首先确保硬件上有贴efuse的相关部分电路,给efuse供电:
1 、RK312X 需要使用治具,EFUSE 需要单独供电才能烧录
2 、RK3288 PCBA 上已经有 EFUSE 已经有供电,烧录软件会自动控制,不需要单独供电
3 、批量烧录前先烧录一台机器,然后用量产工具升级完整固件,确认所有功能正常后再
开始批量烧录
注:我这里验证使用的rk3399的板子,这部分的电路需要贴上,才可以烧写efuse成功,否则会提示烧写efuse失败。
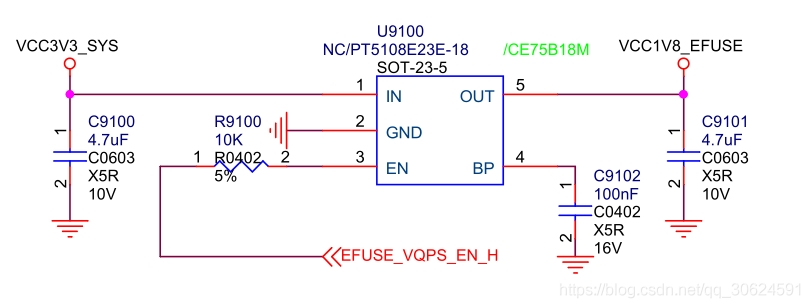
1、使用SecureBootTool.exe工具生成 RSA KEY(privateKey.bin和publicKey.bin文件),这里rk3399使用的是SecureBootTool v1.85版本,每款机器只生成一次,因此要特别注意保存好,以后签名都只用这对 KEY,建议最好再备份一次,避免丢失,目前做法是保存在SDK代码device/rockchip/rk3399/中。
2、secure boot固件要求:固件要求 boot.img 和 和 recovery.img 都需要包含 kernel.img,即SDK自动编译脚本build.sh需要添加语句:./mkimage.sh ota,加在make otapackage -j4之后。
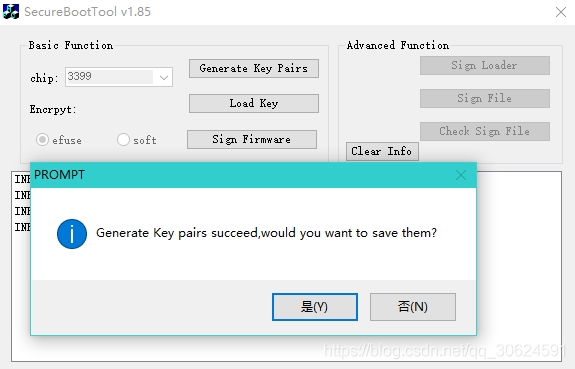
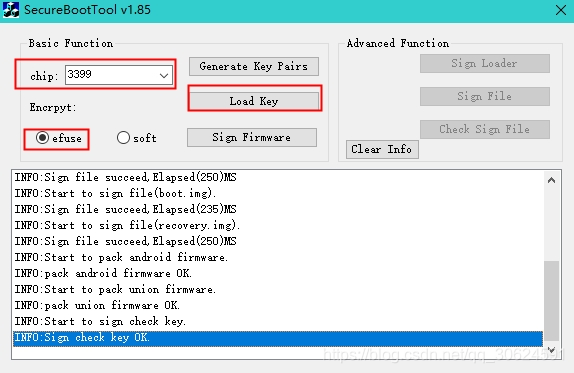
3、固件签名:使用SecureBootTool.exe工具进行固件签名,Load key加载1生成的 RSA KEY(privateKey.bin和publicKey.bin文件),然后Sign Firmware加载要签名的固件update.img,签名成功会在out目录生成update_sign.img。
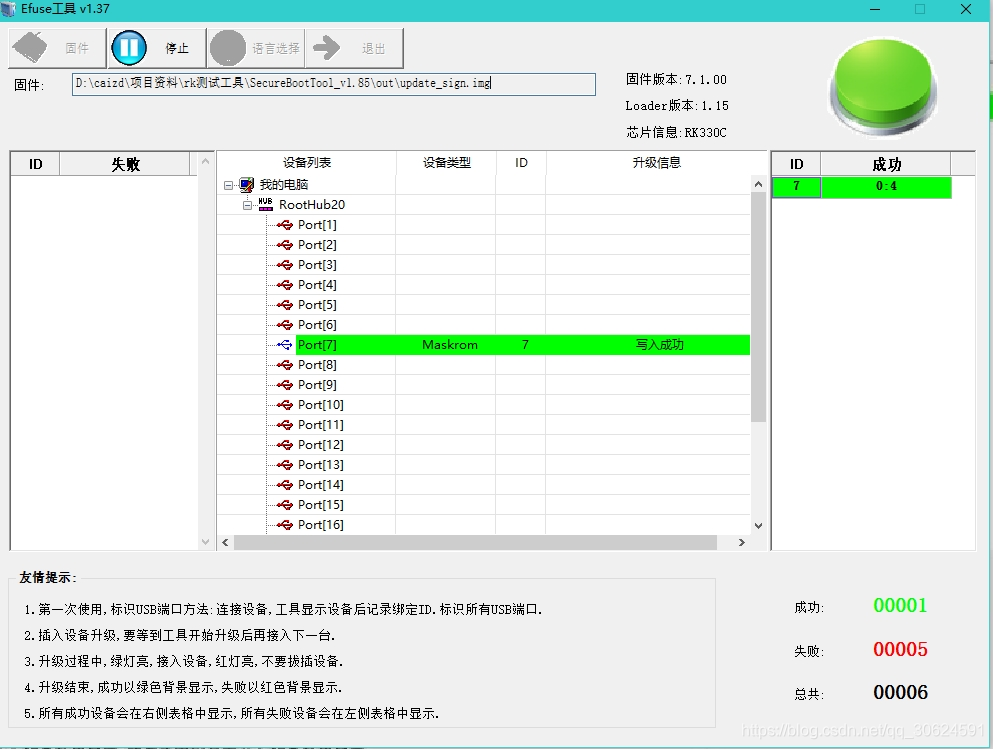
4、使用EfuseTool.exe工具【我这里的版本是efuse_v1.37,这个工具界面跟量产工厂工具的烧录工具有点像,注意不要搞错】烧录efuse到板子,加载的是2生成的签名固件update_sign.img,注意是在maskrom模式下烧录efuse(未烧录固件的新板子上电就是maskrom模式或者短接flash/emmc就会进maskrom模式),烧写成功则出现如下图所示,写入成功。对应log如下:
powerOn 81802
gCBW.Len = 100 gCBW.LBA = 0
gCBW.Len = 100 FW_DataLenCnt= 100
EfuseWriteData 0 100 3104240 0
write efuse: 0000000003104240 + 0x0:0x00,0x00,0x01,0x01,0x00,0x00,0x01,0x00,0x00,0x01,0x01,0x01,0x01,0x00,0x01,0x00,
write efuse: 0000000003104240 + 0x10:0x00,0x01,0x00,0x00,0x00,0x01,0x01,0x01,0x00,0x01,0x01,0x01,0x01,0x00,0x01,0x00,
write efuse: 0000000003104240 + 0x20:0x01,0x00,0x01,0x01,0x01,0x00,0x00,0x01,0x00,0x01,0x00,0x00,0x01,0x00,0x01,0x01,
write efuse: 0000000003104240 + 0x30:0x00,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x01,0x01,0x00,0x00,0x00,0x00,0x01,0x00,
