28. Multi-process Support (dpdk多进程支持)
在DPDK中,多进程支持被设计成允许一组DPDK进程以一种简单透明的方式协同工作,以执行包处理或其他工作负载。为了支持这个功能,对核心DPDK环境抽象层(EAL)进行了一些功能添加。
EAL已经被修改为允许生成不同类型的DPDK进程,每个处理应用程序使用的hugepage内存都有不同的权限。目前,支持两种进程类型:
- 主进程(primary),主进程初始化共享内存,它具有对共享内存的完整权限
- 副进程(secondary),它不能初始化共享内存,但可以使用主进程初始化的共享内存,并在其中创建内存对象(可以称为辅助进程或是次进程)
独立运行的DPDK进程只能是主进程,而副进程只能在主进程已经配置了hugepage共享内存之后运行。为了支持这两种进程类型,以及稍后描述的其他多进程设置,可以使用两个额外的命令行参数:
- --proc-type:指定一个dpdk进程是主进程还是副进程(参数值就用上面的primary或是secondary,或者是auto)
- --file-prefix:允许非合作的进程拥有不同的内存区域
28.1 Memory Sharing(共享内存)
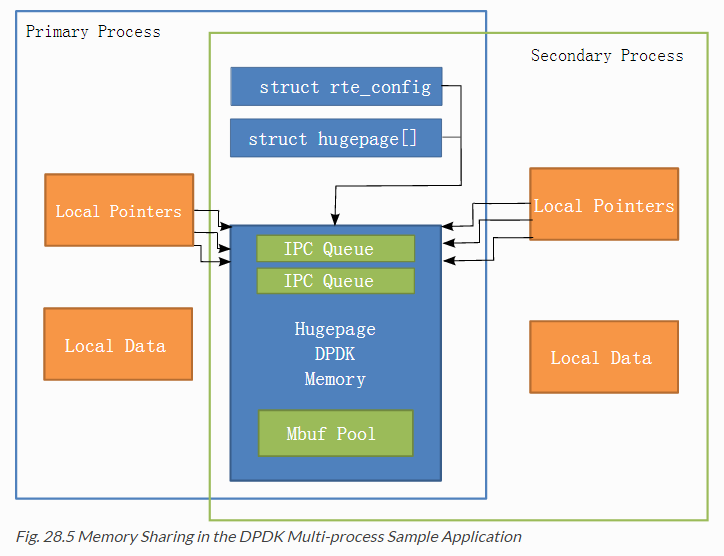
DPDK多进程的关键是确保在组成这多进程应用程序的过程中适当地共享内存资源。一旦有了可以被多个进程访问的共享内存块,那么诸如进程间通信(IPC)之类的问题就变得简单多了。
主进程启动后,DPDK通过内存映射文件详细记录正在使用的内存配置-hugepages使用情况,虚拟地址的映射,内存频道的数量等等。当副进程启动时,通过读取映射文件后重新创建和主进程相同的内存配置,这样,所有进程之间共享所有的内存区域,所有指向内存的指针都是有效的,并指向同一个对象。
!Note
有关Linux内核地址空间随机分布(ASLR)如何影响内存共享的详细信息,请参阅多进程限制( Multi-process Limitations)。
EAL 还支持自动检测模式(--proc-type=auto 设置),如果一个主进程已经运行,那么DPDK进程将作为一个副进程启动。
28.2 Deployment Models(调度模式)
28.2.1 Symmetric/Peer Processes(对等进程 )
DPDK多进程可创建一组对等进程,每个进程执行相同的工作负载。这个模型相当于拥有多个线程,每个线程运行相同的主循环函数,就像大多数提供的DPDK样例应用程序所做的那样。在这个模型中,第一个进程应该使用--proc-type=primary,而所有后续的进程都应该使用--proc-type=secondary。
simple_mp和symmetric_mp示例应用程序演示了这种使用模型。它们在“ DPDK Sample Application’s User ”中的“Multi-process Sample Application”一章中进行了描述。
28.2.2 Asymmetric/Non-Peer Processes(不对等进程)
DPDK多进程支持的另一种部署模型是,运行一个单独的主进程,它在worker或客户线程中充当负载平衡器或数据包分发服务器,worker或客户机线程是副进程类型。在这种情况下,大量使用rte_ring对象,它们位于共享的hugepage内存中。
(这种模式就是一个主进程收取所有网络接口的数据报文,然后根据分配算法把数据包分发给其他worker(多进程中的一个进程,类型为副进程)或是客户线程(dpdk进程内部支持多线程,主线程类似于主进程,其它线程类似于副进程))
28.2.3. Running Multiple Independent DPDK Applications(运行多个独立的dpdk应用)
