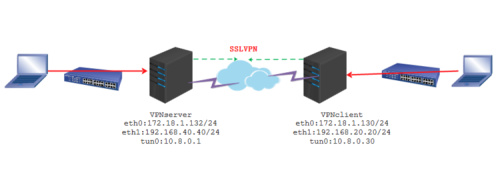
1 网络拓扑:
2 配置如下:
[root@Open***-S config]# cat server.conf
local 172.18.1.132
port 3889
proto udp
dev tun
ca /root/open***-2.3.3/config/ca.crt
cert /root/open***-2.3.3/config/***S.crt
key /root/open***-2.3.3/config/***S.key # This file should be kept secret
dh /root/open***-2.3.3/config/dh2048.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist /root/open***-2.3.3/config/ipp.txt
push "route 192.168.40.0 255.255.255.0"
client-config-dir /usr/local/open***/etc/ccd
route 192.168.20.0 255.255.255.0
client-to-client
duplicate-cn
keepalive 10 120
tls-auth /root/open***-2.3.3/config/ta.key 0 # This file is secret
cipher AES-128-CBC # AES
comp-lzo
max-clients 100
user nobody
group nobody
persist-key
persist-tun
verb 3
mute 20
[root@Open***-S config]# mkdir -p /usr/local/open***/etc/ccd
[root@Open***-S config]# vim /usr/local/open***/etc/ccd/user1
iroute 192.168.20.0 255.255.255.0 #保护子网
ifconfig-push 10.8.0.30 10.8.0.1 #指定client端ip为10.8.0.30,10.8.0.1为server端地址
[root@Open***-C config]# cat client.conf
client
dev tun
proto udp
remote 172.18.1.132 3889
resolv-retry infinite
nobind
user nobody
group nobody
persist-key
persist-tun
reneg-sec 28800 #秘钥8小时重新协商
ca /root/open***-2.3.3/config/ca.crt
cert /root/open***-2.3.3/config/user1.crt
key /root/open***-2.3.3/config/user1.key
tls-auth /root/open***-2.3.3/config/ta.key 1
ns-cert-type server
cipher AES-128-CBC
comp-lzo
verb 3
mute 20
3 打印信息如下:
服务器
[root@Open***-S config]# /usr/local/sbin/open*** --config /root/open***-2.3.3/config/server.conf
Mon Sep 4 18:46:14 2017 Open*** 2.3.3 x86_64-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Aug 31 2017
Mon Sep 4 18:46:14 2017 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Mon Sep 4 18:46:14 2017 WARNING: --ifconfig-pool-persist will not work with --duplicate-cn
Mon Sep 4 18:46:14 2017 Diffie-Hellman initialized with 2048 bit key
Mon Sep 4 18:46:14 2017 Control Channel Authentication: using '/root/open***-2.3.3/config/ta.key' as a Open*** static key file
Mon Sep 4 18:46:14 2017 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:46:14 2017 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:46:14 2017 Socket Buffers: R=[124928->131072] S=[124928->131072]
Mon Sep 4 18:46:14 2017 ROUTE_GATEWAY 172.18.1.254/255.255.254.0 IFACE=eth0 HWADDR=00:0c:29:8c:24:c0
Mon Sep 4 18:46:14 2017 TUN/TAP device tun0 opened
Mon Sep 4 18:46:14 2017 TUN/TAP TX queue length set to 100
Mon Sep 4 18:46:14 2017 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Mon Sep 4 18:46:14 2017 /sbin/ifconfig tun0 10.8.0.1 pointopoint 10.8.0.2 mtu 1500
Mon Sep 4 18:46:14 2017 /sbin/route add -net 192.168.20.0 netmask 255.255.255.0 gw 10.8.0.2
Mon Sep 4 18:46:14 2017 /sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.2
Mon Sep 4 18:46:14 2017 GID set to nobody
Mon Sep 4 18:46:14 2017 UID set to nobody
Mon Sep 4 18:46:14 2017 UDPv4 link local (bound): [AF_INET]172.18.1.132:3889
Mon Sep 4 18:46:14 2017 UDPv4 link remote: [undef]
Mon Sep 4 18:46:14 2017 MULTI: multi_init called, r=256 v=256
Mon Sep 4 18:46:14 2017 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
Mon Sep 4 18:46:14 2017 IFCONFIG POOL LIST
Mon Sep 4 18:46:14 2017 Initialization Sequence Completed
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 TLS: Initial packet from [AF_INET]172.18.1.130:45045, sid=0824b2bd 6437e902
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 VERIFY OK: depth=1, C=CN, ST=GD, L=SZ, O=softown, OU=softown_admin, CN=Open***_CA, name=EasyRSA, emailAddress=admin@softown.cn
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 VERIFY OK: depth=0, C=CN, ST=GD, L=SZ, O=softown, OU=softown_admin, CN=user1, name=EasyRSA, emailAddress=admin@softown.cn
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Mon Sep 4 18:46:21 2017 172.18.1.130:45045 [user1] Peer Connection Initiated with [AF_INET]172.18.1.130:45045
