1. 证书
数字证书就是通讯中标志通讯各方身份信息的一系列数据,提供了一种在Internet上验证您身份的方式,其作用类似于司机的驾驶执照或日常生活中的身份证。
简单说明:数字证书由 用户信息 + 公钥 + 私钥组成;
公私钥:
又名非对称密钥“相互加密,相互解密”;
由公钥加密的数据只能由私钥进行解密,由私钥加密的数据只能用公钥解密;
公钥一般都公开给用户,私钥不对外泄露;
传统的做法:
用 “123”加密数据, 解密也是用 “123” 这种称为对称加密算法
CA
证书签发机构,大家都信任的权威机构;
CA 证书
用于签发用户证书的证书;
谁给 CA 签发证书: (CA 是自己给自己签发,又名自签名证书,顶级CA 证书),当然 CA 还可以签发二级 CA 等等, 子CA 也是可以签发用户证书的,也就是所谓的 证书链;
签发证书过程
由用户提供个人信息主要包括(国家、省份、城市、公司、部门、用户名、邮箱)
CA 对用户信息进去确认(这些信息代表的是否是这个人),为用户生成公私钥对,将用户的信息和公钥按照一定的格式(X509)生成一个文件叫证书生成请求文件(CSR),最后用CA的私钥对CSR 文件进行签名,生成数字证书。
第二种做法就是由用户提供 CSR 文件给 CA,CA签名生成数字证书。
签名:
以电子形式存在于数据信息之中的,或作为其附件的或逻辑上与之有联系的数据,可用于辨别数据签署人的身份,并表明签署人对数据信息中包含的信息的认可。
简单的说就是对用户信息(CSR)文件进行HASH处理,其中hash算法主要有md5, sha1, sha256等获取CSR 的消息摘要,让后用 CA 的私钥进行对消息摘要加密存放在证书里面。
消息摘要:
就是 MD5 等算法计算出来的值,特点是 计算值有改动消息摘要 就会不一样(也有可能一样hash 碰撞)。
怎么确认用户身份:
就是 拿CA 的公钥解密获取消息摘要,然后按照相同的HASH 算法计算消息摘要,比较两个消息摘要是否相同,最后确认用户信息(包括国家、省份、城市、公司、部门、用户名、邮箱)。
CRL 证书吊销列表
CRL 可以简单的理解为一个记录了用户证书序列号的文件,该文件由CA签发发布,记录了的证书序列号表示该证书已经失效。也就是 CRL 里面记录的证书序列号表示由这个CA签发的证书并且序列号在CRL文件里面的都已经是无效了的证书。
OCSP 在线证书状态查询
通过 http(https)的方式来查询证书是否有效;
一般 CRL 不是每一天都发布,而是一定周期性的发布;但是在这个周期内有可能有其他的证书被吊销。
比如:
6.1 发布了 CRL 文件, 下次颁发时间为 6.15日;那么在 6.1 以后吊销的证书CRL 里面都没有记录 OCSP 就是为了解决这个问题,通过 http(https)的方式直接去CA服务器进行查询;
无线新产品证书相关
我们设备里面的证书主要有三个用途:
1. CA 证书, 用于验证由该CA签发的用户证书;
2. 服务器证书 提供给客户端验证的,告诉客户端你连接的这台就是你想要连接的而不是一台钓鱼机器(客户端验证服务器证书是可选的)
3. 设备证书 主要用于做 https 处理;
服务器证书,设备证书,用户证书区别
本质上他们其实是没有区别的,只是拥有的证书权限(目的)不同;
比如 CA 证书 就有签发证书权限,一般的证书是没有签发证书的权限的,这个是生成证书的时候可以进行设置;这个权限选项比较都啦“服务器身份验证、客户端身份验证、代码签名、安全电子邮件等等”
Openssl 使用手册
1. 公私钥对
openssl genrsa 2048 > rsa.txt // 或者
openssl genrsa -out rsa.txt 1024
说明: 产生2048 位的私钥数据保存在 rsa.txt 文件中 。
openssl rsa -in rsa.txt -pubout -out pubkey.txt
说明: 从私钥数据中提取公钥并且保存到 pubkey.txt 文件中。
openssl rsa -in rsa.txt -des3 -out privkey.key
说明: 对私钥明文数据进行加密保存到文件 privkey.key 中。
openssl rsa -in privkey.key -out rsa.txt
说明: 对加密的私钥文件 privkey.key 进行解密,将解密后的明文私钥保存到 rsa.txt 文件中。
openssl genrsa -des3 -out privkey.key 1024
说明: 产生 1024 位的私钥数据并且使用 des3 加密算法对私钥数据进行加密。
openssl rsa -noout -text -in myserver.key
说明: 查看私钥数据信息(可以看到公钥数据信息)
openssl rsa -noout -text -pubin -in pubkey.key -modulus
说明: 查看公钥文件相关信息
openssl genpkey -algorithm RSA -out privatekey.pem -pass pass:1234 -des-ede3-cbc
说明: 使用RSA算法产生公私钥对并且使用des-ede3-cbc对称加密算法加密私钥数据,加密密码为 “1234”
2. 使用公钥和私钥实现加密与解密操作
openssl rsautl -encrypt -in 待加密文件 -inkey 公钥 -pubin -out 密文文件
说明: 使用公钥对指定的文件进行加密操作。
openssl rsautl -decrypt -in 密文文件 -inkey 私钥 -out 明文文件
说明: 使用私钥解密公钥加密后的数据。
3. Hash 与 签名
openssl dgst <-md5 / - sha1 / -ripemd160> -out <印章文件> <原始文件>
说明: 计算原始文件的 hash<摘要>值, 保存到指定的文件中<印章文件>
openssl rsautl -sign -in <印章文件> -inkey <RSA 私钥> -out <签名文件>
说明: 对<印章文件>进行签名操作。
openssl rsautl -verify -in <签名文件> -pubin -inkey <RSA 公钥> -out <印章文件>
说明: 解密签名文件得到<印章文件>
4. 证书操作
CSR是证书请求文件的缩写。它包括了用户的基本信息以及一个密钥。你需要填写信息来生成CSR文件,并提供给证书服务商。证书服务商需要通过CSR文件来生成证书。
网站推荐: http://www.umich.edu/~x509/ssleay/index.html
在较新版本的OpenSSL中,生成CSR和私钥已经能一行搞定:
openssl req -new -nodes -newkey rsa:2048 -keyout xx.key -out xx.csr
说明: 如果没有 (-newkey rsa:2048) 默认为 openssl.cnf 文件中指定的位数。
openssl req -noout -text -in server.csr
说明: 查看 CSR 文件相关信息
自签名CA证书:
Openssl genrsa -des3 -out ./demoCA/private/cakey.pem 1024
openssl req -new -x509 -days 3650 -key ./demoCA/private/cakey.pem -out ./demoCA/cacert.pem
签发用户证书
openssl ca -in userreq.pem -out usercert.pem
# 这种方式适合,配置了完整的 openssl.cnf 文件, CA 证书和 CA 证书的私钥都放入到指定的地方,创建了 index.txt 和 serial 文件, 具体配置可以参考 openssl.cnf 文件
创建自签名CA 颁发用户证书
