10.11 Linux网络相关
ifconfig命令:查看网卡信息(安装net-tools包),ip addr命令也能查看网卡信息(显示没那么规整)
[root@lgs-01 ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.87.130 netmask 255.255.255.0 broadcast 192.168.87.255
inet6 fe80::f74d:28a0:35b4:f7a3 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:d0:e2:b8 txqueuelen 1000 (Ethernet)
RX packets 109 bytes 11724 (11.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 90 bytes 11619 (11.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 72 bytes 5712 (5.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 72 bytes 5712 (5.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@lgs-01 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:d0:e2:b8 brd ff:ff:ff:ff:ff:ff
inet 192.168.87.130/24 brd 192.168.87.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::f74d:28a0:35b4:f7a3/64 scope link
valid_lft forever preferred_lft forever
-a选项:显示所有网络接口的信息,无论是否激活(如禁用网卡 ifconfig ens33 down之后)
ifconfig ens33 down:禁用网卡; ifconfig ens33 up:启用网卡。
不加-a选项,看不到禁用的网卡。 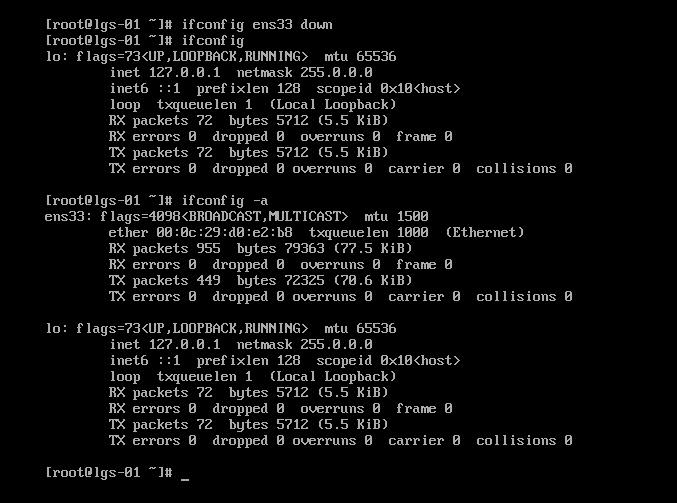
ifdown ens33:把网卡断开连接 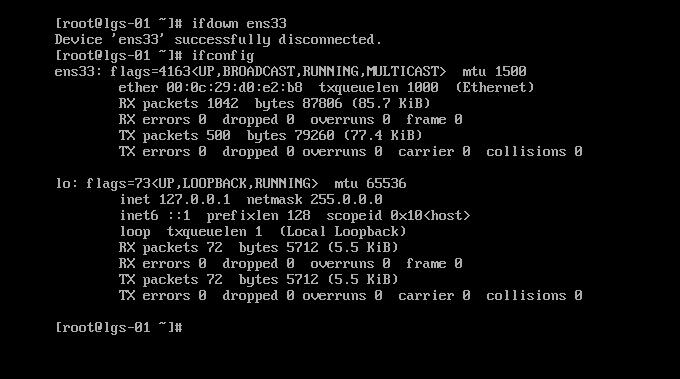
ifup ens33:把网卡连接上 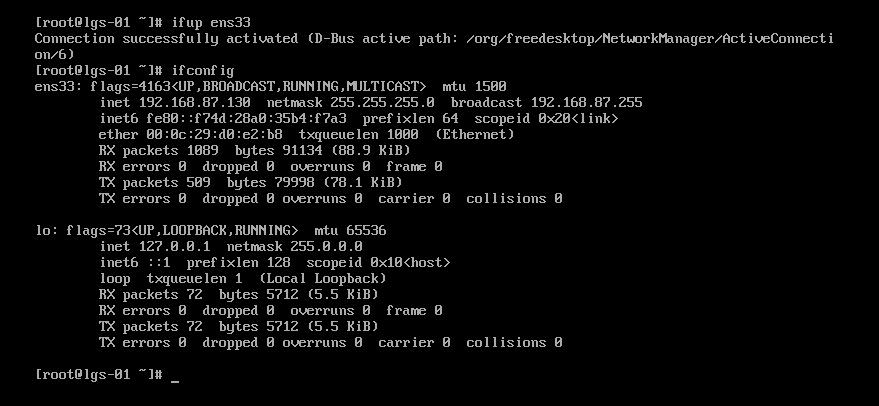
ifup、ifdown只是脚本,不是命令。
ifdown要与ifup 一起连着用,防止远程登录失效,导致外地的服务器连接不上。
[root@lgs-01 ~]# ifdown ens33 && ifup ens33
成功断开设备 'ens33'。
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/7)
设定一个虚拟网卡:拷贝网卡配置文件,修改ip信息即可。虚拟网卡一般在lvs、keepalived中使用
修改完配置文件,重连网卡
[root@lgs-01 ~]# cd /etc/sysconfig/network-scripts/
[root@lgs-01 network-scripts]# ls
ifcfg-ens33 ifdown-eth ifdown-post ifdown-Team ifup-aliases ifup-ipv6 ifup-post ifup-Team init.ipv6-global
ifcfg-lo ifdown-ippp ifdown-ppp ifdown-TeamPort ifup-bnep ifup-isdn ifup-ppp ifup-TeamPort network-functions
ifdown ifdown-ipv6 ifdown-routes ifdown-tunnel ifup-eth ifup-plip ifup-routes ifup-tunnel network-functions-ipv6
ifdown-bnep ifdown-isdn ifdown-sit ifup ifup-ippp ifup-plusb ifup-sit ifup-wireless
[root@lgs-01 network-scripts]# cp ifcfg-ens33 ifcfg-ens33\:0
[root@lgs-01 network-scripts]# ls
ifcfg-ens33 ifdown-bnep ifdown-isdn ifdown-sit ifup ifup-ippp ifup-plusb ifup-sit ifup-wireless
ifcfg-ens33:0 ifdown-eth ifdown-post ifdown-Team ifup-aliases ifup-ipv6 ifup-post ifup-Team init.ipv6-global
ifcfg-lo ifdown-ippp ifdown-ppp ifdown-TeamPort ifup-bnep ifup-isdn ifup-ppp ifup-TeamPort network-functions
ifdown ifdown-ipv6 ifdown-routes ifdown-tunnel ifup-eth ifup-plip ifup-routes ifup-tunnel network-functions-ipv6
[root@lgs-01 network-scripts]# vim ifcfg-ens33:0
[root@lgs-01 network-scripts]# ifdown ens33 && ifup ens33
成功断开设备 'ens33'。
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/9)
