npm 更新 npm
Web Security is an ever-changing field, with attackers finding new and innovative ways to access an unsuspecting user’s system. An insecure app is bound to be exploited by a seasoned attacker, in one form or another.
Web安全是一个日新月异的领域,攻击者正在寻找新颖和创新的方式来访问毫无戒心的用户系统。 一个不安全的应用程序必然会以一种或多种形式被经验丰富的攻击者利用。
We take a look at 10 of the best security practices that you can implement right now to keep your Node.JS application safe. Without further ado, let us dive right in.
我们来看一下您现在可以实施的10种最佳安全实践,以确保Node.JS应用程序安全。 事不宜迟,让我们立即潜水。
1.以非root用户身份运行Node.JS。 (1. Run Node.JS as a non-root user.)
Most node.js apps don’t need root access and can easily run without root privileges. A user should only be able to access the information and resources that they need, which means granting every user root access will leave you open to attacks. You don’t want the attacker to have unlimited power over the local machine, which they can then use to divert traffic to another server.
大多数node.js应用程序不需要root访问权限,并且无需root特权即可轻松运行。 用户只能访问所需的信息和资源,这意味着授予每个用户root访问权限将使您容易受到攻击。 您不希望攻击者对本地计算机具有无限的控制权,然后他们可以将其用于将流量转移到另一台服务器。
The solution: Create a non-root user and then run the process on the user’s behalf, by invoking the container with the flag “-u username.” You can also bake the non-root user into the Docker image.
解决方案:创建一个非root用户,然后通过标记“ -u username”的容器代表该用户运行该过程。 您也可以将非root用户烘烤到Docker映像中。
2.使用两因素身份验证。 (2. Use Two Factor Authentication.)
In the case of a majority of node.js development environments, the access is secured with the help of a password. But passwords such as password, letmein, or donkeykong are easy to guess and leaves the system open to attack. Weak session management policies implemented in applications usually leaves the door wide open to attackers. You may have a user logging in from a public computer that has a password manager, and the password that you or your company spent hours generating is now open to the public.
在大多数的node.js开发环境中,访问是通过密码保护的。 但是, 密码,letmein或donkeykong之类的密码很容易猜到,并使系统容易受到攻击。 应用程序中实施的弱会话管理策略通常会向攻击者敞开大门。 您可能有一个用户从具有密码管理器的公用计算机上登录,并且您或您的公司花了数小时生成的密码现已向公众开放。
The solution: Use Two-Factor Authorization to keep all your passwords secure. Adding an extra layer of security, even if an attacker has your user’s login credentials, they still can’t get into your system without access to a secondary device, such as a mobile phone. Use pre-existing solutions such as Okta, 0Auth, or provide Two-Factor Authorization in-app using a package such as speakeasy.
解决方案:使用双重授权,以确保所有密码的安全。 即使攻击者拥有您用户的登录凭据,也可以增加安全性,即使没有访问辅助设备(例如手机),他们仍然无法进入您的系统。 使用现有的解决方案(例如Okta,0Auth),或使用诸如talkeasy之类的软件包提供应用内的双向授权。
3.明确指出进程何时崩溃。 (3. Explicitly state when a process should crash.)
Denial of Service (DOS) attacks will crash a system or make it inaccessible and is a preferred mode of attack among hackers. Attackers accomplish DOS attacks by sending a huge surge of traffic to your server, bombarding it with useless information that will cause the server to slow down / crash eventually. Node.JS processes will usually crash when errors are not handled properly. If the attackers know which errors will cause the system to crash, they will repeatedly send the same request.
拒绝服务(DOS)攻击将使系统崩溃或使其无法访问,这是黑客首选的攻击方式。 攻击者通过向服务器发送大量流量来攻击DOS,并用无用的信息对其进行轰炸,最终使服务器减速/崩溃。 如果错误处理不当,Node.JS进程通常会崩溃。 如果攻击者知道哪些错误将导致系统崩溃,他们将反复发送相同的请求。
The solution: Solutions include alerting any time a process crashes due to an unhandled error, avoiding crashing the process when the user input is invalid, and wrapping all routes with a catch. You can also limit the payload that a user can submit to your app/ api / service. You can also set a maximum number of requests that a user can make, and after all the requests, lock the user out for a set period.
解决方案:解决方案包括在进程由于未处理的错误而崩溃时发出警报,避免在用户输入无效时使进程崩溃,以及用catch包裹所有路由。 您还可以限制用户可以提交到您的app / api /服务的有效负载。 您还可以设置用户可以发出的最大请求数,并且在所有请求之后,将用户锁定一段时间。
4.跟踪所有漏洞。 (4. Keep track of all the vulnerabilities.)
