文章目录
- helm
- 创建用户并添加到sudo名单
- name: nginx-ingress
- Timeout in milliseconds which the Ingress Controller will wait for a successful NGINX reload after a change or at the initial start.
- Default is 4000 (default is 20000 instead if enable-app-protect is true)
- If set to 0, default values will be used.
- Support for App Protect
- Enables the Ingress controller pods to use the host's network namespace.
- Enables debugging for NGINX. Uses the nginx-debug binary. Requires error-log-level: debug in the ConfigMap via `controller.config.entries`.
- The log level of the Ingress Controller.
- A list of custom ports to expose on the NGINX ingress controller pod. Follows the conventional Kubernetes yaml syntax for container ports.
- It is recommended to use your own TLS certificates and keys
- The node selector for pod assignment for the Ingress controller pods.
- The termination grace period of the Ingress controller pod.
- The resources of the Ingress controller pods.
- The tolerations of the Ingress controller pods.
- The affinity of the Ingress controller pods.
- The volumes of the Ingress controller pods.
- - name: extra-conf
- configMap:
- name: extra-conf
- - name: extra-conf
- mountPath: /etc/nginx/conf.d/extra.conf
- subPath: extra.conf
- The number of replicas of the Ingress controller deployment.
- A class of the Ingress controller.
- For Kubernetes >= 1.18, a corresponding IngressClass resource with the name equal to the class must be deployed. Otherwise,
- the Ingress Controller will fail to start.
- The Ingress controller only processes resources that belong to its class - i.e. have the "ingressClassName" field resource equal to the class.
- For Kubernetes < 1.18, the Ingress Controller only processes resources that belong to its class -
- i.e have the annotation "kubernetes.io/ingress.class" (for Ingress resources)
- or field "ingressClassName" (for VirtualServer/VirtualServerRoute/TransportServer resources) equal to the class.
- Additionally, the Ingress Controller processes resources that do not have the class set,
- which can be disabled by setting the controller.useIngressClassOnly parameter to true.
- The Ingress Controller processes all the VirtualServer/VirtualServerRoute/TransportServer resources that do not have the "ingressClassName" field for all versions of kubernetes.
- For kubernetes versions >= 1.18 this flag will be IGNORED.
- Ignore Ingress resources without the "kubernetes.io/ingress.class" annotation
- Only for Kubernetes >= 1.18
- New Ingresses without an ingressClassName field specified will be assigned the class specified in `controller.ingressClass`.
- Namespace to watch for Ingress resources. By default the Ingress controller watches all namespaces.
- Enable the custom resources.
- Enable preview policies.
- Enable TLS Passthrough on port 443. Requires controller.enableCustomResources.
- Enable custom NGINX configuration snippets in VirtualServer, VirtualServerRoute and TransportServer resources.
- Add a location based on the value of health-status-uri to the default server. The location responds with the 200 status code for any request.
- Useful for external health-checking of the Ingress controller.
- Sets the URI of health status location in the default server. Requires controller.healthStatus.
- The PriorityClass of the ingress controller pods.
- Enable collection of latency metrics for upstreams. Requires prometheus.create.
