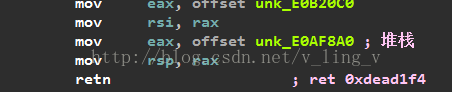
分析程序,发现sub_DEAD3AF返回的地方,修改了用户堆栈。
之后程序基本就陷入jmp***;***;ret指令中。稍微跟了一下,发现实在太多。
改了个代码,能打印出程序运行的rip,原理是使用ptrace。
#include <stdio.h>
#include <stdarg.h>
#include <stdlib.h>
#include <signal.h>
#include <syscall.h>
#include <sys/ptrace.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <sys/reg.h>
#include <sys/user.h>
#include <unistd.h>
#include <errno.h>
unsigned long startAddr = 0x000000000DEAd000;
unsigned long endAddr = 0x000000000DEAD524;
unsigned long closeAddr = 0x000000000DEAD3AF;
/* Print a message to stdout, prefixed by the process ID
*/
void procmsg(const char* format, ...)
{
va_list ap;
fprintf(stdout, "[%d] ", getpid());
va_start(ap, format);
vfprintf(stdout, format, ap);
va_end(ap);
}
void run_target(const char* programname)
{
procmsg("target started. will run '%s'\n", programname);
/* Allow tracing of this process */
if (ptrace(PTRACE_TRACEME, 0, 0, 0) < 0) {
perror("ptrace");
return;
}
/* Replace this process's image with the given program */
execl(programname, programname, 0);
}
void run_debugger(pid_t child_pid)
{
int wait_status;
unsigned icounter = 0;
FILE *fp;
procmsg("debugger started\n");
/* Wait for child to stop on its first instruction */
wait(&wait_status);
fp = fopen("log.txt","w");
while (WIFSTOPPED(wait_status)) {
//icounter++;
struct user_regs_struct regs;
ptrace(PTRACE_GETREGS, child_pid, 0, ®s);
unsigned instr = ptrace(PTRACE_PEEKTEXT, child_pid, regs.rip, 0);
//procmsg("icounter = %u. EIP = 0x%08x. instr = 0x%08x\n",
// icounter, regs.eip, instr);
//if(regs.rip)
if(regs.rip==closeAddr)
{
fflush(fp);
}
if((regs.rip >= startAddr) && (regs.rip <= endAddr))
{
fprintf(fp, "%p\n", regs.rip);
}
/* Make the child execute another instruction */
if (ptrace(PTRACE_SINGLESTEP, child_pid, 0, 0) < 0) {
perror("ptrace");
return;
}
/* Wait for child to stop on its next instruction */
wait(&wait_status);
}
fclose(fp);
procmsg("the child executed %u instructions\n", icounter);
}
int main(int argc, char** argv)
{
pid_t child_pid;
if (argc < 2) {
fprintf(stderr, "Expected a program name as argument\n");
return -1;
}
child_pid = fork();
if (child_pid == 0)
run_target(argv[1]);
else if (child_pid > 0)
run_debugger(child_pid);
else {
perror("fork");
return -1;
}
return 0;
}idapython:获取指令对应的汇编。
from idaapi import *
from idc import *
from idautils import *
f = open('d:/log.txt', 'r')
f2 = open('d:/output.txt', 'w')
for line in f:
ea = int(line.strip('\n'),16)
f2.write(line.strip('\n')+' '+idc.GetDisasm(ea)+'\n')
f.close()
f2.close()
print 'done'再写脚本,去掉其中的jmp;ret;subrsi,8; addrsi,8;之后大概有500多行。然后在其中分析数据走向,发现输入的数据只传给了r8和r12。
r8=key
r12=1
r12=r8*r12
r8=r8*r8
r8=r8*r8
r8=r8*r8
r12=r8*r12
r8=r8*r8
r12=r12*r8
r8=r8*r8
r8=r8*r8
r8=r8*r8
r8=r8*r8
r8=r8*r8
r8=r8*r8
r12=r12*r8
r8=r8*r8
r8=r8*r8
r12=r12*r8
r8=r8*r8
r12=r8*r12
r8=r8*r8
r12 == 0x2724090c0798e4c5
整理了一下:
0x2724090c0798e4c5 =x ^ 13337 mod 2^64
好吧,数学问题。
队友写了个脚本解:
left = 0x2a900a13b88bcca5
mi = 13337
mo = 64
right = []
for i in range(mo):
m = (pow(2, i + 1))
l = left % m
r = 0
for index, value in enumerate(right):
r += value * pow(2, index)
if pow(r, mi, m) == l:
right.append(0)
elif pow((r + pow(2, i)), mi, m) == l:
right.append(1)
else:
raise
r = 0
for index, value in enumerate(right):
r += value * pow(2, index)
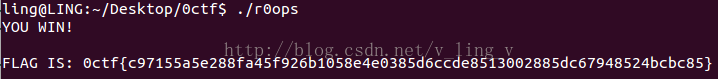
print r经过8轮比较,程序吐出了flag。
import telnetlib
from convert import *
ip = '192.168.194.129'
port = 13337
#port = 35892
t = telnetlib.Telnet(ip, port)
t.write(l64(15397851891508532645)+l64(5882479468299745861)+l64(6203462900357968133)+l64(11756062250229433221)+ \
l64(6010465035347615365)+l64(10697597399494305925)+l64(14617956564689458309)+l64(9036388475871214725)+l64(0)+'\n')
t.interact()





















 2015
2015

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








