一.目录
1.IDA
2.babyre
3.babyandoird
4.运动的elf
5.TupEAx
6.ezpy
二.WP
1.IDA
下载好文件,解压缩,例行查壳,没有壳,64bit的
那就直接把文件丢到ida-64里分析,分析结束,
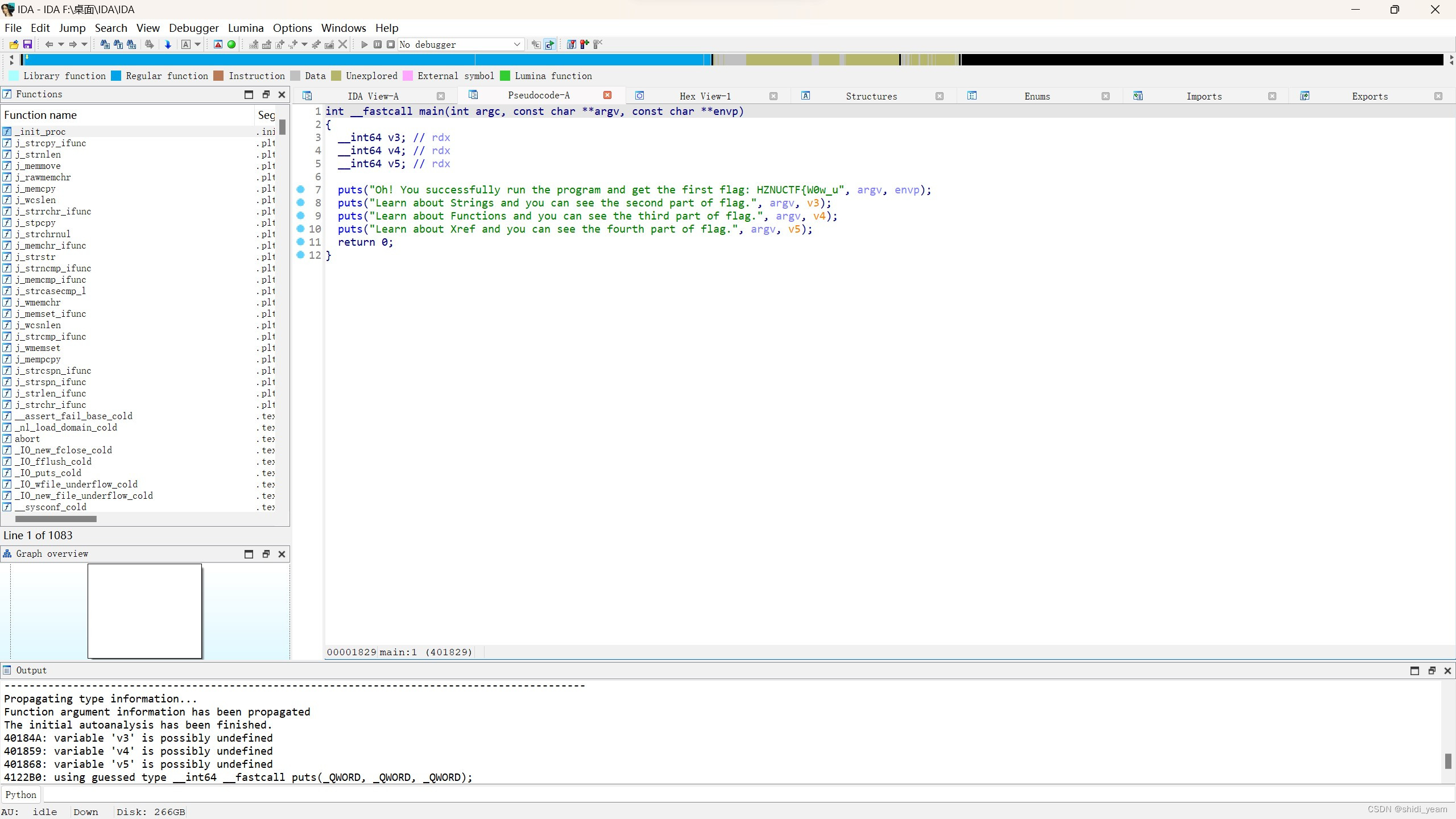
找到main函数,很清晰,第一部分flag就在第一个puts语句中,第二个flag在字符串页面中,shift+F12查看即可,

第三部分,就是让我们在函数窗口找到flag,flag以函数名的形式出现,很明显,就在main函数上方,

然后就是最后一部分了,就是一个交叉引用,CTRL+x,
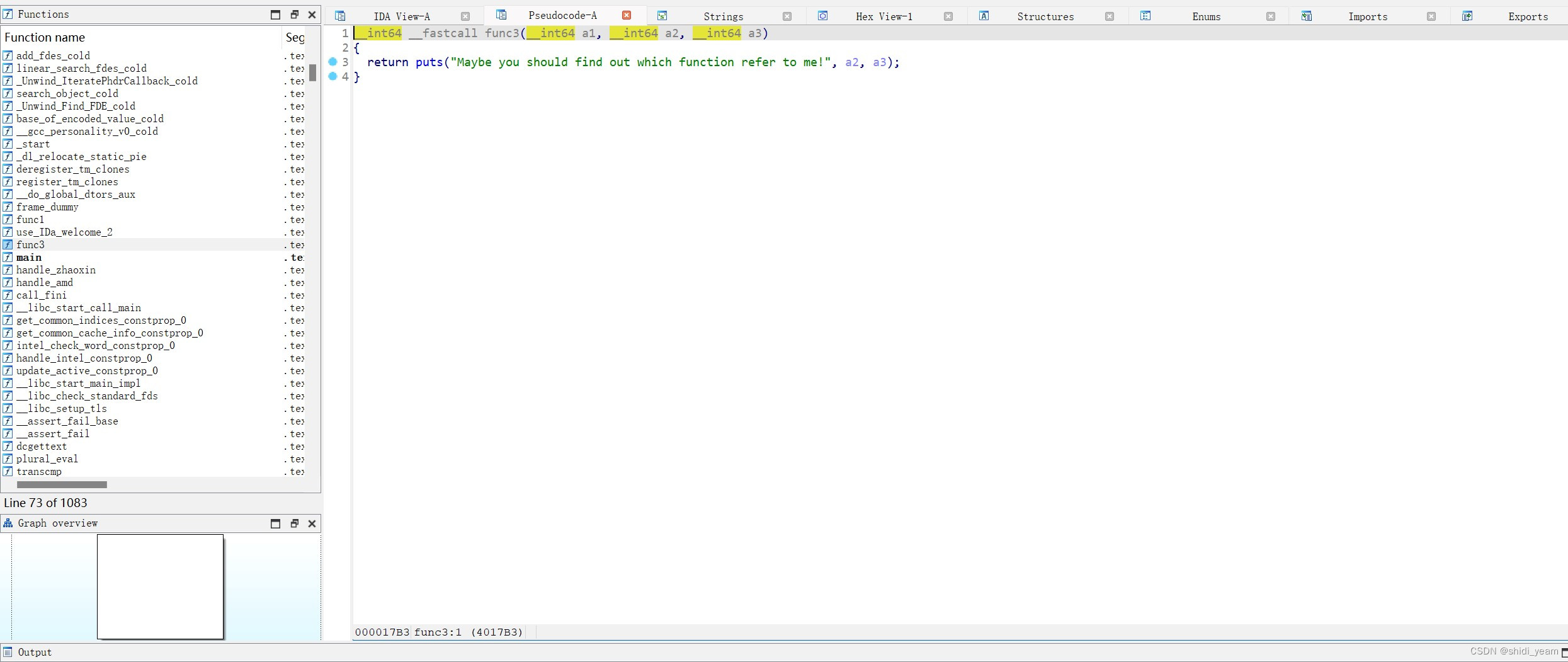
找到func3函数,然后TABLE键,转到汇编页面,
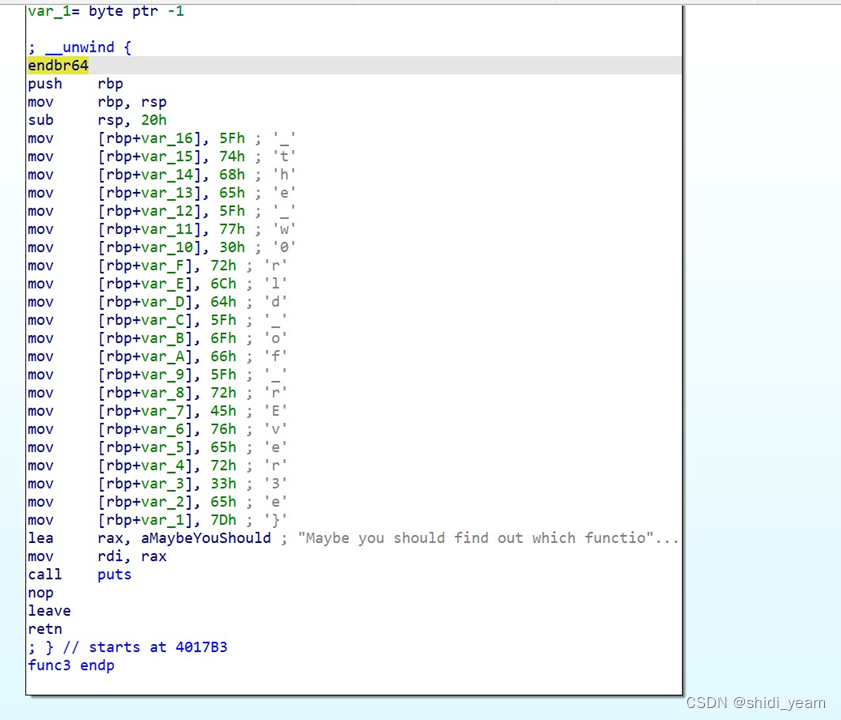
