoFLZMRd9h\n"
+
"09cetxEAzamJGqIghyvq+nenonljkP10SE5sgXDVrRun+BItwCv0Oz71we/k6/V9\n"
+
"FGFkN5k1fjHO2sqCypJMk0It5k5i2+nbMCTTwWefjzhlZGKa4k6BgrHQu5tHTXTs\n"
+
"/AC+KHbYkRsDcB8PuJZikBdViQ22XQIDAQABAoICAB7heNiLICp2XvjZB1ahNk6i\n"
+
"5TqwovkQ3AZP8al29lkL9gFvqELzu6jyeVLKPMhzISYk+NJ4Hnr+myRSHj6UDSNq\n"
+
"j98s97QT4j5jJgLsTgTmPIjipdcOQsjVSYwq0QLLY+x9pXY9l86yhNP7Z3z331Dp\n"
+
"PilJqqOSqMHxLucLxBejGyfUr5yYKL+pIj+urMrqrUULUxYz8PPlLeuTX9SjnuLg\n"
+
"mjUdi7ao2r50qIKAj7C05JusRo+q47mRrBWculqjloA8ezC+Wi6vJhc8FY4+HUaD\n"
+
"KikD/Jo8DsLwo1P5LTkdOqDkXsk0RQxYmsrvi9cD5DYJ/nHbiEa+9LJ2mhSkUqon\n"
+
"c7feM9yEpmSRSTpdJ2ngcbhKfvbui9Wu5W47LXzD0y/MoISbd88f/JKZckYsu4hI\n"
+
"SLynSJWse67IPXRs3DjUSeRhvELZ/L+3PD+CPjsb3AJzZzhKryHGYG9OmnN4cpVB\n"
+
"11zVwu2b4ILI9XMWSchnHV0/kYLe171qqTLe/mWLZF/N67GwW3zMi2TYcsBTubic\n"
+
"Hq5u7eDp0D07Lylbb/tW/0aC9RMZSg+8Haa8CpOt2a+NtIJXfjTaNoVWqNJ7ydKh\n"
+
"vub/fb7oNe7vRBlnuA+LngYf26EQwocuzHk5hqUIfJXnR+eVyjwWvlvEBHEAoTIu\n"
+
"OhoEBMoQDQ0RD5Q5Pu49AoIBAQDVjhKS2lQkaAb5kXAL1Jcb5I3Lbfm56TQttH/Y\n"
+
"5HS2gcto8Y0MFj+alxkcVAyiCYesoNB33U98q8GWEYSsviWC7oARpUjqsjfO0CUO\n"
+
"ZW7TWQyaYYC2/3Bd9sXpLbxGngEXOl1UHRJfjGFo51iGNMEQuQKECqnXB0Rk5n00\n"
+
"wnH9U8nsN/KnyTDnqGTW+bQg5yy4a8Hypsj3E/EYp9OXdBL1w8EqZbMi1TuBAtXY\n"
+
"ax5REDwSJVQVPXwY3K+5+0kTWs3RiUO+0yWF7dkMZ1bQ4K+jkagqRZTbuB3hVPhG\n"
+
"QhGO69vKQKA5385fYU76bhLXafgqkOdHw3oLl6AWUGKpyFRfAoIBAQDRalh9MRCe\n"
+
"w/pbzsg19Z18UKMhQXHHQgMYiAo1ibcVx3fzLUQR0NOwIind3SNEqLFVbsC4zWqW\n"
+
"OWbA1MLvJXYNGOqG+rFk6T5TOtEgNoEVIGetX+3H/YevmXh6qM5Ej0GGTCpIWwOu\n"
+
"dCn2FveFgxWgWnW6zCLMvrfWkcA+nq0s7YuELIPQvKS/auipWFmVQZ6+NvtWSpZZ\n"
+
"SdPBJJrGbCln4RPJ1ksjlO2heHZWVkzKGQ8KGIw3xEdcEj/FK61NpdWTNllWPj6T\n"
+
"W3tjm8fzbqT5a5WlmThkVeb9P4zk2miYq2fqpulcBAsbDq2e7MhUQAOz/DG44UXi\n"
+
"lETe7OfwD87DAoIBAQC/dx+D9qeV9Ia8Xv78PGA2q9XNXA6X9lPH3pr5VOqnbvt2\n"
+
