hellopasswd
iptables nat
- nat表应用
- A机器两块网卡ens33(192.168.133.130)、ens37(192.168.100.1),ens33可以上外网,ens37仅仅是内部网络,B机器只有ens37(192.168.100.100),和A机器ens37可以通信互联。
- 需求1:可以让B机器连接外网
- A机器上打开路由转发 echo "1" > /proc/sys/net/ipv4/ip_forward
- A上执行iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -o ens33 -j MASQUERADE
- B上设置网关为192.168.100.1
- 需求2:C机器只能和A通信,让C机器可以直接连通B机器的22端口
- A上打开路由转发echo "1" > /proc/sys/net/ipv4/ip_forward
- A上执行iptables -t nat -A PREROUTING -d 192.168.133.130 -p tcp --dport 1122 -j DNAT --to 192.168.100.100:22
- A上执行iptables -t nat -A POSTROUTING -s 192.168.100.100 -j SNAT --to 192.168.133.130
- B上设置网关为192.168.100.1
内网Linux连接外网
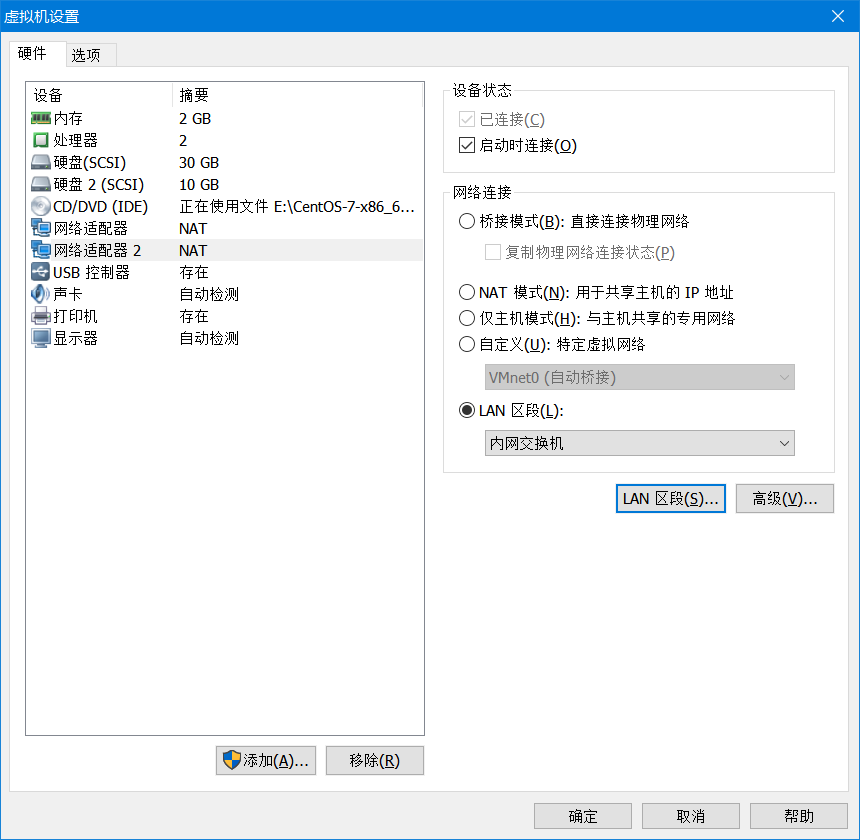
首先Linux主机1 设置 添加网卡
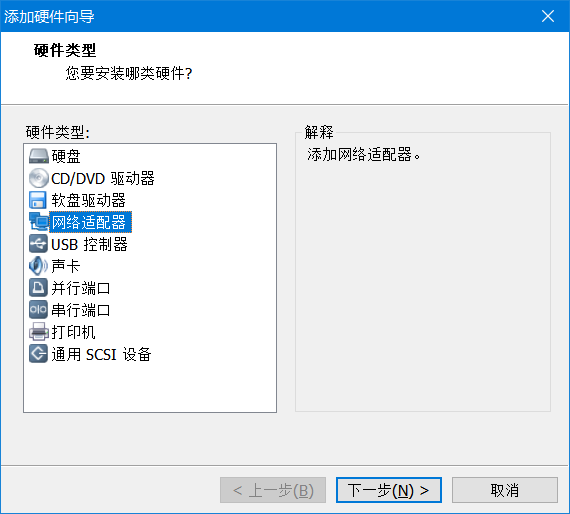
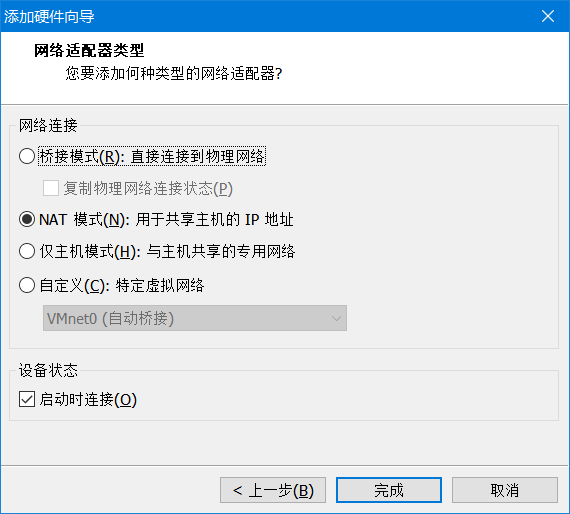
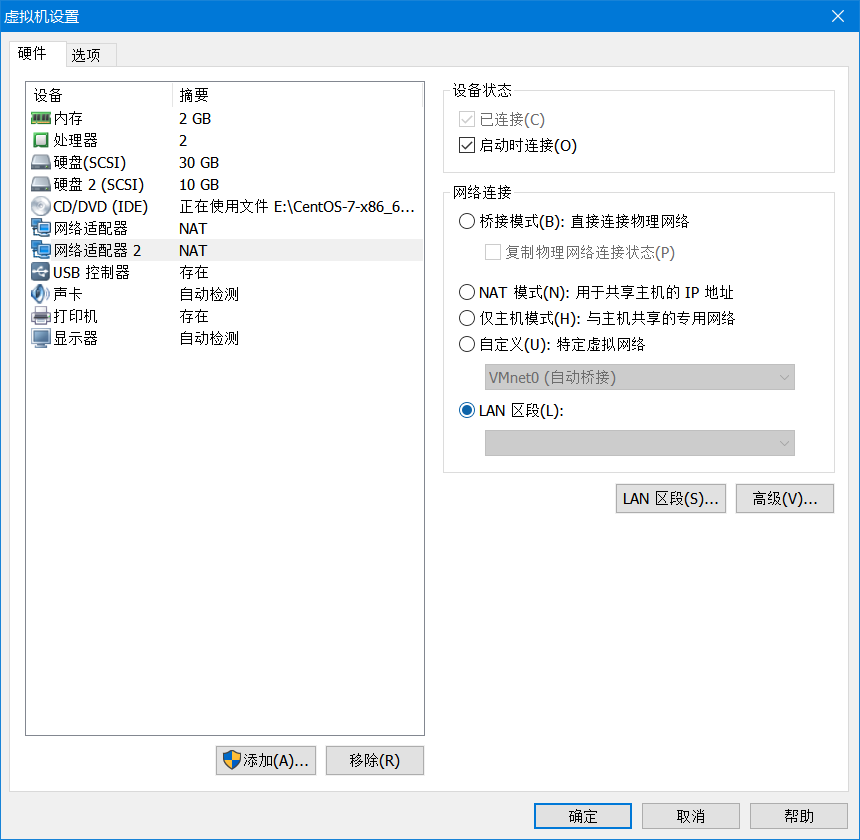
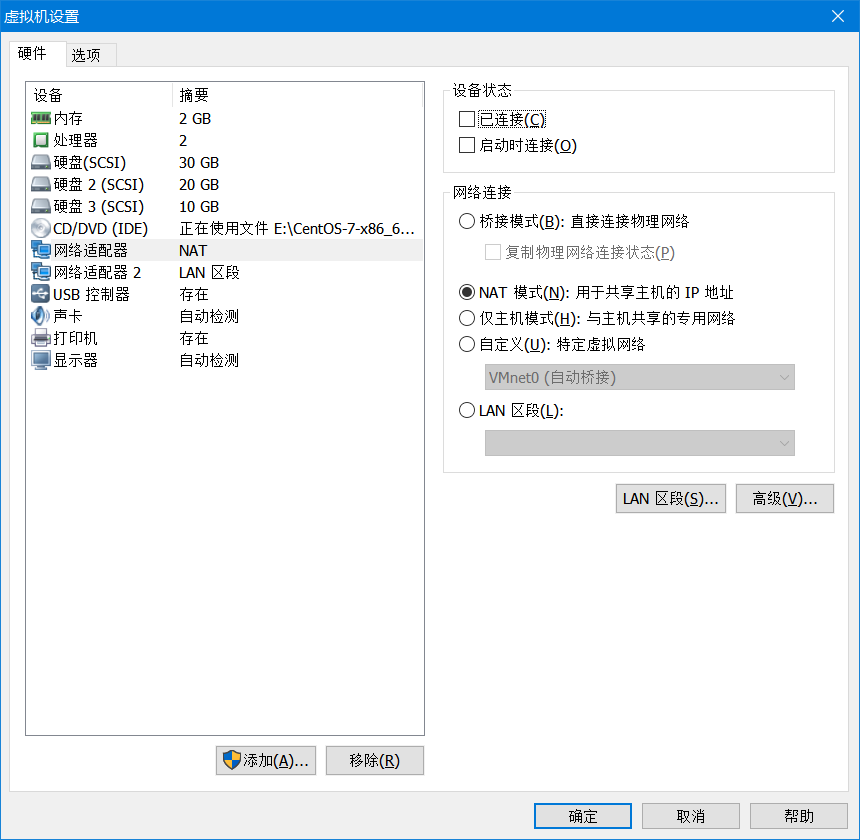
Linux主机2 取消 启动时连接,然后一切同上
这时Linux主机B终端连接会失败,因为ip更改或取消
- Linux主机A
[root@localhost ~]# ifconfig
eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.9.134 netmask 255.255.255.0 broadcast 192.168.9.255
inet6 fe80::20c:29ff:fe0a:e7fc prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:0a:e7:fc txqueuelen 1000 (Ethernet)
RX packets 429 bytes 30383 (29.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 77 bytes 13013 (12.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eno16777736:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.9.139 netmask 255.255.255.0 broadcast 192.168.9.255
ether 00:0c:29:0a:e7:fc txqueuelen 1000 (Ethernet)
ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet6 fe80::20c:29ff:fe0a:e706 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:0a:e7:06 txqueuelen 1000 (Ethernet)
RX packets 41 bytes 14022 (13.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 14 bytes 2172 (2.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 0 (Local Loopback)
RX packets 2 bytes 196 (196.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2 bytes 196 (196.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
设置临时ip
[root@localhost ~]# ifconfig ens37 192.168.100.1/24
[root@localhost ~]# ifconfig
eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.9.134 netmask 255.255.255.0 broadcast 192.168.9.255
inet6 fe80::20c:29ff:fe0a:e7fc prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:0a:e7:fc txqueuelen 1000 (Ethernet)
RX packets 557 bytes 39888 (38.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 118 bytes 18957 (18.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eno16777736:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.9.139 netmask 255.255.255.0 broadcast 192.168.9.255
ether 00:0c:29:0a:e7:fc txqueuelen 1000 (Ethernet)
ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.100.1 netmask 255.255.255.0 broadcast 192.168.100.255
inet6 fe80::20c:29ff:fe0a:e706 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:0a:e7:06 txqueuelen 1000 (Ethernet)
RX packets 41 bytes 14022 (13.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 25 bytes 4907 (4.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 0 (Local Loopback)
RX packets 2 bytes 196 (196.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2 bytes 196 (196.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
- Linux主机B
ifconfig
ifdown ens33
ifconfig ens37 192.168.100.100/24
ifconfig
ping 192.168.100.1
- Windows主机
C:\Users\Administrator>ping 192.168.100.1
正在 Ping 192.168.100.1 具有 32 字节的数据:
请求超时。
请求超时。
请求超时。
请求超时。
192.168.100.1 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 0,丢失 = 4 (100% 丢失),
C:\Users\Administrator>ping 192.168.100.100
正在 Ping 192.168.100.100 具有 32 字节的数据:
请求超时。
请求超时。
请求超时。
请求超时。
192.168.100.100 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 0,丢失 = 4 (100% 丢失),
- Linux主机B
ping 192.168.9.134
ping www.baidu.com
- Linux主机A
打开端口转发
[root@localhost ~]# cat /proc/sys/net/ipv4/ip_forward
0
[root@localhost ~]# echo "1" > !$
echo "1" > /proc/sys/net/ipv4/ip_forward
[root@localhost ~]# !cat
cat /proc/sys/net/ipv4/ip_forward
1
[root@localhost ~]# iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -o eno16777736 -j MASQUERADE
[root@localhost ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * ens33 192.168.100.0/24 0.0.0.0/0
这里我出现了一个很严重的问题,Linux主机A的网卡不为ens33,只顾一味照抄是非常严重的错误!!!
- Linux主机B
route -n
route add default gw 192.168.100.1
route -n
ping 192.168.9.134
终端连接内网Linux
端口映射
- Linux主机A
[root@localhost ~]# cat /proc/sys/net/ipv4/ip_forward
1
[root@localhost ~]# iptables -t nat -D POSTROUTING -s 192.168.100.0/24 -o eno16777736 -j MASQUERADE
[root@localhost ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