没想到flag就出来了,都还没交叉引用呢,四部分拼在一起就好了
HZNUCTF{W0w_u_h@ve_l34rned_hOw_2_use_IDa_welcome_2_the_w0rld_of_rEver3e}
2.babyre
拿到附件,解压缩,先跑一下,看看回显
ok,查壳,没有壳,32bit的,
直接丢到ida-32分析,
分析结束,直接就是main函数,F5反汇编,跟进main_函数,
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
size_t v3; // eax
char v5; // [esp+0h] [ebp-188h]
char v6; // [esp+0h] [ebp-188h]
int v7; // [esp+Ch] [ebp-17Ch]
int j; // [esp+D4h] [ebp-B4h]
signed int v9; // [esp+E0h] [ebp-A8h]
unsigned __int8 *v10; // [esp+ECh] [ebp-9Ch]
int i; // [esp+104h] [ebp-84h]
char flag[17]; // [esp+110h] [ebp-78h] BYREF
char v13[43]; // [esp+121h] [ebp-67h] BYREF
char v14[32]; // [esp+14Ch] [ebp-3Ch] BYREF
char v15[10]; // [esp+16Ch] [ebp-1Ch] BYREF
char v16[14]; // [esp+176h] [ebp-12h] BYREF
__CheckForDebuggerJustMyCode(&unk_41C008);
qmemcpy(v15, "yk", 2);
v15[2] = 127;
v15[3] = 100;