[root@lgs-01 network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.87.130 netmask 255.255.255.0 broadcast 192.168.87.255
inet6 fe80::f74d:28a0:35b4:f7a3 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:d0:e2:b8 txqueuelen 1000 (Ethernet)
RX packets 2197 bytes 186162 (181.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1125 bytes 172779 (168.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens33:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.87.138 netmask 255.255.255.0 broadcast 192.168.87.255
ether 00:0c:29:d0:e2:b8 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 72 bytes 5712 (5.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 72 bytes 5712 (5.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
查看网卡是否接线:link ok即可;用ethtool也可以:Link detected: yes
[root@lgs-01 network-scripts]# mii-tool ens33
ens33: negotiated 1000baseT-FD flow-control, link ok
[root@lgs-01 network-scripts]# ethtool ens33
Settings for ens33:
Supported ports: [ TP ]
Supported link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
1000baseT/Full
Supported pause frame use: No
Supports auto-negotiation: Yes
Advertised link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
1000baseT/Full
Advertised pause frame use: No
Advertised auto-negotiation: Yes
Speed: 1000Mb/s
Duplex: Full
Port: Twisted Pair
PHYAD: 0
Transceiver: internal
Auto-negotiation: on
MDI-X: off (auto)
Supports Wake-on: d
Wake-on: d
Current message level: 0x00000007 (7)
drv probe link
Link detected: yes
更改主机名:hostnamectl set-hostname lgs-xp
进入子bash生效,或者重连shell就生效。
[root@lgs-01 ~]# hostnamectl set-hostname lgs
[root@lgs-01 ~]# hostname
lgs
[root@lgs-01 ~]# cat /etc/hostname
lgs
[root@lgs-01 ~]# bash
[root@lgs ~]#
修改DNS:在配置文件 /etc/resolv/conf 修改,临时生效。网卡重启时,会被网卡的配置文件的DNS覆盖。
[root@lgs ~]# cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 119.29.29.29
[root@lgs ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens33
[root@lgs ~]# cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 119.29.29.29
[root@lgs ~]# ifdown ens33 && ifup ens33
成功断开设备 'ens33'。
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/10)
[root@lgs ~]# cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 119.29.29.29
nameserver 8.8.8.8
host文件:指定本机域名解析到指定的ip,只在本机生效,绕过DNS服务器。可以多个域名指向一个ip。
[root@lgs ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
[root@lgs ~]# vim /etc/hosts
[root@lgs ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.87.130 www.123.com www.163.com
192.168.87.2 www.qq.com
192.168.87.2 www.abc.com
[root@lgs ~]# ping www.163.com
PING www.123.com (192.168.87.130) 56(84) bytes of data.
