一、Project overview
| item | content | remark |
|---|---|---|
| Authorized penetration range | http://192.168.88.141/ | Local test |
| Source code download | https://www.seacms.net/SeaCMS_V13.1_install_f.zip | Open source project |
| Scope of vulnerability | SeaCMS_V13.1 |
二、Vulnerability description
1、Logic bug - Unlimited top-up members
| category | content | remark |
|---|---|---|
| Vulnerability location(URL) | http://192.168.200.141/member.php?action=hyz&gid=3&mon=1 | |
| Vulnerability type | Logic hole | |
| Vulnerability description | SeaCMS has a logical flaw that could be exploited by an attacker to allow any user to recharge members indefinitely |
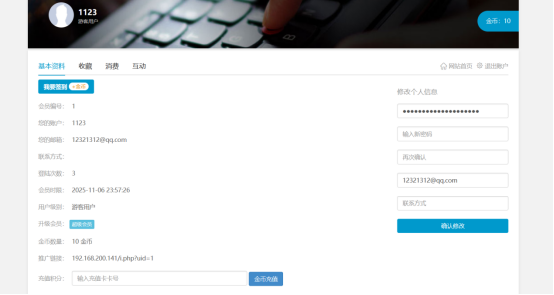
*Visit a center and click on Super Member*
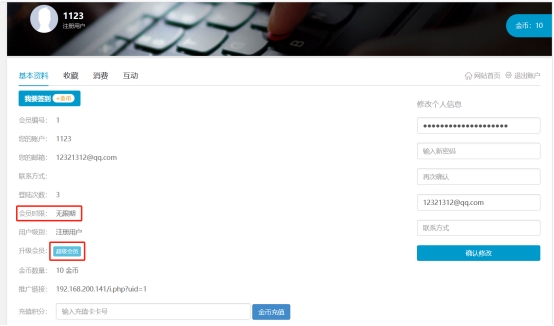
*Click on 100 gold per month and grab the pack*
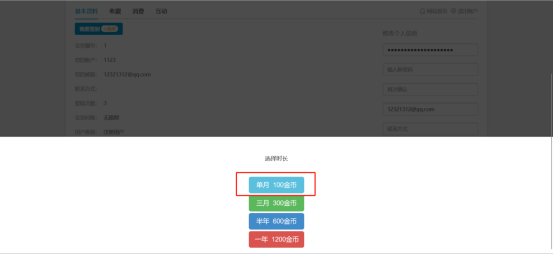
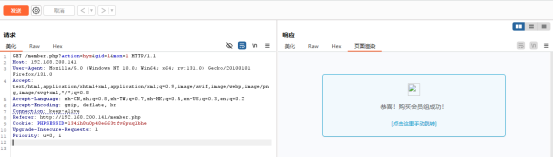
*If the gid parameter is changed to 1, the system returns that the recharge is successful*
*Refresh the Personal Center page, successfully add one month membership time*
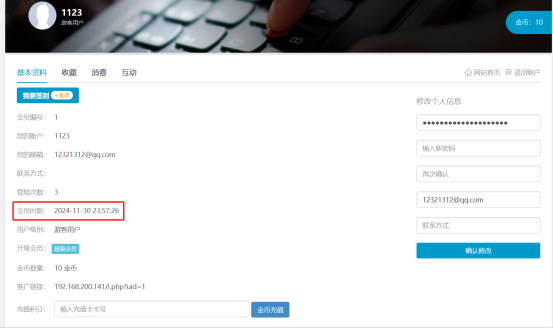
*Multiple packages, refresh the personal center page again, you can see the time lengthened*
 项目无限充值会员逻辑漏洞分析
项目无限充值会员逻辑漏洞分析






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








