一、背景
ftp是一个古老协议,明文传输数据,所以为了安全需要结合ssl证书加密通讯 。本文是继上两篇的扩展优化。
二、创建本地ssl证书
#(umask 077;openssl genrsa -out /etc/vsftpd/ftpkey.pri 2048) #openssl req -new -key /etc/vsftpd/ftpkey.pri -out /etc/vsftpd/ftpreq.csr # (umask 077;openssl genrsa -out /etc/vsftpd/ftpkey.pri 2048)
Generating RSA private key, 2048 bit long modulus
..............................................................+++
............+++
e is 65537 (0x10001)
]# openssl req -new -key /etc/vsftpd/ftpkey.pri -out /etc/vsftpd/ftpreq.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:ShangHai
Locality Name (eg, city) [Default City]:xuihui
Organization Name (eg, company) [Default Company Ltd]:testkey
Organizational Unit Name (eg, section) []:testkey
Common Name (eg, your name or your server's hostname) []:192.168.10.168
Email Address []:14921xxx@qq.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
#(umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 3650 touch /etc/pki/CA/index.txt echo "01" >/etc/pki/CA/serial openssl ca -in /etc/vsftpd/ftpreq.csr -out /etc/vsftpd/certftp.crt -days 3650
三、vsftpd.conf配置
cat /etc/vsftpd/vsftpd.conf |egerp -v '(^$|^#)'
#数据连接侦听端口 listen_port=10021 #禁止匿名用户访问 anonymous_enable=NO local_enable=YES write_enable=YES local_umask=022 dirmessage_enable=YES xferlog_enable=YES xferlog_std_format=YES xferlog_file=/var/log/xferlog dual_log_enable=YES vsftpd_log_file=/var/log/vsftpd.log connect_from_port_20=YES chroot_list_enable=YES chroot_list_file=/etc/vsftpd/chroot_list listen=YES max_clients=20 max_per_ip=2 local_max_rate=409600 pam_service_name=vsftpd userlist_enable=YES tcp_wrappers=YES pasv_enable=YES pasv_min_port=65530 pasv_max_port=65535 #证书位置 rsa_cert_file=/etc/vsftpd/certftp.crt rsa_private_key_file=/etc/vsftpd/ftpkey.pri #开启ssl ssl_enable=YES allow_anon_ssl=NO ssl_tlsv1=YES ssl_sslv2=YES ssl_sslv3=YES #强制使用ssl安全连接 force_local_data_ssl=YES force_local_logins_ssl=YES require_ssl_reuse=NO ssl_ciphers=HIGH
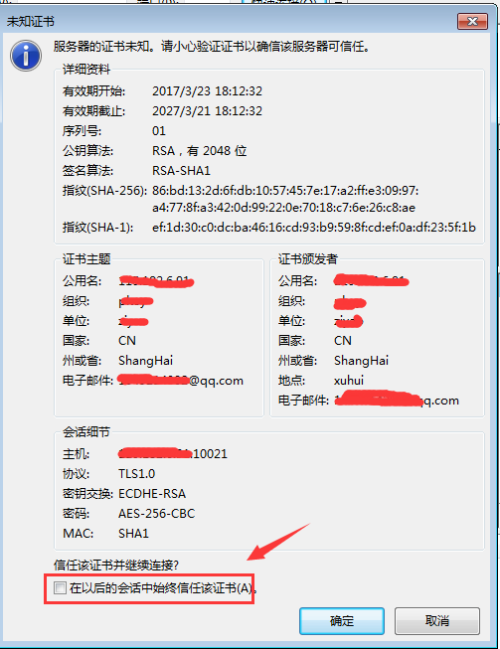
#重启vsftpd,看上去没有什么变化,连接访问时如下:
这时候客户端和ftp之间的连接通讯和数据传输都是ssl加密连接传输。可以通过抓包工具验证!
防火墙的配置见上往篇中的配置.
转载于:https://blog.51cto.com/dyc2005/1940990





















 5339
5339











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