- Configures RBAC.
- Expose NGINX or NGINX Plus metrics in the Prometheus format.
- Configures the port to scrape the metrics.
- Specifies the namespace/name of a Kubernetes TLS Secret which will be used to protect the Prometheus endpoint.
- Configures the HTTP scheme used.
user
SXUgQ8sxdl
export NODE_PORT= ( k u b e c t l g e t − − n a m e s p a c e d e f a u l t − o j s o n p a t h = " . s p e c . p o r t s [ 0 ] . n o d e P o r t " s e r v i c e s m y − w e b − t o m c a t ) e x p o r t N O D E I P = (kubectl get --namespace default -o jsonpath="{.spec.ports[0].nodePort}" services my-web-tomcat) export NODE_IP= (kubectlget−−namespacedefault−ojsonpath=".spec.ports[0].nodePort"servicesmy−web−tomcat)exportNODEIP=(kubectl get nodes --namespace default -o jsonpath="{.items[0].status.addresses[0].address}")
echo http:// N O D E I P : NODE_IP: NODEIP:NODE_PORT/
helm search repo tomcat
helm pull aliyuncs/tomcat --untar
helm install my-web tomcat --set service.type=NodePort --set persistence.enabled=false
查看端口:
kubectl get svc,services
helm
查看真实节点ip,使用nodeport暴露真实节点端口,这样外界/虚机,主机才能访问到k8s内的应用 ,好像容器会和宿主机做端口映射一样–port
kubectl get nodes -o wide
实时查看/追踪节点状态
kubectl get pods -w
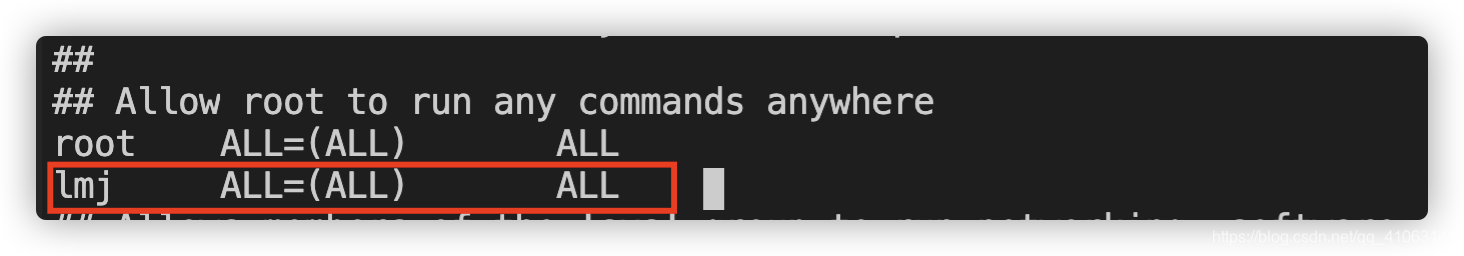
创建用户并添加到sudo名单
yum install vim -y
yum install tree -y
yum install lsof -y
yum install telnet -y
yum install wget -y
创建用户lmj
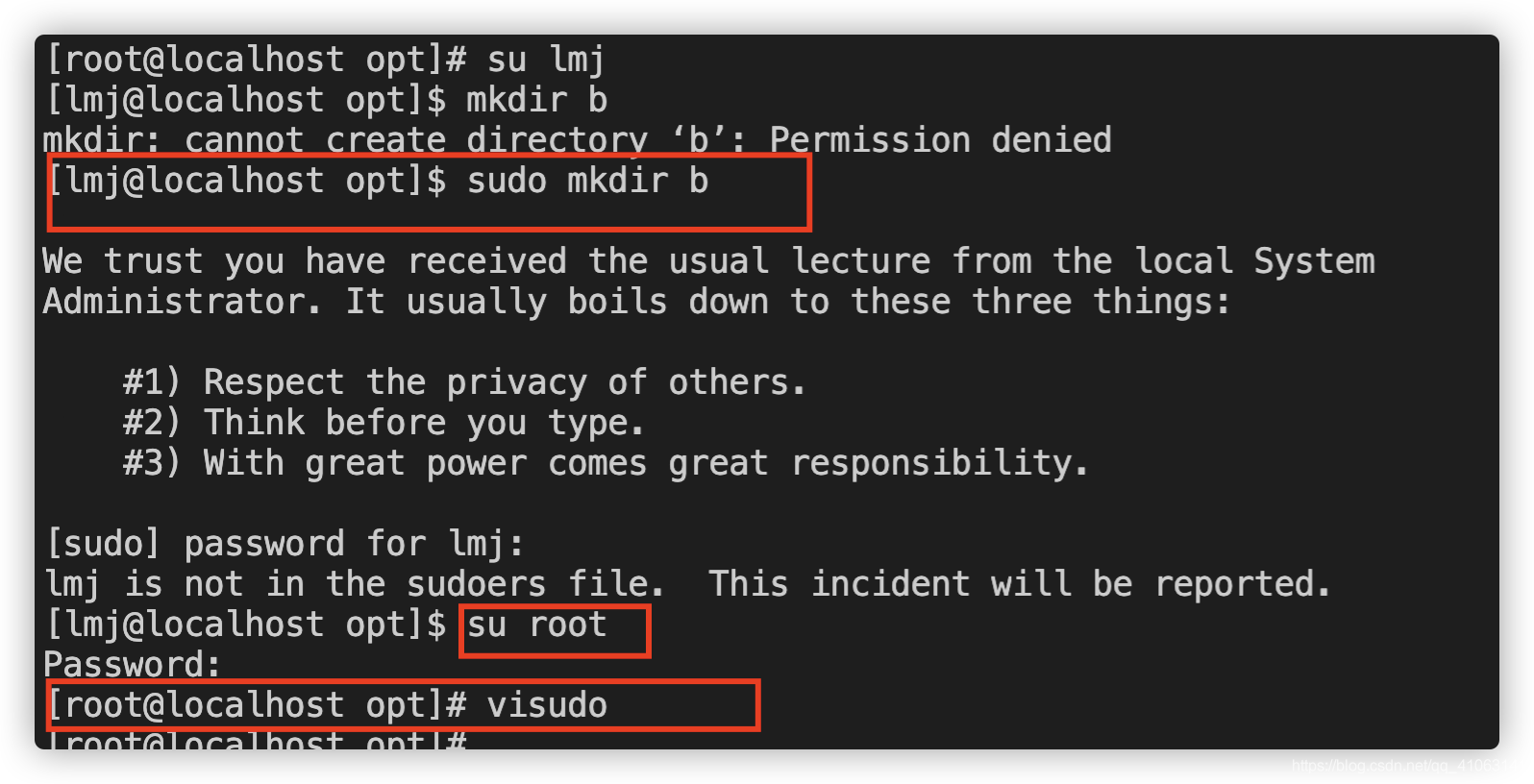
chmod 777 -R /opt
sb千万别chmod 777 -R / ,以及chown -R lmj:lmj / 一样命令下去系统直接崩溃了
rm -rf /opt/* 不要用rm -rf /opt/ 他会直接删除opt文件
系统初始化一些操作:(https://www.cnblogs.com/xyz349925756/p/14780638.html)
systemctl stop firewalld && systemctl disable firewalld
sed -i 's/enforcing/disabled/' /etc/selinux/config
sed -ri 's/.*swap.*/#&/' /etc/fstab
swapoff -a
添加内核桥接参数
cat > /etc/sysctl.d/k8s.conf << EOF
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
EOF
时区日期同步
yum install ntpdate -y
ntpdate time.windows.com
cp /usr/share/zoneinfo/Asia/Shanghai /etc/localtime
安装docker-ce
yum install -y yum-utils \
device-mapper-persistent-data \
lvm2
yum-config-manager \
--add-repo \
https://download.docker.com/linux/centos/docker-ce.repo
yum install docker-ce -y
systemctl start docker
curl -LO https://dl.k8s.io/release/v1.22.0/bin/linux/amd64/kubectl
sudo install -o root -g root -m 0755 kubectl /usr/local/bin/kubectl
kubectl version
curl -LO https://storage.googleapis.com/minikube/releases/latest/minikube-linux-amd64
sudo install minikube-linux-amd64 /usr/local/bin/minikube
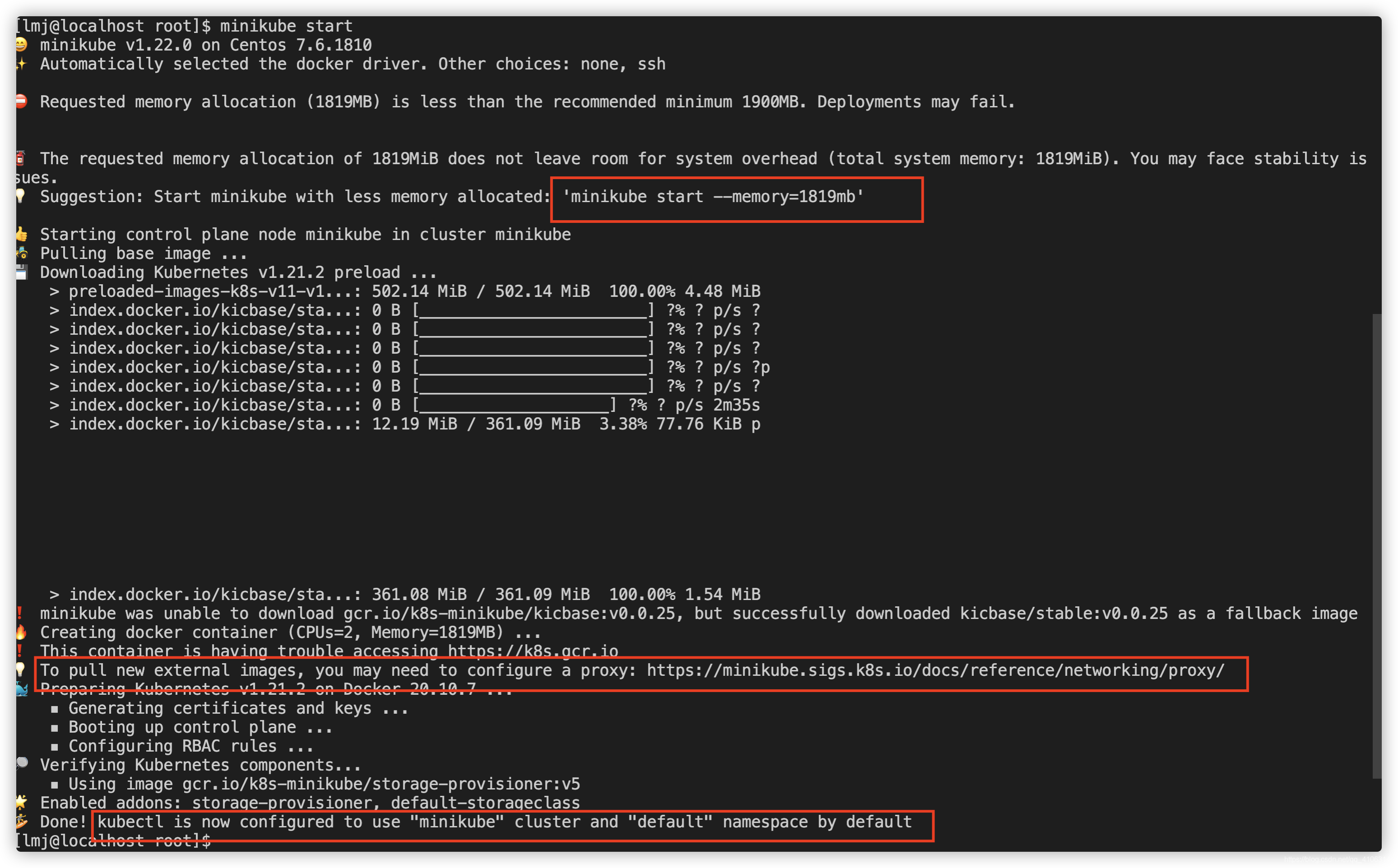
su lmj
sudo usermod -aG docker $USER && newgrp docker
minikube start --memory=1819mb
这一步需要等个5分钟样子
helm3安装
wget https://get.helm.sh/helm-v3.5.3-linux-amd64.tar.gz
tar zxf helm-v3.5.3-linux-amd64.tar.gz
cp linux-amd64/helm /usr/local/bin/
helm version
helm repo add nginx-stable https://helm.nginx.com/stable
helm search repo nginx-ingress
helm show values nginx-stable/nginx-ingress
helm install gateway nginx-stable/nginx-ingress
–set controller.service.type=NodePort
–set controller.service.httpPort.nodePort=30080
–set controller.service.httpsPort.nodePort=30443
💡 Suggestion: Start minikube with less memory allocated: ‘minikube start --memory=1819mb’
👍 Starting control plane node minikube in cluster minikube
🚜 Pulling base image …
💾 Downloading Kubernetes v1.21.2 preload …
> preloaded-images-k8s-v11-v1…: 502.14 MiB / 502.14 MiB 100.00% 4.48 MiB
> index.docker.io/kicbase/sta…: 0 B [________________________] ?% ? p/s ?
