应用程序字体模糊
I generally prefer manual hacking when approaching a new web app target. Manual testing is useful for discovering new and unexpected attack vectors, but it also takes up a lot of time and effort.
当接近新的Web应用程序目标时,我通常更喜欢手动黑客。 手动测试对于发现新的和意外的攻击媒介很有用,但也要花费大量时间和精力。
Automated testing, on the other hand, is much more efficient at teasing out a large number of bugs within a short time frame. In fact, bugs discovered through fuzzing now account for the majority of new CVE entries.
另一方面,自动化测试在短时间内消除大量错误的效率更高。 实际上,通过模糊检测发现的错误现在占了新的CVE条目的大部分。
Today, let’s talk a bit about fuzzing web applications, how it is done, and what it can achieve for you.
今天,让我们谈谈模糊Web应用程序,如何完成以及它可以为您带来什么。
什么是绒毛? (What is fuzzing?)
Fuzzing is a way of finding bugs using automation. It involves providing a wide range of invalid and unexpected data into an application then monitoring the application for exceptions.
模糊测试是一种使用自动化发现错误的方法。 它涉及向应用程序中提供各种无效和意外数据,然后监视应用程序中的异常。
The invalid data used to fuzz an application could be crafted for a specific purpose, or randomly generated. The goal is to induce unexpected behavior of an application (like crashes and memory leaks) and see if it leads to an exploitable bug.
用来模糊应用程序的无效数据可以出于特定目的而制作,也可以随机生成。 目的是引起应用程序的异常行为(例如崩溃和内存泄漏),并查看其是否导致可利用的bug。
In general, fuzzing is particularly useful for exposing bugs like memory leaks, control flow issues, and race conditions.
通常,模糊测试对于暴露诸如内存泄漏,控制流问题和竞争条件之类的错误特别有用。
模糊化Web应用程序 (Fuzzing web applications)
There are many different kinds of fuzzing, each optimized for testing a specific type of application. Web application fuzzing is the field of fuzzing web applications to expose common web vulnerabilities, like injection issues, XSS, and more.
有很多不同类型的模糊测试,每种都针对测试特定类型的应用程序进行了优化。 Web应用程序模糊测试是对Web应用程序进行模糊测试以暴露常见的Web漏洞(例如注入问题,XSS等)的领域。
模糊与静态分析 (Fuzzing versus static analysis)
So, your question now might be: why not just do static analysis on the source code? What are the advantages of fuzzing an application versus simply diving into the code?
因此,您现在的问题可能是:为什么不对源代码进行静态分析呢? 与仅仅深入研究代码相比,模糊应用程序有什么优势?
I am a huge proponent of doing static code analysis to find bugs. Here’s an intro to get you started reviewing code for security purposes:
我非常支持进行静态代码分析以查找错误。 这是一个简介,可让您开始查看出于安全目的的代码:
Static code analysis is an invaluable tool to identify bugs and improper programming practices that can be exploited by attackers. However, static analysis has its limitations.
静态代码分析是一种有价值的工具,用于识别攻击者可以利用的错误和不正确的编程实践。 但是,静态分析有其局限性。
First, it only evaluates an application in a non-live state. Performing code review on an application won’t let you simulate how the application will react when it’s running live and clients are interacting with it. It is very difficult to take into account all the possible malicious inputs an attacker can provide when doing static analysis.
首先,它仅评估处于非活动状态的应用程序。 在应用程序上执行代码审查不会让您模拟应用程序在实时运行且客户端与之交互时的React。 在进行静态分析时,很难考虑攻击者可能提供的所有可能的恶意输入。
Static code analysis also requires access to the source code of an application. When doing a black-box test and you are not able to obtain the source code, fuzzing is a great way of increasing test coverage since source code is not needed when fuzzing an application.
静态代码分析还需要访问应用程序的源代码。 在进行黑盒测试时,您将无法获得源代码,因此,模糊测试是增加测试覆盖率的一种好方法,因为在对应用程序进行模糊测试时不需要源代码。
模糊Web应用程序的步骤 (Steps of fuzzing a web application)
Let’s go through the steps that you must take while fuzzing a web app!
让我们完成在模糊Web应用程序时必须执行的步骤!
Determine the data entry points
确定数据输入点
The first thing to do when fuzzing a web application is to identify the ways a client can provide input to the application. What are the endpoints that take input? What are the parameters used? What headers do the application use?
对Web应用程序进行模糊处理时,要做的第一件事是确定客户端可以向应用程序提供输入的方式。 接受输入的端点是什么? 使用什么参数? 应用程序使用哪些标题?
