集中星型 ×××
如果创建两个在安全设备处终止的 ××× 通道,则可设置一对路由,这样,安全设
备就能引导流量离开一个通道,到达另一通道。如果两个通道都包含在一个单独区
段内,则无需创建允许流量从一个通道到达另一通道的策略。只需定义路由。这种
布置就是通常所说的集中星型 ×××。
也可在一个区段内配置多个 ×××,并在任意两个通道之间发送流量
备就能引导流量离开一个通道,到达另一通道。如果两个通道都包含在一个单独区
段内,则无需创建允许流量从一个通道到达另一通道的策略。只需定义路由。这种
布置就是通常所说的集中星型 ×××。
也可在一个区段内配置多个 ×××,并在任意两个通道之间发送流量
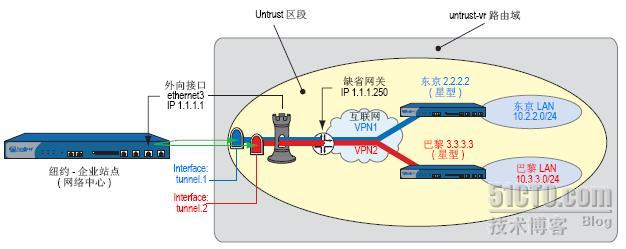
在本例中,东京和巴黎的两个办事处之间通过一对 ××× 通道 ×××1 和 ×××2 进行通信。每个通道都起始于远程站点,终止于纽约的企业站点。位于企业站点的安全设备引导流量离开一个通道,而进入另一通道。
在通道间引导流量时,由于两个远程端点都在同一区段 (Untrust 区段) 中,因此,通过禁用内部区段阻塞,位于企业站点的安全设备只需进行路由查找,而不必进行策略查找。
注意: 也可选择启用内部区段阻塞,并定义内部区段策略,允许两个通道接口间的流量。
在通道间引导流量时,由于两个远程端点都在同一区段 (Untrust 区段) 中,因此,通过禁用内部区段阻塞,位于企业站点的安全设备只需进行路由查找,而不必进行策略查找。
注意: 也可选择启用内部区段阻塞,并定义内部区段策略,允许两个通道接口间的流量。
将通道绑定到通道接口 tunnel.1 和 tunnel.2,二者均无编号。这两个通道使用“自动密钥 IKE”,并带有预共享密钥。选择与阶段 1 和阶段 2 提议都“Compatible”的预定义安全级别。将 Untrust 区段绑定到 untrust-vr。Untrust 区段接口为ethernet3。
注意: 以下配置针对基于路由的 ×××。如果配置基于策略的集中星型 ×××,必须在策略中使用 Trust 和 Untrust 区段;不能使用用户定义的安全区段。
注意: 以下配置针对基于路由的 ×××。如果配置基于策略的集中星型 ×××,必须在策略中使用 Trust 和 Untrust 区段;不能使用用户定义的安全区段。
图:
WebUI ( 纽约)
1. 安全区段和虚拟路由器
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
IP Address/Netmask: 0.0.0.0/0
Manage IP: 0.0.0.0
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
Zone Name: Null
Network > Zones > Edit ( 对于 Untrust): 输入以下内容,然后单击 OK:
Virtual Router Name: untrust-vr
Block Intra-Zone Traffic: ( 清除)
IP Address/Netmask: 0.0.0.0/0
Manage IP: 0.0.0.0
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
Zone Name: Null
Network > Zones > Edit ( 对于 Untrust): 输入以下内容,然后单击 OK:
Virtual Router Name: untrust-vr
Block Intra-Zone Traffic: ( 清除)
2. 接口
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
Zone Name: Untrust
Static IP: ( 出现时选择此选项)
IP Address/Netmask: 1.1.1.1/24
Network > Interfaces > New Tunnel IF: 输入以下内容,然后单击 OK:
Tunnel Interface Name: tunnel.1
Zone (VR): Untrust (untrust-vr)
Unnumbered: ( 选择)
Interface: ethernet3 (untrust-vr)
Network > Interfaces > New Tunnel IF: 输入以下内容,然后单击 OK:
Tunnel Interface Name: tunnel.2
Zone (VR): Untrust (untrust-vr)
Unnumbered: ( 选择)
Interface: ethernet3 (untrust-vr)
3. 东京办事处的 ×××
×××s > AutoKey IKE > New: 输入以下内容,然后单击 OK:
××× Name: ×××1
Security Level: Compatible
Remote Gateway: Create a Simple Gateway: ( 选择)
Gateway Name: Tokyo
Type: Static IP: ( 选择), Address/Hostname: 2.2.2.2
Preshared Key: netscreen1
Security Level: Compatible
Outgoing Interface: ethernet3
> Advanced: 输入以下高级设置,然后单击 Return,返回基本 AutoKey
IKE 配置页:
Proxy-ID: ( 选择)
Local IP/Netmask: 0.0.0.0/0
Remote IP/Netmask: 0.0.0.0/0
Service: ANY
×××s > AutoKey IKE > New: 输入以下内容,然后单击 OK:
××× Name: ×××1
Security Level: Compatible
Remote Gateway: Create a Simple Gateway: ( 选择)
