17.1 聚合分析
def:n个操作序列在最坏情况下花费的总时间T(n),则这些操作的花费平均到对每一个元素上的平均代价,称为摊还代价:T(n)/n
栈操作和二进制计数器递增在操作互相影响的情况下计算摊还代价能够得到比只分析单一操作的更紧确的上界。
17.2 核算法
栈操作的PUSH操作和INCREMENT的SET动作的花费设置包含其他动作的费用,把其摊还代价设为2。便能够保证信用为非负值。从而得到T(n)值。
17.3 势能法
对比于核算法的“信用”的概念,势能法从该数据结构的总体上的某个指标去考虑操作的代价,而核算法更加注重考虑摸个操作上保留信用来覆盖其他操作的花费。
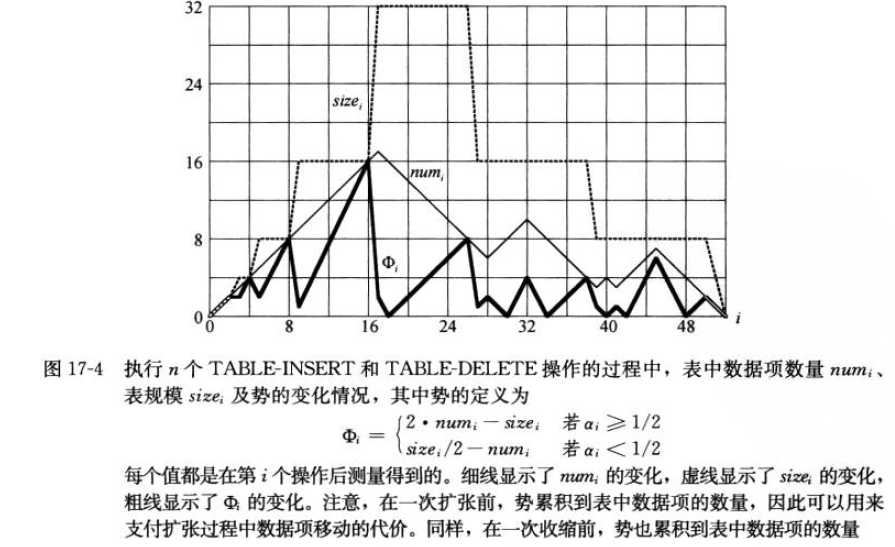
17.4 动态表
运用摊还分析方法来分析表的扩张和收缩,可以发现扩张和收缩的代价比较高,但是其摊还代价为O(1)。
对于表扩张,当超出时扩张两倍的大小,则问题变为练习17.1_3,但对于删除元素若元素小于1/2时,收缩表在最坏情况下n个操作的总代价为theta(n^2),摊还代价为theta(n)(从核算法的角度看,扩张后插入元素的信用不足以支付收缩表操作中元素的费用)。我们修改收缩策略为删除至1/4num,并定义势函数如下:

























 3545
3545











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