2. Decide on the payload list
2.确定有效负载列表
After you’ve identified the data entry points, you’d have to determine what data to feed to the application. For web applications, the most useful fuzzing data would be lists of known XSS payloads, SQLi payloads, and so on. I recommend downloading SecLists here for a pretty comprehensive payload list for fuzzing web applications:
确定数据入口点之后,必须确定要向应用程序馈送什么数据。 对于Web应用程序,最有用的模糊数据将是已知XSS有效负载,SQLi有效负载等的列表。 我建议在此处下载SecLists,以获得用于模糊Web应用程序的相当全面的有效负载列表:
SecList is pretty good for detecting already known vulnerabilities. Another way of fuzzing is to generate payloads randomly, including payloads like the below to try to induce errors in the web app:
SecList非常适合检测已知漏洞。 模糊测试的另一种方法是随机生成有效载荷,包括如下所示的有效载荷,以尝试在Web应用程序中引起错误:
- Payloads that are really long, 有效负载非常长,
- payloads that contain odd characters of various encodings, 包含各种编码的奇数字符的有效载荷,
- and payloads that contain certain special characters, like the new line character, the line feed character, and more. 以及包含某些特殊字符的有效负载,例如换行符,换行符等。
By feeding the application garbage data like this, you might be able to detect unexpected behavior and discover new classes of vulnerabilities!
通过像这样输入应用程序垃圾数据,您也许能够检测到意外行为并发现新的漏洞类别!
3. Fuzz
3.起毛
Now, all there is to do is to systematically feed your fuzz payload list to the data entry points of the application! There are several ways of doing it, depending on your needs and your programming skills.
现在,所有要做的就是将您的模糊有效负载列表系统地馈送到应用程序的数据输入点! 有多种方法,具体取决于您的需求和编程技能。
Burp Intruder
打p者
The first way to automate fuzzing is to use the BurpSuite intruder. Burp provides a GUI for configuring your fuzzer settings, so you can basically choose an endpoint, choose a payload list and start fuzzing!
自动执行模糊测试的第一种方法是使用BurpSuite入侵者。 Burp提供了一个用于配置模糊器设置的GUI,因此您基本上可以选择一个端点,选择一个有效负载列表并开始进行模糊处理!
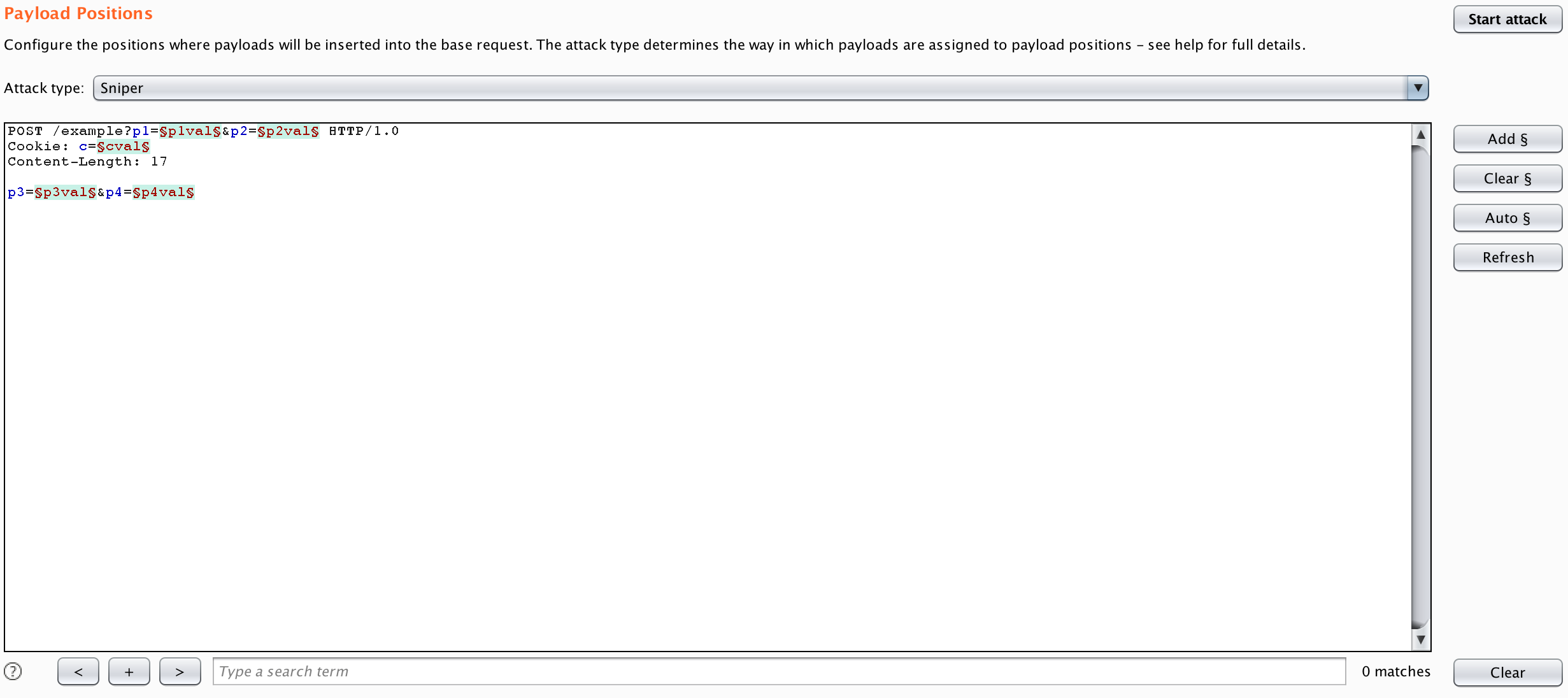
With Burp Intruder, you can specify where the payloads should go in a request, which data parameters to insert into, and how many different positions to insert the payloads at once.
