DNS服务
DNS基础概念
DNS(Domain Name Service)即域名服务。域名由”主机名+域名组成”,也就是所谓的完全限定域名。举个例子:如:"http://www.baidu.com"是一个域名,从严格意义上讲,"http://baidu.com"才被称为域名(全球唯一),而"www"是主机名。
"主机名.域名"称为完全限定域名(FQDN),一个域名下可以有多个主机,域名全球唯一,那么"主机名.域名"肯定也是全球唯一的。
域名分为根域,顶级域,一级域,二级域等组成,其构造为树状图(如下图所示)。
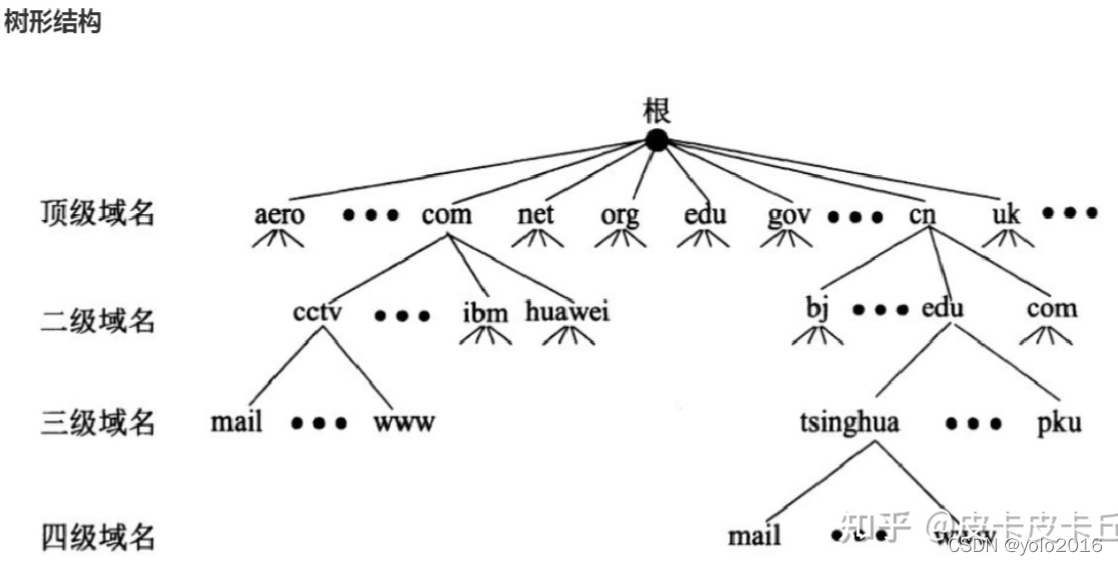
DNS解析过程
当应用过程需要将一个主机域名映射为IP地址时,就调用域名解析函数,解析函数将待转换的域名放在DNS请求中,以UDP报文方式发给本地域名服务器。本地的域名服务器查到域名后,将对应的IP地址放在应答报文中返回。同时域名服务器还必须具有连向其他服务器的信息以支持不能解析时的转发。若域名服务器不能回答该请求,则此域名服务器就暂成为DNS中的另一个客户,向根域名服务器发出请求解析,根域名服务器一定能找到下面的所有二级域名的域名服务器,这样以此类推,一直向下解析,直到查询到所请求的域名。

DNS服务器的端口分别为TCP 53和UPD 53。
DNS的解析种类分为两种,分别是递归查询和迭代查询。
递归查询:客户机与本地DNS服务器之间叫做递归查询。
迭代查询:本地DNS服务器与根等其他DNS服务器的解析过程叫迭代查询(如下图所示)。