> index.docker.io/kicbase/sta…: 0 B [________________________] ?% ? p/s ?
> index.docker.io/kicbase/sta…: 0 B [________________________] ?% ? p/s ?
> index.docker.io/kicbase/sta…: 0 B [________________________] ?% ? p/s ?p
> index.docker.io/kicbase/sta…: 0 B [____] ?% ? p/s ?
> index.docker.io/kicbase/sta…: 0 B [] ?% ? p/s 2m35s
> index.docker.io/kicbase/sta…: 12.19 MiB / 361.09 MiB 3.38% 77.76 KiB p
> index.docker.io/kicbase/sta...: 361.08 MiB / 361.09 MiB 100.00% 1.54 MiB
❗ minikube was unable to download gcr.io/k8s-minikube/kicbase:v0.0.25, but successfully downloaded kicbase/stable:v0.0.25 as a fallback image
🔥 Creating docker container (CPUs=2, Memory=1819MB) …
❗ This container is having trouble accessing https://k8s.gcr.io
💡 To pull new external images, you may need to configure a proxy: https://minikube.sigs.k8s.io/docs/reference/networking/proxy/
🐳 Preparing Kubernetes v1.21.2 on Docker 20.10.7 …
▪ Generating certificates and keys …
▪ Booting up control plane …
▪ Configuring RBAC rules …
🔎 Verifying Kubernetes components…
▪ Using image gcr.io/k8s-minikube/storage-provisioner:v5
🌟 Enabled addons: storage-provisioner, default-storageclass
🏄 Done! kubectl is now configured to use “minikube” cluster and “default” namespace by default
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$ p
bash: p: command not found
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$ helm repo add nginx-stable https://helm.nginx.com/stable
“nginx-stable” has been added to your repositories
[lmj@localhost root]$
[lmj@localhost root]$ helm search repo nginx-ingress
NAME CHART VERSION APP VERSION DESCRIPTION
nginx-stable/nginx-ingress 0.10.0 1.12.0 NGINX Ingress Controller
[lmj@localhost root]$
[lmj@localhost root]$ helm show values nginx-stable/nginx-ingress
controller:
The name of the Ingress controller daemonset or deployment.
Autogenerated if not set or set to “”.
name: nginx-ingress
The kind of the Ingress controller installation - deployment or daemonset.
kind: deployment
Deploys the Ingress controller for NGINX Plus.
nginxplus: false
Timeout in milliseconds which the Ingress Controller will wait for a successful NGINX reload after a change or at the initial start.
Default is 4000 (default is 20000 instead if enable-app-protect is true)
If set to 0, default values will be used.
nginxReloadTimeout: 0
Support for App Protect
appprotect:
## Enable the App Protect module in the Ingress Controller.
enable: false
Enables the Ingress controller pods to use the host’s network namespace.
hostNetwork: false
Enables debugging for NGINX. Uses the nginx-debug binary. Requires error-log-level: debug in the ConfigMap via controller.config.entries.
nginxDebug: false
The log level of the Ingress Controller.
logLevel: 1
A list of custom ports to expose on the NGINX ingress controller pod. Follows the conventional Kubernetes yaml syntax for container ports.
customPorts: []
image:
## The image repository of the Ingress controller.
repository: nginx/nginx-ingress
## The tag of the Ingress controller image.
tag: "1.12.0"
## The pull policy for the Ingress controller image.
pullPolicy: IfNotPresent
config:
## The name of the ConfigMap used by the Ingress controller.
## Autogenerated if not set or set to “”.
# name: nginx-config
## The annotations of the Ingress Controller configmap.
annotations: {}
## The entries of the ConfigMap for customizing NGINX configuration.
entries: {}
It is recommended to use your own TLS certificates and keys
defaultTLS:
## The base64-encoded TLS certificate for the default HTTPS server. If not specified, a pre-generated self-signed certificate is used.
## Note: It is recommended that you specify your own certificate.
cert: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN2akNDQWFZQ0NRREFPRjl0THNhWFhEQU5CZ2txaGtpRzl3MEJBUXNGQURBaE1SOHdIUVlEVlFRRERCWk8KUjBsT1dFbHVaM0psYzNORGIyNTBjbTlzYkdWeU1CNFhEVEU0TURreE1qRTRNRE16TlZvWERUSXpNRGt4TVRFNApNRE16TlZvd0lURWZNQjBHQTFVRUF3d1dUa2RKVGxoSmJtZHlaWE56UTI5dWRISnZiR3hsY2pDQ0FTSXdEUVlKCktvWklodmNOQVFFQkJRQURnZ0VQQURDQ0FRb0NnZ0VCQUwvN2hIUEtFWGRMdjNyaUM3QlBrMTNpWkt5eTlyQ08KR2xZUXYyK2EzUDF0azIrS3YwVGF5aGRCbDRrcnNUcTZzZm8vWUk1Y2Vhbkw4WGM3U1pyQkVRYm9EN2REbWs1Qgo4eDZLS2xHWU5IWlg0Rm5UZ0VPaStlM2ptTFFxRlBSY1kzVnNPazFFeUZBL0JnWlJVbkNHZUtGeERSN0tQdGhyCmtqSXVuektURXUyaDU4Tlp0S21ScUJHdDEwcTNRYzhZT3ExM2FnbmovUWRjc0ZYYTJnMjB1K1lYZDdoZ3krZksKWk4vVUkxQUQ0YzZyM1lma1ZWUmVHd1lxQVp1WXN2V0RKbW1GNWRwdEMzN011cDBPRUxVTExSakZJOTZXNXIwSAo1TmdPc25NWFJNV1hYVlpiNWRxT3R0SmRtS3FhZ25TZ1JQQVpQN2MwQjFQU2FqYzZjNGZRVXpNQ0F3RUFBVEFOCkJna3Foa2lHOXcwQkFRc0ZBQU9DQVFFQWpLb2tRdGRPcEsrTzhibWVPc3lySmdJSXJycVFVY2ZOUitjb0hZVUoKdGhrYnhITFMzR3VBTWI5dm15VExPY2xxeC9aYzJPblEwMEJCLzlTb0swcitFZ1U2UlVrRWtWcitTTFA3NTdUWgozZWI4dmdPdEduMS9ienM3bzNBaS9kclkrcUI5Q2k1S3lPc3FHTG1US2xFaUtOYkcyR1ZyTWxjS0ZYQU80YTY3Cklnc1hzYktNbTQwV1U3cG9mcGltU1ZmaXFSdkV5YmN3N0NYODF6cFErUyt1eHRYK2VBZ3V0NHh3VlI5d2IyVXYKelhuZk9HbWhWNThDd1dIQnNKa0kxNXhaa2VUWXdSN0diaEFMSkZUUkk3dkhvQXprTWIzbjAxQjQyWjNrN3RXNQpJUDFmTlpIOFUvOWxiUHNoT21FRFZkdjF5ZytVRVJxbStGSis2R0oxeFJGcGZnPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
