硬件防火墙 ASA
【实验名称】:
硬件防火墙ASA的配置
【实验原理】:
【实验背景】:
思科ASA5500系列自适应安全设备是能够为从小型办公室、家庭办公室和中小型企业到大型企业的各类环境提供新一代安全性和×××服务模块化安全平台。思科ASA5500系列能为企业提供全面的服务,而且这些服务都可以根据客户对防火墙、***防御、Anit-X和×××的要求而特别制定。
【实验环境】:
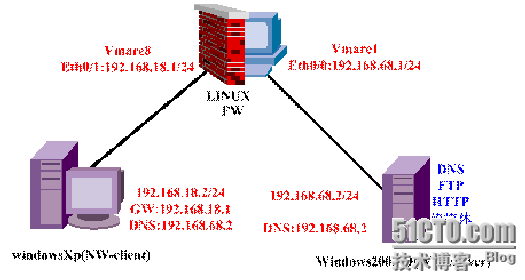
Windows2003-C(DNS-Server):192.168.68.2/24 GW:192.168.68.1
windowsXp(client):192.168.18.2/24 GW:192.168.18.1 DNS:192.168.68.2
ASAFW:eth0/1[内网Vmare1]:192.168.18.1 255.255.255.0
eth0/1[外网Vmare8]:192.168.68.1 255.255.255.0
注意:
安装ASA:
1. 解压缩ASA-VM6.5.1.rar文件。
2. 安装解压文件夹中的WinPcap_4_0_1.exe
3. 安装解压文件夹中的nptp.exe
4. 使用vmware workstation6.5以上版本的虚拟机软件,打开“Other Linux 2.6.x kernel.vmx”虚拟机系统。
5. 运行Named Pipe TCP Proxy程序,并在其中选择工具“create new pipe connector”,设置pipe为“\\.\pipe\asa”,同时指定一个空闲的端口号码,如1688.
6. 使用telnet ip 1688的方式连接ASA防火墙,即可开始试验。
【实验拓扑】:
【实验目标】:
配置基本ASA:
1. 配置主机名、域名和密码
2.配置接口
3.配置路由
4.配置远程管理接入
5.为出站流量配置网络地址转换
6.配置ACL
7.测试
配置ASA的高级配置--URL过滤
配置日志
启用基本威胁检测
IDS的配置
启用远程管理的配置:
【实验步骤】:
配置基本ASA:
ciscoasa>
ciscoasa> enable
Password:
ciscoasa# config t
ciscoasa(config)#
ciscoasa(config)# hostname ASA5520
ASA5520(config)#
ASA5520(config)# domain-name xapc.com
ASA5520(config)#
ASA5520(config)# enable password ASA5520
ASA5520(config)#
ASA5520(config)# passwd cisco
ASA5520(config)#
ASA5520(config)# config t
ASA5520(config)#
ASA5520(config)# interface ethernet 0/0
ASA5520(config-if)#
ASA5520(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
ASA5520(config-if)#
ASA5520(config-if)# security-level 0
ASA5520(config-if)#
ASA5520(config-if)# ip address 192.168.68.1 255.255.255.0
ASA5520(config-if)#
ASA5520(config-if)# no shutdown
ASA5520(config-if)#
ASA5520(config-if)# exit
ASA5520(config)#
ASA5520(config)#
ASA5520(config)#
ASA5520(config)# interface ethernet 0/1
ASA5520(config-if)#
ASA5520(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ASA5520(config-if)#
ASA5520(config-if)# security-level 100
ASA5520(config-if)#
ASA5520(config-if)# ip address 192.168.18.1 255.255.255.0
ASA5520(config-if)#
ASA5520(config-if)# no shutdown
ASA5520(config-if)#
ASA5520(config-if)# exit
ASA5520(config)#
ASA5520(config)# route outside 0.0.0.0 0.0.0.0 192.168.68.1
ASA5520(config)#
ASA5520(config)# end
ASA5520#
ASA5520# show route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 192.168.68.1 to network 0.0.0.0
C 192.168.68.0 255.255.255.0 is directly connected, outside
C 192.168.18.0 255.255.255.0 is directly connected, inside
S* 0.0.0.0 0.0.0.0 [1/0] via 192.168.68.1, outside
ASA5520#
ASA5520# conf t
ASA5520(config)#
ASA5520(config)# telnet 192.168.18.0 255.255.255.0 inside
ASA5520(config)#
ASA5520(config)# telnet timeout 15
ASA5520(config)#
ASA5520(config)# crypto key generate rsa modulus 1024
INFO: The name for the keys will be: <Default-RSA-Key>
Keypair generation process begin. Please wait...