DNS常用解析类型
| 类型 | 定义 |
|---|---|
| A 和 AAAA 记录(Adress record) | 正向记录,域名解析到IP。 “A” 记录用于将主机映射到 IPv4 IP 地址,而 “AAAA” 记录用于将主机映射到 IPv6 地址 |
| PTR记录(PoinTer record) | 反向记录,用于定义与IP相关联的名称 |
| CNAME记录(Canonical Name record) | CNAME记录为服务器(由A或AAAA记录定义的名称)定义规范名称的别名 |
| MX记录(Mail exchange record) | MX记录解析是做邮箱解析使用的。记录类型选择MX,线路类型选择通用或者同时添加三条线路类型为电信、网通、教育网的记录;记录值填写邮局商提供的服务器IP地址或别名地址;TTL设置默认的3600即可,MX优先级填写邮局提供商要求的数据,或是默认10,有多条MX记录的时候,优先级要设置不一样的数据。 |
DNS服务器类型
主名称服务器(primary name server)。从域管理员构造的本地磁盘文件中加载域信息,该文件(区域文件)包含着该服务器具有管理权的一部分域结构的最精确信息。主服务器是一种权威性服务器,因为它以绝对的权威去回答对其管辖域的任何查询。
从名称服务器(secondary name server)。它可从主服务器中复制一整套域信息。区域文件是从主服务器中复制出来的,并作为本地磁盘文件存储在辅助服务器中。这种复制称为”区域文件复制”。在辅助域名服务器中有一个所有域信息的完整拷贝,可以有权威地回答对该域的查询。因此,辅助域名服务器也称作权威性服务器。配置辅助域名服务器不需要生成本地区文件,因为可以从主服务器中下载该区文件。
唯高速缓存名称服务器(caching-only server)。可运行域名服务器软件,但是没有域名数据库软件。它从某个远程服务器取得域名服务器查询的结果,一旦取得一个,就将它放在高速缓存中,以后查询相同的信息时就用它予以回答。高速缓存服务器不是权威性服务器,因为它提供的所有信息都是间接信息。当BIND被配置为缓存服务器的时候,它只会回应已缓存的请求,并将所有其他的请求转发到上游的 DNS 服务器。缓存名称服务器只需要.这个zone file文件即可。
DNS服务器搭建(Linux)——Master
安装bind包
//安装bind包
yum -y install bind bind-libs bind-utils
配置/etc/named.conf文件
//配置named.conf文件
/*
Sample named.conf BIND DNS server 'named' configuration file
for the Red Hat BIND distribution.
See the BIND Administrator's Reference Manual (ARM) for details about the
configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
*/
options
{
// Put files that named is allowed to write in the data/ directory:
directory "/var/named"; // "Working" directory
dump-file "data/cache_dump.db";
statistics-file "data/named_stats.txt";
memstatistics-file "data/named_mem_stats.txt";
recursing-file "data/named.recursing";
secroots-file "data/named.secroots";
/*
Specify listenning interfaces. You can use list of addresses (';' is
delimiter) or keywords "any"/"none"
*/
listen-on port 53 { any; };
//listen-on port 53 { 127.0.0.1; };
//listen-on-v6 port 53 { any; };
//listen-on-v6 port 53 { ::1; };
/*
Access restrictions
There are two important options:
allow-query { argument; };
- allow queries for authoritative data
allow-query-cache { argument; };
- allow queries for non-authoritative data (mostly cached data)
You can use address, network address or keywords "any"/"localhost"/"none" as argument
Examples:
allow-query { localhost; 10.0.0.1; 192.168.1.0/8; };
allow-query-cache { ::1; fe80::5c63:a8ff:fe2f:4526; 10.0.0.1; };
*/
allow-query { any; };
allow-query-cache { any; };
/* Enable/disable recursion - recursion yes/no;
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
forwarders {
192.168.3.1;
223.5.5.5;
8.8.8.8; };
/* DNSSEC related options. See information about keys ("Trusted keys", bellow) */
/* Enable serving of DNSSEC related data - enable on both authoritative
and recursive servers DNSSEC aware servers */
dnssec-enable yes;
/* Enable DNSSEC validation on recursive servers */
dnssec-validation yes;
/* In RHEL-7 we use /run/named instead of default /var/run/named
so we have to configure paths properly. */
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
managed-keys-directory "/var/named/dynamic";
};
logging
{
/* If you want to enable debugging, eg. using the 'rndc trace' command,
* named will try to write the 'named.run' file in the $directory (/var/named).
* By default, SELinux policy does not allow named to modify the /var/named directory,
* so put the default debug log file in data/ :
*/
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
/*
Views let a name server answer a DNS query differently depending on who is asking.
By default, if named.conf contains no "view" clauses, all zones are in the
"default" view, which matches all clients.
Views are processed sequentially. The first match is used so the last view should
match "any" - it's fallback and the most restricted view.
If named.conf contains any "view" clause, then all zones MUST be in a view.
*/
zone "." IN {
type hint;
file "named.ca"; // 根DNS服务器的列表
};
include "/etc/named.rfc1912.zones";
#include "/etc/named.root.key";
配置/etc/named.rfc1912.zones文件
[root@sysadmin etc]# cat named.rfc1912.zones
// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "test.com" IN {
type master;
file "test.com.zone";
allow-update { none; };
forwarders { 8.8.8.8; };
};
zone "3.168.192.in-addr.arpa" IN {
type master;
file "192.168.3.zone";
allow-update { none; };
forwarders { 8.8.8.8; };
};
添加A记录(正向解析)
[root@sysadmin named]# cat /var/named/test.com.zone
$TTL 3H
@ IN SOA sysadmin sysadmin (
1 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS ns.test.com.
ns IN A 192.168.3.50
host100 IN A 192.168.3.100
host101 IN A 192.168.3.101
host102 IN A 192.168.3.102
host200 IN A 192.168.3.200
host201 IN A 192.168.3.201
host202 IN A 192.168.3.202
host203 IN A 192.168.3.203
sysadmin IN A 192.168.3.50