write efuse: 0000000003104240 + 0x40:0x00,0x00,0x00,0x01,0x00,0x01,0x01,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x01,0x01,
write efuse: 0000000003104240 + 0x50:0x01,0x01,0x00,0x01,0x01,0x00,0x00,0x01,0x00,0x01,0x01,0x00,0x00,0x01,0x00,0x01,
write efuse: 0000000003104240 + 0x60:0x00,0x01,0x01,0x00,0x01,0x00,0x00,0x01,0x01,0x00,0x00,0x00,0x01,0x00,0x01,0x01,
write efuse: 0000000003104240 + 0x70:0x00,0x01,0x00,0x01,0x00,0x01,0x01,0x00,0x00,0x01,0x01,0x00,0x01,0x00,0x00,0x01,
write efuse: 0000000003104240 + 0x80:0x00,0x01,0x01,0x01,0x00,0x00,0x00,0x00,0x01,0x00,0x01,0x01,0x00,0x00,0x01,0x00,
write efuse: 0000000003104240 + 0x90:0x01,0x00,0x01,0x00,0x00,0x00,0x01,0x01,0x00,0x00,0x00,0x01,0x00,0x01,0x01,0x00,
write efuse: 0000000003104240 + 0xa0:0x01,0x00,0x00,0x01,0x00,0x01,0x01,0x00,0x00,0x00,0x01,0x01,0x00,0x01,0x01,0x01,
write efuse: 0000000003104240 + 0xb0:0x00,0x00,0x00,0x01,0x00,0x00,0x01,0x01,0x00,0x00,0x01,0x01,0x01,0x01,0x01,0x00,
write efuse: 0000000003104240 + 0xc0:0x01,0x01,0x01,0x00,0x00,0x00,0x01,0x00,0x01,0x00,0x00,0x00,0x01,0x01,0x01,0x01,
write efuse: 0000000003104240 + 0xd0:0x01,0x01,0x01,0x01,0x00,0x00,0x00,0x00,0x00,0x01,0x01,0x01,0x01,0x01,0x01,0x01,
write efuse: 0000000003104240 + 0xe0:0x01,0x01,0x01,0x00,0x00,0x01,0x01,0x01,0x01,0x01,0x01,0x01,0x00,0x00,0x01,0x01,
write efuse: 0000000003104240 + 0xf0:0x00,0x01,0x00,0x00,0x01,0x01,0x01,0x01,0x01,0x00,0x00,0x00,0x00,0x01,0x00,0x00,
EfuseReadData 100 100 325dc2c 1
efuse1: 0000000003114b28 + 0x0:0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,