Mon Sep 4 18:46:21 2017 user1/172.18.1.130:45045 OPTIONS IMPORT: reading client specific options from: /usr/local/open***/etc/ccd/user1
Mon Sep 4 18:46:21 2017 user1/172.18.1.130:45045 MULTI: Learn: 10.8.0.30 -> user1/172.18.1.130:45045
Mon Sep 4 18:46:21 2017 user1/172.18.1.130:45045 MULTI: primary virtual IP for user1/172.18.1.130:45045: 10.8.0.30
Mon Sep 4 18:46:21 2017 user1/172.18.1.130:45045 MULTI: internal route 192.168.20.0/24 -> user1/172.18.1.130:45045
Mon Sep 4 18:46:21 2017 user1/172.18.1.130:45045 MULTI: Learn: 192.168.20.0/24 -> user1/172.18.1.130:45045
Mon Sep 4 18:46:23 2017 user1/172.18.1.130:45045 PUSH: Received control message: 'PUSH_REQUEST'
Mon Sep 4 18:46:23 2017 user1/172.18.1.130:45045 send_push_reply(): safe_cap=940
Mon Sep 4 18:46:23 2017 user1/172.18.1.130:45045 SENT CONTROL [user1]: 'PUSH_REPLY,route 192.168.40.0 255.255.255.0,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.30 10.8.0.1' (status=1)
客户端
[root@Open***-C ~]# /usr/local/sbin/open*** --config /root/open***-2.3.3/config/client.conf
Mon Sep 4 18:45:16 2017 Open*** 2.3.3 x86_64-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Aug 31 2017
Mon Sep 4 18:45:16 2017 Control Channel Authentication: using '/root/open***-2.3.3/config/ta.key' as a Open*** static key file
Mon Sep 4 18:45:16 2017 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:45:16 2017 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:45:16 2017 Socket Buffers: R=[124928->131072] S=[124928->131072]
Mon Sep 4 18:45:16 2017 NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay
Mon Sep 4 18:45:16 2017 UDPv4 link local: [undef]
Mon Sep 4 18:45:16 2017 UDPv4 link remote: [AF_INET]172.18.1.132:3889
Mon Sep 4 18:45:16 2017 TLS: Initial packet from [AF_INET]172.18.1.132:3889, sid=caab9acf 35e9a489
Mon Sep 4 18:45:16 2017 VERIFY OK: depth=1, C=CN, ST=GD, L=SZ, O=softown, OU=softown_admin, CN=Open***_CA, name=EasyRSA, emailAddress=admin@softown.cn
Mon Sep 4 18:45:16 2017 VERIFY OK: nsCertType=SERVER
Mon Sep 4 18:45:16 2017 VERIFY OK: depth=0, C=CN, ST=GD, L=SZ, O=softown, OU=softown_admin, CN=***S, name=EasyRSA, emailAddress=admin@softown.cn
Mon Sep 4 18:45:16 2017 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Sep 4 18:45:16 2017 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:45:16 2017 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Sep 4 18:45:16 2017 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Sep 4 18:45:16 2017 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Mon Sep 4 18:45:16 2017 [***S] Peer Connection Initiated with [AF_INET]172.18.1.132:3889
Mon Sep 4 18:45:18 2017 SENT CONTROL [***S]: 'PUSH_REQUEST' (status=1)
Mon Sep 4 18:45:18 2017 PUSH: Received control message: 'PUSH_REPLY,route 192.168.40.0 255.255.255.0,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.30 10.8.0.1'
Mon Sep 4 18:45:18 2017 OPTIONS IMPORT: timers and/or timeouts modified
Mon Sep 4 18:45:18 2017 OPTIONS IMPORT: --ifconfig/up options modified
Mon Sep 4 18:45:18 2017 OPTIONS IMPORT: route options modified
Mon Sep 4 18:45:18 2017 ROUTE_GATEWAY 172.18.1.254/255.255.254.0 IFACE=eth0 HWADDR=00:0c:29:b5:22:a8
Mon Sep 4 18:45:18 2017 TUN/TAP device tun0 opened
Mon Sep 4 18:45:18 2017 TUN/TAP TX queue length set to 100
Mon Sep 4 18:45:18 2017 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Mon Sep 4 18:45:18 2017 /sbin/ifconfig tun0 10.8.0.30 pointopoint 10.8.0.1 mtu 1500
Mon Sep 4 18:45:18 2017 /sbin/route add -net 192.168.40.0 netmask 255.255.255.0 gw 10.8.0.1
Mon Sep 4 18:45:18 2017 /sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.1
Mon Sep 4 18:45:18 2017 GID set to nobody
Mon Sep 4 18:45:18 2017 UID set to nobody
Mon Sep 4 18:45:18 2017 Initialization Sequence Completed
4 测试
服务器 -> 客户端
[root@Open***-S config]# ping 10.8.0.30 #ping客户端隧道地址
PING 10.8.0.30 (10.8.0.30) 56(84) bytes of data.