Gateway Name: Tokyo
Type: Static IP: ( 选择), Address/Hostname: 2.2.2.2
Preshared Key: netscreen1
Security Level: Compatible
Outgoing Interface: ethernet3
> Advanced: 输入以下高级设置,然后单击 Return,返回基本 AutoKey
IKE 配置页:
Proxy-ID: ( 选择)
Local IP/Netmask: 0.0.0.0/0
Remote IP/Netmask: 0.0.0.0/0
Service: ANY
4. 巴黎办事处的 ×××
×××s > AutoKey IKE > New: 输入以下内容,然后单击 OK:
××× Name: ×××2
Security Level: Compatible
Remote Gateway: Create a Simple Gateway: ( 选择)
Gateway Name: Paris
Type: Static IP: ( 选择), Address/Hostname: 3.3.3.3
Preshared Key: netscreen2
Security Level: Compatible
Outgoing Interface: ethernet3
> Advanced: 输入以下高级设置,然后单击 Return,返回基本 AutoKey
IKE 配置页:
Proxy-ID: ( 选择)
Local IP/Netmask: 0.0.0.0/0
Remote IP/Netmask: 0.0.0.0/0
Service: ANY
5. 路由
Network > Routing > Routing Entries > untrust-vr New: 输入以下内容,然后
单击 OK:
Network Address / Netmask: 10.2.2.0/24
Gateway: ( 选择)
Interface: tunnel.1
Gateway IP Address: 0.0.0.0
Network > Routing > Routing Entries > untrust-vr New: 输入以下内容,然后
单击 OK:
Network Address / Netmask: 10.3.3.0/24
Gateway: ( 选择)
Interface: tunnel.2
Gateway IP Address: 0.0.0.0
Network > Routing > Routing Entries > untrust-vr New: 输入以下内容,然后
单击 OK:
Network Address / Netmask: 0.0.0.0/0
Gateway: ( 选择)
Interface: ethernet3
Gateway IP Address: 1.1.1.250
WebUI ( 东京)
1. 安全区段和虚拟路由器
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
IP Address/Netmask: 0.0.0.0/0
Manage IP: 0.0.0.0
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
Zone Name: Null
Network > Zones > Edit ( 对于 Untrust): 输入以下内容,然后单击 OK:
Virtual Router Name: untrust-vr
Block Intra-Zone Traffic: ( 选择)
2. 接口
Network > Interfaces > Edit ( 对于 ethernet1): 输入以下内容,然后单击
Apply:
Zone Name: Trust
Static IP: ( 出现时选择此选项)
IP Address/Netmask: 10.2.2.1/24
选择以下内容,然后单击 OK:
Interface Mode: NAT
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
Zone Name: Untrust
Static IP: ( 出现时选择此选项)
IP Address/Netmask: 2.2.2.2/24
Network > Interfaces > New Tunnel IF: 输入以下内容,然后单击 OK:
Tunnel Interface Name: tunnel.1
Zone (VR): Untrust (untrust-vr)
Unnumbered: ( 选择)
Interface: ethernet3 (untrust-vr)
3. 地址
Objects > Addresses > List > New: 输入以下内容,然后单击 OK:
Address Name: Paris
IP Address/Domain Name:
IP/Netmask: ( 选择), 10.3.3.0/24
Zone: Untrust
4. ×××
×××s > AutoKey IKE > New: 输入以下内容,然后单击 OK:
××× Name: ×××1
Security Level: Compatible
Remote Gateway: Create a Simple Gateway: ( 选择)
Gateway Name: New York
Type: Static IP: ( 选择), Address/Hostname: 1.1.1.1
Preshared Key: netscreen1
Security Level: Compatible
Outgoing Interface: ethernet3
> Advanced: 输入以下高级设置,然后单击 Return,返回基本 AutoKey
IKE 配置页:
Proxy-ID: ( 选择)
Local IP/Netmask: 0.0.0.0/0
Remote IP/Netmask: 0.0.0.0/0
