Linux服务器使用WebShellKiller后门自动化查杀教程
世界和平 • 2019 年 11 月 22 日
Loading...
## 前言
如果服务器出现文件上传漏洞和命令执行类漏洞(包括命令注入、缓冲区溢出、反序列化等)都会让人担心,系统是否系统已被上传webshell甚至植入木马程序。
依靠人工排查,一是工作量大二是需要一定程度的技术知识和业务知识才能判断什么是正常什么是异常。
工作量大决定排查工作不可能由个别具有技术知识和业务知识的人来完成工作而需要其他人员参与,而如果这些没有“一定程度的技术知识和业务知识”的人员参与基本必然后导致大量的误报和漏报(主要是漏报)。
总而言之,在大量设备场景中人工排查后门是很难切实有效推行的排查手段。
所谓服务器后门,其本质其与桌面系统的病毒、木马并没有很大区别。
在桌面系统中我们可以轻松使用360点击查杀完成病毒木马的查杀,在服务器我们也可以使用类似工具完成后门的查杀。
至于漏报误报必然还是有的但会比人工排查少,至于效率则会高得多。
## WebShellKiller简介
WebShellKiller是深信服发布的一款webshell查杀工具,支持jsp、asp、aspx、php等脚本的检查。
[下载及更详细说明][1]
由于不是商用产品也不是开源产品,所以不能保证其后续是否持续维护更新,但基于以下两点就算不再更新该产品还是比较可靠的。
首先,从当前效果看使用[webshell][2]进行测试绝大部分都是能正确判断。
其次,身为webshell注定其最终必定要生成代码调用那些固定的危险函数,所以webshell的变形是有限制的,也就是所谓的“免杀”其实有比较高的门槛。
WebShellKiller支持windows和linux,我们这里只讲linux,windows直接解压双击运行没有什么操作性就不多讲了。
另外windows平台的webshell查杀还可以使用[d盾WebShellKill][3]
在线查杀可使用[百度webdir+][4]
## WebShellKiller安装使用
```````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````bash
# 下载WebShellKiller
wget http://edr.sangfor.com.cn/tool/WebShellKillerForLinux.tar.gz
# 解压到当前目录
tar -zxf WebShellKillerForLinux.tar.gz
# 查看解压结果,可以看到多出centos_32、centos_64、linux_64三个文件夹
# 如果是centos 32/redhat 32那就使用centos_32,如果是centos 64/redhat 64那就使用centos_64,如果是其他linux 64那就使用linux_64
ls
# 查看当前操作系统
cat /etc/system-release
# 查看当前操作系统是32位还是64位;x86是32位,x86_64或x64是64位;一般都是64位
uname -m
# 我这里是centos 64所以进入centos_64
cd centos_64/wscan_app/
# 查看当前目录文件,wscan是主程序
ls
# wscan默认没有可执行权限,需要加上
chmod u+x wscan
# wscan从LD_LIBRARY_PATH加载so文件,需要将当前路径加到LD_LIBRARY_PATH以使wscan能找到当前目录下的so
export LD_LIBRARY_PATH=`pwd`:$LD_LIBRARY_PATH
# 执行扫描,/www/wwwroot/app_805ds_com是我这里要扫描的路径,改成自己要扫描的即可
# 被列出的文件即是被认为可疑的文件,人工识别是否为web应用自己所用文件即可
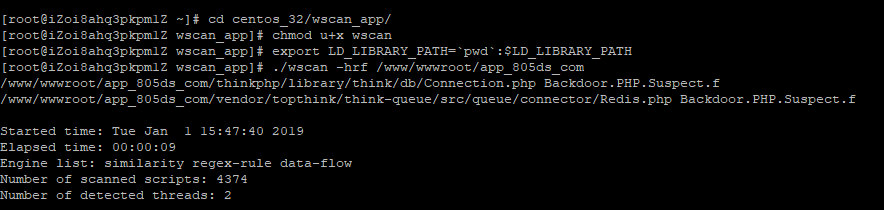
./wscan -hrf /www/wwwroot/app_805ds_com
```````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````
## 操作截图
[1]: https://www.blogbig.cn/go/TGaQoHjm/
[2]: https://www.blogbig.cn/go/X4vuR8Kh/
[3]: https://www.blogbig.cn/go/8fiPa9o0/
[4]: https://www.blogbig.cn/go/tevWg2EM/
[5]: https://image.blogbig.cn/2019/11/23/1574509578.jpg





















 496
496

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