64 bytes from www.123.com (192.168.87.130): icmp_seq=1 ttl=64 time=0.102 ms
64 bytes from www.123.com (192.168.87.130): icmp_seq=2 ttl=64 time=0.082 ms
64 bytes from www.123.com (192.168.87.130): icmp_seq=3 ttl=64 time=0.087 ms
^C
--- www.123.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 0.082/0.090/0.102/0.011 ms
[root@lgs ~]# ping www.123.com
PING www.123.com (192.168.87.130) 56(84) bytes of data.
64 bytes from www.123.com (192.168.87.130): icmp_seq=1 ttl=64 time=0.060 ms
64 bytes from www.123.com (192.168.87.130): icmp_seq=2 ttl=64 time=0.070 ms
^C
--- www.123.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 0.060/0.065/0.070/0.005 ms
如果有同样重复的域名的,只有最后一行生效。
[root@lgs ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.87.130 www.123.com www.163.com
192.168.87.2 www.qq.com
127.0.0.1 www.123.com
[root@lgs ~]# ping www.123.com
PING www.123.com (127.0.0.1) 56(84) bytes of data.
64 bytes from localhost (127.0.0.1): icmp_seq=1 ttl=64 time=0.042 ms
64 bytes from localhost (127.0.0.1): icmp_seq=2 ttl=64 time=0.079 ms
64 bytes from localhost (127.0.0.1): icmp_seq=3 ttl=64 time=0.079 ms
64 bytes from localhost (127.0.0.1): icmp_seq=4 ttl=64 time=0.067 ms
^C
--- www.123.com ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 0.042/0.066/0.079/0.018 ms
10.12 firewalld和netfilter
setenforce 0:临时关闭selinux
[root@lgs ~]# getenforce
Enforcing
[root@lgs ~]# setenforce 0
[root@lgs ~]# getenforce
Permissive
要永久关闭selinux:修改配置文件SELINUX=disabled,重启系统生效
[root@lgs ~]# vim /etc/selinux/config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled
# SELINUXTYPE= can take one of three two values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
防火墙firewalld:centos 7版本的防火墙
防火墙netfilter:centos 5、6版本的防火墙
在centos7上也可以开启netfilter防火墙:
1、不开机启动firewalld,关闭firewalld
[root@lgs ~]# systemctl disable firewalld
Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
[root@lgs ~]# systemctl stop firewalld
2、安装iptables-services包
[root@lgs ~]# yum install -y iptables-services
已加载插件:fastestmirror
Loading mirror speeds from cached hostfile
* epel: mirror01.idc.hinet.net
正在解决依赖关系
--> 正在检查事务
---> 软件包 iptables-services.x86_64.0.1.4.21-18.3.el7_4 将被 安装
--> 正在处理依赖关系 iptables = 1.4.21-18.3.el7_4,它被软件包 iptables-services-1.4.21-18.3.el7_4.x86_64 需要
--> 正在检查事务
---> 软件包 iptables.x86_64.0.1.4.21-18.0.1.el7.centos 将被 升级
---> 软件包 iptables.x86_64.0.1.4.21-18.3.el7_4 将被 更新
--> 解决依赖关系完成
依赖关系解决
==============================================================================================================================================================
Package 架构 版本 源 大小
==============================================================================================================================================================
正在安装:
iptables-services x86_64 1.4.21-18.3.el7_4 updates 51 k
为依赖而更新:
iptables x86_64 1.4.21-18.3.el7_4 updates 428 k
事务概要
==============================================================================================================================================================
安装 1 软件包
升级 ( 1 依赖软件包)
总下载量:479 k
Downloading packages:
Delta RPMs disabled because /usr/bin/applydeltarpm not installed.
(1/2): iptables-services-1.4.21-18.3.el7_4.x86_64.rpm | 51 kB 00:00:00
(2/2): iptables-1.4.21-18.3.el7_4.x86_64.rpm | 428 kB 00:00:00
--------------------------------------------------------------------------------------------------------------------------------------------------------------
总计 691 kB/s | 479 kB 00:00:00
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
正在更新 : iptables-1.4.21-18.3.el7_4.x86_64 1/3
正在安装 : iptables-services-1.4.21-18.3.el7_4.x86_64 2/3
清理 : iptables-1.4.21-18.0.1.el7.centos.x86_64 3/3
验证中 : iptables-1.4.21-18.3.el7_4.x86_64 1/3
验证中 : iptables-services-1.4.21-18.3.el7_4.x86_64 2/3
验证中 : iptables-1.4.21-18.0.1.el7.centos.x86_64 3/3
已安装:
iptables-services.x86_64 0:1.4.21-18.3.el7_4
作为依赖被升级:
iptables.x86_64 0:1.4.21-18.3.el7_4
完毕!