Service: ANY
×××s > AutoKey IKE > New: 输入以下内容,然后单击 OK:
××× Name: ×××1
Security Level: Compatible
Remote Gateway: Create a Simple Gateway: ( 选择)
Gateway Name: New York
Type: Static IP: ( 选择), Address/Hostname: 1.1.1.1
Preshared Key: netscreen1
Security Level: Compatible
Outgoing Interface: ethernet3
> Advanced: 输入以下高级设置,然后单击 Return,返回基本 AutoKey
IKE 配置页:
Proxy-ID: ( 选择)
Local IP/Netmask: 0.0.0.0/0
Remote IP/Netmask: 0.0.0.0/0
Service: ANY
5. 路由
Network > Routing > Routing Entries > trust-vr New: 输入以下内容,然后单
击 OK:
Network Address / Netmask: 0.0.0.0/0
Next Hop Virtual Router Name: ( 选择); untrust-vr
Network > Routing > Routing Entries > untrust-vr New: 输入以下内容,然后
单击 OK:
Network Address / Netmask: 0.0.0.0/0
Gateway: ( 选择)
Interface: ethernet3
Gateway IP Address: 2.2.2.250
Network > Routing > Routing Entries > untrust-vr New: 输入以下内容,然后
单击 OK:
Network Address / Netmask: 10.3.3.0/24
Gateway: ( 选择)
Interface: tunnel.1
Gateway IP Address: 0.0.0.0
6. 策略
Policies > (From: Trust, To: Untrust) New: 输入以下内容,然后单击 OK:
Source Address:
Address Book Entry: ( 选择), Any
Destination Address:
Address Book Entry: ( 选择), Paris
Service: ANY
Action: Permit
WebUI ( 巴黎)
1. 安全区段和虚拟路由器
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
IP Address/Netmask: 0.0.0.0/0
Manage IP: 0.0.0.0
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
Zone Name: Null
Network > Zones > Edit ( 对于 Untrust): 输入以下内容,然后单击 OK:
Virtual Router Name: untrust-vr
Block Intra-Zone Traffic: ( 选择)
2. 接口
Network > Interfaces > Edit ( 对于 ethernet1): 输入以下内容,然后单击
Apply:
Zone Name: Trust
Static IP: ( 出现时选择此选项)
IP Address/Netmask: 10.3.3.1/24
选择以下内容,然后单击 OK:
Interface Mode: NAT
Network > Interfaces > Edit ( 对于 ethernet3): 输入以下内容,然后单击 OK:
Zone Name: Untrust
Static IP: ( 出现时选择此选项)
IP Address/Netmask: 3.3.3.3/24
Network > Interfaces > New Tunnel IF: 输入以下内容,然后单击 OK:
Tunnel Interface Name: tunnel.1
Zone (VR): Untrust (untrust-vr)
Unnumbered: ( 选择)
Interface: ethernet3 (untrust-vr)
3. 地址
Objects > Addresses > List > New: 输入以下内容,然后单击 OK:
Address Name: Tokyo
IP Address/Domain Name:
IP/Netmask: ( 选择), 10.2.2.0/24
Zone: Untrust
4. ×××
×××s > AutoKey IKE > New: 输入以下内容,然后单击 OK:
××× Name: ×××2
Security Level: Compatible
Remote Gateway: Create a Simple Gateway: ( 选择)
Gateway Name: New York
Type: Static IP: ( 选择), Address/Hostname: 1.1.1.1
Preshared Key: netscreen2
Security Level: Compatible
Outgoing Interface: ethernet3
> Advanced: 输入以下高级设置,然后单击 Return,返回基本 AutoKey
IKE 配置页:
Proxy-ID: ( 选择)
Local IP/Netmask: 0.0.0.0/0
Remote IP/Netmask: 0.0.0.0/0
Service: ANY
5. 路由
Network > Routing > Routing Entries > trust-vr New: 输入以下内容,然后单
击 OK:
Network Address / Netmask: 0.0.0.0/0
Next Hop Virtual Router Name: ( 选择); untrust-vr
Network > Routing > Routing Entries > untrust-vr New: 输入以下内容,然后
单击 OK:
Network Address / Netmask: 0.0.0.0/0
Gateway: ( 选择)
Interface: ethernet3
Gateway IP Address: 3.3.3.250
Network > Routing > Routing Entries > untrust-vr New: 输入以下内容,然后
单击 OK:
Network Address / Netmask: 10.2.2.0/24
Gateway: ( 选择)
Interface: tunnel.1
Gateway IP Address: 0.0.0.0
6. 策略
Policies > (From: Trust, To: Untrust) New: 输入以下内容,然后单击 OK:
Source Address:
Address Book Entry: ( 选择), Any
Destination Address:
Address Book Entry: ( 选择), Tokyo
Service: ANY
Action: Permit
---------------------------------------------------------------------
以下为命令行下:
CLI ( 纽约)
1. 安全区段和虚拟路由器
unset interface ethernet3 ip
unset interface ethernet3 zone
set zone untrust vrouter untrust-vr
unset zone untrust block
2. 接口
set interface ethernet3 zone untrust
set interface ethernet3 ip 1.1.1.1/24
set interface tunnel.1 zone untrust
set interface tunnel.1 ip unnumbered interface ethernet3
set interface tunnel.2 zone untrust
set interface tunnel.2 ip unnumbered interface ethernet3
3. 东京办事处的 ×××
set ike gateway Tokyo address 2.2.2.2 outgoing-interface ethernet3 preshare
netscreen1 sec-level compatible
set *** ×××1 gateway Tokyo sec-level compatible
set *** ×××1 bind interface tunnel.1
set *** ×××1 proxy-id local-ip 0.0.0.0/0 remote-ip 0.0.0.0/0 any
4. 巴黎办事处的 ×××
set ike gateway Paris address 3.3.3.3 outgoing-interface ethernet3 preshare
netscreen2 sec-level compatible
set *** ×××2 gateway Paris sec-level compatible
set *** ×××2 bind interface tunnel.2
set *** ×××2 proxy-id local-ip 0.0.0.0/0 remote-ip 0.0.0.0/0 any
5. 路由
set vrouter untrust-vr route 10.2.2.0/24 interface tunnel.1
set vrouter untrust-vr route 10.3.3.0/24 interface tunnel.2
set vrouter untrust-vr route 0.0.0.0/0 interface ethernet3 gateway 1.1.1.250
save
1. 安全区段和虚拟路由器
unset interface ethernet3 ip
unset interface ethernet3 zone
set zone untrust vrouter untrust-vr
unset zone untrust block
2. 接口
set interface ethernet3 zone untrust
set interface ethernet3 ip 1.1.1.1/24
set interface tunnel.1 zone untrust
set interface tunnel.1 ip unnumbered interface ethernet3
set interface tunnel.2 zone untrust
set interface tunnel.2 ip unnumbered interface ethernet3
3. 东京办事处的 ×××
set ike gateway Tokyo address 2.2.2.2 outgoing-interface ethernet3 preshare
netscreen1 sec-level compatible
set *** ×××1 gateway Tokyo sec-level compatible
set *** ×××1 bind interface tunnel.1
set *** ×××1 proxy-id local-ip 0.0.0.0/0 remote-ip 0.0.0.0/0 any
4. 巴黎办事处的 ×××
set ike gateway Paris address 3.3.3.3 outgoing-interface ethernet3 preshare
