客户需求:实现公交站台无线覆盖,并有安全性认证,认证页面可以定制。并且支持审计,流控,日志记录等。
技术方案:短信认证+IMC平台管理
设备型号:H3C LA3616
拓扑如下:

图中AP为H3C LA3616,认证平台在省网bars。AP放在公交站台,29.0.0.0为终端ip地址,ap与172.25.140.250三层互联。
配置log:
<H3C>dis cu
#
version 7.1.064, Release 0615P15
#
sysname H3C
#
telnet server enable
#
dialer-group 1 rule ip permit
#
dhcp enable
#
dns server 113.215.2.222
dns server 113.214.230.25
#
mirroring-group 1 local
#
password-recovery enable
#
vlan 1
#
vlan 2
#
vlan 100
#
dhcp server ip-pool 1
gateway-list 29.94.129.254
network 29.94.129.0 mask 255.255.255.0
dns-list 113.214.230.25 113.215.2.222
#
apn-profile Cellular1/0
apn static public.vpdn.zj
authentication-mode pap user 182107@zjphhsgdwlyxgs.vpdn.zj password cipher $c$3$OYSiBhtRSR26NBUIhgOKRb5J/qjjsGnXTL5J
#
wlan service-template 1
ssid ijiaxing
vlan 100
portal enable method direct
portal domain shengwang
portal bas-ip 29.94.129.254
portal apply web-server shengwang-FZ2
portal apply mac-trigger-server ip
portal user-dhcp-only
portal nas-port-type wireless
service-template enable
#
controller Cellular1/0
eth-channel 0
#
controller Cellular2/0
eth-channel 0
#
interface NULL0
#
interface Vlan-interface1
#
interface Vlan-interface100
ip address 29.94.129.254 255.255.255.0
mirroring-group 1 mirroring-port both
dhcp server apply ip-pool 1
#
interface GigabitEthernet0/0
port link-mode route
#
interface GigabitEthernet0/1
port link-mode route
mirroring-group 1 monitor-port
#
interface WLAN-Radio0/0
service-template 1
#
interface WLAN-Radio0/1
service-template 1
#
interface Eth-channel1/0:0
dialer circular enable
dialer-group 1
dialer timer idle 0
dialer timer autodial 5
dialer number #777 autodial
ip address cellular-alloc
tcp mss 1310
mirroring-group 1 mirroring-port both
apn-profile apply Cellular1/0
#
interface Eth-channel2/0:0
tcp mss 1024
#
scheduler logfile size 16
#
line class console
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line con 0
user-role network-admin
#
line vty 0 4
authentication-mode scheme
user-role network-operator
#
line vty 5 63
user-role network-operator
#
ip route-static 0.0.0.0 0 Eth-channel1/0:0
#
undo info-center enable
#
radius session-control enable
#
radius scheme shengwang
primary authentication 30.254.8.227
primary accounting 30.254.8.227
key authentication cipher $c$3$JsTIwhcoDAnu5/EhcEUXulL4CUtYUAVFWTZL1i8=
key accounting cipher $c$3$Uio2eWJhztO0WjgFSIeSQZvbmY44Ow7WIB/HecE=
user-name-format without-domain
nas-ip 29.94.129.254
#
domain shengwang
authentication portal radius-scheme shengwang
authorization portal radius-scheme shengwang
accounting portal radius-scheme shengwang
#
domain system
#
domain default enable shengwang
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$udKW/IdOAGGI4ESG$/cZqFbUF7D3hX+O9ZgIptp9uxIstk9paxrNWn3w+pGv88n8yJG2X+EBFQRpcAiSmfwnvitdmh13SfzQgb5Vb6A==