v15[4] = 114;
v15[5] = 101;
v15[6] = 119;
v15[7] = 74;
v15[8] = 99;
v15[9] = 2;
strcpy(v16, "n");
qmemcpy(&v16[2], "BnGTc", 5);
qmemcpy(v14, "eV8xbnQzcmVzdDFuZ0BfQH0=", 24);
print("please input your flag: ", v5);
scanf("%s", (char)flag);
if ( j_strlen(flag) == 34 )
{
for ( i = 0; i < 17; ++i )
{
if ( (flag[i] ^ 0x31) != v15[i] )
goto LABEL_13;
}
v10 = (unsigned __int8 *)malloc(0x40u);
j_memset(v10, 0, 0x40u);
v3 = j_strlen(v13);
sub_4110EB(v13, v3, v10);
v9 = (4 * j_strlen(v13) - 1) / 3 + 1;
if ( v9 % 4 == 3 )
v7 = v9 + 1;
else
v7 = v9 + 2;
for ( j = 0; j < v7; ++j )
{
if ( v10[j] != v14[j] )
goto LABEL_13;
}
print("right!", v6);
return 0;
}
else
{
LABEL_13:
print("error!\n", v6);
return 0;
}
}直接得到伪代码,为了方便看点,把一些函数名和字符串数组名改了。分析代码逻辑,就是把flag分成平均两部分,一部分进行一个异或操作,第二部分进入到一个加密函数里进行加密,但是,我们可以发现,第一部分flag,在进行完异或之后,与v15数组进行比对,这个v15数组的个数不对,不是 