1、What’s this:
1、查壳:
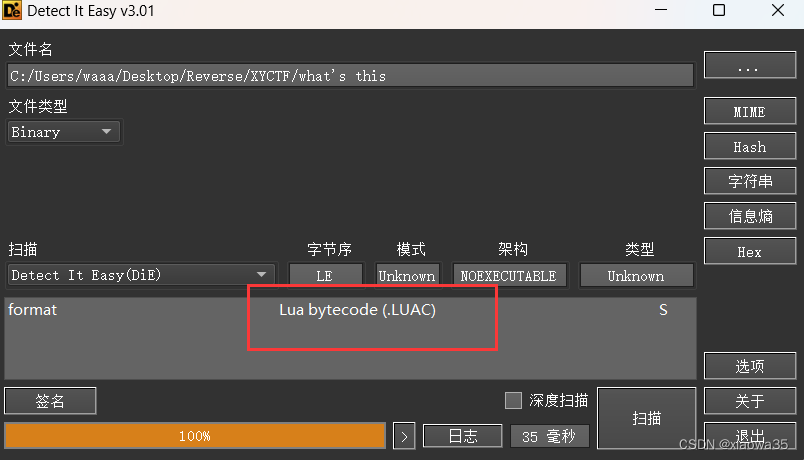
2、反编译:
查壳发现是Lua文件,在网上找一个反编译的
找了很多网站,觉得这个好用
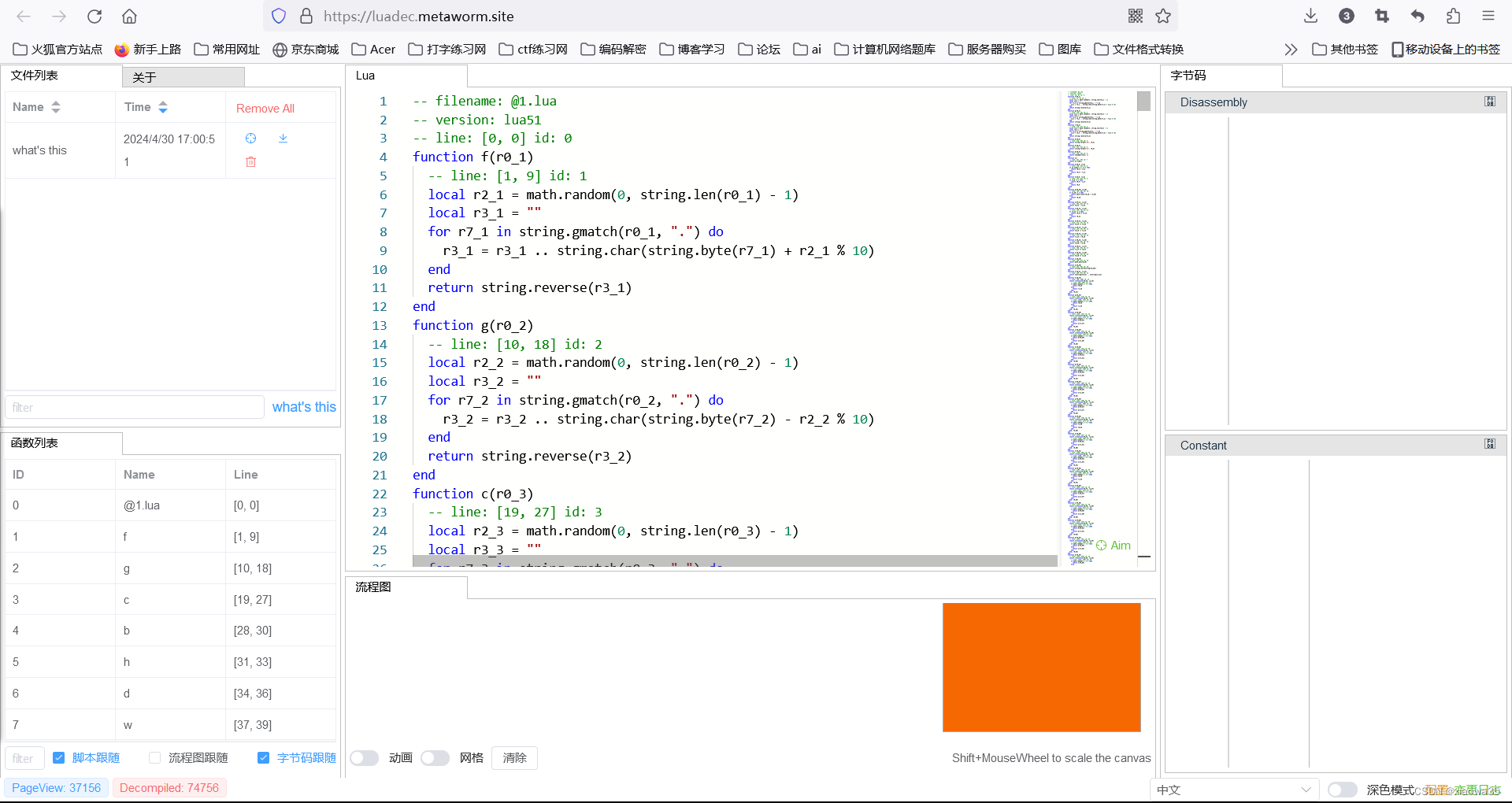
下面是加密的主要部分(主要是在最后一部分):
repeat
value = value .. string.char(Xor(string.byte(flag, i), 8) % 256)
i = i + 1
until string.len(flag) < i
for r3_0 = 1, 1000, 1 do
x = 3
y = x * 3
z = y / 4
w = z - 5
if w == 0 then
print("This line will never be executed")
end
end
for r3_0 = 1, string.len(flag), 1 do
temp = string.byte(value, r3_0)
temp = string.char(temp + 3)
output = output .. temp
end
result = output:rep(10)
invalid_list = {
1,
2,
3
}
for r3_0 = 1, 20, 1 do
table.insert(invalid_list, 4)
end
for r3_0 = 1, 50, 1 do
result = result .. "A"
table.insert(invalid_list, 4)
end
for r3_0 = 1, string.len(output), 1 do
temp = string.byte(output, r3_0)
temp = string.char(temp - 1)
end
for r3_0 = 1, 30, 1 do
result = result .. string.lower(output)
end
for r3_0 = 1, 950, 1 do
x = 3
y = x * 3
z = y / 4
w = z - 5
if w == 0 then
print("This line will never be executed")
end
end
for r3_0 = 1, 50, 1 do
x = -1
y = x * 4
z = y / 2