ASA5520(config)#
ASA5520(config)# ssh 192.168.18.0 255.255.255.0 inside
ASA5520(config)#
ASA5520(config)# ssh 0 0 outside
ASA5520(config)#
ASA5520(config)# ssh timeout 30
ASA5520(config)#
ASA5520(config)# ssh version 2
ASA5520(config)#
ASA5520(config)# http server enable 8080
ASA5520(config)#
ASA5520(config)# http 192.168.18.0 255.255.255.0 inside
ASA5520(config)#
ASA5520(config)# http 0 0 outside
ASA5520(config)#
ASA5520(config)# http 0 0 inside
ASA5520(config)#
ASA5520(config)# username xapc password xapccom privilege 15
ASA5520(config)#
ASA5520(config)# nat-control
ASA5520(config)#
ASA5520(config)# nat (inside) 1 0 0
ASA5520(config)#
ASA5520(config)# global (outside) 1 interface
INFO: outside interface address added to PAT pool
ASA5520(config)#
ASA5520(config)# access-list in_to_out permit ip any any
ASA5520(config)#
ASA5520(config)# access-group in_to_out in interface inside
ASA5520(config)#
ASA5520(config)# access-list 111 permit icmp any any echo-reply
ASA5520(config)#
ASA5520(config)# access-list 111 permit icmp any any unreachable
ASA5520(config)#
ASA5520(config)# access-list 111 permit icmp any any time-exceeded
ASA5520(config)#
ASA5520(config)# access-list 111 permit icmp any any
ASA5520(config)#
ASA5520(config)# access-list 111 permit ip any any
ASA5520(config)#
ASA5520(config)# access-group 111 in int outside
ASA5520(config)#
ASA5520(config)# access-group 111 in int inside
ASA5520(config)#
ASA5520(config)# end
ASA5520#
ASA5520#
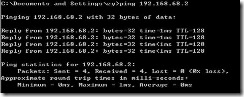
测试验证:
配置ASA的高级配置--URL过滤
ASA5520# config t
ASA5520(config)#
ASA5520(config)# access-list tcp_filter1 permit tcp 192.168.18.0 255.255.255.2$
ASA5520(config)#
ASA5520(config)#
ASA5520(config)#
ASA5520(config)# class-map tcp_filter_class1
ASA5520(config-cmap)#
ASA5520(config-cmap)# match access-list tcp_filter1
ASA5520(config-cmap)#
ASA5520(config-cmap)# exit
ASA5520(config)#
ASA5520(config)#
ASA5520(config)#
ASA5520(config)# regex url1 \.sina\.com
ASA5520(config)#
ASA5520(config)#
ASA5520(config)#
ASA5520(config)# class-map type regex match-any url_class1
ASA5520(config-cmap)#
ASA5520(config-cmap)# match regex url1
ASA5520(config-cmap)#
ASA5520(config-cmap)# exit
ASA5520(config)#
ASA5520(config)#
ASA5520(config)#
ASA5520(config)# class-map type inspect http http_url_class1
ASA5520(config-cmap)#
ASA5520(config-cmap)# match not request header host regex class url_class1
ASA5520(config-cmap)#
ASA5520(config-cmap)# exit
ASA5520(config)#
ASA5520(config)# policy-map type inspect http http_url_policy1
ASA5520(config-pmap)#
ASA5520(config-pmap)# class http_url_class1
ASA5520(config-pmap-c)#
ASA5520(config-pmap-c)# drop-connection log
ASA5520(config-pmap-c)#
ASA5520(config-pmap-c)# exit
ASA5520(config-pmap)#
ASA5520(config-pmap)# exit
ASA5520(config)#
ASA5520(config)#
ASA5520(config)#
ASA5520(config)# policy-map inside_http_url_policy
ASA5520(config-pmap)#
ASA5520(config-pmap)# class tcp_filter_class1
ASA5520(config-pmap-c)#
ASA5520(config-pmap-c)# inspect http http_url_policy1
ASA5520(config-pmap-c)#
ASA5520(config-pmap-c)# exit
ASA5520(config-pmap)#
ASA5520(config-pmap)# exit
ASA5520(config)#
ASA5520(config)# policy-map inside_http_url_policy
ASA5520(config-pmap)#
ASA5520(config-pmap)# class tcp_filter_class1
ASA5520(config-pmap-c)#
ASA5520(config-pmap-c)# inspect http http_url_policy1
ASA5520(config-pmap-c)#
ASA5520(config-pmap-c)# exit
ASA5520(config-pmap)#
ASA5520(config-pmap)# exit
ASA5520(config)#
ASA5520(config)# service-policy inside_http_url_policy interface inside
ASA5520(config)#
ASA5520(config)#
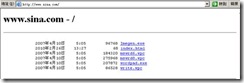
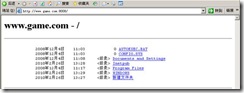
测试验证:
配置日志
ASA5520(config)#
ASA5520(config)# logging enable
ASA5520(config)#
ASA5520(config)# logging buffered informational
ASA5520(config)#
ASA5520(config)# logging asdm informational