efuse1: 0000000003114b28 + 0x40:0x089d35ac,0x720ee15f,0xec7c018d,0x2681f4d9,0x0c7e1cfb,0x2c5465a4,0x00000011,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,
EfuseReadData 100 100 325dc2c 1
efuse1: 0000000003114b28 + 0x0:0x00000001,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x5ee25e4c,0x4308d29d,0xa69bc168,0x966ad196,0x68c54d0e,0x7cc8ec69,0xfe0ff147,0x21f2cfe7,
efuse1: 0000000003114b28 + 0x40:0x089d35ac,0x720ee15f,0xec7c018d,0x2681f4d9,0x0c7e1cfb,0x2c5465a4,0x00000011,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,
enable secure
EfuseReadData 0 100 3100040 0
efuse1: 0000000003114b28 + 0x0:0x000000ff,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x5ee25e4c,0x4308d29d,0xa69bc168,0x966ad196,0x68c54d0e,0x7cc8ec69,0xfe0ff147,0x21f2cfe7,
efuse1: 0000000003114b28 + 0x40:0x089d35ac,0x720ee15f,0xec7c018d,0x2681f4d9,0x0c7e1cfb,0x2c5465a4,0x00000011,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,
enable secure
EfuseReadData 0 100 3100040 0
efuse1: 0000000003114b28 + 0x0:0x000000ff,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x5ee25e4c,0x4308d29d,0xa69bc168,0x966ad196,0x68c54d0e,0x7cc8ec69,0xfe0ff147,0x21f2cfe7,
efuse1: 0000000003114b28 + 0x40:0x089d35ac,0x720ee15f,0xec7c018d,0x2681f4d9,0x0c7e1cfb,0x2c5465a4,0x00000011,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,0x00000000,
5、然后使用FactoryTool_v1.66工具,升级签名固件。
6、验证结果:
6.1使用串口工具(如SecureCRT)抓取log。有以下打印表示安全启动:
Secure Boot find rsa key in ram.
Secure Boot Mode: 0x1
SecureBootEn = 1, SecureBootLock = 1
6.2设备已编程eFuse将启用安全启动rom,无法从未签名的固件启动。
因此,尝试升级未签名固件或不匹配的密钥签名固件将会失败;
升级匹配的签名固件将引导成功。
























 420
420











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










