Site-site ×××ipsec
实验报告
<?xml:namespace prefix = o ns = "urn:schemas-microsoft-com:office:office" />
1.
实验拓扑:
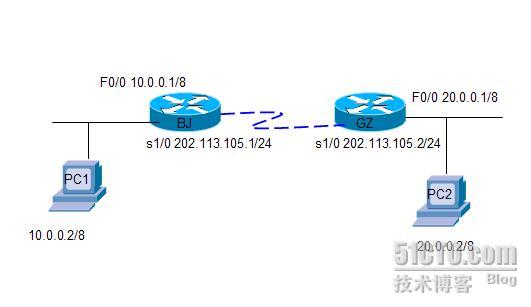
2.
实验目的:
2.1
按要求正确连接路由器
2.2GZ
办事处需要用
×××
方式连入
BJ
总部
3.
操作详细步骤
Setp 1.
按要求配置相应的接口
IP
路由器
BJ
配置如下
Router>en
Router#conf t
Router(config)#ho BJ
BJ(config)#int f0/0
BJ(config-if)#ip add <?xml:namespace prefix = st1 ns = "urn:schemas-microsoft-com:office:smarttags" />10.0.0.1 255.0.0.0
BJ(config-if)#no shut
BJ(config-if)#exit
BJ(config)#int s1/0
BJ(config-if)#ip add 202.113.105.1 255.255.255.0
BJ(config-if)#no shut
BJ(config-if)#
*Mar 1 00:05:02.587: %LINK-3-UPDOWN: Interface Serial1/0, changed state to up
*Mar 1 00:05:03.587: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial1/0,
changed state to up
BJ(config-if)#exit
路由器
GZ
配置如下:
Router>en
Router#conf t
Router(config)#ho GZ
GZ(config)#int f0/0
GZ(config-if)#ip add 20.0.0.1 255.0.0.0
GZ(config-if)#no shut
GZ(config-if)#exit
GZ(config)#int s1/0
GZ(config-if)#ip add 202.113.105.2 255.255.255.0
GZ(config-if)#no shut
GZ(config-if)#exit
GZ(config)#
PC1
配置如下:
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#ho pc2
pc2(config)#no ip routing
pc1(config)#int f0/0
pc1(config-if)#ip add 10.0.0.2 255.0.0.0
pc1(config-if)#no shut
pc1(config)#ip default-gateway 10.0.0.1
pc1(config)#exit
pc1#ping 20.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
PC2
配置如下:
Router(config)#ho pc2
pc2(config)#no ip routing
pc2(config)#int f0/0
pc2(config-if)#ip add 20.0.0.2 255.0.0.0
pc2(config-if)#no shut
pc2(config-if)# exit
pc2(config)#ip default-gateway 20.0.0.1
pc2(config)#exit
pc2#ping 10.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
配置默认路由是全网互通
路由器
BJ
配置如下
BJ(config)#ip route 0.0.0.0 0.0.0.0 s1/0
BJ(config)#exit
BJ#show ip rou
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
C 202.113.105.0/24 is directly connected, Serial1/0
C 10.0.0.0/8 is directly connected, FastEthernet0/0
S* 0.0.0.0/0 is directly connected, Serial1/0
路由器
GZ
配置如下:
GZ(config)#ip route 0.0.0.0 0.0.0.0 s1/0
验证:
Pc1#ping 20.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 124/198/340 ms
pc2#ping 10.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 124/198/340 ms
Step 2
组建
×××
配置
IKE
协商
路由器
BJ
配置如下
BJ(config)#crypto isakmp policy 1
// 建立IKE协商策略
BJ(config-isakmp)#hash md5
// 建立密钥验证所用的算法
BJ(config-isakmp)#authentication pre-share
//设置路由器要使用预先共享的密钥
BJ(config-isakmp)#crypto isakmp key benet address 202.113.105.2
//设置共享密钥和对端地址
路由器
GZ
配置如下:
GZ(config)#crypto isakmp policy 1
/ 建立IKE协商策略
GZ(config-isakmp)#hash md5
GZ(config-isakmp)#authentication pre-share
GZ(config-isakmp)#crypto isakmp key benet address 202.113.105.1
配置
Ipsec
相关参数:
路由器
BJ
配置如下
//配置IPSec的传输模式
BJ(config)#crypto ipsec transform-set cisco ah-md5-hmac esp-des
BJ(cfg-crypto-trans)#exit
//指定Crypto访问列表
BJ(config)#$ 101 permit ip 10.0.0.0 0.255.255.255 20.0.0.0 0.255.255.255
路由器
GZ
配置如下
GZ(config)#crypto ipsec transform-set cisco ah-md5-hmac esp-des
GZ(cfg-crypto-trans)#exit
GZ(config)#$ 101 permit ip 20.0.0.0 0.255.255.255 10.0.0.0 0.255.255.255
配置端口的应用:
路由器
BJ
配置如下
BJ(config)#crypto map benetmap 1 ipsec-isakmp
//创建Crypto Map
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
BJ(config-crypto-map)#set peer 202.113.105.2 //
指定×××对端的IP地址
BJ(config-crypto-map)#set transform-set cisco
//
指定Crypto Map所使用的传输模式
BJ(config-crypto-map)#match address 101 //
指定Crypto Map使用的访问控制列表
BJ(config-crypto-map)#exit
BJ(config)# int s1/0 //
应用Crypto Map到端口
BJ(config-if)#crypto map benetmap
BJ(config-if)#
*Mar 1 00:17:46.251: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
BJ(config-if)#exit
BJ(config)#exit
BJ#
*Mar 1 00:18:01.571: %SYS-5-CONFIG_I: Configured from console by console
*Mar 1 00:18:14.755: %CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd packet not an IPSEC p
acket.