ASA5520(config)#
ASA5520(config)# logging trap informational
ASA5520(config)#
ASA5520(config)# logging host inside 192.168.18.1
ASA5520(config)#
启用基本威胁检测
ASA5520(config)# threat-detection basic-threat
ASA5520(config)#
ASA5520(config)# fragment chain 1
ASA5520(config)#
IDS的配置
ASA5520(config)# ip audit name inside_ids_info info action alarm
ASA5520(config)#
ASA5520(config)# ip audit name inside_ids_attack attack action alarm
ASA5520(config)#
ASA5520(config)# ip audit name outside_ids_info info action alarm
ASA5520(config)#
ASA5520(config)# ip audit name outside_ids_attack attack action alarm reset
ASA5520(config)#
ASA5520(config)# ip audit interface inside inside_ids_info
ASA5520(config)#
ASA5520(config)# ip audit interface inside inside_ids_attack
ASA5520(config)#
ASA5520(config)# ip audit interface outside outside_ids_info
ASA5520(config)#
ASA5520(config)# ip audit interface outside outside_ids_attack
ASA5520(config)# ip audit signature 2000 disable
ASA5520(config)#
ASA5520(config)# no ip audit signature 2000
启用远程管理的配置:
ASA5520(config)# config t
ASA5520(config)#
ASA5520(config)# web***
ASA5520(config-web***)#
ASA5520(config-web***)# username zhang password cisco
ASA5520(config)#
ASA5520(config)# http server enable
ASA5520(config)#
ASA5520(config)# http 192.168.18.0 255.255.255.0 inside
ASA5520(config)#
ASA5520(config)# end
【参考配置】
enable
config t
hostname ASA5520 -----修改主机名
domain-name xapc.com.cn -----修改DNS域名
enable password ASA5520 -----设置相应的登录密码
passwd cisco
config t
interface ethernet 0/0
nameif outside ---配置接口名字
security-level 0 ---配置接口的安全级别(outside默认为0)
ip address 192.168.68.1 255.255.255.0 ----配置接口IP
no shutdown
exit
interface ethernet 0/1
nameif inside ---配置接口名字
security-level 100 ---配置接口安全级别(inside默认为100)
ip address 192.168.18.1 255.255.255.0 ---配置接口IP
no shutdown
exit
route outside 0.0.0.0 0.0.0.0 192.168.68.1 ---配置缺省路由
end
show route
配置远程管理接入
conf t
telnet 192.168.18.0 255.255.255.0 inside
telnet timeout 15 ---配置空闲超时时间
配置SSH接入
crypto key generate rsa modulus 1024 ----生成RSA密钥对
ssh 192.168.18.0 255.255.255.0 inside ----配置防火墙允许SSH接入
ssh 0 0 outside
ssh timeout 30 ---配置空闲超时时间
ssh version 2 ---配置版本
配置ASDM(自适应安全设备管理器)接入
http 192.168.18.0 255.255.255.0 inside ---配置防火墙允许HTTPS接入
http 0 0 outside
http 0 0 inside
(asdm image disk0:/asdmfile) ---指定ASDM的镜像位置
username xapc password xapccomcn privilege 15 ---配置客户端登录使用的用户名和密码
为出站流量配置网络地址转换
nat-control
nat (inside) 1 0 0 ---指定要转换流量的种类为“inside”
global (outside) 1 interface ---指定一个全局地支池
配置ACL
access-list in_to_out deny ip 192.168.18.0 255.255.255.240 any ---指定访问控制列表
access-list in_to_out permit ip any any
access-group in_to_out in interface inside ---将ACL应用到接口
清空ACL
no access-list in_to_out deny ip 192.168.18.0 255.255.255.240 any
no access-list in_to_out permit ip any any
no access-group in_to_out in interface inside
配置ICMP协议
access-list 111 permit icmp any any echo-reply
access-list 111 permit icmp any any unreachable
access-list 111 permit icmp any any time-exceeded
no access-list 111 permit icmp any any echo-reply
no access-list 111 permit icmp any any unreachable
no access-list 111 permit icmp any any time-exceeded
access-list 111 permit icmp any any
access-list 111 permit ip any any
access-group 111 in int outside
access-group 111 in int inside
end
保存配置
write memory
copy running-config startup-config
清除配置信息:
conf t
clear configure all
clear configure command [level2 command]
end
****************************************************************************
ASA的高级配置--URL过滤
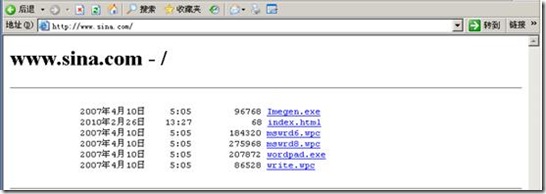
####sina.com####
创建class-map,识别传输流量
config t
access-list tcp_filter1 permit tcp 192.168.18.0 255.255.255.240 any eq www
class-map tcp_filter_class1
match access-list tcp_filter1
exit
regex url1 \.sina\.com
class-map type regex match-any url_class1