Openssl genrsa -des3 -out client.key 1024
Openssl req -new -key client.key -out client.csr
Openssl ca -in client.csr -out client.crt -config ./openssl.cnf
或者:
Openssl genrsa -des3 -out client.key 1024
Openssl x509 -req -in client.csr -out client.crt -CA ./ca.crt -CAkey ./ca.key -CAcreateserial -days 3650 -config ./openssl.cnf
这种签发用户证书的方式适合,没有怎么严格配置 openssl.cnf 文件的方式
# 序列号的指定的方式
-CAcreateserial 说明:随机指定一个序列号
-CAserial 序列号文件 说明:使用序列号文件中的数字作为序列号,数字必须为偶数个
-set_serial num 说明: 使用指定的数作为序列号
合并为 p12 证书
openssl pkcs12 -export -in client.crt -inkey client.key -out client.p12
要求手动输入密码,如果不想设置密码可以直接按回车
openssl pkcs12 -export -in client.crt -inkey client.key -out client.p12 -passout pass:”qwer1234”
设置p12默认密码为 qwer1234, 如果不想输入密码,而且密码为空,修改为入下形式
-passout pass:””
检测证书的合法性
openssl verify -CAfile ca.crt client.crt
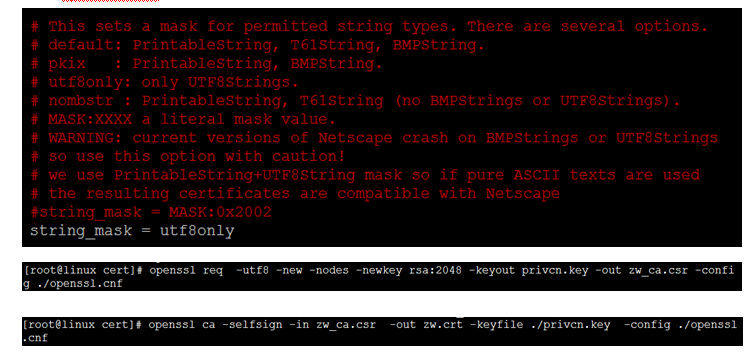
生成UTF-8 格式CA证书
修改 openssl.cnf 文件
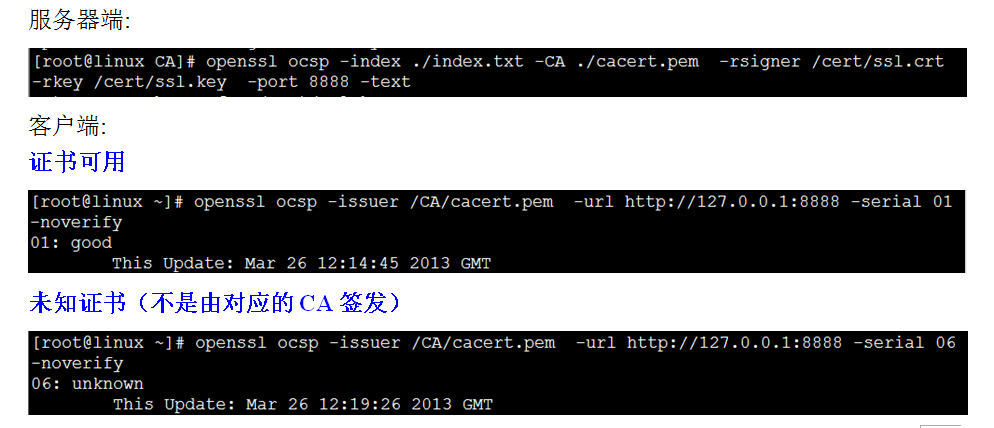
ocsp 检测
服务器端:
openssl ocsp -index ./CA/index.txt -CA ./ca.crt -rsigner ./server.crt -rkey ./server.key -port 8888 -text
客户端:
openssl ocsp -issuer ca.crt -url http://127.0.0.1:8888 -serial 01 -VAfile server.crt
说明: 服务器和客户端的 -CA 与 -issuer 后面都是接 ca 证书
服务器端的 -rsigner 和 -rkey 应该是一对 ./server.crt 是证书 ./server.key 是私钥, 用于对 传输过程中的 ocsp 消息进行签名
客户端的 -VAfile 的 ./server.crt 和 服务器端的 -rsigner 是一样的 都是证书, 客户端用于解签名数据,判断 ocsp 在传输过程中是否被篡改 。
-serial 后边参数为 待验证证书的序列号 。
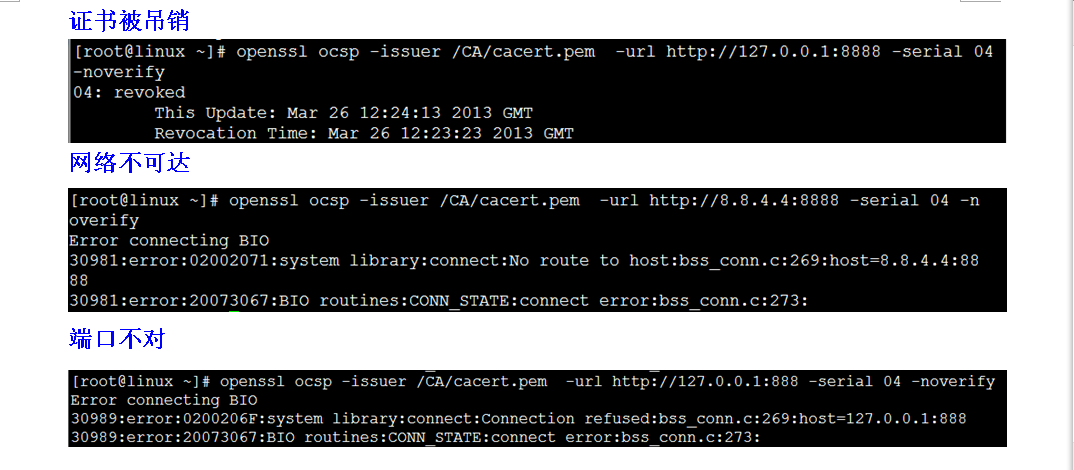
CRL 处理
吊销一张证书:
openssl ca -revoke xx.pem
生成 CRL
openssl ca -gencrl -out xx.crl
验证CRL签名
openssl crl -in crl.crl -CAfile ./ca.crt -noout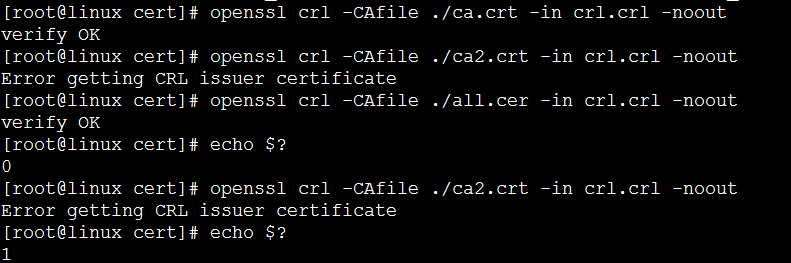
查看 CRL
openssl crl -noout -text -in xx.crl
如果 CRL 为 DER 编码:
openssl crl -noout -text -in xx.crt -inform DER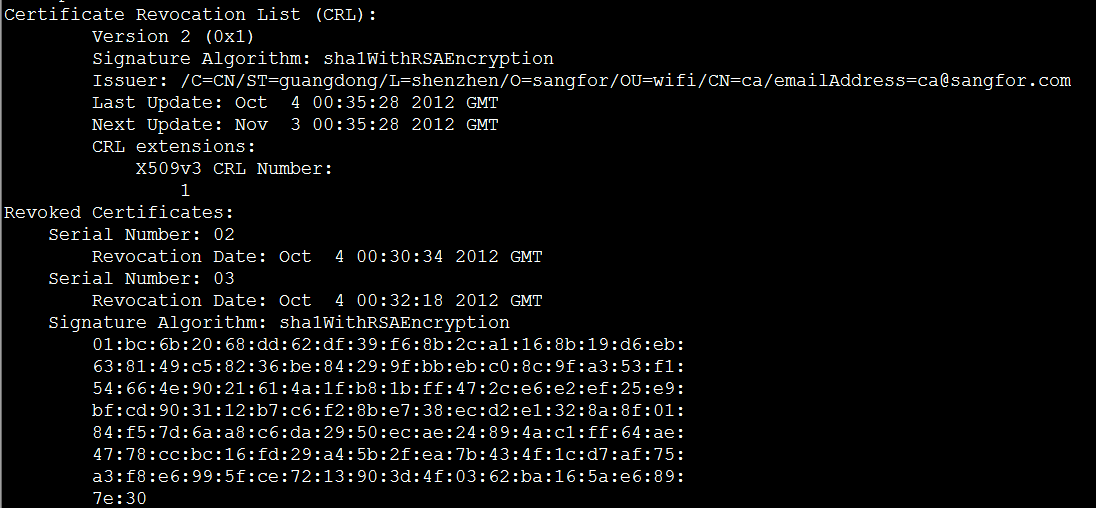
注意: crlnumber 记录了 CRL 数字:
证书转换:
openssl 命令在没有指定证书格式的情况下为 pem 格式的证书。
(一) pfx 和 p12 转换为 pem
openssl pkcs12 -in xx.pfx -out xx.pem -nodes
-nodes 表示 私钥以明文的形式保存在 xx.pem 文件中
(二) DER 证书转换为PEM 证书
openssl x509 -inform DER -in der.cer -outform PEM -out xx.pem
证书信息结构
openssl.conf 配置目录树:
5. Openssl 版本信息:
[root@linux cert]# openssl version -a
OpenSSL 0.9.8e-fips-rhel5 01 Jul 2008
built on: Mon Jun 29 18:09:52 EDT 2009
platform: linux-elf
options: bn(64,32) md2(int) rc4(idx,int) des(ptr,risc1,16,long) blowfish(idx)
compiler: gcc -fPIC -DOPENSSL_PIC -DZLIB -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -DKRB5_MIT -I/usr/kerberos/include -DL_ENDIAN -DTERMIO -Wall -O2 -g -pipe -Wall -Wp,-D_FORTIFY_SOURCE=2 -fexceptions -fstack-protector --param=ssp-buffer-size=4 -m32 -march=i686 -mtune=generic -fasynchronous-unwind-tables -Wa,--noexecstack -DOPENSSL_USE_NEW_FUNCTIONS -fno-strict-aliasing -DOPENSSL_BN_ASM_PART_WORDS -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DSHA1_ASM -DMD5_ASM -DRMD160_ASM -DAES_ASM
OPENSSLDIR: "/etc/pki/tls"
engines: padlock dynamic
Openssl 支持的功能 :
Standard commands
asn1parse ca ciphers crl crl2pkcs7
dgst dh dhparam dsa dsaparam
enc engine errstr gendh gendsa
genrsa nseq ocsp passwd pkcs12
pkcs7 pkcs8 prime rand req
rsa rsautl s_client s_server s_time
sess_id smime speed spkac verify
version x509
Message Digest commands (see the `dgst' command for more details)
md2 md4 md5 rmd160 sha
sha1
Cipher commands (see the `enc' command for more details)
aes-128-cbc aes-128-ecb aes-192-cbc aes-192-ecb aes-256-cbc
aes-256-ecb base64 bf bf-cbc bf-cfb
bf-ecb bf-ofb cast cast-cbc cast5-cbc