除了上述涉及多个DPDK进程共同协作的应用场景外,也可以并行地运行多个DPDK进程,这些进程都是独立工作的。对这个使用场景的支持是使用--file-prefix参数来提供的。
默认情况下,在每个hugetlbfs文件系统上使用rtemap_X 文件名创建hugepage文件,其中X在0到最大的hugepages - 1之间。同样,它使用/var/run/.rte_config文件名来创建共享配置文件、每个进程映射的内存。当作为root(或$ HOME /.rte_config,作为非root用户运行时;如果设置了文件系统和设备权限,则允许这样做)。上述每个文件的rte部分都可以使用--file-prefix参数进行配置。
除了指定--file-prefix参数之外,任何要并行运行的DPDK应用程序都必须显式地限制其内存使用。这是通过将 -m 标志传递给每个进程来指定每个进程可以使用多少百万字节的的hugepage内存(也可以通过--socket-mem参数来指定进程在每个cpu socket上的hugepage内存大小)。
(现在常用--socket-mem参数,eg:单socket,--socket-mem=512;在numa中,--socket-mem=512,512;多个socket间用‘,’号隔开;)
!Note
多个独立的DPDK实例进程在一台机器上并行运行,不能共享任何网络端口。任何一个进程使用的网络端口都应该在其他进程中被列入黑名单。
(通常一个dpdk进程在运行时通过白名单参数-w pci号指定使用指定接口,eg:-w 0000:06:00.0)
28.2.4. Running Multiple Independent Groups of DPDK Applications(独立运行进程组)
同样,独立的DPDK应用程序可以在单个系统上并行运行,也可以简单地扩展到并行运行多进程组。在这种情况下,同一个组的副进程必须使用和主进程相同的--file-prefix参数来连接到共享内存。
!Note
在这个使用场景中,也包括多个独立DPDK进程并行运行的所有限制和问题。
28.3. Multi-process Limitations(多进程限制)
在运行DPDK多进程应用程序时,有很多限制。其中一些记录如下:
- 多进程特性要求在所有应用程序中都存在完全相同的hugepage内存映射。Linux安全特性——地址空间随机分布ASLR)会干扰这个映射,因此,为了可靠地运行多进程应用程序,可能需要禁用该特性。
- 所有以单独应用程序运行并使用共享内存的DPDK进程必须具有不同的coremask / corelist参数。同一个逻辑核,不可能运行一个主进程和一个副进程,或是运行2个副进程。试图这样做会导致内存池缓存的损坏,以及其他问题。
- 在副进程中,不能接收所有中断,如以太网*设备链路状态中断。所有中断都只在主进程内触发。在dpdk多进程中所有需要响应中断的副进程必须提供自己的机制,将主进程中的中断通告传递到副进程中。
- 不支持基于编译的不同二进制文件的多进程之间使用函数指针,因为在一个进程中给定函数的位置可能在一秒钟内与它的位置不同。这将阻止librte_hash库在多线程实例中正常运行,因为它在内部使用一个指向hash函数的指针。
- 根据使用的硬件和使用的DPDK进程的数量,也许不可能在每个DPDK实例中都有HPET计时器。Linux *用户空间中可用的HPET比较器的最小值可能只有一个,这意味着,只有DPDK主进程实例可以打开和mmap /dev/hpet。如果需要的DPDK进程的数量超过可用的HPET比较器的数量,则TSC(这个版本中的默认计时器)必须作为跨所有进程的时间源,而不是HPET。






















 6600
6600

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