With a large number of open-source packages available for the JavaScript ecosystem, it is easy for an attacker to sneak in malicious code into one of our applications. Keeping track of all the various versions and licensing of these packages is often tedious, leaving a window of opportunity to a dedicated attacker. It is important to keep all the dependencies in check as and when new vulnerabilities are found. Otherwise, an attacker can assess your entire web framework and attack all its known vulnerabilities.
借助可用于JavaScript生态系统的大量开源软件包,攻击者很容易将恶意代码潜入我们的应用程序之一。 跟踪这些软件包的所有不同版本和许可通常很乏味,这给专门的攻击者留下了机会之窗。 当发现新漏洞时,务必检查所有依赖项。 否则,攻击者可以评估您的整个Web框架并攻击其所有已知漏洞。
The solution: Use readily available tools such as npm audit, snyk, or nsp to monitor and patch all known vulnerabilities. Package managers such as Yarn can also help to block these outlets by locking versions of packages installed. By running $ npm audit, you can find an audit report with all the installed dependencies.
解决方案:使用npm audit , snyk或nsp等现成的工具来监视和修补所有已知漏洞。 诸如Yarn之类的软件包管理器还可以通过锁定所安装软件包的版本来帮助阻止这些出口。 通过运行$ npm audit,您可以找到包含所有已安装依赖项的审计报告。
5.使用TLS (5. Use TLS)
Transport Layer Security (TLS) is critical if your app deals with sensitive data, to secure the connection and the data. Before data is transmitted between the client and the server, TLS encrypts it so that there is no pocket sniffing or man-in-the-middle attacks. A man-in-the-middle attack is a type of attack when an attacker is able to put themselves between two parties and intercept and influence the traffic between them. This type of attack can compromise the integrity of data in your application and is commonly carried out when you work over a public Wi fi network.
如果您的应用处理敏感数据以保护连接和数据,则传输层安全性(TLS)至关重要。 在客户端和服务器之间传输数据之前,TLS会对它进行加密,这样就不会出现袖珍嗅探或中间人攻击。 中间人攻击是一种攻击类型,当攻击者能够将自己置于两方之间并拦截并影响它们之间的流量时。 这种类型的攻击可能会损害应用程序中数据的完整性,通常在通过公共Wi Fi网络工作时会发生。
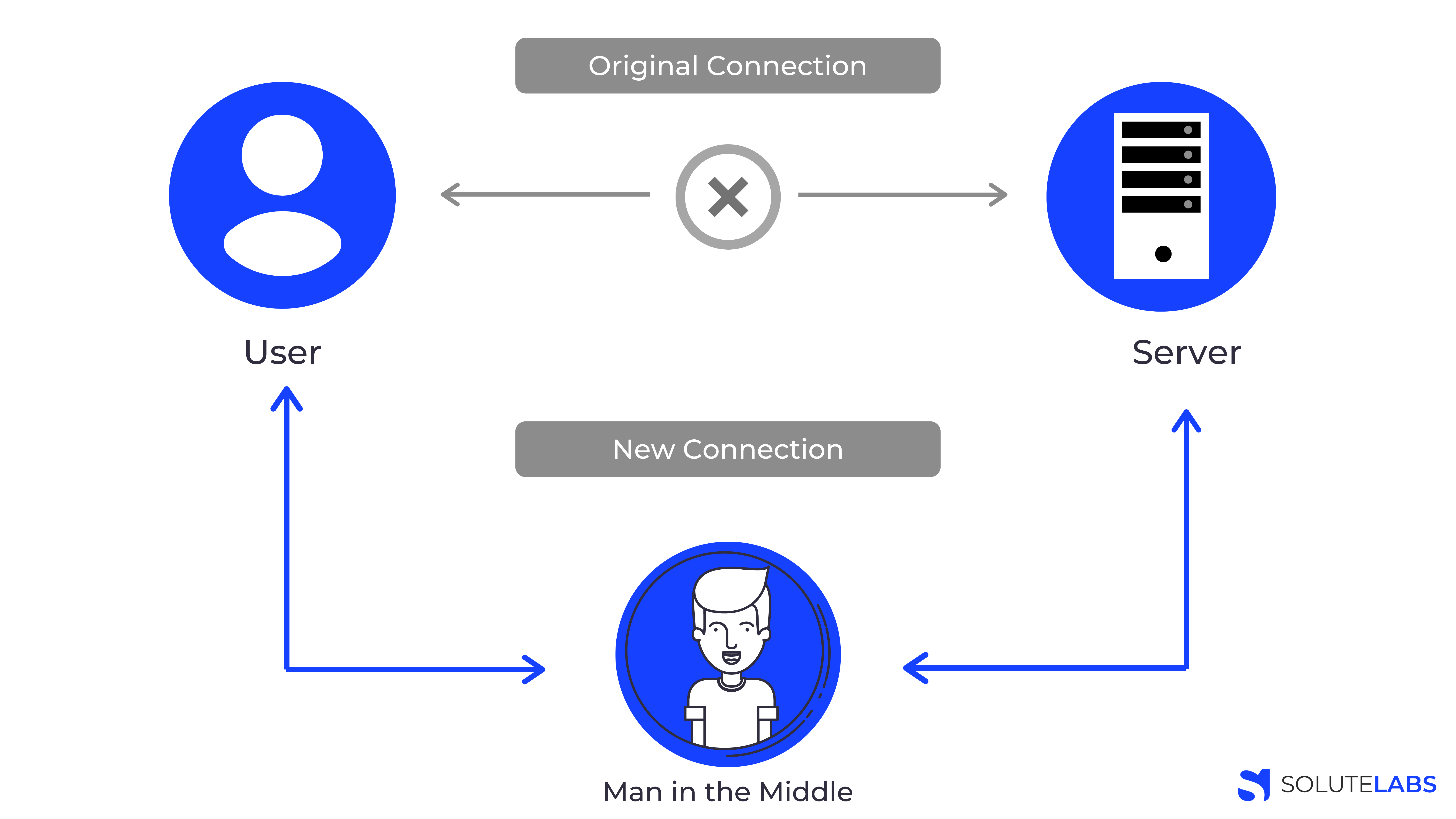
The solution: Avoiding your Node.JS application from being directly exposed to the internet is a brutal but effective way to stop MITM attacks. Terminating the SSL prior to the Node.JS stage, using a tool such as NGINX, is also a viable option. TLS is just an advanced version of the SSL, and we highly recommend using TLS to prevent any type of attack.
解决方案:避免Node.JS应用程序直接暴露于互联网是阻止MITM攻击的一种残酷但有效的方法。 使用诸如NGINX之类的工具在Node.JS阶段之前终止SSL也是可行的选择。 TLS只是SSL的高级版本,我们强烈建议使用TLS来防止任何类型的攻击。