## The base64-encoded TLS key for the default HTTPS server. Note: If not specified, a pre-generated key is used.
## Note: It is recommended that you specify your own key.
key: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBdi91RWM4b1JkMHUvZXVJTHNFK1RYZUprckxMMnNJNGFWaEMvYjVyYy9XMlRiNHEvClJOcktGMEdYaVN1eE9ycXgrajlnamx4NXFjdnhkenRKbXNFUkJ1Z1B0ME9hVGtIekhvb3FVWmcwZGxmZ1dkT0EKUTZMNTdlT1l0Q29VOUZ4amRXdzZUVVRJVUQ4R0JsRlNjSVo0b1hFTkhzbysyR3VTTWk2Zk1wTVM3YUhudzFtMApxWkdvRWEzWFNyZEJ6eGc2clhkcUNlUDlCMXl3VmRyYURiUzc1aGQzdUdETDU4cGszOVFqVUFQaHpxdmRoK1JWClZGNGJCaW9CbTVpeTlZTW1hWVhsMm0wTGZzeTZuUTRRdFFzdEdNVWozcGJtdlFmazJBNnljeGRFeFpkZFZsdmwKMm82MjBsMllxcHFDZEtCRThCay90elFIVTlKcU56cHpoOUJUTXdJREFRQUJBb0lCQVFDZklHbXowOHhRVmorNwpLZnZJUXQwQ0YzR2MxNld6eDhVNml4MHg4Mm15d1kxUUNlL3BzWE9LZlRxT1h1SENyUlp5TnUvZ2IvUUQ4bUFOCmxOMjRZTWl0TWRJODg5TEZoTkp3QU5OODJDeTczckM5bzVvUDlkazAvYzRIbjAzSkVYNzZ5QjgzQm9rR1FvYksKMjhMNk0rdHUzUmFqNjd6Vmc2d2szaEhrU0pXSzBwV1YrSjdrUkRWYmhDYUZhNk5nMUZNRWxhTlozVDhhUUtyQgpDUDNDeEFTdjYxWTk5TEI4KzNXWVFIK3NYaTVGM01pYVNBZ1BkQUk3WEh1dXFET1lvMU5PL0JoSGt1aVg2QnRtCnorNTZud2pZMy8yUytSRmNBc3JMTnIwMDJZZi9oY0IraVlDNzVWYmcydVd6WTY3TWdOTGQ5VW9RU3BDRkYrVm4KM0cyUnhybnhBb0dCQU40U3M0ZVlPU2huMVpQQjdhTUZsY0k2RHR2S2ErTGZTTXFyY2pOZjJlSEpZNnhubmxKdgpGenpGL2RiVWVTbWxSekR0WkdlcXZXaHFISy9iTjIyeWJhOU1WMDlRQ0JFTk5jNmtWajJTVHpUWkJVbEx4QzYrCk93Z0wyZHhKendWelU0VC84ajdHalRUN05BZVpFS2FvRHFyRG5BYWkyaW5oZU1JVWZHRXFGKzJyQW9HQkFOMVAKK0tZL0lsS3RWRzRKSklQNzBjUis3RmpyeXJpY05iWCtQVzUvOXFHaWxnY2grZ3l4b25BWlBpd2NpeDN3QVpGdwpaZC96ZFB2aTBkWEppc1BSZjRMazg5b2pCUmpiRmRmc2l5UmJYbyt3TFU4NUhRU2NGMnN5aUFPaTVBRHdVU0FkCm45YWFweUNweEFkREtERHdObit3ZFhtaTZ0OHRpSFRkK3RoVDhkaVpBb0dCQUt6Wis1bG9OOTBtYlF4VVh5YUwKMjFSUm9tMGJjcndsTmVCaWNFSmlzaEhYa2xpSVVxZ3hSZklNM2hhUVRUcklKZENFaHFsV01aV0xPb2I2NTNyZgo3aFlMSXM1ZUtka3o0aFRVdnpldm9TMHVXcm9CV2xOVHlGanIrSWhKZnZUc0hpOGdsU3FkbXgySkJhZUFVWUNXCndNdlQ4NmNLclNyNkQrZG8wS05FZzFsL0FvR0FlMkFVdHVFbFNqLzBmRzgrV3hHc1RFV1JqclRNUzRSUjhRWXQKeXdjdFA4aDZxTGxKUTRCWGxQU05rMXZLTmtOUkxIb2pZT2pCQTViYjhibXNVU1BlV09NNENoaFJ4QnlHbmR2eAphYkJDRkFwY0IvbEg4d1R0alVZYlN5T294ZGt5OEp0ek90ajJhS0FiZHd6NlArWDZDODhjZmxYVFo5MWpYL3RMCjF3TmRKS2tDZ1lCbyt0UzB5TzJ2SWFmK2UwSkN5TGhzVDQ5cTN3Zis2QWVqWGx2WDJ1VnRYejN5QTZnbXo5aCsKcDNlK2JMRUxwb3B0WFhNdUFRR0xhUkcrYlNNcjR5dERYbE5ZSndUeThXczNKY3dlSTdqZVp2b0ZpbmNvVlVIMwphdmxoTUVCRGYxSjltSDB5cDBwWUNaS2ROdHNvZEZtQktzVEtQMjJhTmtsVVhCS3gyZzR6cFE9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
## The secret with a TLS certificate and key for the default HTTPS server.
## The value must follow the following format: `<namespace>/<name>`.
## Used as an alternative to specifying a certificate and key using `controller.defaultTLS.cert` and `controller.defaultTLS.key` parameters.
## Format: <namespace>/<secret_name>
secret:
wildcardTLS:
## The base64-encoded TLS certificate for every Ingress host that has TLS enabled but no secret specified.
## If the parameter is not set, for such Ingress hosts NGINX will break any attempt to establish a TLS connection.
cert: “”
## The base64-encoded TLS key for every Ingress host that has TLS enabled but no secret specified.
## If the parameter is not set, for such Ingress hosts NGINX will break any attempt to establish a TLS connection.
key: ""
## The secret with a TLS certificate and key for every Ingress host that has TLS enabled but no secret specified.
## The value must follow the following format: `<namespace>/<name>`.
## Used as an alternative to specifying a certificate and key using `controller.wildcardTLS.cert` and `controller.wildcardTLS.key` parameters.
## Format: <namespace>/<secret_name>
secret:
The node selector for pod assignment for the Ingress controller pods.
nodeSelector: {}
The termination grace period of the Ingress controller pod.
terminationGracePeriodSeconds: 30
The resources of the Ingress controller pods.
resources: {}
# limits:
# cpu: 100m
# memory: 64Mi
# requests:
# cpu: 100m
# memory: 64Mi
The tolerations of the Ingress controller pods.
tolerations: []
The affinity of the Ingress controller pods.
affinity: {}
The volumes of the Ingress controller pods.
volumes: []
- name: extra-conf
configMap:
name: extra-conf
The volumeMounts of the Ingress controller pods.
volumeMounts: []
- name: extra-conf
mountPath: /etc/nginx/conf.d/extra.conf
subPath: extra.conf
The number of replicas of the Ingress controller deployment.
replicaCount: 1
A class of the Ingress controller.
For Kubernetes >= 1.18, a corresponding IngressClass resource with the name equal to the class must be deployed. Otherwise,
the Ingress Controller will fail to start.
The Ingress controller only processes resources that belong to its class - i.e. have the “ingressClassName” field resource equal to the class.
For Kubernetes < 1.18, the Ingress Controller only processes resources that belong to its class -
i.e have the annotation “kubernetes.io/ingress.class” (for Ingress resources)
or field “ingressClassName” (for VirtualServer/VirtualServerRoute/TransportServer resources) equal to the class.
Additionally, the Ingress Controller processes resources that do not have the class set,
which can be disabled by setting the controller.useIngressClassOnly parameter to true.
The Ingress Controller processes all the VirtualServer/VirtualServerRoute/TransportServer resources that do not have the “ingressClassName” field for all versions of kubernetes.
ingressClass: nginx
For kubernetes versions >= 1.18 this flag will be IGNORED.
Ignore Ingress resources without the “kubernetes.io/ingress.class” annotation
useIngressClassOnly: false
Only for Kubernetes >= 1.18
New Ingresses without an ingressClassName field specified will be assigned the class specified in controller.ingressClass.
setAsDefaultIngress: false
Namespace to watch for Ingress resources. By default the Ingress controller watches all namespaces.
watchNamespace: “”
Enable the custom resources.
enableCustomResources: true
Enable preview policies.
enablePreviewPolicies: false
Enable TLS Passthrough on port 443. Requires controller.enableCustomResources.
enableTLSPassthrough: false
globalConfiguration:
## Creates the GlobalConfiguration custom resource. Requires controller.enableCustomResources.
create: false
## The spec of the GlobalConfiguration for defining the global configuration parameters of the Ingress Controller.
spec: {}
# listeners:
# - name: dns-udp
# port: 5353
# protocol: UDP
# - name: dns-tcp
# port: 5353
# protocol: TCP
Enable custom NGINX configuration snippets in VirtualServer, VirtualServerRoute and TransportServer resources.
enableSnippets: false
Add a location based on the value of health-status-uri to the default server. The location responds with the 200 status code for any request.
