Linux系统本身提供了相当丰富的资源管控机制,管理者可以借由这些功能来精准地将系统资源分配给不同的用户,提高系统的运作效率,而一般的用户也可以使用这样的机制来限制进程使用的系统资源。
普通用户
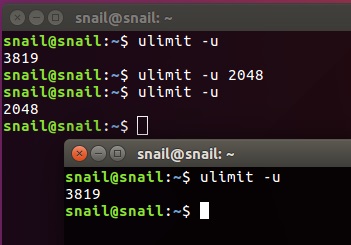
Linux系统上的普通用户若要限制自己可启动的进程数量,可以使用ulimit指令,它是 Linux 中用来限制系统资源的命令,在更改设定之前,我们可以先查询一下目前使用者可开启的进程数量上限:
$ ulimit -u
这个值可以直接使用 ulimit 来更改:
$ ulimit -u 2048
$ ulimit -u
对于普通而言,使用 ulimit 所设定的限制条件有一定的范围,它只对所在的 shell 进程以及该 shell 所衍生的子进程有效,该使用者其他的 shell 进程不受影响,也不会影像系统上其他的进程。
虽然 ulimit 的限制条件在不同的 shell 中是独立的,但是 ulimit 计算进程数目的方式却是以整个系统中该使用者所有的进程为准,因此不同的进程之间还是会互相影响,以下我们用一个简单的示例来说明。
假设有一个用户有两个不同的脚本,在开头设定脚本可开启的进程数目上限,分开控制两个不同的程式。
第一个脚本:
#!/bin/bash
# 可以开启的进程数目上限为 512
ulimit -u 512
# 执行其他指令 ...
第二个脚本:
#!/bin/bash
# 可以开启的进程数目上限为 2048
ulimit -u 2048
# 执行比较复杂的指令 ...
假设在准备执行这两个脚本时,该用户在系统上已经开启了 200 个进程,那么这时候若执行第一个脚本,则第一个脚本与其衍生的进程最多只能开启 312 个行程(也就是 512 扣掉原本系统上的 200),同样地若这时候执行第二个脚本,它只能开启 1848 个进程。
请注意 ulimit 是依照整个系统上所有该用户的进程来计算的,假如这两个脚本各需要开启 300 的行程,若同时执行的话就会多出 600 个进程,第一个脚本就会超出其 ulimit 所制定的限制,而只有第二个程式可以正常执行。
管理员用户
Linux系统管理员掌控着整个系统资源、防止系统超载也是很重要的事情,而整个系统的 ulimit 设定都写在 /etc/security/limits.conf 这个文档中,示例:
#
@student hard nproc 20
@faculty soft nproc 20
@faculty hard nproc 50
ftp hard nproc 0
第一个 domain 栏可以放用户帐号或群组,第二个 type 栏位可以放 soft(软性限制条件,可变更)或 hard(硬性限制条件,不可变更),item 则填入 nproc(代表进程数目),而最后的 value 则是要指定的进程数目上限数值。
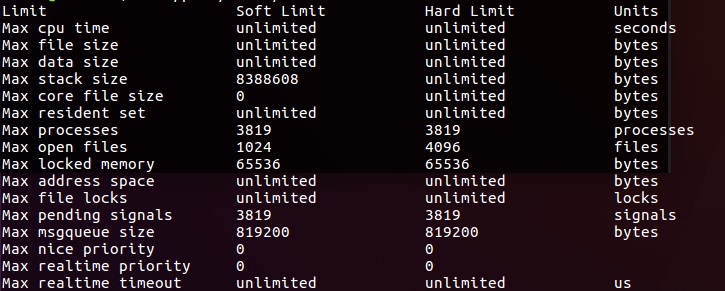
查询某进程的资源限制
cat /proc//limits # proc_id 进程ID
输出如下:
查看limits.conf帮助:
$ man limits.conf
LIMITS.CONF(5) Linux-PAM Manual LIMITS.CONF(5)
NAME
limits.conf - configuration file for the pam_limits module
DESCRIPTION
The pam_limits.so module applies ulimit limits, nice priority and
number of simultaneous login sessions limit to user login sessions.
This description of the configuration file syntax applies to the
/etc/security/limits.conf file and *.conf files in the
/etc/security/limits.d directory.