[root@localhost ~]# iptables -t nat -A PREROUTING -d 192.168.9.134 -p tcp --dport 1122 -j DNAT --to 192.168.100.100:22
指把进来的包,转发到192.168.100.100的22端口,同时回来的包也要作操作
[root@localhost ~]# iptables -t nat -A POSTROUTING -s 192.168.100.100 -j SNAT --to 192.168.9.134
iptables 规则备份和恢复
- 保存和备份iptables规则
- service iptables save #将规则保存到/etc/sysconfig/iptables
- 把iptables规则备份到my.ipt文件中
- iptables-save > my.ipt
- 恢复刚才备份的规则
- iptables-restore < my.ipt
临时备份
[root@localhost ~]# iptables-save > /tmp/ipt.txt
[root@localhost ~]# cat /tmp/ipt.txt
# Generated by iptables-save v1.4.21 on Sat Dec 2 03:21:24 2017
*nat
:PREROUTING ACCEPT [42:3651]
:INPUT ACCEPT [3:268]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 192.168.100.0/24 -o eno16777736 -j MASQUERADE
COMMIT
# Completed on Sat Dec 2 03:21:24 2017
# Generated by iptables-save v1.4.21 on Sat Dec 2 03:21:24 2017
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [78:8880]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
# Completed on Sat Dec 2 03:21:24 2017
恢复
[root@localhost ~]# iptables -t nat -F
[root@localhost ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
[root@localhost ~]# iptables-restore < /tmp/ipt.txt
[root@localhost ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * eno16777736 192.168.100.0/24 0.0.0.0/0
永久备份
cp备份/etc/sysconfig/iptables
总结:设置两台主机内网Linux的IP地址,并且同一个网段内能够通信/proc/sys/net/ipv4/ip_forward,连接主机ip设置iptables规则,并且在主机B设置网关和DNS,实现内网Linux内通信到访问外网
修改于 171130






















 149
149

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