Useful for external health-checking of the Ingress controller.
healthStatus: false
Sets the URI of health status location in the default server. Requires controller.healthStatus.
healthStatusURI: “/nginx-health”
nginxStatus:
## Enable the NGINX stub_status, or the NGINX Plus API.
enable: true
## Set the port where the NGINX stub_status or the NGINX Plus API is exposed.
port: 8080
## Add IPv4 IP/CIDR blocks to the allow list for NGINX stub_status or the NGINX Plus API. Separate multiple IP/CIDR by commas.
allowCidrs: "127.0.0.1"
service:
## Creates a service to expose the Ingress controller pods.
create: true
## The type of service to create for the Ingress controller.
type: LoadBalancer
## The externalTrafficPolicy of the service. The value Local preserves the client source IP.
externalTrafficPolicy: Local
## The annotations of the Ingress controller service.
annotations: {}
## The extra labels of the service.
extraLabels: {}
## The static IP address for the load balancer. Requires controller.service.type set to LoadBalancer. The cloud provider must support this feature.
loadBalancerIP: ""
## The list of external IPs for the Ingress controller service.
externalIPs: []
## The IP ranges (CIDR) that are allowed to access the load balancer. Requires controller.service.type set to LoadBalancer. The cloud provider must support this feature.
loadBalancerSourceRanges: []
## The name of the service
## Autogenerated if not set or set to "".
# name: nginx-ingress
httpPort:
## Enables the HTTP port for the Ingress controller service.
enable: true
## The HTTP port of the Ingress controller service.
port: 80
## The custom NodePort for the HTTP port. Requires controller.service.type set to NodePort.
nodePort: ""
## The HTTP port on the POD where the Ingress controller service is running.
targetPort: 80
httpsPort:
## Enables the HTTPS port for the Ingress controller service.
enable: true
## The HTTPS port of the Ingress controller service.
port: 443
## The custom NodePort for the HTTPS port. Requires controller.service.type set to NodePort.
nodePort: ""
## The HTTPS port on the POD where the Ingress controller service is running.
targetPort: 443
## A list of custom ports to expose through the Ingress controller service. Follows the conventional Kubernetes yaml syntax for service ports.
customPorts: []
serviceAccount:
## The name of the service account of the Ingress controller pods. Used for RBAC.
## Autogenerated if not set or set to “”.
# name: nginx-ingress
## The name of the secret containing docker registry credentials.
## Secret must exist in the same namespace as the helm release.
imagePullSecretName: ""
reportIngressStatus:
## Updates the address field in the status of Ingress resources with an external address of the Ingress controller.
## You must also specify the source of the external address either through an external service via controller.reportIngressStatus.externalService,
## controller.reportIngressStatus.ingressLink or the external-status-address entry in the ConfigMap via controller.config.entries.
## Note: controller.config.entries.external-status-address takes precedence over the others.
enable: true
## Specifies the name of the service with the type LoadBalancer through which the Ingress controller is exposed externally.
## The external address of the service is used when reporting the status of Ingress, VirtualServer and VirtualServerRoute resources.
## controller.reportIngressStatus.enable must be set to true.
## The default is autogenerated and matches the created service (see controller.service.create).
# externalService: nginx-ingress
## Specifies the name of the IngressLink resource, which exposes the Ingress Controller pods via a BIG-IP system.
## The IP of the BIG-IP system is used when reporting the status of Ingress, VirtualServer and VirtualServerRoute resources.
## controller.reportIngressStatus.enable must be set to true.
ingressLink: ""
## Enable Leader election to avoid multiple replicas of the controller reporting the status of Ingress resources. controller.reportIngressStatus.enable must be set to true.
enableLeaderElection: true
## Specifies the name of the ConfigMap, within the same namespace as the controller, used as the lock for leader election. controller.reportIngressStatus.enableLeaderElection must be set to true.
## Autogenerated if not set or set to "".
# leaderElectionLockName: "nginx-ingress-leader-election"
## The annotations of the leader election configmap.
annotations: {}
pod:
## The annotations of the Ingress Controller pod.
annotations: {}
The PriorityClass of the ingress controller pods.
priorityClassName:
readyStatus:
## Enables readiness endpoint “/nginx-ready”. The endpoint returns a success code when NGINX has loaded all the config after startup.
enable: true
## Set the port where the readiness endpoint is exposed.
port: 8081
Enable collection of latency metrics for upstreams. Requires prometheus.create.
enableLatencyMetrics: false
rbac:
Configures RBAC.
create: true
prometheus:
Expose NGINX or NGINX Plus metrics in the Prometheus format.
create: true
Configures the port to scrape the metrics.
port: 9113
Specifies the namespace/name of a Kubernetes TLS Secret which will be used to protect the Prometheus endpoint.
secret: “”
Configures the HTTP scheme used.
scheme: http
[lmj@localhost root]$
[lmj@localhost root]$ helm install gateway nginx-stable/nginx-ingress \
–set controller.service.type=NodePort
–set controller.service.httpPort.nodePort=30080
–set controller.service.httpsPort.nodePort=30443
W0822 12:13:08.656216 21469 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
W0822 12:13:08.847034 21469 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
NAME: gateway
LAST DEPLOYED: Sun Aug 22 12:13:08 2021
NAMESPACE: default
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
The NGINX Ingress Controller has been installed.
[lmj@localhost root]$ ————————————————
bash: ————————————————: command not found
[lmj@localhost root]$ 版权声明:本文为CSDN博主「twingao」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
bash: 版权声明:本文为CSDN博主「twingao」的原创文章,遵循CC: command not found
[lmj@localhost root]$ 原文链接:https://blog.csdn.net/twingao/article/details/105157724
bash: 原文链接:https://blog.csdn.net/twingao/article/details/105157724: No such file or directory
[lmj@localhost root]$
[lmj@localhost root]$ kubectl get all
NAME READY STATUS RESTARTS AGE
pod/gateway-nginx-ingress-7c57b6f5fc-trv4x 0/1 ContainerCreating 0 16s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/gateway-nginx-ingress NodePort 10.97.30.83 80:30080/TCP,443:30443/TCP 16s
service/kubernetes ClusterIP 10.96.0.1 443/TCP 3m26s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/gateway-nginx-ingress 0/1 1 0 16s
NAME DESIRED CURRENT READY AGE
replicaset.apps/gateway-nginx-ingress-7c57b6f5fc 1 1 0 16s
[lmj@localhost root]$ curl http://127.0.0.1:30080
curl: (7) Failed connect to 127.0.0.1:30080; Connection refused
[lmj@localhost root]$ curl http://10.97.30.83:30080
curl: (7) Failed connect to 10.97.30.83:30080; Connection refused
[lmj@localhost root]$ ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:93:6f:b4 brd ff:ff:ff:ff:ff:ff
inet 172.16.191.133/24 brd 172.16.191.255 scope global noprefixroute dynamic ens33
valid_lft 1612sec preferred_lft 1612sec
inet6 fe80::f793:bb08:c38c:9579/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:09:3e:d1:e7 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
inet6 fe80::42:9ff:fe3e:d1e7/64 scope link
valid_lft forever preferred_lft forever
4: br-7d1e728d36db: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:38:40:5d:7b brd ff:ff:ff:ff:ff:ff
inet 192.168.49.1/24 brd 192.168.49.255 scope global br-7d1e728d36db
valid_lft forever preferred_lft forever
inet6 fe80::42:38ff:fe40:5d7b/64 scope link
valid_lft forever preferred_lft forever
10: vethe2bf814@if9: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-7d1e728d36db state UP group default
link/ether 0a:4e:74:12:fa:1d brd ff:ff:ff:ff:ff:ff link-netnsid 1
inet6 fe80::84e:74ff:fe12:fa1d/64 scope link
valid_lft forever preferred_lft forever
[lmj@localhost root]$ curl http://172.16.191.133:30080
curl: (7) Failed connect to 172.16.191.133:30080; Connection refused
[lmj@localhost root]$
[lmj@localhost root]$ kubectl get all
NAME READY STATUS RESTARTS AGE
pod/gateway-nginx-ingress-7c57b6f5fc-trv4x 1/1 Running 0 2m4s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/gateway-nginx-ingress NodePort 10.97.30.83 80:30080/TCP,443:30443/TCP 2m4s
service/kubernetes ClusterIP 10.96.0.1 443/TCP 5m14s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/gateway-nginx-ingress 1/1 1 1 2m4s
NAME DESIRED CURRENT READY AGE
replicaset.apps/gateway-nginx-ingress-7c57b6f5fc 1 1 1 2m4s
[lmj@localhost root]$ kubectl get pods
NAME READY STATUS RESTARTS AGE
gateway-nginx-ingress-7c57b6f5fc-trv4x 1/1 Running 0 2m15s
[lmj@localhost root]$ kubectl logs gateway-nginx-ing
Error from server (NotFound): pods “gateway-nginx-ing” not found
[lmj@localhost root]$ kubectl logs gateway-nginx-ingress-7c57b6f5fc-trv4x
I0822 04:13:50.217374 1 main.go:271] Starting NGINX Ingress controller Version=1.12.0 GitCommit=c9d3618da566b158a53a6da098ff677aac28b7ff Date=2021-06-30T10:34:29Z PlusFlag=false
W0822 04:13:50.227354 1 main.go:310] The ‘-use-ingress-class-only’ flag will be deprecated and has no effect on versions of kubernetes >= 1.18.0. Processing ONLY resources that have the ‘ingressClassName’ field in Ingress equal to the class.