"XYs+GPxxl6L12Q1ygeTYi14c+Zj4h+2KpK41Sk3LdBXyvCQB+EM88zUmER8p8h7w\n"
+
"kxaZ+689L7EFfPHexm7n6nYeoeoFLJFxQmoF+WpXmeh9hin8FhHl/RioouUcYXEa\n"
+
"jpbKhAGK0VmHvF0ZWuqndkVvTsXDcGeq2V1F3tXY7udTIddYFaHB607bOD74IvwY\n"
+
"sMsQOA35JHOQ5ZEA/1qk0NKiViDAUR1Wl5gosioHFuKU88mgrRRtIIdwRnADmcd3\n"
+
"MDX3bYdT0KTEtsfBxsqvLzeNCd90YT8wgmXTHz81AoIBAQDQF6/Uv0O3sCCAyCrU\n"
+
"y7txg6OGcUTBbswqvUv/xVgkETEVeN6SIYOpG1mk+JCKMmL89PAW8zA+FM4RQZpv\n"
+
"DzeObjrmZAiQsOFYzTJvoxmDx86eTpu2xizlhkhdAo7tO7kt3VOK0L4Ixa/ItSvD\n"
+
"BO4hiKJCO4U9FSsS0YRJ9V06LtYbQiy96CaBe5e0Z3GlSi6W74WzSqy6Dw2XeGtA\n"
+
"TsyaR+NlBkdmFSBI+q4Evv7RODNkod37sFQEnrG1mOA+L1LaVQBTHckKnrYu1ebL\n"
+
"9B+FJa3vfyC1O1MsRdEYvBuB0ZmSZ8etwurSOTS3nqy2Y2IKoMk74MaUDyecqacU\n"
+
"OnEHAoIBAQCZXt3vuw0fzm8bWoQNP5FbJ+805kOh9kxlIdsfmQuB8wkxxyysgZMC\n"
+
"y+7R2hx5m6QAlW/TCON1Mv8k6TwDMr3Cj0VF5sc2gsqkZemgPwsLjA7U8hg91zeP\n"
+
"M6Ca3I09CynzewhqxTMmkqtX2wB0S8GWWC1ftIC8BTKuHs+Q4kMU5HUgBjwMaHE2\n"
+
"YxnO4LeAwOxMIZqyDRVZLlgHKb10jzcKwvqZ05EDE5WwxWHGSQKcIWKzGnW5+u6q\n"
+
"DvLT/XzN4zaaGQ6ZYaZn63hJZoFynjUYBltw/K0pC7ZEPqim2kkvxTalCtlkkNjL\n"
+
"+o00Yfa055c3/rBAHN3eB/X2rFYkynB+\n"
+
"-----END PRIVATE KEY-----"
;
public
static
void
main(String[] args)
throws
Exception{
jwttest1();
}
static
void
jwttest1()
throws
Exception{
SimpleDateFormat sdf =
new
SimpleDateFormat(
" yyyy-MM-dd HH:mm:ss "
);
String compactJws = Jwts.builder()
.setHeaderParam(
"typ"
,
"JWT"
)
//.setHeaderParam("alg", "RS256") //有或者没有,都能成功,调用signWith(SignatureAlgorithm.RS256,key)的时候,会自检header签名内容,如没有会自动添加上.此行,可去掉.
.setIssuer(
"e9d24e5d802743b8822d8e0e6e7e64bf"
)
.setExpiration(sdf.parse(
" 2017-09-18 19:20:00 "
))
//.signWith(SignatureAlgorithm.RS256, getPrivateKey(strPk)) //test result: success.
.signWith(SignatureAlgorithm.RS256, getPKCS8PrivateKey(pkcs8PrivateKey))
//test result: success.