(ip) vrf/dest_addr= /10.0.0.2, src_addr= 20.0.0.2, prot= 1
Pc1#ping 20.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
pc2#ping 10.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
路由器
GZ
配置如下
GZ(config)#crypto map benetmap 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
GZ(config-crypto-map)#set peer 202.113.105.1
GZ(config-crypto-map)#set transform-set cisco
GZ(config-crypto-map)#match address 101
GZ(config-crypto-map)#exit
GZ(config)#int s1/0
GZ(config-if)#crypto map benetmap
GZ(config-if)#exit
*Mar 1 00:19:47.523: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is O
N
GZ(config)#exit
Pc1#ping 20.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 200/308/448 ms
pc2#ping 10.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 112/348/876 ms
Setp3.
检查
×××
配置
显示所有尝试协商的策略以及最后的默认策略设置
BJ#show crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
显示在路由器上设置的
transform-set
BJ#show crypto ipsec transform-set
Transform set cisco: { ah-md5-hmac }
will negotiate = { Tunnel, },
{ esp-des }
will negotiate = { Tunnel, },
显示当前安全联盟使用的设置
BJ#show crypto ipsec sa
interface: Serial1/0
Crypto map tag: benetmap, local addr 202.113.105.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.0.0.0/255.0.0.0/0/0)
remote ident (addr/mask/prot/port): (20.0.0.0/255.0.0.0/0/0)
current_peer 202.113.105.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 12, #pkts encrypt: 12, #pkts digest: 12
#pkts decaps: 12, #pkts decrypt: 12, #pkts verify: 12
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 8, #recv errors 0
local crypto endpt.: 202.113.105.1, remote crypto endpt.: 202.113.105.2
path mtu 1500, ip mtu 1500
current outbound spi: 0x812173DD(2166453213)
inbound esp sas:
spi: 0xC9C0A74C(3384846156)
transform: esp-des ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: benetmap
sa timing: remaining key lifetime (k/sec): (4546831/3474)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
spi: 0xD18A5E16(3515506198)
transform: ah-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: benetmap
sa timing: remaining key lifetime (k/sec): (4546831/3472)
replay detection support: Y
Status: ACTIVE
inbound pcp sas:
outbound esp sas:
spi: 0x812173DD(2166453213)
transform: esp-des ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: benetmap
sa timing: remaining key lifetime (k/sec): (4546831/3472)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
spi: 0xE3081833(3808958515)
transform: ah-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: benetmap
sa timing: remaining key lifetime (k/sec): (4546831/3471)
replay detection support: Y
Status: ACTIVE
outbound pcp sas:
显示所有配置在路由器上的crypto map
BJ#show crypto map
Crypto Map "benetmap" 1 ipsec-isakmp
Peer = 202.113.105.2
Extended IP access list 101
access-list 101 permit ip 10.0.0.0 0.255.255.255 20.0.0.0 0.255.255.
255
Current peer: 202.113.105.2
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
cisco,
}
Interfaces using crypto map benetmap:
Serial1/0
BJ#show crypto isakmp sa
dst src state conn-id slot status
202.113.105.2 202.113.105.1 QM_IDLE 1 0 ACTIVE
试验总结:
IPSec ×××
的配置:
启动
IKE
:
Router(config)#crypto isakmp enable
建立
IKE
协商策略:
Router(config)#crypto isakmp policy priority
*priority
:取值范围
1~1000
,数值越小,优先级越高
配置
IKE
协商策略:
Router(config-isakmp)#authentication pre-share //
使用预定义密钥
Router(config-isakmp)#encryption {des | 3des} //
加密算法
Router(config-isakmp)#hash {md5 | sha1} //
认证算法
Router(config-isakmp)#lifetime seconds //SA
活动时间
设置共享密钥和对端地址:
Router(config)#crypto isakmp key keystring address peer-address
*keystring
:密钥;
peer-address
:对端
IP
设置传输模式集:
Router(config)#crypto ipsec transform-set transform-set-name transform1 [transform 2 [transform3]]
*transform
:定义了使用
AH
还是
ESP
协议,以及相应协议所用的算法
配置保护访问控制列表:
Router(config)#access-list access-list-number {deny | permit} protocol source source-wildcard destination destination-wildcard
*
用来定义哪些报文需要经过
IPSec
加密后发送,哪些报文直接发送
创建端口
Crypto Maps
:
Router(config)#crypto map map-name seq-num ipsec-isakmp
*seq-num
:
Map
优先级,取值范围
1~65535
,值越小,优先级越高
配置
Crypto Maps
:
Router(config-crypto-map)#match address access-list-number
Router(config-crypto-map)#set peer ip_address //
对端
IP
地址
Router(config-crypto-map)#set transform-set name //
传输模式的名称
应用
Crypto Maps
到端口:
Router(config-if)#crypto map map-name
检查
IPSec
配置:
查看
IKE
策略:
Router#show crypto isakmp policy
查看
IPSec
策略:
Router#show crypto ipsec transform-set
查看
SA
信息:
Router#show crypto ipsec sa
查看加密映射:
Router#show crypto map
转载于:https://blog.51cto.com/dongwei/62969





















 5060
5060











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