使用Burp Intruder,您可以指定负载在请求中的位置,要插入的数据参数以及一次插入负载的位置。
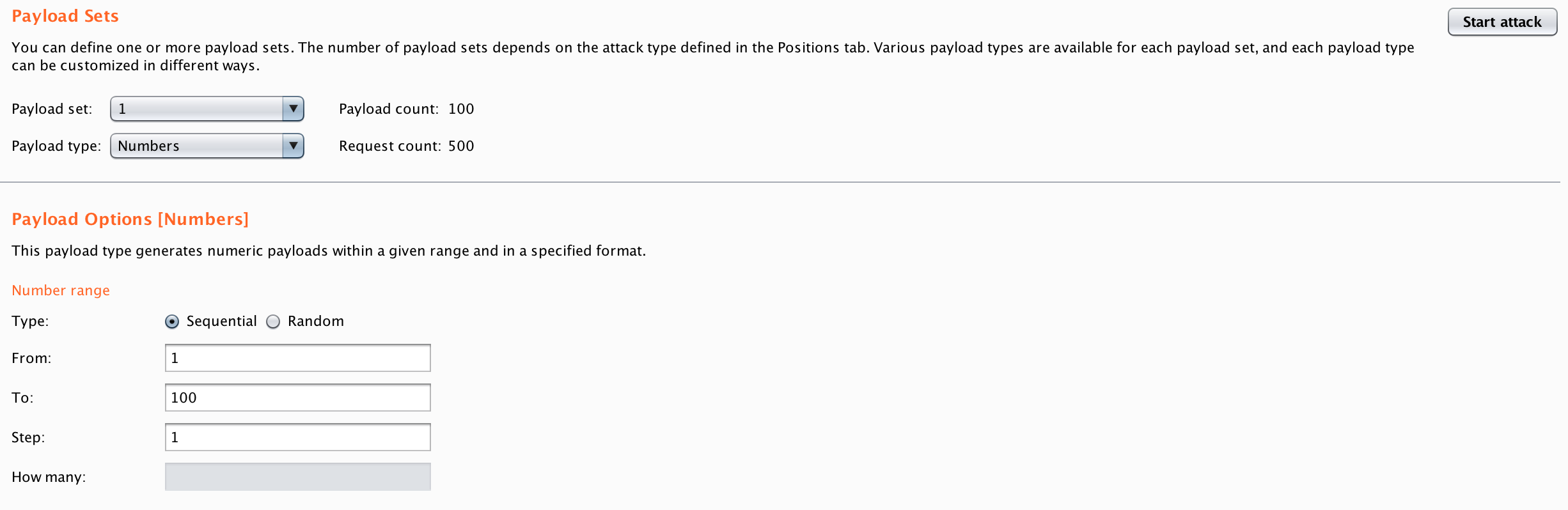
You can also select a predefined list of payloads or generate payload lists within burp.
您还可以选择预定义的负载列表或在burp中生成负载列表。
The downside to using Burp is that the community version limits the functionality of the fuzzer, and time throttles its attacks. So it would be a lot less efficient than a non-time-throttled fuzzer. So unless you have the professional version, I would recommend simply implementing your own fuzzer with a programming language of your choice, or to use the OWASP ZAP fuzzer.