W0822 04:13:50.256028 1 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
I0822 04:13:50.263289 1 main.go:413] Using nginx version: nginx/1.21.0
2021/08/22 04:13:50 [notice] 12#12: using the “epoll” event method
2021/08/22 04:13:50 [notice] 12#12: nginx/1.21.0
2021/08/22 04:13:50 [notice] 12#12: built by gcc 8.3.0 (Debian 8.3.0-6)
2021/08/22 04:13:50 [notice] 12#12: OS: Linux 3.10.0-957.el7.x86_64
2021/08/22 04:13:50 [notice] 12#12: getrlimit(RLIMIT_NOFILE): 1048576:1048576
2021/08/22 04:13:50 [notice] 12#12: start worker processes
2021/08/22 04:13:50 [notice] 12#12: start worker process 13
2021/08/22 04:13:50 [notice] 12#12: start worker process 14
I0822 04:13:50.287960 1 listener.go:55] Starting Prometheus listener on: :9113/metrics
I0822 04:13:50.288142 1 leaderelection.go:243] attempting to acquire leader lease default/gateway-nginx-ingress-leader-election…
W0822 04:13:50.330744 1 warnings.go:70] networking.k8s.io/v1beta1 Ingress is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 Ingress
W0822 04:13:50.347487 1 warnings.go:70] networking.k8s.io/v1beta1 Ingress is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 Ingress
I0822 04:13:50.353369 1 leaderelection.go:253] successfully acquired lease default/gateway-nginx-ingress-leader-election
2021/08/22 04:13:50 [notice] 12#12: signal 1 (SIGHUP) received from 20, reconfiguring
2021/08/22 04:13:50 [notice] 12#12: reconfiguring
2021/08/22 04:13:50 [notice] 12#12: using the “epoll” event method
2021/08/22 04:13:50 [notice] 12#12: start worker processes
2021/08/22 04:13:50 [notice] 12#12: start worker process 21
2021/08/22 04:13:50 [notice] 12#12: start worker process 22
2021/08/22 04:13:50 [notice] 14#14: gracefully shutting down
2021/08/22 04:13:50 [notice] 13#13: gracefully shutting down
2021/08/22 04:13:50 [notice] 13#13: exiting
2021/08/22 04:13:50 [notice] 14#14: exiting
2021/08/22 04:13:50 [notice] 14#14: exit
2021/08/22 04:13:50 [notice] 13#13: exit
I0822 04:13:50.516418 1 event.go:282] Event(v1.ObjectReference{Kind:“ConfigMap”, Namespace:“default”, Name:“gateway-nginx-ingress”, UID:“ea7bbebf-b618-46bf-af0f-e9f90743d17e”, APIVersion:“v1”, ResourceVersion:“625”, FieldPath:""}): type: ‘Normal’ reason: ‘Updated’ Configuration from default/gateway-nginx-ingress was updated
2021/08/22 04:13:50 [notice] 12#12: signal 17 (SIGCHLD) received from 13
2021/08/22 04:13:50 [notice] 12#12: worker process 13 exited with code 0
2021/08/22 04:13:50 [notice] 12#12: signal 29 (SIGIO) received
2021/08/22 04:13:50 [notice] 12#12: signal 17 (SIGCHLD) received from 14
2021/08/22 04:13:50 [notice] 12#12: worker process 14 exited with code 0
2021/08/22 04:13:50 [notice] 12#12: signal 29 (SIGIO) received
2021/08/22 04:13:50 [notice] 12#12: signal 1 (SIGHUP) received from 24, reconfiguring
2021/08/22 04:13:50 [notice] 12#12: reconfiguring
2021/08/22 04:13:50 [notice] 12#12: using the “epoll” event method
2021/08/22 04:13:50 [notice] 12#12: start worker processes
2021/08/22 04:13:50 [notice] 12#12: start worker process 25
2021/08/22 04:13:50 [notice] 12#12: start worker process 26
2021/08/22 04:13:50 [notice] 22#22: gracefully shutting down
2021/08/22 04:13:50 [notice] 22#22: exiting
2021/08/22 04:13:50 [notice] 22#22: exit
2021/08/22 04:13:50 [notice] 21#21: gracefully shutting down
2021/08/22 04:13:50 [notice] 21#21: exiting
2021/08/22 04:13:50 [notice] 21#21: exit
I0822 04:13:50.629157 1 event.go:282] Event(v1.ObjectReference{Kind:“Secret”, Namespace:“default”, Name:“gateway-nginx-ingress-default-server-tls”, UID:“5665ae25-793b-4b58-bb80-37f842cf14ed”, APIVersion:“v1”, ResourceVersion:“623”, FieldPath:""}): type: ‘Normal’ reason: ‘Updated’ the special Secret default/gateway-nginx-ingress-default-server-tls was updated
2021/08/22 04:13:50 [notice] 12#12: signal 17 (SIGCHLD) received from 22
2021/08/22 04:13:50 [notice] 12#12: worker process 22 exited with code 0
2021/08/22 04:13:50 [notice] 12#12: signal 29 (SIGIO) received
2021/08/22 04:13:50 [notice] 12#12: signal 17 (SIGCHLD) received from 21
2021/08/22 04:13:50 [notice] 12#12: worker process 21 exited with code 0
2021/08/22 04:13:50 [notice] 12#12: signal 29 (SIGIO) received
[lmj@localhost root]$ lsof -i:30080
[lmj@localhost root]$ telnet localhost 30080
[lmj@localhost root]$ telnet localhost 80
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$
[lmj@localhost root]$ cd /opt/
[lmj@localhost opt]$ ls
containerd k8s
[lmj@localhost opt]$ cd k8s/
[lmj@localhost k8s]$ ls
package
[lmj@localhost k8s]$ mkdir app
[lmj@localhost k8s]$ cd app/
[lmj@localhost app]$ ls
[lmj@localhost app]$ vi echo-service.yaml
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ vi httpbin-service.yaml
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ kubectl apply -f echo-service.yaml
service/echo created
deployment.apps/echo created
[lmj@localhost app]$
[lmj@localhost app]$ kubectl apply -f httpbin-service.yaml
service/httpbin created
deployment.apps/httpbin created
[lmj@localhost app]$
[lmj@localhost app]$ vi echo-ingress.yaml
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ vi httpbin-ingress.yaml
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ kubectl apply -f echo-ingress.yaml
Warning: extensions/v1beta1 Ingress is deprecated in v1.14+, unavailable in v1.22+; use networking.k8s.io/v1 Ingress
ingress.extensions/echo-ingress created
[lmj@localhost app]$ kubectl apply -f httpbin-ingress.yaml
Warning: extensions/v1beta1 Ingress is deprecated in v1.14+, unavailable in v1.22+; use networking.k8s.io/v1 Ingress
ingress.extensions/httpbin-ingress created
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ curl -i -H “Host: echo.com” http://localhost:30080/
curl: (7) Failed connect to localhost:30080; Connection refused
[lmj@localhost app]$
[lmj@localhost app]$ curl -i -H “Host: httpbin.com” http://192.168.1.55:30080/status/200
^C
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ ls
echo-ingress.yaml echo-service.yaml httpbin-ingress.yaml httpbin-service.yaml
[lmj@localhost app]$ kubectl get pods
NAME READY STATUS RESTARTS AGE
echo-6d6b56d4d9-kg4r2 1/1 Running 0 8m48s
gateway-nginx-ingress-7c57b6f5fc-trv4x 1/1 Running 0 15m
httpbin-67b6469cff-6vhb7 1/1 Running 0 8m40s
[lmj@localhost app]$ kubectl exec -it gateway-nginx-ingress-7c57b6f5fc-trv4x /bin/bash
kubectl exec [POD] [COMMAND] is DEPRECATED and will be removed in a future version. Use kubectl exec [POD] – [COMMAND] instead.