w = z - 3
if w == 0 then
print("This line will also never be executed")
end
end
require("base64")
obfuscated_output = to_base64(output)
obfuscated_output = string.reverse(obfuscated_output)
obfuscated_output = string.gsub(obfuscated_output, "g", "3")
obfuscated_output = string.gsub(obfuscated_output, "H", "4")
obfuscated_output = string.gsub(obfuscated_output, "W", "6")
invalid_variable = obfuscated_output:rep(5)
if obfuscated_output == "==AeuFEcwxGPuJ0PBNzbC16ctFnPB5DPzI0bwx6bu9GQ2F1XOR1U" then
print("You get the flag.")
else
print("F**k!")
end
加密流程:
首先异或8-----》然后+3-------》base64加密--------》替换字符-------》倒序输出
给一下解密代码:
import base64
enc='==AeuFEcwxGPuJ0PBNzbC16ctFnPB5DPzI0bwx6bu9GQ2F1XOR1U'
data=list(enc[::-1])
for i in range(len(data)):
if data[i]=='3':
data[i]='g'
if data[i]=='4':
data[i]='H'
if data[i]=='6':
data[i]='W'
data=str(data)
ans=base64.b64decode(data)
flag=''
print(ans)
for i in range(len(ans)):
flag+=chr(((ans[i])-3)^8)
print(flag)
此题总结:
初次尝试Lua逆向





















 1446
1446

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