The syntax of the lines is as follows:
The fields listed above should be filled as follows:
· a username
· a groupname, with @group syntax. This should not be confused with netgroups.
· the wildcard *, for default entry.
· the wildcard %, for maxlogins limit only, can also be used with %group syntax. If the % wildcard is used alone it is identical to using * with maxsyslogins limit. With a group specified after % it limits the total number of logins of all users that are member of the group.
· an uid range specified as :. If min_uid is omitted, the match is exact for the max_uid. If max_uid is omitted, all uids greater than or equal min_uid match.
· a gid range specified as @:. If min_gid is omitted, the match is exact for the max_gid. If max_gid is omitted, all gids greater than or equal min_gid match. For the exact match all groups including the user's supplementary groups are examined. For the range matches only the user's primary group is examined.
· a gid specified as %: applicable to maxlogins limit only. It limits the total number of logins of all users that are member of the group with the specified gid.
NOTE: group and wildcard limits are not applied to the root user. To set a limit for the root user, this field must contain the literal username root.
hard for enforcing hard resource limits. These limits are set by the superuser and enforced by the Kernel. The user cannot raise his requirement of system resources above such values.
soft for enforcing soft resource limits. These limits are ones that the user can move up or down within the permitted range by any pre-existing hard limits. The values specified with this token can be thought of as default values, for normal system usage.
-
for enforcing both soft and hard resource limits together.
Note, if you specify a type of '-' but neglect to supply the item and value fields then the module will never enforce any limits on the specified user/group etc. .
core
limits the core file size (KB)
data
maximum data size (KB)
fsize
maximum filesize (KB)
memlock
maximum locked-in-memory address space (KB)
nofile
maximum number of open files
rss
maximum resident set size (KB) (Ignored in Linux 2.4.30 and higher)
stack
maximum stack size (KB)
cpu
maximum CPU time (minutes)
nproc
maximum number of processes
as
address space limit (KB)
maxlogins
maximum number of logins for this user except for this with uid=0 maxsyslogins
maximum number of all logins on system priority
the priority to run user process with (negative values boost process priority)
locks
maximum locked files (Linux 2.4 and higher)
sigpending
maximum number of pending signals (Linux 2.6 and higher)
msgqueue
maximum memory used by POSIX message queues (bytes) (Linux 2.6 and higher)
nice
maximum nice priority allowed to raise to (Linux 2.6.12 and higher) values: [-20,19]
rtprio
maximum realtime priority allowed for non-privileged processes
(Linux 2.6.12 and higher)
chroot
the directory to chroot the user to
All items support the values -1, unlimited or infinity indicating no
limit, except for priority and nice.
If a hard limit or soft limit of a resource is set to a valid value,
but outside of the supported range of the local system, the system may
reject the new limit or unexpected behavior may occur. If the control
value required is used, the module will reject the login if a limit
could not be set.
In general, individual limits have priority over group limits, so if
you impose no limits for admin group, but one of the members in this
group have a limits line, the user will have its limits set according
to this line.
Also, please note that all limit settings are set per login. They are
not global, nor are they permanent; existing only for the duration of
the session. One exception is the maxlogin option, this one is system
wide. But there is a race, concurrent logins at the same time will not
always be detect as such but only counted as one.
In the limits configuration file, the '#' character introduces a
comment - after which the rest of the line is ignored.
The pam_limits module does report configuration problems found in its
configuration file and errors via syslog(3).
EXAMPLES
These are some example lines which might be specified in
/etc/security/limits.conf.
* soft core 0
root hard core 100000
* hard nofile 512
@student hard nproc 20
@faculty soft nproc 20
@faculty hard nproc 50
ftp hard nproc 0
@student - maxlogins 4
:123 hard cpu 5000
@500: soft cpu 10000
600:700 hard locks 10
SEE ALSO
pam_limits(8), pam.d(5), pam(7), getrlimit(2)getrlimit(3p)
AUTHOR
pam_limits was initially written by Cristian Gafton
Linux-PAM Manual 09/19/2013 LIMITS.CONF(5)




















 165
165











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