cast5-cfb cast5-ecb cast5-ofb des des-cbc
des-cfb des-ecb des-ede des-ede-cbc des-ede-cfb
des-ede-ofb des-ede3 des-ede3-cbc des-ede3-cfb des-ede3-ofb
des-ofb des3 desx rc2 rc2-40-cbc
rc2-64-cbc rc2-cbc rc2-cfb rc2-ecb rc2-ofb
rc4 rc4-40
证书格式转换:
证书格式简介及不同格式之间的转换方式
1.证书格式
PEM 格式
PEM格式通常用于数字证书认证机构(Certificate Authorities,CA),扩展名为.pem, .crt, .cer, and .key。内容为Base64编码的ASCII码文件,有类似"-----BEGIN CERTIFICATE-----" 和 "-----END CERTIFICATE-----"的头尾标记。服务器认证证书,中级认证证书和私钥都可以储存为PEM格式(认证证书其实就是公钥)。Apache和类似的服务器使用PEM格式证书。
DER 格式
DER格式与PEM不同之处在于其使用二进制而不是Base64编码的ASCII。扩展名为.der,但也经常使用.cer用作扩展名,所有类型的认证证书和私钥都可以存储为DER格式。Java使其典型使用平台。
PKCS#7/P7B 格式
PKCS#7 或 P7B格式通常以Base64的格式存储,扩展名为.p7b 或 .p7c,有类似BEGIN PKCS7-----" 和 "-----END PKCS7-----"的头尾标记。PKCS#7 或 P7B只能存储认证证书或证书路径中的证书(就是存储认证证书链,本级,上级,到根级都存到一个文件中)。不能存储私钥,Windows和Tomcat都支持这种格式。
PKCS#12/PFX 格式
PKCS#12 或 PFX格式是以加密的二进制形式存储服务器认证证书,中级认证证书和私钥。扩展名为.pfx 和 .p12,PXF通常用于Windows中导入导出认证证书和私钥。
PEM to DER
openssl x509 -outform der -in certificate.pem -out certificate.der
编码转换: -inform DER -outform PEM 表示输入为 DER 编码 输出为 PEM 编码
或者: -inform PEM -outform DER 表示输入为 PEM 编码 输出为 DER编码
PEM to P7B
openssl crl2pkcs7 -nocrl -certfile certificate.cer -out certificate.p7b -certfile CACert.cer
PEM to PFX
openssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in certificate.crt -certfile CACert.crt
DER to PEM
openssl x509 -inform der -in certificate.cer -out certificate.pem
P7B to PEM
openssl pkcs7 -print_certs -in certificate.p7b -out certificate.cer
PFX to PEM
openssl pkcs12 -in certificate.pfx -out certificate.cer -nodes
6. 获取 X509 证书信息
获取序列号:
openssl x509 -in ./user1.crt -serial -noout
获取 subject 字段
openssl x509 -in ./ca.crt -noout -subject
获取 issuer 字段
openssl x509 -in ./user1.crt -issuer -noout
获取 md5 指纹值
openssl x509 -md5 -in ./user1.crt -noout -fingerprint
获取 sha1 指纹值
openssl x509 -sha1 -in ./user1.crt -noout -fingerprint
获取生效和失效时间
openssl x509 -dates -in ./user1.crt -noout
获取 E-mail 信息
openssl x509 -email -in ./user1.crt -noout
或取 subject 的 hash 值
openssl x509 -subject_hash -in ./user1.crt -noout
获取 issuer 的 hash 值
openssl x509 -issuer_hash -in ./user1.crt -noout
获取生效时间
openssl x509 -startdate -in ./user1.crt -noout
获取失效时间
openssl x509 -enddate -in ./user1.crt -noout
获取 modulus 值
openssl x509 -modulus -in ./user1.crt -noout
获取公钥数据
openssl x509 -pubkey -in ./user1.crt -noout
查看证书相关功能(用途)
openssl x509 -purpose -in ./user1.crt -noout
查看 X509 证书 全部信息:
[root@linux cert.old]# openssl x509 -in ./ca.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f2:66:56:7d:a3:bf:6b:67
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=CN, ST=guangdong, L=shenzhen, O=sangfor, OU=wifi, CN=ca/emailAddress=ca@sangfor.com
Validity
Not Before: Sep 16 00:52:28 2012 GMT
Not After : Sep 14 00:52:28 2022 GMT
Subject: C=CN, ST=guangdong, L=shenzhen, O=sangfor, OU=wifi, CN=ca/emailAddress=ca@sangfor.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:f2:dc:9b:b7:bb:61:c3:e7:1e:4d:76:76:cb:46:
3c:47:e7:3b:12:d5:73:f7:e8:82:a2:c8:ee:9f:fa:
a7:96:6f:05:3e:c7:35:fe:21:d2:52:92:95:e2:78:
92:ce:7c:e3:40:61:dc:0a:64:f4:3b:bc:ad:0a:32:
6e:d2:7d:0d:73:67:27:75:93:98:f3:6e:ff:25:25:
bc:09:34:a0:9e:a8:3e:1b:77:da:96:99:c8:5f:75:
85:51:bf:3a:21:d2:b6:ae:41:15:7f:42:22:5b:4d:
3e:21:6d:8e:4a:71:4f:cf:13:9f:5b:1c:51:70:37:
e6:e2:cd:39:2d:68:a3:98:09
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