service-type ssh telnet terminal http https
authorization-attribute user-role level-15
authorization-attribute user-role network-operator
#
portal nas-port-id format 4
portal host-check enable
portal device-id H3C
portal free-rule 2 source ip any destination ip 113.215.2.222 255.255.255.255
portal free-rule 3 source ip any destination ip 30.254.8.226 255.255.255.255
portal free-rule 4 source ip any destination ip 30.254.183.56 255.255.255.255
portal free-rule 5 source ip any destination ip 30.254.183.60 255.255.255.255
portal free-rule 6 source ip any destination ip 30.254.180.136 255.255.255.255
portal free-rule 8 source ip any destination ip 218.108.168.165 255.255.255.255
portal free-rule 9 source ip any destination ip 122.97.253.215 255.255.255.255
portal free-rule 10 source ip any destination ip 101.201.169.72 255.255.255.255
portal free-rule 11 destination AdMaster,AI驱动的社交和洞察解决方案提供商
portal free-rule 12 destination hm.baidu.com
portal free-rule 13 destination res.wiplatform.com
portal free-rule 14 destination jf.wiplatform.com
portal free-rule 15 destination 7xiyfb.com0.z0.glb.qiniucdn.com
portal free-rule 16 destination portal.e-wifi.com
portal free-rule 17 source ip any destination ip 29.94.129.254 255.255.255.255
portal free-rule 18 source ip any destination ip 30.254.8.227 255.255.255.255
portal free-rule 19 source ip any destination ip 30.254.180.194 255.255.255.255
portal free-rule 20 source ip any destination ip 30.254.180.191 255.255.255.255
portal free-rule 21 source ip any destination ip 113.214.230.25 255.255.255.255
portal free-rule 30 destination 微信网页版
#
portal web-server shengwang-FZ2
url http://30.254.8.226:8080/authentication/portal/login
server-type cmcc
captive-bypass ios optimize enable
url-parameter acip value 29.94.129.254
url-parameter apmac ap-mac
url-parameter oldurl original-url
url-parameter ssid ssid
url-parameter userip source-address
url-parameter usermac source-mac
url-parameter vlan value 100
#
portal server shengwang-FZ
ip 30.254.180.194 key cipher $c$3$EuELH4cTpe7aSR+li5r4eiZDnbX9H3O3ST2ASA==
port 2000
server-type cmcc
#
portal mac-trigger-server ip
ip 30.254.8.227
version 2
server-type cmcc
aaa-fail nobinding enable
#
wlan global-configuration
#
return
配置完之后,认证成功,但是会出现偶尔弹不出认证页面/认证失败现象!
现场抓包,发现AP发送radius请求报文,认证平台一直没有回复
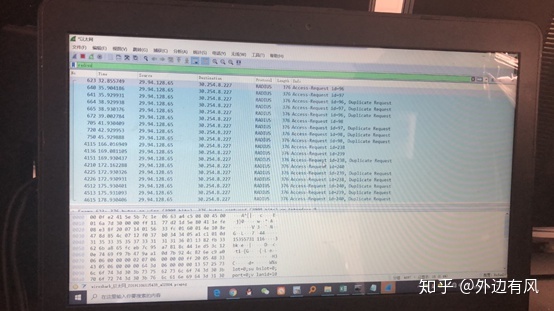
联系平台那边,平台一直不好好配合,一直说平台没问题让我们排查配置问题,由于工期将近,无奈写了一个技术文档,让客户跟省部领导取得联系,并建了一个微信群,将省领导,以及区域领导拉进微信群,由于领导在微信群里,所以平台和省部运维便配合我们做相关的抓包分析。
最终排查出问题: 根据省网ip地址的统一规划,全省各地市acip都需使用30地址段,之前的问题就是因为使用了非规划的29地址导致的。 所以正式业务上线时,acip需要使用省网规划的30地址。
省部对ip进行了限制访问,不是其分配的ip不能访问其radius服务器。
总结:重大项目一定要建通信群,并把领导拉进去,对于一些协调问题,可以让领导想办法协调,并快速定位问题所在。



















 5640
5640











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