netscreen2 sec-level compatible
set *** ×××2 gateway Paris sec-level compatible
set *** ×××2 bind interface tunnel.2
set *** ×××2 proxy-id local-ip 0.0.0.0/0 remote-ip 0.0.0.0/0 any
5. 路由
set vrouter untrust-vr route 10.2.2.0/24 interface tunnel.1
set vrouter untrust-vr route 10.3.3.0/24 interface tunnel.2
set vrouter untrust-vr route 0.0.0.0/0 interface ethernet3 gateway 1.1.1.250
save
CLI ( 东京)
1. 安全区段和虚拟路由器
unset interface ethernet3 ip
unset interface ethernet3 zone
set zone untrust vrouter untrust-vr
2. 接口
set interface ethernet1 zone trust
set interface ethernet1 ip 10.2.2.1/24
set interface ethernet1 nat
set interface ethernet3 zone untrust
set interface ethernet3 ip 2.2.2.2/24
set interface tunnel.1 zone untrust
set interface tunnel.1 ip unnumbered interface ethernet3
3. 地址
set address untrust Paris 10.3.3.0/24
4. ×××
set ike gateway "New York" address 1.1.1.1 outgoing-interface ethernet3 preshare
netscreen1 sec-level compatible
set *** ×××1 gateway "New York" sec-level compatible
set *** ×××1 bind interface tunnel.1
set *** ×××1 proxy-id local-ip 0.0.0.0/0 remote-ip 0.0.0.0/0 any
5. 路由
set vrouter trust-vr route 0.0.0.0/0 vrouter untrust-vr
set vrouter untrust-vr route 0.0.0.0/0 interface ethernet3 gateway 2.2.2.250
set vrouter untrust-vr route 10.3.3.0/24 interface tunnel.1
6. 策略
set policy from trust to untrust any Paris any permit
set policy from untrust to trust Paris any any permit
save
CLI ( 巴黎)
1. 安全区段和虚拟路由器
unset interface ethernet3 ip
unset interface ethernet3 zone
set zone untrust vrouter untrust-vr
2. 接口
set interface ethernet1 zone trust
set interface ethernet1 ip 10.3.3.1/24
set interface ethernet1 nat
set interface ethernet3 zone untrust
set interface ethernet3 ip 3.3.3.3/24
set interface tunnel.1 zone untrust
set interface tunnel.1 ip unnumbered interface ethernet3
3. 地址
set address untrust Tokyo 10.2.2.0/24
4. ×××
set ike gateway "New York" address 1.1.1.1 outgoing-interface ethernet3 preshare
netscreen2 sec-level compatible
set *** ×××2 gateway "New York" sec-level compatible
set *** ×××2 bind interface tunnel.1
set *** ×××2 proxy-id local-ip 0.0.0.0/0 remote-ip 0.0.0.0/0 any
5. 路由
set vrouter trust-vr route 0.0.0.0/0 vrouter untrust-vr
set vrouter untrust-vr route 0.0.0.0/0 interface ethernet3 gateway 3.3.3.250
set vrouter untrust-vr route 10.2.2.0/24 interface tunnel.1
6. 策略
set policy from trust to untrust any Tokyo any permit
set policy from untrust to trust Tokyo any any permit
save
转载于:https://blog.51cto.com/dlnat/141511




















 161
161











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