FC:0A:0B:63:0D:14:CB:5F:30:33:16:32:81:04:B1:52:67:9B:25:B3
X509v3 Authority Key Identifier:
keyid:FC:0A:0B:63:0D:14:CB:5F:30:33:16:32:81:04:B1:52:67:9B:25:B3
DirName:/C=CN/ST=guangdong/L=shenzhen/O=sangfor/OU=wifi/CN=ca/emailAddress=ca@sangfor.com
serial:F2:66:56:7D:A3:BF:6B:67
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha1WithRSAEncryption
84:50:30:99:f5:70:c5:d3:45:02:4b:63:fa:dd:71:1b:ec:3c:
e1:20:1c:35:5b:61:ba:35:17:10:21:6b:d8:1f:22:c3:e6:80:
27:7d:f4:28:00:4b:57:38:89:06:67:03:be:93:14:87:09:c0:
f0:28:36:db:2a:a8:07:20:35:7f:01:47:58:df:c9:cd:f8:3f:
a2:26:42:e5:45:18:e7:31:8d:a0:0e:f3:42:69:9f:c5:44:5b:
61:d5:54:f8:7a:8b:06:11:88:9d:26:d9:24:54:15:94:d2:91:
7c:1f:49:e8:3f:37:6e:8f:8e:58:a1:3f:8f:f9:87:6f:73:37:
71:e6
以 C 语言风格显示证书信息
[root@linux cert.old]# openssl x509 -C -in ./user1.crt -noout
/* subject:/C=CN/ST=guangdong/O=sangfor/OU=wifi/CN=user1/emailAddress=user1@sangfor.com */
/* issuer :/C=CN/ST=guangdong/L=shenzhen/O=sangfor/OU=wifi/CN=ca/emailAddress=ca@sangfor.com */
unsigned char XXX_subject_name[118]={
0x30,0x74,0x31,0x0B,0x30,0x09,0x06,0x03,0x55,0x04,0x06,0x13,0x02,0x43,0x4E,0x31,
0x12,0x30,0x10,0x06,0x03,0x55,0x04,0x08,0x13,0x09,0x67,0x75,0x61,0x6E,0x67,0x64,
0x6F,0x6E,0x67,0x31,0x10,0x30,0x0E,0x06,0x03,0x55,0x04,0x0A,0x13,0x07,0x73,0x61,
0x6E,0x67,0x66,0x6F,0x72,0x31,0x0D,0x30,0x0B,0x06,0x03,0x55,0x04,0x0B,0x13,0x04,
0x77,0x69,0x66,0x69,0x31,0x0E,0x30,0x0C,0x06,0x03,0x55,0x04,0x03,0x13,0x05,0x75,
0x73,0x65,0x72,0x31,0x31,0x20,0x30,0x1E,0x06,0x09,0x2A,0x86,0x48,0x86,0xF7,0x0D,
0x01,0x09,0x01,0x16,0x11,0x75,0x73,0x65,0x72,0x31,0x40,0x73,0x61,0x6E,0x67,0x66,
0x6F,0x72,0x2E,0x63,0x6F,0x6D,
};
unsigned char XXX_public_key[162]={
0x30,0x81,0x9F,0x30,0x0D,0x06,0x09,0x2A,0x86,0x48,0x86,0xF7,0x0D,0x01,0x01,0x01,
0x05,0x00,0x03,0x81,0x8D,0x00,0x30,0x81,0x89,0x02,0x81,0x81,0x00,0xB7,0x8F,0x7B,
0xEC,0x9D,0x9D,0xEF,0x6E,0x98,0x6E,0x25,0x62,0x2F,0xD6,0xAA,0x08,0x40,0xF0,0x0F,
0xFB,0x2E,0xEC,0x9C,0xD5,0x88,0x13,0xCC,0x95,0x76,0x54,0x19,0x18,0xDC,0x25,0x8E,
0x06,0x32,0x0D,0xA7,0x2A,0xAF,0xFA,0x54,0x6D,0x2D,0xA4,0x6C,0xAA,0x9A,0x78,0x45,
0x36,0x15,0x25,0xCB,0xAD,0xF8,0x61,0x0A,0x3A,0xE4,0xDE,0x21,0x2C,0xD5,0x62,0x91,
0x24,0x17,0xD5,0x69,0x29,0x1A,0x7C,0xC2,0x24,0x4B,0xD5,0xDA,0x47,0xAD,0x92,0xCF,
0x28,0xDA,0x62,0xC3,0xAD,0x7A,0xD8,0x10,0xE1,0xC3,0xC0,0x44,0x56,0x61,0xD6,0xB5,
0x1A,0xF1,0xA9,0xD1,0x60,0xD6,0xCC,0xE2,0x89,0xF3,0x64,0x87,0x2D,0x3B,0x88,0x03,
0xE6,0x39,0x85,0x98,0xFC,0xD5,0x57,0xB1,0xBB,0x53,0x45,0xCD,0x45,0x02,0x03,0x01,
0x00,0x01,
};
unsigned char XXX_certificate[747]={
0x30,0x82,0x02,0xE7,0x30,0x82,0x02,0x50,0xA0,0x03,0x02,0x01,0x02,0x02,0x01,0x02,
0x30,0x0D,0x06,0x09,0x2A,0x86,0x48,0x86,0xF7,0x0D,0x01,0x01,0x05,0x05,0x00,0x30,
0x81,0x81,0x31,0x0B,0x30,0x09,0x06,0x03,0x55,0x04,0x06,0x13,0x02,0x43,0x4E,0x31,
0x12,0x30,0x10,0x06,0x03,0x55,0x04,0x08,0x13,0x09,0x67,0x75,0x61,0x6E,0x67,0x64,
0x6F,0x6E,0x67,0x31,0x11,0x30,0x0F,0x06,0x03,0x55,0x04,0x07,0x13,0x08,0x73,0x68,
0x65,0x6E,0x7A,0x68,0x65,0x6E,0x31,0x10,0x30,0x0E,0x06,0x03,0x55,0x04,0x0A,0x13,
0x07,0x73,0x61,0x6E,0x67,0x66,0x6F,0x72,0x31,0x0D,0x30,0x0B,0x06,0x03,0x55,0x04,
0x0B,0x13,0x04,0x77,0x69,0x66,0x69,0x31,0x0B,0x30,0x09,0x06,0x03,0x55,0x04,0x03,
0x13,0x02,0x63,0x61,0x31,0x1D,0x30,0x1B,0x06,0x09,0x2A,0x86,0x48,0x86,0xF7,0x0D,
0x01,0x09,0x01,0x16,0x0E,0x63,0x61,0x40,0x73,0x61,0x6E,0x67,0x66,0x6F,0x72,0x2E,