.compact();
log.info(
"jwt token:Bearer {}"
, compactJws);
}
/**
* @param strPk RSA PRIVATE key
* test result: success
* */
private
static
PrivateKey getPrivateKey(String strPk)
throws
Exception {
// Remove markers and new line characters in private key
String realPK = strPk.replaceAll(
"-----END RSA PRIVATE KEY-----"
,
""
)
.replaceAll(
"-----BEGIN RSA PRIVATE KEY-----"
,
""
)
.replaceAll(
"\n"
,
""
);
byte
[] b1 = Base64.getDecoder().decode(realPK);
PKCS8EncodedKeySpec spec =
new
PKCS8EncodedKeySpec(b1);
KeyFactory kf = KeyFactory.getInstance(
"RSA"
);
return
kf.generatePrivate(spec);
}
/**
* * @param strPk PKCS8 RSA PRIVATE key
* test result: success
* */
private
static
PrivateKey getPKCS8PrivateKey(String strPk)
throws
Exception {
// Remove markers and new line characters in private key
String realPK = strPk.replaceAll(
"-----END PRIVATE KEY-----"
,
""
)
.replaceAll(
"-----BEGIN PRIVATE KEY-----"
,
""
)
.replaceAll(
"\n"
,
""
);
byte
[] b1 = Base64.getDecoder().decode(realPK);
PKCS8EncodedKeySpec spec =
new
PKCS8EncodedKeySpec(b1);
KeyFactory kf = KeyFactory.getInstance(
"RSA"
);
return
kf.generatePrivate(spec);
}
}
|
2.3 计算签名
2.3.1 执行计算签名
按照2.2.5编写完成签名算法,执行main方法,输出签名。
得到签名:
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJlOWQyNGU1ZDgwMjc0M2I4ODIyZDhlMGU2ZTdlNjRiZiIsImV4cCI6MTUwNTczMzYwMH0.irjqj-13xTZbddT8OyvP9lhFqSG8EpZi4UPRqBwRcj5TBwA7ju0NvZogEUvab674c9NL7cPKd4MWyjRCV9fPZTc-Wb7V7V1JEPMf1-WS29QsKUB6lYJ4sR217l2OLnwGV_mzZpHz5-TqMp5zCDz_gYY6c22zVJPIC-znf1RLu4EvytsD6MxxLRTnEEhmJfP8V3T5K7S_8fYm87XSFB5BADgDiWReEKhukzDH4Z8ryB1cCAhApbbgMA9EhI1jWJUgMImJMsersx3dBUOrwF33Qq2zFyn-8jv6dGR_aGP0ZjDiTP5wdZDqYKA_QL6li0UrYNmr7-Guw6x9yxPYCYap2W6EjQrbyM54L1acSZNtVWXFwmV8l8L2JcgAK45ejrA0U-FhTZVFoPbhzTn9Vl99ICaIQYiS7TaK3myEZvkuHE3W7ieBfiL6CVxcU0BhUIaB5f6kt58T26-J7f1YpEPDJPXlETNOA7kTeWEe86B6xII_olNY_EV1bfw8f5de8zE45Dq3JycNtgwoDZB5Al48EMak9rodBko8qH1U2QuG3NCEC_AXxUEmEVJykzm8cZn4PYdk2u58y1ieVgfvbMeYfuwW7H9u7AHOenNIz1C2KOvQiecAptgE2VOGWpPm7A_1Ycppm0c4erY2gDAsadjm72AA_Ez_zZ9eEciCjG3gUnk
|
注意:以上签名只有一行。
2.3.2 校验签名
利用www.jwt.io 工具验证签名是否正确。
验证结果显示:Signature Verified true!通过。
2.4 模拟客户端调用
curl -X POST \
http:
//10
.110.2.3:8000
/testJWT
\
-H
'authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJlOWQyNGU1ZDgwMjc0M2I4ODIyZDhlMGU2ZTdlNjRiZiIsImV4cCI6MTUwNTczMzYwMH0.irjqj-13xTZbddT8OyvP9lhFqSG8EpZi4UPRqBwRcj5TBwA7ju0NvZogEUvab674c9NL7cPKd4MWyjRCV9fPZTc-Wb7V7V1JEPMf1-WS29QsKUB6lYJ4sR217l2OLnwGV_mzZpHz5-TqMp5zCDz_gYY6c22zVJPIC-znf1RLu4EvytsD6MxxLRTnEEhmJfP8V3T5K7S_8fYm87XSFB5BADgDiWReEKhukzDH4Z8ryB1cCAhApbbgMA9EhI1jWJUgMImJMsersx3dBUOrwF33Qq2zFyn-8jv6dGR_aGP0ZjDiTP5wdZDqYKA_QL6li0UrYNmr7-Guw6x9yxPYCYap2W6EjQrbyM54L1acSZNtVWXFwmV8l8L2JcgAK45ejrA0U-FhTZVFoPbhzTn9Vl99ICaIQYiS7TaK3myEZvkuHE3W7ieBfiL6CVxcU0BhUIaB5f6kt58T26-J7f1YpEPDJPXlETNOA7kTeWEe86B6xII_olNY_EV1bfw8f5de8zE45Dq3JycNtgwoDZB5Al48EMak9rodBko8qH1U2QuG3NCEC_AXxUEmEVJykzm8cZn4PYdk2u58y1ieVgfvbMeYfuwW7H9u7AHOenNIz1C2KOvQiecAptgE2VOGWpPm7A_1Ycppm0c4erY2gDAsadjm72AA_Ez_zZ9eEciCjG3gUnk'
|
返回结果:
{
"success"
:
true
,
"result"
:
"成功了,恭喜你."
,
"error"
:
null
}
|
以上内容由源接口返回。
至此,JWT插件RSA256非对称加密验证通过。
























 3万+
3万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