17,那么我们就动调看看,随便输入一个34位的字符串进去,绕过长度检查,但是这里有个反调试,我们得先把断点下在反调试函数这里,程序跑到了这里,然后改一下ZF寄存器的值,改成1,绕过反调试.最后开始反调试,输入字符串后,我们直接双击v15这个字符串,查看其内容,

这才是正确的用来比对的密文,然后shift+E,提取出来
用厨子梭一下
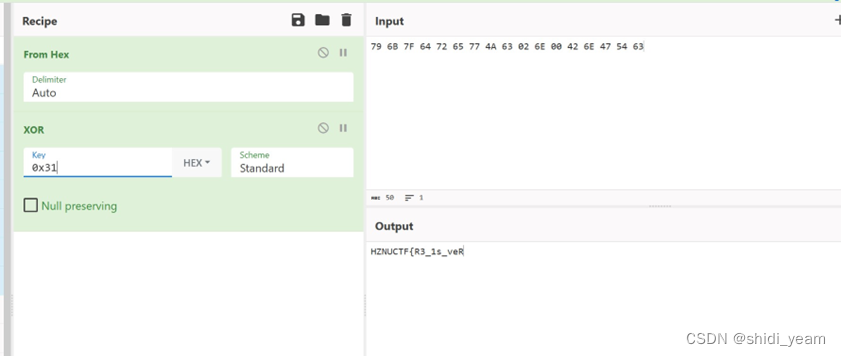
第二部分的话,就得进入到加密函数中查看了,
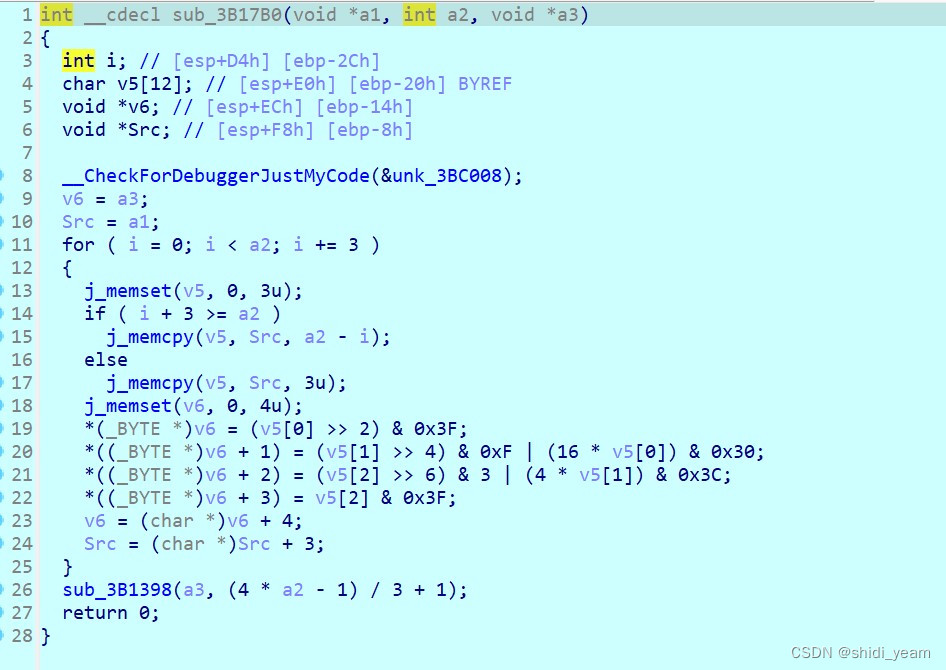
这看下来就是一个base64,继续进入到sub_3B1398函数里查看,
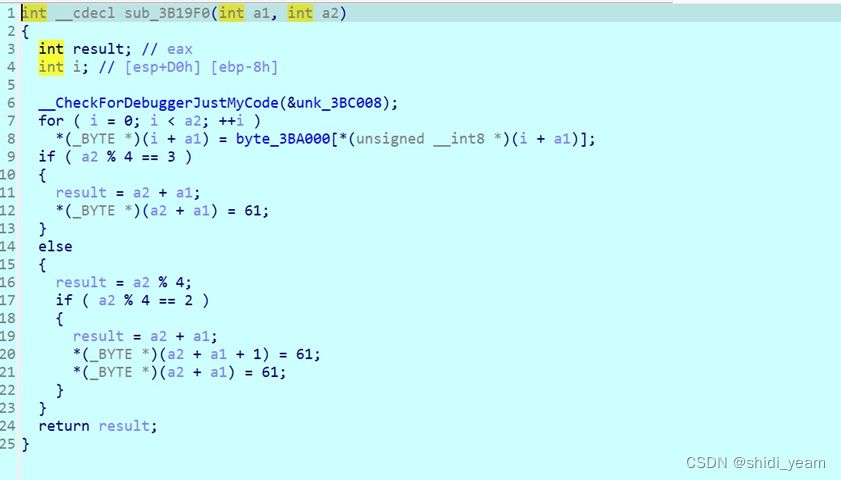
一直跟进下去,可以看到这个数组,点击查看,
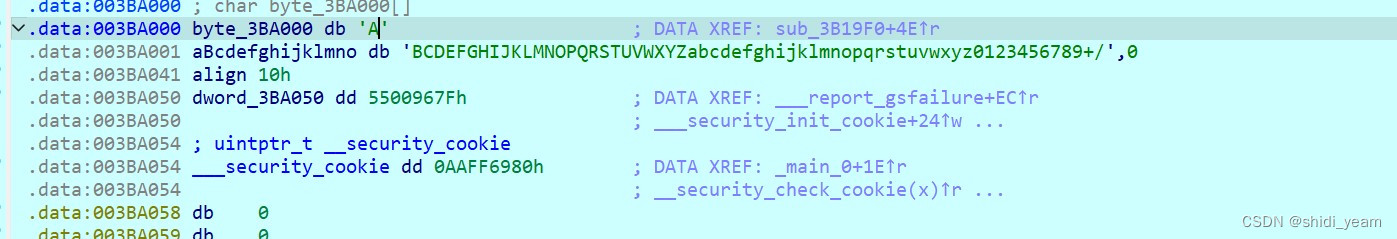