3、开机启动iptables,开启iptables服务
[root@lgs ~]# systemctl enable iptables
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
[root@lgs ~]# systemctl start iptables
4、开启netfilter防火墙成功,查看iptables默认规则。netfilter才是防火墙的名字,iptables只是他的一个工具。
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
25 1728 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 15 packets, 1412 bytes)
pkts bytes target prot opt in out source destination
10.13 netfilter5表5链介绍
netfilter的5个表:filter、nat、mangle、raw、security,一般操作filter和nat即可。 CentOS 5、6没有 security表。
[root@lgs ~]# man iptables
IPTABLES(8) iptables 1.4.21 IPTABLES(8)
NAME
iptables/ip6tables — administration tool for IPv4/IPv6 packet filtering and NAT
SYNOPSIS
iptables [-t table] {-A|-C|-D} chain rule-specification
ip6tables [-t table] {-A|-C|-D} chain rule-specification
iptables [-t table] -I chain [rulenum] rule-specification
iptables [-t table] -R chain rulenum rule-specification
iptables [-t table] -D chain rulenum
iptables [-t table] -S [chain [rulenum]]
iptables [-t table] {-F|-L|-Z} [chain [rulenum]] [options...]
iptables [-t table] -N chain
iptables [-t table] -X [chain]
iptables [-t table] -P chain target
iptables [-t table] -E old-chain-name new-chain-name
rule-specification = [matches...] [target]
match = -m matchname [per-match-options]
target = -j targetname [per-target-options]
DESCRIPTION
Iptables and ip6tables are used to set up, maintain, and inspect the tables of IPv4 and IPv6 packet filter rules in the Linux kernel. Several dif‐
ferent tables may be defined. Each table contains a number of built-in chains and may also contain user-defined chains.
Each chain is a list of rules which can match a set of packets. Each rule specifies what to do with a packet that matches. This is called a `tar‐
get', which may be a jump to a user-defined chain in the same table.
TARGETS
A firewall rule specifies criteria for a packet and a target. If the packet does not match, the next rule in the chain is examined; if it does
match, then the next rule is specified by the value of the target, which can be the name of a user-defined chain, one of the targets described in
iptables-extensions(8), or one of the special values ACCEPT, DROP or RETURN.
ACCEPT means to let the packet through. DROP means to drop the packet on the floor. RETURN means stop traversing this chain and resume at the
next rule in the previous (calling) chain. If the end of a built-in chain is reached or a rule in a built-in chain with target RETURN is matched,
the target specified by the chain policy determines the fate of the packet.
TABLES
There are currently five independent tables (which tables are present at any time depends on the kernel configuration options and which modules are
present).
-t, --table table
This option specifies the packet matching table which the command should operate on. If the kernel is configured with automatic module
loading, an attempt will be made to load the appropriate module for that table if it is not already there.
The tables are as follows:
filter:
This is the default table (if no -t option is passed). It contains the built-in chains INPUT (for packets destined to local sockets),
FORWARD (for packets being routed through the box), and OUTPUT (for locally-generated packets).
nat:
This table is consulted when a packet that creates a new connection is encountered. It consists of three built-ins: PREROUTING (for
altering packets as soon as they come in), OUTPUT (for altering locally-generated packets before routing), and POSTROUTING (for altering
packets as they are about to go out). IPv6 NAT support is available since kernel 3.7.
mangle:
This table is used for specialized packet alteration. Until kernel 2.4.17 it had two built-in chains: PREROUTING (for altering incoming
packets before routing) and OUTPUT (for altering locally-generated packets before routing). Since kernel 2.4.18, three other built-in
chains are also supported: INPUT (for packets coming into the box itself), FORWARD (for altering packets being routed through the box),
and POSTROUTING (for altering packets as they are about to go out).
raw:
This table is used mainly for configuring exemptions from connection tracking in combination with the NOTRACK target. It registers at
the netfilter hooks with higher priority and is thus called before ip_conntrack, or any other IP tables. It provides the following
built-in chains: PREROUTING (for packets arriving via any network interface) OUTPUT (for packets generated by local processes)
security:
This table is used for Mandatory Access Control (MAC) networking rules, such as those enabled by the SECMARK and CONNSECMARK targets.