添加PTR记录(反向记录)
[root@sysadmin named]# pwd
/var/named
[root@sysadmin named]# cat 192.168.3.zone
$TTL 3H
@ IN SOA sysadmin sysadmin (
1 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS ns.test.com.
100 IN PTR host100.test.com.
50 IN PTR sysadmin.test.com.
重启DNS服务
[root@sysadmin etc]# chkconfig named on
Note: Forwarding request to 'systemctl enable named.service'.
Created symlink from /etc/systemd/system/multi-user.target.wants/named.service to /usr/lib/systemd/system/named.service.
[root@sysadmin etc]#
[root@sysadmin etc]#
[root@sysadmin etc]#
[root@sysadmin etc]#
[root@sysadmin etc]# service named restart
Redirecting to /bin/systemctl restart named.service
从配置——Slave
从服务器/etc/named.conf 配置
[root@host200 slaves]# cat /etc/named.conf
/*
Sample named.conf BIND DNS server 'named' configuration file
for the Red Hat BIND distribution.
See the BIND Administrator's Reference Manual (ARM) for details about the
configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
*/
options
{
// Put files that named is allowed to write in the data/ directory:
directory "/var/named"; // "Working" directory
dump-file "data/cache_dump.db";
statistics-file "data/named_stats.txt";
memstatistics-file "data/named_mem_stats.txt";
recursing-file "data/named.recursing";
secroots-file "data/named.secroots";
/*
Specify listenning interfaces. You can use list of addresses (';' is
delimiter) or keywords "any"/"none"
*/
listen-on port 53 { any; };
//listen-on port 53 { 127.0.0.1; };
//listen-on-v6 port 53 { any; };
//listen-on-v6 port 53 { ::1; };
/*
Access restrictions
There are two important options:
allow-query { argument; };
- allow queries for authoritative data
allow-query-cache { argument; };
- allow queries for non-authoritative data (mostly cached data)
You can use address, network address or keywords "any"/"localhost"/"none" as argument
Examples:
allow-query { localhost; 10.0.0.1; 192.168.1.0/8; };
allow-query-cache { ::1; fe80::5c63:a8ff:fe2f:4526; 10.0.0.1; };
*/
allow-query { any; };
allow-query-cache { any; };
/* Enable/disable recursion - recursion yes/no;
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
forwarders {
192.168.3.1;
223.5.5.5;
8.8.8.8; };
/* DNSSEC related options. See information about keys ("Trusted keys", bellow) */
/* Enable serving of DNSSEC related data - enable on both authoritative
and recursive servers DNSSEC aware servers */
dnssec-enable yes;
/* Enable DNSSEC validation on recursive servers */
dnssec-validation yes;
/* In RHEL-7 we use /run/named instead of default /var/run/named
so we have to configure paths properly. */
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
managed-keys-directory "/var/named/dynamic";
};
logging
{
/* If you want to enable debugging, eg. using the 'rndc trace' command,
* named will try to write the 'named.run' file in the $directory (/var/named).
* By default, SELinux policy does not allow named to modify the /var/named directory,
* so put the default debug log file in data/ :
*/
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
/*
Views let a name server answer a DNS query differently depending on who is asking.
By default, if named.conf contains no "view" clauses, all zones are in the
"default" view, which matches all clients.
Views are processed sequentially. The first match is used so the last view should
match "any" - it's fallback and the most restricted view.
If named.conf contains any "view" clause, then all zones MUST be in a view.
*/
zone "." IN {
type hint;
file "named.ca"; // ??NS?..?ㄧ.?.〃
};
include "/etc/named.rfc1912.zones";
#include "/etc/named.root.key";
从服务器/etc/named.conf 配置
[root@host200 slaves]# cat /etc/named.rfc1912.zones
// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "test.com" IN {
type slave;
file "slaves/test.com.zone";
forwarders { 8.8.8.8; };
masters {192.168.3.50;};
};
zone "3.168.192.in-addr.arpa" IN {
type slave;
file "slaves/192.168.3.zone";
forwarders { 8.8.8.8; };
masters {192.168.3.50;};
};
从服务器信息同步检查

结果验证

转发验证

配置参数解析
seral number 版本号,定义版本号
refresh 刷新时间,定义刷新版本号时间
retry 重试时间,定义刷新版本号没有响应后的重新刷新时间
expire 过期时间,定义规定时间内没有反应说明主机当掉
nagative answer ttl 否定答案的缓存时长
SOA: 起始授权记录, 用于标记一个区域文件的开始
ZONE NAME TTL IN SOA FQDN mail地址 (5种属性值)
FAQ
nslookup:command not found的解决办法
- 配置文件检查命令
named-checkconf /etc/named.conf
named-checkzone test.com /var/named/test.com.zone
named-checkzone 3.168.192.in-addr.arpa /var/named/192.168.3.zone
- 配置文件解析以及模板
See the BIND Administrator’s Reference Manual (ARM) for details about the
configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
参考
内网环境搭建之DNS服务器
DNS记录类型
DNS之BIND使用小结(Forward转发)
详解 linux 下的DNS配置过程及原理参数
Linux系统下DNS主从配置详解






















 453
453

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