match regex url1
exit
class-map type inspect http http_url_class1
match not request header host regex class url_class1
exit
创建policy-map,关联class-map
policy-map type inspect http http_url_policy1
class http_url_class1
drop-connection log
exit
exit
policy-map inside_http_url_policy
class tcp_filter_class1
inspect http http_url_policy1
exit
exit
应用policy-map到接口上
service-policy inside_http_url_policy interface inside
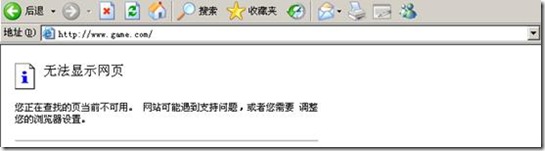
#####game.com#######
access-list tcp_filter2 permit tcp any any eq www
class-map tcp_filter_class2
match access-list tcp_filter2
exit
regex url2 \.game\.com
class-map type regex match-any url_class2
match regex url2
exit
class-map type inspect http http_url_class2
match request header host regex class url_class2
exit
policy-map type inspect http http_url_policy2
class http_url_class2
drop-connection log
exit
exit
policy-map inside_http_url_policy
class tcp_filter_class2
inspect http http_url_policy2
exit
exit
service-policy inside_http_url_policy interface inside
*************************************************************************
配置日志
+配置Log Buffer:
logging enable
logging buffered informational
+配置ASDM日志
logging asdm informational
+配置日志服务器
logging trap informational
logging host inside 192.168.18.1
**************************************************************************
启用基本威胁检测
threat-detection basic-threat
防范IP分片***
fragment chain 1
IDS的配置
ip audit name name {info | attack} [action [alarm] [drop] [reset]]
ip audit name inside_ids_info info action alarm
ip audit name inside_ids_attack attack action alarm
ip audit name outside_ids_info info action alarm
ip audit name outside_ids_attack attack action alarm reset
ip audit interface inside inside_ids_info
ip audit interface inside inside_ids_attack
ip audit interface outside outside_ids_info
ip audit interface outside outside_ids_attack
ip audit signature 2000 disable ---禁用为2000的签名
no ip audit signature 2000 -----重新启用ID为2000的签名
*************************************************************************
启用远程管理的配置:
config t
web***
username zhang password cisco
http server enable
http 192.168.18.0 255.255.255.0 inside
end
***************************************************************************
在ASA上配置IPSec ×××:
基本配置
conf t
route outside 0 0 ISP网关
nat-control
nat (inside) 1 0 0
global (outside) 1 interface
NAT豁免,即指定某些地址的流量不进行NAT转换
access-list nonat extended permit ip 192.168.18.0 255.255.255.0 192.168.68.0 255.255.255.0
nat (inside) 0 access-list nonat
启用ISAKMP(cisco路由器上IKE默认是启用的,但ASA防火墙上IKE默认为关闭,必须显式启用)
crypto isakmp enable outside
配置ISAKMP策略(防火墙与路由器在策略的默认设置上存在差异,主要是在加密、HASH算法以及身份认证方式上存在差异)
crypto isakmp policy 1
encryption aes
hash sha
authentication pre-share
group 1
exit
isakmp key xapcedu address 192.168.68.2
ASA 7.0及以上版本一般使用隧道组来配置(当企业内部需要建立多条×××隧道时,隧道组可以减少配置量)
tunnel-group 200.0.0.1 type ipsec-l2l
tunnel-group 200.0.0.1 ipsec-attributes
pre-shared-key xapcedu
exit
配置crypto ACL (只能使用名称列表)
access-list xa*** extended permit ip 192.168.18.0 255.255.255.0 192.168.68.0 255.255.255.0
配置数据连接的传输集
crypto ipsec transform-set xapc-set esp-aes esp-sha-hmac
配置crypto map并应用到outside接口上
crypto map xapc-map 1 match address xa***
crypto map xapc-map 1 set peer 192.168.68.2
crypto map xapc-map 1 set transform-set xapc-set
crypto map xapc-map interface outside
==========================================
路由器实现NAT-T
外网发起建立管理连接或数据连接
conf t
ip nat inside source list access-list-number interface f0/1 overload
ip nat inside source static udp local-ip 500 interface f0/1 500
ip nat inside source static udp local-ip 4500 interface f0/1 4500
debug crypto isakmp
show crypto isakmp sa
debug crypto ipsec
转载于:https://blog.51cto.com/dnsdhcp/601933





















 381
381











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