6.转义JS,HTML和CSS输出。 (6. Escape JS, HTML and CSS output.)
Web languages such as HTML generally mix content with executable code. Your code may be in the form of an HTML paragraph that may contain a visual representation of the data along with JS executable instructions. Sometimes, JS code that was not intended to be displayed while rendering the HTML may actually get interpreted and executed by the browser. This commonly happens when content that was inserted into the database by an attacker is rendered.
HTML之类的Web语言通常将内容与可执行代码混合在一起。 您的代码可能采用HTML段落的形式,其中可能包含数据的可视表示形式以及JS可执行指令。 有时,原本打算在呈现HTML时不显示的JS代码实际上可能会被浏览器解释和执行。 当呈现攻击者插入到数据库中的内容时,通常会发生这种情况。
The solution: Instruct the browser to interpret any chunk of untrusted data as content only and never to interpret it. This technique is called Escaping. Escaping capabilities are provided by many NPM libraries and templating engines. Escaping is also sometimes called encoding, and it is a way of representing data that will not be executed or interpreted.
解决方案:指示浏览器将不可信数据的任何块都解释为仅内容,而不要解释它。 此技术称为转义。 许多NPM库和模板引擎都提供转义功能。 转义有时也称为编码,它是表示将不会执行或解释的数据的一种方式。
7.不要将机密发布到NPM注册表。 (7. Don’t publish secrets to the NPM registry.)
When working with the NPM registry, there is a high chance that you may publish some of the secrets such as API keys, passwords, or other secrets on the npm public registry. Files such as .env, which should ideally be added to a .gitignore to avoid committing it to an SCM, may find its way into your working directory. This is because files you do not want to commit to your repository also usually files you do not want to be published. There is also a file called .npmignore, which behaves exactly like .gitignore. This comes with the additional challenge that you will most likely publish a file you thought you had excluded if you try to use both.
使用NPM注册表时,很有可能会在npm公共注册表上发布某些机密,例如API密钥,密码或其他机密。 最好将.env这样的文件添加到.gitignore中,以避免将其提交到SCM,它们可能会进入您的工作目录。 这是因为您不想提交到存储库的文件通常也不想发布。 还有一个名为的文件。 npmignore ,其行为与.gitignore完全相同。 这带来了另一个挑战,如果您尝试同时使用这两个文件,则很有可能会发布您认为已排除的文件。
The solution: Use the files property in package.json, that works as a whitelist and specifies the array of files that are to be included in the package to be created and installed. Also, add a — dry-run argument to your publish command in order to see how the tarball is actually created without publishing it to the registry.
