月初的安卓开发者峰会上,谷歌已经宣布,将于明年3月份发布Android Q操作系统的第一个开发者预览版。同时还将要大力提升新系统的升级速度,力求让更多的用户和开发者能够参与到安卓Q的尝鲜与内测当中。

作为新一代的操作系统,其将会有什么变化呢?最近,有消息人士称,新版的安卓Q将会新增一个智能拨号的功能,根据用户所拨区域的号码。自动添加区号。此外,还有一个多窗口显示功能,这个功能相当于Windows的多任务模式。
至于首批开放尝鲜的手机,自然要数谷歌的亲儿子pixel系列,而且一些支持Project Treble的手机也将会在第一时间尝鲜。
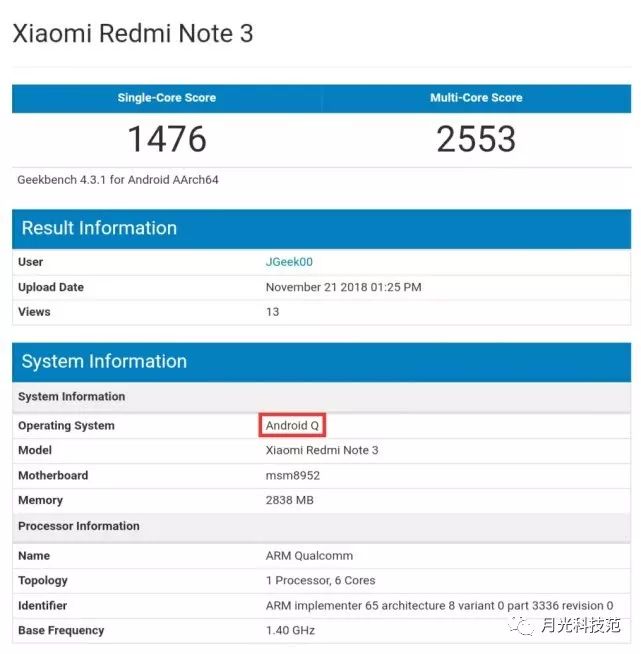
令人意外的是,最近在GeekBench跑分数据库现身了红米NOTE 3的身影,这款手机是三年前发布的,并不说这款手机在硬件上有了什么改动,而是其搭载了最新的安卓 Q系统。目前小米官方已经对这款手机停止更新,所以这款系统或许是第三方开发者适配的。

红米NOTE 3在发布的时候预装安卓6.0系统,现在能够经历四个大版本的迭代,也算是一代神机了。你手里的红米NOTE 3已经丢掉了吗?























 2850
2850

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