nginx@gateway-nginx-ingress-7c57b6f5fc-trv4x:/$
nginx@gateway-nginx-ingress-7c57b6f5fc-trv4x:/$
nginx@gateway-nginx-ingress-7c57b6f5fc-trv4x:/$ ls
bin docker-entrypoint.d home media nginx.ingress.tmpl nginx.virtualserver.tmpl root srv usr
boot docker-entrypoint.sh lib mnt nginx.tmpl opt run sys var
dev etc lib64 nginx-ingress nginx.transportserver.tmpl proc sbin tmp
nginx@gateway-nginx-ingress-7c57b6f5fc-trv4x:/$ ps -rf|grep nginx
bash: ps: command not found
nginx@gateway-nginx-ingress-7c57b6f5fc-trv4x:/$ curl 1
curl: (7) Couldn’t connect to server
nginx@gateway-nginx-ingress-7c57b6f5fc-trv4x:/$ curl 127.0.0.1
404 Not Found
Search provides the ability to search for Helm charts in the various places
they can be stored including the Artifact Hub and repositories you have added.
Use search subcommands to search different locations for charts.
Usage:
helm search [command]
Available Commands:
hub search for charts in the Artifact Hub or your own hub instance
repo search repositories for a keyword in charts
Flags:
-h, --help help for search
Global Flags:
–debug enable verbose output
–kube-apiserver string the address and the port for the Kubernetes API server
–kube-as-group stringArray group to impersonate for the operation, this flag can be repeated to specify multiple groups.
–kube-as-user string username to impersonate for the operation
–kube-ca-file string the certificate authority file for the Kubernetes API server connection
–kube-context string name of the kubeconfig context to use
–kube-token string bearer token used for authentication
–kubeconfig string path to the kubeconfig file
-n, --namespace string namespace scope for this request
–registry-config string path to the registry config file (default “/home/lmj/.config/helm/registry.json”)
–repository-cache string path to the file containing cached repository indexes (default “/home/lmj/.cache/helm/repository”)
–repository-config string path to the file containing repository names and URLs (default “/home/lmj/.config/helm/repositories.yaml”)
Use “helm search [command] --help” for more information about a command.
[lmj@localhost app]$ ls
echo-ingress.yaml echo-service.yaml httpbin-ingress.yaml httpbin-service.yaml
[lmj@localhost app]$ mkdir nginx-todo
[lmj@localhost app]$ mv * nginx-todo/
mv: cannot move ‘nginx-todo’ to a subdirectory of itself, ‘nginx-todo/nginx-todo’
[lmj@localhost app]$ ls
nginx-todo
[lmj@localhost app]$ cd …
[lmj@localhost k8s]$ ls
app package
[lmj@localhost k8s]$ cd app/
[lmj@localhost app]$ ls
nginx-todo
[lmj@localhost app]$ helm search nginx-ingress
Search provides the ability to search for Helm charts in the various places
they can be stored including the Artifact Hub and repositories you have added.
Use search subcommands to search different locations for charts.
Usage:
helm search [command]
Available Commands:
hub search for charts in the Artifact Hub or your own hub instance
repo search repositories for a keyword in charts
Flags:
-h, --help help for search
Global Flags:
–debug enable verbose output
–kube-apiserver string the address and the port for the Kubernetes API server
–kube-as-group stringArray group to impersonate for the operation, this flag can be repeated to specify multiple groups.
–kube-as-user string username to impersonate for the operation
–kube-ca-file string the certificate authority file for the Kubernetes API server connection
–kube-context string name of the kubeconfig context to use
–kube-token string bearer token used for authentication
–kubeconfig string path to the kubeconfig file
-n, --namespace string namespace scope for this request
–registry-config string path to the registry config file (default “/home/lmj/.config/helm/registry.json”)
–repository-cache string path to the file containing cached repository indexes (default “/home/lmj/.cache/helm/repository”)
–repository-config string path to the file containing repository names and URLs (default “/home/lmj/.config/helm/repositories.yaml”)
Use “helm search [command] --help” for more information about a command.
[lmj@localhost app]$ helm search repo nginx-ingress
NAME CHART VERSION APP VERSION DESCRIPTION
nginx-stable/nginx-ingress 0.10.0 1.12.0 NGINX Ingress Controller
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ helm install my-release nginx-stable/nginx-ingress
Error: failed to download “nginx-stable/nginx-ingress” (hint: running helm repo update may help)
[lmj@localhost app]$ helm repo update
Hang tight while we grab the latest from your chart repositories…
…Successfully got an update from the “nginx-stable” chart repository
Update Complete. ⎈Happy Helming!⎈
[lmj@localhost app]$ helm install my-release nginx-stable/nginx-ingress
Error: failed to download “nginx-stable/nginx-ingress” (hint: running helm repo update may help)
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ helm repo add nginx-stable https://helm.nginx.com/stable
“nginx-stable” already exists with the same configuration, skipping
[lmj@localhost app]$
[lmj@localhost app]$ helm repo update
Hang tight while we grab the latest from your chart repositories…
…Successfully got an update from the “nginx-stable” chart repository
Update Complete. ⎈Happy Helming!⎈
[lmj@localhost app]$
[lmj@localhost app]$ helm install my-nginx nginx-stable/nginx-ingress
W0822 12:46:58.381310 43107 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
Error: rendered manifests contain a resource that already exists. Unable to continue with install: IngressClass “nginx” in namespace “” exists and cannot be imported into the current release: invalid ownership metadata; annotation validation error: key “meta.helm.sh/release-name” must equal “my-nginx”: current value is “gateway”
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ helm uninstall gateway
W0822 12:48:08.732808 43462 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
release “gateway” uninstalled
[lmj@localhost app]$ helm install my-nginx nginx-stable/nginx-ingress
W0822 12:48:24.819744 43521 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
W0822 12:48:24.919977 43521 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
NAME: my-nginx
LAST DEPLOYED: Sun Aug 22 12:48:24 2021
NAMESPACE: default
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
The NGINX Ingress Controller has been installed.
[lmj@localhost app]$ kubectl get services
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 443/TCP 38m
my-nginx-nginx-ingress LoadBalancer 10.109.130.48 80:30566/TCP,443:31265/TCP 23s
[lmj@localhost app]$ lsof -i:30566
[lmj@localhost app]$ lsof -i:30566
[lmj@localhost app]$ lsof -i:80
[lmj@localhost app]$ curl 10.109.130.48 30566
^C
[lmj@localhost app]$ curl 10.109.130.48:30566
^C
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ helm uninstall my-nginx
W0822 12:50:53.475524 44512 warnings.go:70] networking.k8s.io/v1beta1 IngressClass is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 IngressClassList
release “my-nginx” uninstalled
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ helm repo add ingress-nginx https://kubernetes.github.io/ingress-nginx
“ingress-nginx” has been added to your repositories
[lmj@localhost app]$
[lmj@localhost app]$ helm repo update
Hang tight while we grab the latest from your chart repositories…
…Successfully got an update from the “nginx-stable” chart repository
…Successfully got an update from the “ingress-nginx” chart repository
Update Complete. ⎈Happy Helming!⎈
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ helm install ingress-nginx ingress-nginx/ingress-nginx
NAME: ingress-nginx
LAST DEPLOYED: Sun Aug 22 12:51:47 2021
NAMESPACE: default
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
The ingress-nginx controller has been installed.