使用Burp的不利之处在于,社区版本限制了模糊测试器的功能,并且时间限制了它的攻击。 因此,它比没有时间限制的模糊器效率要低得多。 因此,除非您拥有专业版本,否则我建议您仅使用所选的编程语言来实现自己的模糊器,或者使用OWASP ZAP模糊器。
OWASP ZAP模糊器 (OWASP ZAP Fuzzer)
The OWASP Zed Attack Proxy (ZAP) also has a built-in fuzzer that you can use. Unlike the Burp intruder, it is not time-throttled and all functionalities are free.
OWASP Zed攻击代理(ZAP)也具有内置的模糊测试器,您可以使用它。 与Burp入侵者不同,它不受时间限制,所有功能都是免费的。
But just like the Burp Intruder, with these pre-built fuzzers, it is sometimes difficult to have all the functionalities that you need. So, feel free to try writing your own fuzzer.
但是,就像带有这些预先构建的模糊器的Burp Intruder一样,有时很难拥有所需的所有功能。 因此,随时尝试编写自己的模糊器。
4. Monitor the results
4.监控结果
The final step is to analyze the results your fuzzer returned. You should look for patterns and anomalies from the server response. What you should be looking for will depend on the payload set that you use. For example, when fuzzing for SQLi, you might want to look for a change in content length or response time. And when searching for path traversals, you might look for special keywords in the response. Looking more into each vulnerability type will help you identify the key signatures of each vulnerability being present.
最后一步是分析您的模糊器返回的结果。 您应该从服务器响应中查找模式和异常。 您应寻找的内容取决于您使用的有效负载集。 例如,在对SQLi进行模糊处理时,您可能希望查找内容长度或响应时间的变化。 搜索路径遍历时,您可能会在响应中寻找特殊的关键字。 深入研究每种漏洞类型将有助于您识别存在的每个漏洞的关键特征。
模糊的陷阱 (Pitfalls of fuzzing)
Of course, fuzzing is not the magic cure-all solution for all bug detection. There are certain limitations to using fuzzing to hack web applications.
当然,模糊检测并不是解决所有错误的万灵药。 使用模糊测试来入侵Web应用程序存在某些限制。
One of these limitations is rate-limiting by the server. During a remote, black-box engagement, you might not be able to send in large numbers of payloads to the application without being detected by the server or hitting some kind of rate-limit. This can cause testing to slow down or even cause you to be banned from the service.
这些限制之一是服务器的速率限制。 在远程黑匣子参与期间,您可能无法在服务器未检测到或未达到某种速率限制的情况下向应用程序发送大量有效负载。 这可能会导致测试速度变慢,甚至导致您被禁止使用该服务。
When fuzzing during black-box testing, it is also difficult to accurately evaluate the impact of the bug since you do not have access to the code and you are getting a very limited sample of the application’s behavior. This means that further manual testing is often needed to classify the bug’s validity and significance.
在黑盒测试期间进行模糊测试时,由于您无权访问代码并且获得的应用程序行为样本非常有限,因此也很难准确评估错误的影响。 这意味着通常需要进一步的手动测试来对错误的有效性和重要性进行分类。
Think of fuzzing as a metal detector: it merely points you to the suspicious spots. And in the end, you need to inspect more closely to see if you have found something of value.
可以将模糊视为金属探测器:它只是将您指向可疑地点。 最后,您需要更仔细地检查以发现是否有价值。
Another limitation is the classes of bugs that fuzzing a web application can find. Although fuzzing is good at finding certain simplistic vulnerabilities like XSS and SQLi, and can sometimes aid in the discovery of new bug types, it is not much help in detecting business logic errors, and bugs that require multiple steps to exploit. These complex bugs are a big source of potential attacks and still need to be teased out manually. This is why fuzzing should be an essential part of your testing process, but it should by no means be the only part of it.
另一个限制是使Web应用程序模糊化可以发现的错误类别。 尽管模糊测试擅长于发现某些简单的漏洞(例如XSS和SQLi),并且有时可以帮助发现新的错误类型,但对于检测业务逻辑错误和需要多个步骤加以利用的错误并没有太大帮助。 这些复杂的错误是潜在攻击的重要来源,仍然需要手动解决。 这就是为什么模糊测试应该是测试过程中必不可少的一部分,但绝不应成为它的唯一部分。
Thanks for reading. And remember: trying this on systems where you don’t have permission to test is illegal. If you’ve found a vulnerability, please disclose it responsibly to the vendor. Help make our Internet a safer place.
谢谢阅读。 请记住:在没有测试许可的系统上尝试这样做是非法的。 如果您发现了漏洞,请以负责任的方式向供应商披露。 帮助使我们的互联网更安全。
翻译自: https://medium.com/swlh/fuzzing-web-applications-e786ca4c4bb6
应用程序字体模糊





















 2637
2637

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