解决方案:使用package.json中的files属性,该属性用作白名单,并指定要包含在要创建和安装的包中的文件数组。 另外,在您的发布命令中添加一个– dry-run参数,以了解如何在不将tarball发布到注册表的情况下实际创建它。
8. 小心处理子进程。 (8. Be careful working with child processes.)
Shell injection attacks are one of the most common exploits on an unsecured Node.js application. In a shell injection attack, the attacker takes over the Operating System(OS) on the server and asks it to execute arbitrary commands, fully compromising the application and all its data. Using child processes and not sanitizing input data often leaves your server vulnerable to shell injection attacks. We don’t want attackers to run a command with a child process instance, which we have created from our app.
Shell注入攻击是不安全的Node.js应用程序上最常见的攻击之一。 在shell注入攻击中,攻击者将接管服务器上的操作系统(OS),并要求其执行任意命令,从而完全破坏了应用程序及其所有数据。 使用子进程而不清理输入数据通常会使您的服务器容易受到外壳注入攻击。 我们不希望攻击者使用通过我们的应用程序创建的子流程实例运行命令。
The solution: Use a child_process.exec file which will execute only a single command with a set of attributes and will not allow shell parameter expansion.
解决方案:使用child_process.exec文件,该文件将仅执行具有一组属性的单个命令,并且不允许扩展Shell参数。
9.反序列化 (9. Deserialization)
Serialization is the process of turning some object into a data format that can be later restored into the original format, and deserialization is the reversal of that process. Insecure deserialization allows deserialization and execution of malicious objects via API calls or remote code execution. The attacker can modify the application by executing remote code on application classes, which will cause a change in the behaviour during serialization. The attacker can also tamper data objects such as cookies with malicious intent.
序列化是将某些对象转换成可以稍后恢复为原始格式的数据格式的过程,反序列化是该过程的逆转。 不安全的反序列化允许通过API调用或远程代码执行反序列化和执行恶意对象。 攻击者可以通过对应用程序类执行远程代码来修改应用程序,这将导致序列化过程中行为的改变。 攻击者还可能出于恶意目的篡改Cookie等数据对象。
The solution: In order to mitigate such attacks, we use something called cross-site request forgery (CSRF). It is as simple as generating a CSRF token from our server and adding it to a hidden form field. The CSRF middleware checks if the incoming token matches what was sent before and rejects requests where the tokens don’t match.
解决方案:为了减轻此类攻击,我们使用一种称为跨站点请求伪造(CSRF)的东西。 就像从我们的服务器生成CSRF令牌并将其添加到隐藏的表单字段一样简单。 CSRF中间件检查传入令牌是否与之前发送的令牌匹配,并拒绝令牌不匹配的请求。
10.隐藏来自客户端的错误消息 (10. Hide error messages from clients)
If you do not handle errors properly in a Node.JS application, sensitive application details such as third party modules in use, server file paths, and other internal workflows of the application can be exploited. An attacker can also access the said information from a leak in the stack trace. Hence we recommend using an integrated express error handler that hides the error details by default.
如果您没有在Node.JS应用程序中正确处理错误,则可以利用敏感的应用程序详细信息,例如正在使用的第三方模块,服务器文件路径以及该应用程序的其他内部工作流程。 攻击者还可以从堆栈跟踪中的泄漏访问所述信息。 因此,我们建议使用集成的快速错误处理程序,该处理程序默认情况下隐藏错误详细信息。
The solution: If not using an integrated express error handler, you can implement your own error handling logic using custom Error objects. In case you use this approach, make sure that you don’t return the entire Error object to the client. This will prevent the leak of sensitive application details.
解决方案:如果不使用集成的Express错误处理程序,则可以使用自定义Error对象实现自己的错误处理逻辑。 如果使用这种方法,请确保不要将整个Error对象返回给客户端。 这将防止敏感应用程序详细信息的泄漏。
There you have it! Ten of the best Node.JS security practices you can implement today that can make your app more secure. For further reading, there is a tonne of information available online, and we are pretty sure our friends at Google will be more than happy to help you out.
你有它! 您今天可以实施的十种最佳Node.JS安全实践,可以使您的应用程序更安全。 为了进一步阅读,在线提供了大量信息,我们非常确定Google的朋友将非常乐意为您提供帮助。
翻译自: https://medium.com/solute-labs/npm-security-best-practices-solutelabs-34978c28f0c
npm 更新 npm




















 924
924











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