0x63,0x6F,0x6D,0x30,0x1E,0x17,0x0D,0x31,0x32,0x30,0x39,0x31,0x36,0x30,0x31,0x30,
0x39,0x33,0x34,0x5A,0x17,0x0D,0x31,0x33,0x30,0x39,0x31,0x36,0x30,0x31,0x30,0x39,
0x33,0x34,0x5A,0x30,0x74,0x31,0x0B,0x30,0x09,0x06,0x03,0x55,0x04,0x06,0x13,0x02,
0x43,0x4E,0x31,0x12,0x30,0x10,0x06,0x03,0x55,0x04,0x08,0x13,0x09,0x67,0x75,0x61,
0x6E,0x67,0x64,0x6F,0x6E,0x67,0x31,0x10,0x30,0x0E,0x06,0x03,0x55,0x04,0x0A,0x13,
0x07,0x73,0x61,0x6E,0x67,0x66,0x6F,0x72,0x31,0x0D,0x30,0x0B,0x06,0x03,0x55,0x04,
0x0B,0x13,0x04,0x77,0x69,0x66,0x69,0x31,0x0E,0x30,0x0C,0x06,0x03,0x55,0x04,0x03,
0x13,0x05,0x75,0x73,0x65,0x72,0x31,0x31,0x20,0x30,0x1E,0x06,0x09,0x2A,0x86,0x48,
0x86,0xF7,0x0D,0x01,0x09,0x01,0x16,0x11,0x75,0x73,0x65,0x72,0x31,0x40,0x73,0x61,
0x6E,0x67,0x66,0x6F,0x72,0x2E,0x63,0x6F,0x6D,0x30,0x81,0x9F,0x30,0x0D,0x06,0x09,
0x2A,0x86,0x48,0x86,0xF7,0x0D,0x01,0x01,0x01,0x05,0x00,0x03,0x81,0x8D,0x00,0x30,
0x81,0x89,0x02,0x81,0x81,0x00,0xB7,0x8F,0x7B,0xEC,0x9D,0x9D,0xEF,0x6E,0x98,0x6E,
0x25,0x62,0x2F,0xD6,0xAA,0x08,0x40,0xF0,0x0F,0xFB,0x2E,0xEC,0x9C,0xD5,0x88,0x13,
0xCC,0x95,0x76,0x54,0x19,0x18,0xDC,0x25,0x8E,0x06,0x32,0x0D,0xA7,0x2A,0xAF,0xFA,
0x54,0x6D,0x2D,0xA4,0x6C,0xAA,0x9A,0x78,0x45,0x36,0x15,0x25,0xCB,0xAD,0xF8,0x61,
0x0A,0x3A,0xE4,0xDE,0x21,0x2C,0xD5,0x62,0x91,0x24,0x17,0xD5,0x69,0x29,0x1A,0x7C,
0xC2,0x24,0x4B,0xD5,0xDA,0x47,0xAD,0x92,0xCF,0x28,0xDA,0x62,0xC3,0xAD,0x7A,0xD8,
0x10,0xE1,0xC3,0xC0,0x44,0x56,0x61,0xD6,0xB5,0x1A,0xF1,0xA9,0xD1,0x60,0xD6,0xCC,
0xE2,0x89,0xF3,0x64,0x87,0x2D,0x3B,0x88,0x03,0xE6,0x39,0x85,0x98,0xFC,0xD5,0x57,
0xB1,0xBB,0x53,0x45,0xCD,0x45,0x02,0x03,0x01,0x00,0x01,0xA3,0x7B,0x30,0x79,0x30,
0x09,0x06,0x03,0x55,0x1D,0x13,0x04,0x02,0x30,0x00,0x30,0x2C,0x06,0x09,0x60,0x86,
0x48,0x01,0x86,0xF8,0x42,0x01,0x0D,0x04,0x1F,0x16,0x1D,0x4F,0x70,0x65,0x6E,0x53,
0x53,0x4C,0x20,0x47,0x65,0x6E,0x65,0x72,0x61,0x74,0x65,0x64,0x20,0x43,0x65,0x72,
0x74,0x69,0x66,0x69,0x63,0x61,0x74,0x65,0x30,0x1D,0x06,0x03,0x55,0x1D,0x0E,0x04,
0x16,0x04,0x14,0x19,0x1D,0xD8,0xA8,0xC5,0x97,0xF7,0x70,0x63,0x64,0x50,0x9A,0x36,
0xAE,0xE2,0x59,0x3D,0x68,0x6F,0xFB,0x30,0x1F,0x06,0x03,0x55,0x1D,0x23,0x04,0x18,
0x30,0x16,0x80,0x14,0xFC,0x0A,0x0B,0x63,0x0D,0x14,0xCB,0x5F,0x30,0x33,0x16,0x32,
0x81,0x04,0xB1,0x52,0x67,0x9B,0x25,0xB3,0x30,0x0D,0x06,0x09,0x2A,0x86,0x48,0x86,
0xF7,0x0D,0x01,0x01,0x05,0x05,0x00,0x03,0x81,0x81,0x00,0x59,0xD4,0xFB,0x9D,0x34,
0x35,0xED,0x07,0xEA,0x8A,0x08,0x06,0x3E,0xFF,0x2F,0x24,0xEA,0xA2,0x4E,0x43,0x8B,
0xCB,0x7F,0xA7,0x1F,0x63,0xBE,0x93,0x75,0x12,0xE8,0xEE,0x56,0xB7,0x9B,0xBC,0xC3,
0x20,0x0D,0x45,0xAB,0x06,0xDB,0xD2,0xAD,0xE2,0x10,0x08,0x02,0x30,0x63,0xA8,0xF1,
0xED,0x22,0x64,0x15,0xD2,0xED,0x94,0xFD,0x3B,0x91,0xEF,0x1E,0xDC,0x95,0xAE,0x4A,
0x5A,0xBA,0x57,0x00,0xD5,0x45,0x1B,0x1F,0xCB,0x79,0x89,0x94,0xA8,0x84,0x4E,0xD3,
0xF8,0x92,0x16,0xCC,0xF8,0xE5,0x24,0x8C,0x86,0x85,0x3B,0x8E,0x8A,0xDA,0x71,0x84,
0xE9,0x53,0x1F,0xBF,0xEB,0x62,0x43,0xC4,0x26,0xDF,0x65,0x1C,0x1B,0x01,0x4B,0x2B,
0xE9,0x92,0x3A,0x17,0x9B,0xC0,0x42,0xF2,0xF1,0x1D,0xE9,
};
7. 查看待签名证书(req)文件信息
证书请求文件(扩展名一般为: csr )
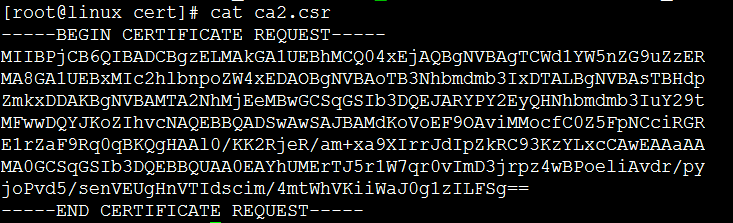
[root@linux cert]# openssl req -in ./ca3.csr -text -noout
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=CN, ST=guangdong, L=shenzhen, O=sangfor, OU=wifi, CN=ca3/emailAddress=ca3@sangfor.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Modulus (2048 bit):
00:c9:3a:aa:64:81:76:83:4d:8b:31:d4:0e:6c:11:
18:d9:24:c2:47:6a:d8:d8:3e:68:62:a0:4a:27:65:
66:66:f1:77:29:69:12:4c:34:62:47:51:b0:ee:f9:
fc:9f:a4:da:6d:b7:70:55:9f:d2:ac:49:8b:59:65:
61:d4:ef:ff:14:2d:51:a2:56:a8:47:2f:ce:0a:26:
d1:9a:23:ef:87:17:f0:6d:70:6b:61:2d:4f:34:20:
8e:84:d3:e0:90:b5:4f:ae:3b:89:e3:35:5e:b5:e9:
a2:fd:1c:57:e1:e1:d1:07:e6:09:bf:0d:29:ae:0c:
d2:3c:fd:99:c4:37:c6:e3:b5:16:9f:52:81:c4:6d:
8f:a4:20:b0:0c:36:25:14:02:31:fd:8a:a0:25:23:
94:15:eb:4b:17:43:b8:9d:ed:c9:89:a0:50:f3:06:
e8:1b:b8:78:dc:66:38:1e:f7:c6:64:c4:55:89:74:
28:68:fa:8a:b0:5d:83:37:e6:ac:45:20:1a:cb:56:
91:72:8a:74:c0:ec:33:dd:22:b2:07:4b:06:3b:a2:
b8:93:7c:b5:25:e0:8c:80:b9:98:e0:c6:c4:aa:3c:
1d:86:cf:19:39:08:a5:4a:40:8e:86:5a:0f:0d:01:
9c:00:db:3f:44:a5:34:02:2b:73:4c:be:61:90:80:
7e:e9
Exponent: 65537 (0x10001)
Attributes:
a0:00
Signature Algorithm: sha1WithRSAEncryption
82:15:ab:ec:9b:84:eb:28:2d:3e:07:20:13:e4:08:09:40:7f:
5c:19:6a:ff:9a:d2:26:75:2e:32:ce:bc:2a:8b:a9:7d:cc:3c:
ea:f0:0f:48:c3:6e:3a:98:01:8d:65:40:42:2b:92:75:85:65:
3c:90:71:26:1e:0d:9a:2b:08:c1:93:6e:b4:15:c1:26:4b:34:
54:36:cd:59:52:b2:c5:a0:c9:77:45:6f:ca:89:16:81:a3:29:
de:8b:49:40:a5:66:bc:c8:0f:e0:6a:56:80:0c:ea:7a:ad:97:
97:e6:35:50:37:20:f5:6c:fd:d1:e3:7f:9f:6d:53:2e:03:f8:
b3:fa:d6:1f:2e:e1:5d:95:6e:dd:41:78:46:26:cf:a6:8d:ea:
ed:88:39:d6:ba:d2:1c:51:a8:c6:a9:31:7b:6b:4c:47:31:21:
7d:1f:8c:e3:12:cd:f8:62:6e:fa:89:4d:63:b5:86:ab:bc:5b:
9f:7f:bf:f4:b2:1c:56:3e:ec:fe:a0:18:2d:d9:7f:cc:e3:27:
52:d3:e6:2a:18:1d:e0:fc:92:2b:09:d2:ed:fe:33:62:8a:2e:
ac:0d:c0:71:81:6a:b4:17:72:3b:cb:52:f8:28:a4:7f:90:76:
2f:a0:cd:23:7b:f8:64:c3:b1:d7:7d:23:64:a2:62:fd:fe:4e:
10:80:d0:ad
显示 subject 字段信息
openssl req -subject -in ./ca3.csr -noout
openssl req -subject -in ./ca3.csr -noout -nameopt RFC2253
显示公钥(和从私钥中提取出来的公钥一样)
图中 ca3.key 是 ca3.csr 对应的私钥文件
openssl rsa -in ca3.key -pubout
openssl req -in ./ca3.csr -pubkey -noout
8. 数据加密、hash、与解密
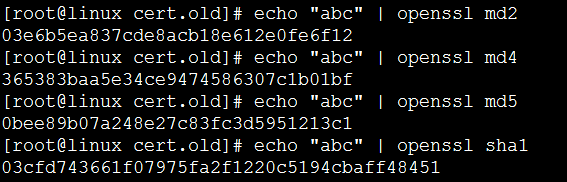
计算 base64 编码![]()
计算 md2、 md4、 md5、 sha1
Base64 解码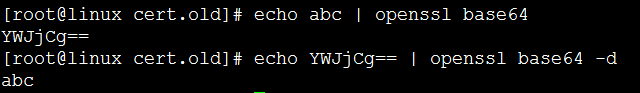
将 base64格式的文件 aa 解码 保存到文件 bb中
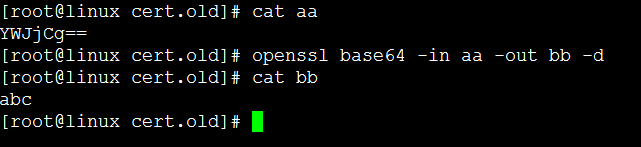
Base64 加解码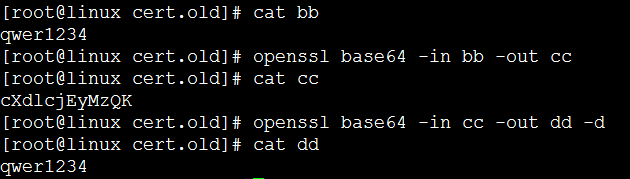
对字符串‘abc’进行aes加密,使用密钥123,输出结果以base64编码格式给出, 然后对密文数据进行解密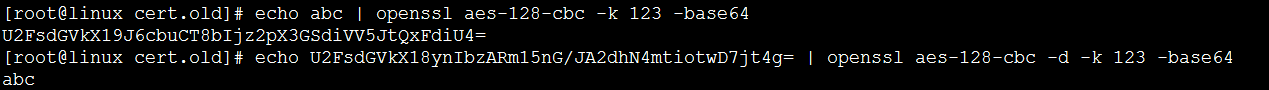
Des3 加密与解密(如果不用 base64编码输出可能为乱码)![]()
9. 签发多级CA
签发二级CA
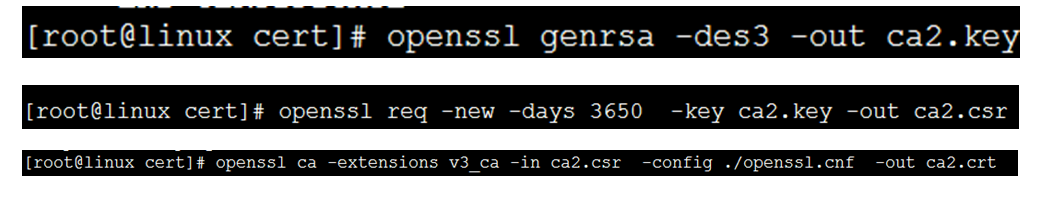
可以用二级CA签发三级CA
用二级证书签发用户证书
Openssl ca -in user2_ca2.crt -days 3650 -out user2_ca2.crt -config ./openssl.conf -cert ./ca2.crt -keyfile ca2.key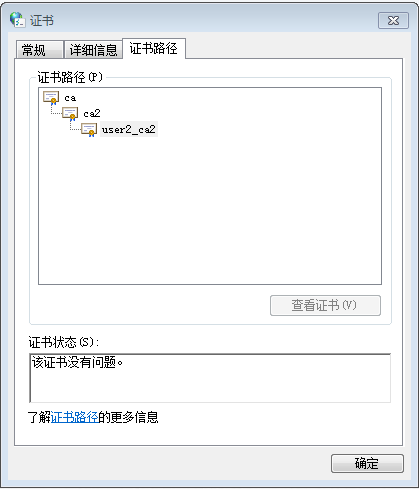
10. Pkcs12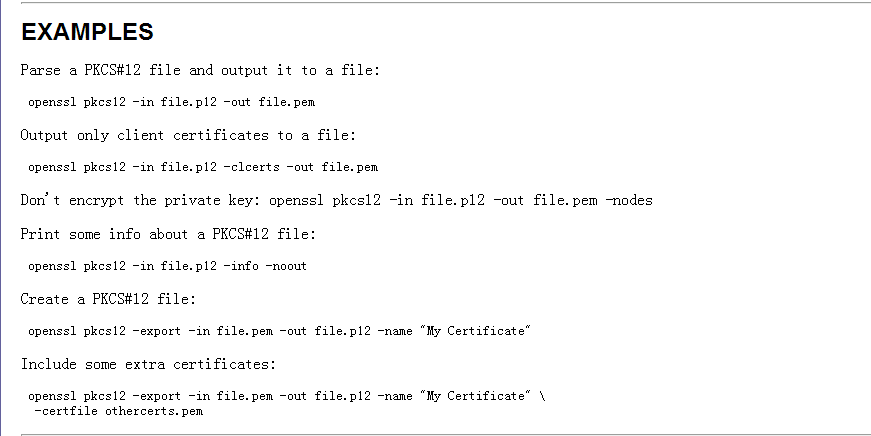
11. Pkcs#7
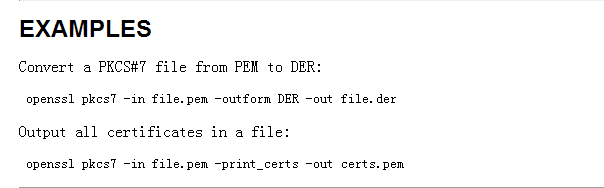
openssl pkcs7 -print_certs -in pkcs7.p7b -out pem.cer
openssl crl2pkcs7 -nocrl -certfile cert1.cer -certfile cert2.cer -out outfile.p7b
OpenSSL Convert PEM
Convert PEM to DER
openssl x509 -outform der -in certificate.pem -out certificate.der
Convert PEM to P7B
openssl crl2pkcs7 -nocrl -certfile certificate.cer -out certificate.p7b -certfile CACert.cer
Convert PEM to PFX
openssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in certificate.crt -certfile CACert.crt
OpenSSL Convert DER
Convert DER to PEM
openssl x509 -inform der -in certificate.cer -out certificate.pem
OpenSSL Convert P7B
Convert P7B to PEM
openssl pkcs7 -print_certs -in certificate.p7b -out certificate.cer
Convert P7B to PFX
openssl pkcs7 -print_certs -in certificate.p7b -out certificate.cer