Mandatory Access Control is implemented by Linux Security Modules such as SELinux. The security table is called after the filter table,
allowing any Discretionary Access Control (DAC) rules in the filter table to take effect before MAC rules. This table provides the fol‐
lowing built-in chains: INPUT (for packets coming into the box itself), OUTPUT (for altering locally-generated packets before routing),
and FORWARD (for altering packets being routed through the box).
filter表:有 INPUT、FORWARD、OUTPUT三个链(chain)
INPUT:数据包进入本机时进行操作的规则
FORWARD:目标地址不是本机的数据包,经过本机转发,没有进入系统内核。转发处理时的规则。
OUTPUT:本机产生的数据包,出去前进行操作的规则。
-t选项:指定表
[root@lgs ~]# iptables -t filter -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
171 13076 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
2 473 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 133 packets, 20408 bytes)
pkts bytes target prot opt in out source destination
nat表:路由器的实现就是用nat原理,还可以进行端口映射。nat有 PREROUTING、OUTPUT、POSTROUTING三个链(chain)
PREROUTING:数据包进来本机时,进行修改的规则
OUTPUT:本机产生的数据包,出去前进行操作的规则。
POSTROUTING:数据包出去本机时,进行修改的规则
默认nat三个链的规则都为空
[root@lgs ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
netfilter的5表5链 参考学习文章:iptables详解 www.cnblogs.com/metoy/p/4320813.html
10.14 iptables语法
iptables -nvL 默认规则:即filter表的默认规则。在配置文件/etc/sysconfig/iptables 里定义。
[root@lgs ~]# cat /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
279 21744 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
58 5158 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 221 packets, 30752 bytes)
pkts bytes target prot opt in out source destination
-F选项:清空后规则,临时生效。重启iptables服务后还是会加载默认规则。
[root@lgs ~]# iptables -F
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 5 packets, 388 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 4 packets, 432 bytes)
pkts bytes target prot opt in out source destination
[root@lgs ~]# service iptables restart
Redirecting to /bin/systemctl restart iptables.service
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
5 388 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 496 bytes)
pkts bytes target prot opt in out source destination
要永久生效,修改规则后要保存一下:
service iptables save
-Z选项:计数器清零包数据的统计
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
55 4084 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 45 packets, 7720 bytes)
pkts bytes target prot opt in out source destination
[root@lgs ~]# iptables -Z && iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
-A选项:增加规则,在现有规则最后增加。后面指定链,-s指定源ip,-p指定协议,--sport端口,-d目标ip,-dport目标端口 -j操作 DROP 丢弃。另外有 ACCEPT 、REJECT等。
[root@lgs ~]# iptables -A INPUT -s 192.168.87.150 -p tcp --sport 1234 -d 192.168.87.130 --dport 80 -j DROP
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
194 13960 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.87.150 192.168.87.130 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 6 packets, 744 bytes)
pkts bytes target prot opt in out source destination
-I选项:插入规则,在现有规则前面插入变成第一条规则。优先过滤执行,如果有匹配的立马执行,后面有相同匹配的就不执行了。
[root@lgs ~]# iptables -I INPUT -p tcp --dport 80 -j DROP
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
306 22376 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
2 473 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.87.150 192.168.87.130 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes)
pkts bytes target prot opt in out source destination
-D选项:删除规则。
[root@lgs ~]# iptables -D INPUT -p tcp --dport 80 -j DROP
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
360 27348 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
2 473 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.87.150 192.168.87.130 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes)
pkts bytes target prot opt in out source destination
如果想删除很久之前添加的规则,但是有不记得具体的参数命令了。可以用规则编号
[root@lgs ~]# iptables -nvL --line-number
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 407 30984 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
4 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
5 2 473 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
6 0 0 DROP tcp -- * * 192.168.87.150 192.168.87.130 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 38 packets, 4860 bytes)
num pkts bytes target prot opt in out source destination
[root@lgs ~]# iptables -D INPUT 6
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
483 36808 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
2 473 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 20 packets, 2108 bytes)
pkts bytes target prot opt in out source destination
-i选项:指定网卡 -i eth0
-P选项:修改默认规则的动作策略,默认是policy ACCEPT,谨慎修改,会导致网络无法访问。
[root@lgs ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
490 37296 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
3 702 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 28 packets, 3860 bytes)
pkts bytes target prot opt in out source destination






















 1090
1090

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