64 bytes from 10.8.0.30: icmp_seq=1 ttl=64 time=0.615 ms
64 bytes from 10.8.0.30: icmp_seq=2 ttl=64 time=0.706 ms
64 bytes from 10.8.0.30: icmp_seq=3 ttl=64 time=0.911 ms
64 bytes from 10.8.0.30: icmp_seq=4 ttl=64 time=0.877 ms
--- 10.8.0.30 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3407ms
rtt min/avg/max/mdev = 0.615/0.777/0.911/0.123 ms
[root@Open***-S config]# ping 192.168.20.20 #ping客户端LAN地址
PING 192.168.20.20 (192.168.20.20) 56(84) bytes of data.
64 bytes from 192.168.20.20: icmp_seq=1 ttl=64 time=0.533 ms
64 bytes from 192.168.20.20: icmp_seq=2 ttl=64 time=0.689 ms
64 bytes from 192.168.20.20: icmp_seq=3 ttl=64 time=0.929 ms
64 bytes from 192.168.20.20: icmp_seq=4 ttl=64 time=0.936 ms
--- 192.168.20.20 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3412ms
rtt min/avg/max/mdev = 0.533/0.771/0.936/0.173 ms
[root@Open***-S ~]# ping -I 192.168.40.40 192.168.20.20 #通过服务器LAN去ping客户端LAN地址
PING 192.168.20.20 (192.168.20.20) from 192.168.40.40 : 56(84) bytes of data.
64 bytes from 192.168.20.20: icmp_seq=1 ttl=64 time=0.497 ms
64 bytes from 192.168.20.20: icmp_seq=2 ttl=64 time=0.865 ms
64 bytes from 192.168.20.20: icmp_seq=3 ttl=64 time=0.712 ms
64 bytes from 192.168.20.20: icmp_seq=4 ttl=64 time=0.775 ms
--- 192.168.20.20 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3422ms
rtt min/avg/max/mdev = 0.497/0.712/0.865/0.136 ms
客户端 -> 服务器
[root@Open***-C config]# ping 10.8.0.1 #ping服务器隧道地址
PING 10.8.0.1 (10.8.0.1) 56(84) bytes of data.
64 bytes from 10.8.0.1: icmp_seq=1 ttl=64 time=0.788 ms
64 bytes from 10.8.0.1: icmp_seq=2 ttl=64 time=0.877 ms
64 bytes from 10.8.0.1: icmp_seq=3 ttl=64 time=0.951 ms
64 bytes from 10.8.0.1: icmp_seq=4 ttl=64 time=0.684 ms
--- 10.8.0.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3476ms
rtt min/avg/max/mdev = 0.684/0.825/0.951/0.099 ms
[root@Open***-C config]# ping 192.168.40.40 #ping服务LAN地址
PING 192.168.40.40 (192.168.40.40) 56(84) bytes of data.
64 bytes from 192.168.40.40: icmp_seq=1 ttl=64 time=0.545 ms
64 bytes from 192.168.40.40: icmp_seq=2 ttl=64 time=0.953 ms
64 bytes from 192.168.40.40: icmp_seq=3 ttl=64 time=0.793 ms
64 bytes from 192.168.40.40: icmp_seq=4 ttl=64 time=0.949 ms
--- 192.168.40.40 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3335ms
rtt min/avg/max/mdev = 0.545/0.810/0.953/0.166 ms
[root@Open***-C ~]# ping -I 192.168.20.20 192.168.40.40 #通过客户端LAN去ping服务LAN地址
PING 192.168.40.40 (192.168.40.40) from 192.168.20.20 : 56(84) bytes of data.
64 bytes from 192.168.40.40: icmp_seq=1 ttl=64 time=0.617 ms
64 bytes from 192.168.40.40: icmp_seq=2 ttl=64 time=0.704 ms
64 bytes from 192.168.40.40: icmp_seq=3 ttl=64 time=0.652 ms
64 bytes from 192.168.40.40: icmp_seq=4 ttl=64 time=0.750 ms
--- 192.168.40.40 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3350ms
rtt min/avg/max/mdev = 0.617/0.680/0.750/0.059 ms
转载于:https://blog.51cto.com/linuxcgi/1965234





















 1824
1824











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