openssl pkcs12 -export -in certificate.cer -inkey privateKey.key -out certificate.pfx -certfile CACert.cer
OpenSSL Convert PFX
Convert PFX to PEM
openssl pkcs12 -in certificate.pfx -out certificate.cer -nodes
待续......
没啥子意义“PXF转PEM后certificate.cer文件包含认证证书和私钥,需要把它们分开存储才能使用。”
Hostapd TLS 加解密
写入明文数据
res = SSL_write(conn->ssl, wpabuf_head(in_data), wpabuf_len(in_data));
读取密文数据
res = BIO_read(conn->ssl_out, wpabuf_mhead(buf), wpabuf_size(buf));
写入密文数据
res = BIO_write(conn->ssl_in, wpabuf_head(in_data),
wpabuf_len(in_data));
获取明文数据
res = SSL_read(conn->ssl, wpabuf_mhead(buf), wpabuf_size(buf));
加密处理:
向 SSL 写入数据
SSL_write(conn->ssl, 明文数据, 文明数据长度);
从 con->ssl_out 读取出来的数据是密文
BIO_read(conn->ssl_out, 保存密文数据指针, 密文数据长度);
解密数据:
BIO_write(conn->ssl_in, 密文数据, 密文数据长度);
SSL_read(conn->ssl, 明文数据, 明文数据长度);
函数篇:
(一)
X509 *crert = NULL;
Cert = X509_new()
X509_set_version(cert, 2);
X509_set_serialNumber()
X509_set_subject_name()
X509_set_issuer_name()
X509_free();
X509 *_cert;
_cert = PEM_read_bio_X509(bio, NULL, NULL, NULL);
1、DER编码转换为内部结构函数
X509 *d2i_X509(X509 **cert, unsigned char **d, int len);
函数功能:把一个DER编码的证书数据转化成OpenSSL内部结构体。
参数:cert:[OUT]X509结构体。 D:[IN]DER编码的证书数据指针地址。Len[IN]证 书数据长度;
返回值:编码后的X509结构体数据
2、获得证书版本函数X509_get_version
#define X509_get_version(x) ASN1_INTEGER_get((x)->cert_info->version)
参数:x:[IN]X509*结构体数据结构。
返回值:证书版本,数据类型“LONG”
3、获得证书序列号函数
ASN1_INTEGER *X509_get_serialNumber(X509 *x);
返回值:证书序列号,数据类型“ASN1_INTEGER”.
4、获得证书颁发者信息函数
X509_NAME *X509_get_issuer_name(X509 *a);
注*:X509_NAME结构体包括多个X509_NAME_ENTRY结构体。X509_NAME_ENTRY保存了颁发者的信息,这些信息包括对象和值(object 和value)。对象的类型包括国家、通用名、单位、组织、地区、邮件等。
(二)
X509_EXTENSION *ext = NULL;
ext = X509_EXTENSION_new();
ext = X509_EXTENSION_dup((X509_EXTENSION *)n);
X509_EXTENSION_free(ext);
(三)
X509_CRL *crt;
crl = X509_CRL_new();
crl = PEM_read_bio_X509_CRL(bio, NULL, NULL, NULL);
FILE *fp = fopen(“crl.crl”, “r”);
crl = PEM_read_X509_CRL(fp, NULL,NULL,NULL);
If (! crt) {
Rewind(fp);
crt = d2i_X509_CRL_fp(fp, NULL);
}
X509_CRL_free(crl);
QString alg = OBJ_nid2ln(OBJ_obj2nid(crl->sig_alg->algorithm)); // 返回签名算法
X509_CRL_set_lastUpdate();
X509_CRL_set_nextUpdate();
// 给CRL 加上扩展项
X509_EXTENSION *ext = xx;
X509_CRL_add_ext(crl, ext, -1);
X509_EXTENSION_free(ext);
给CRL 签名:
EVP_PKEY *pkey;
X509_CRL_sort(crt);
X509_CRL_sign(crl, pkey, md) // const EVP_MD *md;
EVP_PKEY_free(pkey);
将 CRL 写入到文件中
FILE *fp = fopen(“xx.crl”, “w”);
If (fp != NULL) {
If (pem)
PEM_write_X509_CRL(fp, crl);
Else
I2d_X509_CRL_fp(fp, crl);
}
将 PEM 格式的 CRL 写入到内存中
BIO *b = NULL;
b = BIO_new(BIO_s_mem());
PEM_write_bio_X509_CRL(b, crl);
CRL 吊销的记录条数
Int num = sk_X509_REVOKED_num(crl->crl->revoked);
X509_REVOKED *n = sk_X509_REVOKED_value(crl->crl->revoked, num);
验证签名数据:
X509_CRL_verify(crl , 公钥);
X509_CRL *crl=NULL;
int ret;
X509_REVOKED *revoked=NULL;
ASN1_INTEGER *serial;
long serial_NUM;
time_t t;
ASN1_TIME *rvTime;
revoked=X509_REVOKED_new();
serial=ASN1_INTEGER_new();
ret=ASN1_INTEGER_set(serial,serial_NUM);
ret=X509_REVOKED_set_serialNumber(revoked,serial);
rvTime=ASN1_TIME_new();
t=time(NULL);
ASN1_TIME_set(rvTime,t);
ret=X509_REVOKED_set_revocationDate(revoked,rvTime);
ret=X509_CRL_add0_revoked(crl,revoked);
我自己回答一下吧,用如下函数就行,其中crl是指向这个crl的指针,第2个参数为删除的是哪一项,其中0为第一项,注意:如果你删除完这个crl中的某一项一定要为这个crl重新签名,但如果你非要不签名,那么一定要加上注释掉的那句话,否则你对crl的任何修改都是无效的
sk_X509_REVOKED_delete(crl->crl->revoked,1);
// crl->crl->enc.modified = 1;
X509_CRL_sign(crl,pRSAKey,EVP_md5());