It may take a few minutes for the LoadBalancer IP to be available.
You can watch the status by running ‘kubectl --namespace default get services -o wide -w ingress-nginx-controller’
An example Ingress that makes use of the controller:
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: nginx
name: example
namespace: foo
spec:
rules:
- host: www.example.com
http:
paths:
- backend:
serviceName: exampleService
servicePort: 80
path: /
# This section is only required if TLS is to be enabled for the Ingress
tls:
- hosts:
- www.example.com
secretName: example-tls
If TLS is enabled for the Ingress, a Secret containing the certificate and key must also be provided:
apiVersion: v1
kind: Secret
metadata:
name: example-tls
namespace: foo
data:
tls.crt:
tls.key:
type: kubernetes.io/tls
[lmj@localhost app]$ kubectl get svc -o wide
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
ingress-nginx-controller LoadBalancer 10.98.178.145 80:30283/TCP,443:32719/TCP 57s app.kubernetes.io/component=controller,app.kubernetes.io/instance=ingress-nginx,app.kubernetes.io/name=ingress-nginx
ingress-nginx-controller-admission ClusterIP 10.98.219.229 443/TCP 57s app.kubernetes.io/component=controller,app.kubernetes.io/instance=ingress-nginx,app.kubernetes.io/name=ingress-nginx
kubernetes ClusterIP 10.96.0.1 443/TCP 43m
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ kubectl --namespace default get services -o wide -w ingress-nginx-controller
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
ingress-nginx-controller LoadBalancer 10.98.178.145 80:30283/TCP,443:32719/TCP 2m10s app.kubernetes.io/component=controller,app.kubernetes.io/instance=ingress-nginx,app.kubernetes.io/name=ingress-nginx
^C[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$
[lmj@localhost app]$ lsof -i:30283
[lmj@localhost app]$ lsof -i:30283
[lmj@localhost app]$ ps -ef |grep 30283
lmj 46315 16649 0 12:55 pts/0 00:00:00 grep --color=auto 30283
[lmj@localhost app]$ history
1 minikube start
2 p
3 helm repo add nginx-stable https://helm.nginx.com/stable
4 helm search repo nginx-ingress
5 helm show values nginx-stable/nginx-ingress
6 helm install gateway nginx-stable/nginx-ingress --set controller.service.type=NodePort --set controller.service.httpPort.nodePort=30080 --set controller.service.httpsPort.nodePort=30443
7 ————————————————
8 版权声明:本文为CSDN博主「twingao」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
9 原文链接:https://blog.csdn.net/twingao/article/details/105157724
10 kubectl get all
11 curl http://127.0.0.1:30080
12 curl http://10.97.30.83:30080
13 ip addr
14 curl http://172.16.191.133:30080
15 kubectl get all
16 kubectl get pods
17 kubectl logs gateway-nginx-ing
18 kubectl logs gateway-nginx-ingress-7c57b6f5fc-trv4x
19 lsof -i:30080
20 telnet localhost 30080
21 telnet localhost 80
22 cd /opt/
23 ls
24 cd k8s/
25 ls
26 mkdir app
27 cd app/
28 ls
29 vi echo-service.yaml
30 vi httpbin-service.yaml
31 kubectl apply -f echo-service.yaml
32 kubectl apply -f httpbin-service.yaml
33 vi echo-ingress.yaml
34 vi httpbin-ingress.yaml
35 kubectl apply -f echo-ingress.yaml
36 kubectl apply -f httpbin-ingress.yaml
37 curl -i -H “Host: echo.com” http://localhost:30080/
38 curl -i -H “Host: httpbin.com” http://192.168.1.55:30080/status/200
39 ls
40 kubectl get pods
41 kubectl exec -it gateway-nginx-ingress-7c57b6f5fc-trv4x /bin/bash
42 ls
43 kubectl get services
44 export HTTP_NODE_PORT=
(
k
u
b
e
c
t
l
−
−
n
a
m
e
s
p
a
c
e
d
e
f
a
u
l
t
g
e
t
s
e
r
v
i
c
e
s
−
o
j
s
o
n
p
a
t
h
=
"
.
s
p
e
c
.
p
o
r
t
s
[
0
]
.
n
o
d
e
P
o
r
t
"
n
g
i
n
x
−
i
n
g
r
e
s
s
−
n
g
i
n
x
−
i
n
g
r
e
s
s
−
c
o
n
t
r
o
l
l
e
r
)
45
e
x
p
o
r
t
H
T
T
P
S
N
O
D
E
P
O
R
T
=
(kubectl --namespace default get services -o jsonpath="{.spec.ports[0].nodePort}" nginx-ingress-nginx-ingress-controller) 45 export HTTPS_NODE_PORT=
(kubectl−−namespacedefaultgetservices−ojsonpath=".spec.ports[0].nodePort"nginx−ingress−nginx−ingress−controller)45exportHTTPSNODEPORT=(kubectl --namespace default get services -o jsonpath="{.spec.ports[1].nodePort}" nginx-ingress-nginx-ingress-controller)
46 export NODE_IP=
(
k
u
b
e
c
t
l
−
−
n
a
m
e
s
p
a
c
e
d
e
f
a
u
l
t
g
e
t
n
o
d
e
s
−
o
j
s
o
n
p
a
t
h
=
"
.
i
t
e
m
s
[
0
]
.
s
t
a
t
u
s
.
a
d
d
r
e
s
s
e
s
[
1
]
.
a
d
d
r
e
s
s
"
)
47
e
c
h
o
"
V
i
s
i
t
h
t
t
p
:
/
/
(kubectl --namespace default get nodes -o jsonpath="{.items[0].status.addresses[1].address}") 47 echo "Visit http://
(kubectl−−namespacedefaultgetnodes−ojsonpath=".items[0].status.addresses[1].address")47echo"Visithttp://NODE_IP:
H
T
T
P
N
O
D
E
P
O
R
T
t
o
a
c
c
e
s
s
y
o
u
r
a
p
p
l
i
c
a
t
i
o
n
v
i
a
H
T
T
P
.
"
48
e
c
h
o
"
V
i
s
i
t
h
t
t
p
s
:
/
/
HTTP_NODE_PORT to access your application via HTTP." 48 echo "Visit https://
HTTPNODEPORTtoaccessyourapplicationviaHTTP."48echo"Visithttps://NODE_IP:$HTTPS_NODE_PORT to access your application via HTTPS."
49 kubectl get services
50 kubectl get deployments
51 kubectl delete deployment gateway-nginx-ingress
52 kubectl get deployments
53 kubectl get deployment echo
54 kubectl get deployment httpbin
55 kubectl get deployments
56 kubectl get services
57 kubectl delete service gateway-nginx-ingress
58 kubectl delete service echo httpbin
59 kubectl get services
60 helm search nginx-ingress
61 ls
62 mkdir nginx-todo
63 mv * nginx-todo/
64 ls
65 cd …
66 ls
67 cd app/
68 ls
69 helm search nginx-ingress
70 helm search repo nginx-ingress
71 helm install my-release nginx-stable/nginx-ingress
72 helm repo update
73 helm install my-release nginx-stable/nginx-ingress
74 helm repo add nginx-stable https://helm.nginx.com/stable
75 helm repo update
76 helm install my-nginx nginx-stable/nginx-ingress
77 helm uninstall gateway
78 helm install my-nginx nginx-stable/nginx-ingress
79 kubectl get services
80 lsof -i:30566
81 lsof -i:80
82 curl 10.109.130.48 30566
83 curl 10.109.130.48:30566
84 helm uninstall my-nginx
85 helm repo add ingress-nginx https://kubernetes.github.io/ingress-nginx
86 helm repo update
87 helm install ingress-nginx ingress-nginx/ingress-nginx
88 kubectl get svc -o wide
89 kubectl --namespace default get services -o wide -w ingress-nginx-controller
90 lsof -i:30283
91 ps -ef |grep 30283
92 history




















 923
923











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