openssl.cnf
#
# OpenSSL example configuration file.
# This is mostly being used for generation of certificate requests.
#
# This definition stops the following lines choking if HOME isn't
# defined.
HOME = .
RANDFILE = $ENV::HOME/.rnd
# Extra OBJECT IDENTIFIER info:
#oid_file = $ENV::HOME/.oid
oid_section = new_oids
# To use this configuration file with the "-extfile" option of the
# "openssl x509" utility, name here the section containing the
# X.509v3 extensions to use:
# extensions =
# (Alternatively, use a configuration file that has only
# X.509v3 extensions in its main [= default] section.)
[ new_oids ]
# We can add new OIDs in here for use by 'ca' and 'req'.
# Add a simple OID like this:
# testoid1=1.2.3.4
# Or use config file substitution like this:
# testoid2=${testoid1}.5.6
####################################################################
[ ca ]
default_ca = CA_default # The default ca section
####################################################################
[ CA_default ]
dir = ./demoCA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of
# several ctificates with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
#crlnumber = $dir/crlnumber # the current crl number
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
RANDFILE = $dir/private/.rand # private random number file
x509_extensions = usr_cert # The extentions to add to the cert
# Comment out the following two lines for the "traditional"
# (and highly broken) format.
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options
# Extension copying option: use with caution.
# copy_extensions = copy
# Extensions to add to a CRL. Note: Netscape communicator chokes on V2 CRLs
# so this is commented out by default to leave a V1 CRL.
# crlnumber must also be commented out to leave a V1 CRL.
# crl_extensions = crl_ext
default_days = 365 # how long to certify for
default_crl_days= 30 # how long before next CRL
default_md = md5 # which md to use.
preserve = no # keep passed DN ordering
# A few difference way of specifying how similar the request should look
# For type CA, the listed attributes must be the same, and the optional
# and supplied fields are just that :-)
policy = policy_match
# For the CA policy
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
# For the 'anything' policy
# At this point in time, you must list all acceptable 'object'
# types.
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
####################################################################
[ req ]
default_bits = 1024
default_keyfile = privkey.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca # The extentions to add to the self signed cert
# Passwords for private keys if not present they will be prompted for
# input_password = secret
# output_password = secret
# This sets a mask for permitted string types. There are several options.
# default: PrintableString, T61String, BMPString.
# pkix : PrintableString, BMPString.
# utf8only: only UTF8Strings.
# nombstr : PrintableString, T61String (no BMPStrings or UTF8Strings).
# MASK:XXXX a literal mask value.
# WARNING: current versions of Netscape crash on BMPStrings or UTF8Strings
# so use this option with caution!
#string_mask = nombstr
string_mask = utf8only
# req_extensions = v3_req # The extensions to add to a certificate request
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Some-State
localityName = Locality Name (eg, city)
0.organizationName = Organization Name (eg, company)
0.organizationName_default = Internet Widgits Pty Ltd
# we can do this but it is not needed normally :-)
#1.organizationName = Second Organization Name (eg, company)
#1.organizationName_default = World Wide Web Pty Ltd
organizationalUnitName = Organizational Unit Name (eg, section)
#organizationalUnitName_default =
commonName = Common Name (eg, YOUR name)
commonName_max = 64
emailAddress = Email Address
emailAddress_max = 64
# SET-ex3 = SET extension number 3
[ req_attributes ]
challengePassword = A challenge password
challengePassword_min = 4
challengePassword_max = 20
unstructuredName = An optional company name
[ usr_cert ]
1.2.3.4=DER:01020304
# These extensions are added when 'ca' signs a request.
# This goes against PKIX guidelines but some CAs do it and some software
# requires this to avoid interpreting an end user certificate as a CA.
basicConstraints=CA:FALSE
# Here are some examples of the usage of nsCertType. If it is omitted
# the certificate can be used for anything *except* object signing.
# This is OK for an SSL server.
# nsCertType = server
# For an object signing certificate this would be used.
# nsCertType = objsign
# For normal client use this is typical
# nsCertType = client, email
# and for everything including object signing:
# nsCertType = client, email, objsign
# This is typical in keyUsage for a client certificate.
# keyUsage = nonRepudiation, digitalSignature, keyEncipherment
# This will be displayed in Netscape's comment listbox.
#nsComment = "OpenSSL Generated Certificate"
# PKIX recommendations harmless if included in all certificates.
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer:always
# This stuff is for subjectAltName and issuerAltname.
# Import the email address.
# subjectAltName=email:copy
# An alternative to produce certificates that aren't
# deprecated according to PKIX.
# subjectAltName=email:move
# Copy subject details
# issuerAltName=issuer:copy
#nsCaRevocationUrl = http://www.domain.dom/ca-crl.pem
#nsBaseUrl
#nsRevocationUrl
#nsRenewalUrl
#nsCaPolicyUrl
#nsSslServerName
[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
[ v3_ca ]
# Extensions for a typical CA
# PKIX recommendation.
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer:always
# This is what PKIX recommends but some broken software chokes on critical
# extensions.
#basicConstraints = critical,CA:true
# So we do this instead.
basicConstraints = CA:true
# Key usage: this is typical for a CA certificate. However since it will
# prevent it being used as an test self-signed certificate it is best
# left out by default.
# keyUsage = cRLSign, keyCertSign
# Some might want this also
# nsCertType = sslCA, emailCA
# Include email address in subject alt name: another PKIX recommendation
# subjectAltName=email:copy
# Copy issuer details
# issuerAltName=issuer:copy
# DER hex encoding of an extension: beware experts only!
# obj=DER:02:03
# Where 'obj' is a standard or added object
# You can even override a supported extension:
# basicConstraints= critical, DER:30:03:01:01:FF
[ crl_ext ]
# CRL extensions.
# Only issuerAltName and authorityKeyIdentifier make any sense in a CRL.
# issuerAltName=issuer:copy
authorityKeyIdentifier=keyid:always,issuer:always






















 210
210











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