一个标准的base64码表,一样的,厨子梭一下,就可以得到第二部分flag 了,
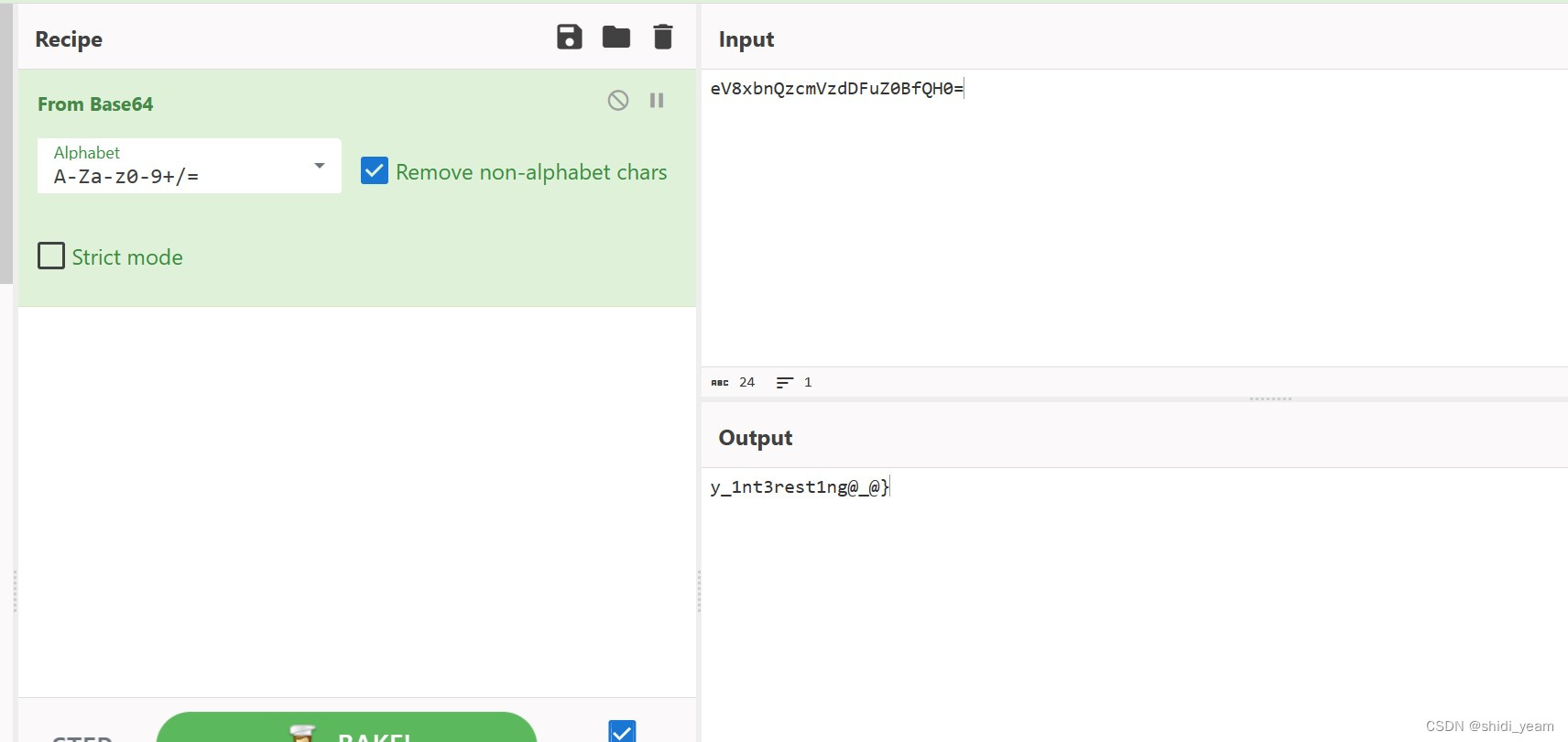
拼接在一起,就是flag
HZNUCTF{R3_1s_veRy_1nt3rest1ng@_@}
3.babyandoird
拿到附件,解压缩一下,一看,.apk 文件,先看看有没有壳
 没壳,那就直接上 jadx 吧
没壳,那就直接上 jadx 吧
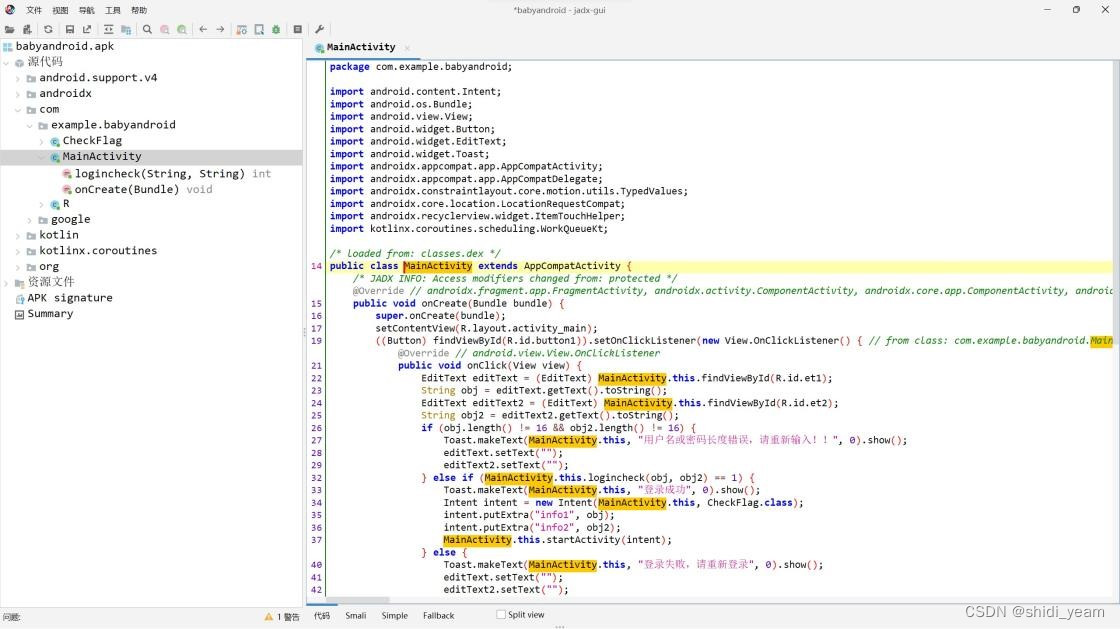
找到主函数,就是一个登录应用,检测用户名和密码,都要是 16 位,然后往下滑动
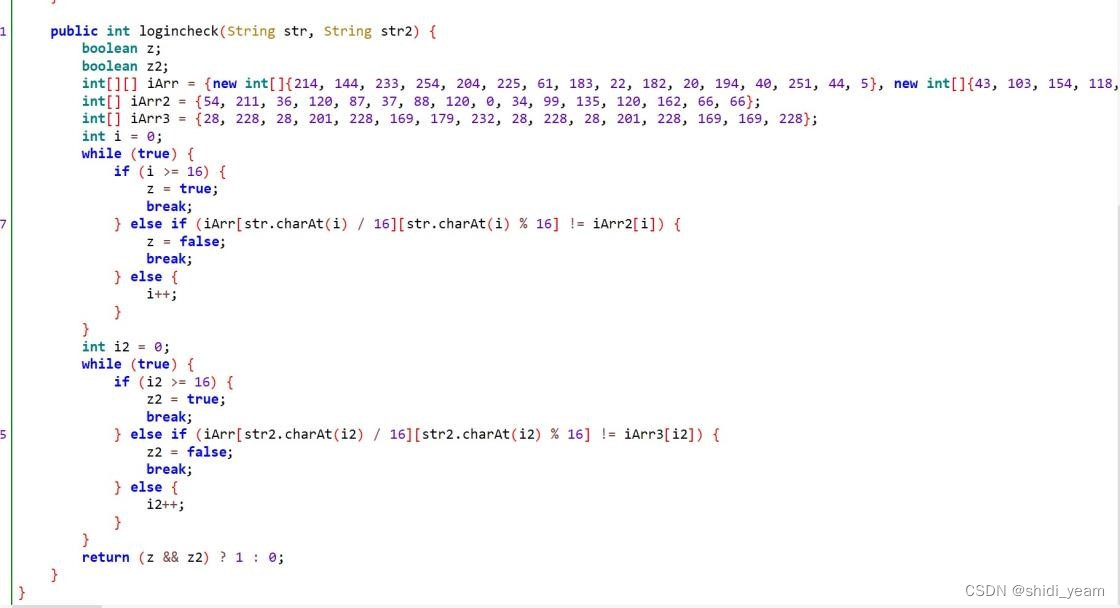
这个函数用来检测用户名和密码,就是将这两者做一些处理后,作为索引,然后在一个已知的二维数组里看能否找到指定数,清楚之后,我就懒得写脚本了,直接暴力直解,
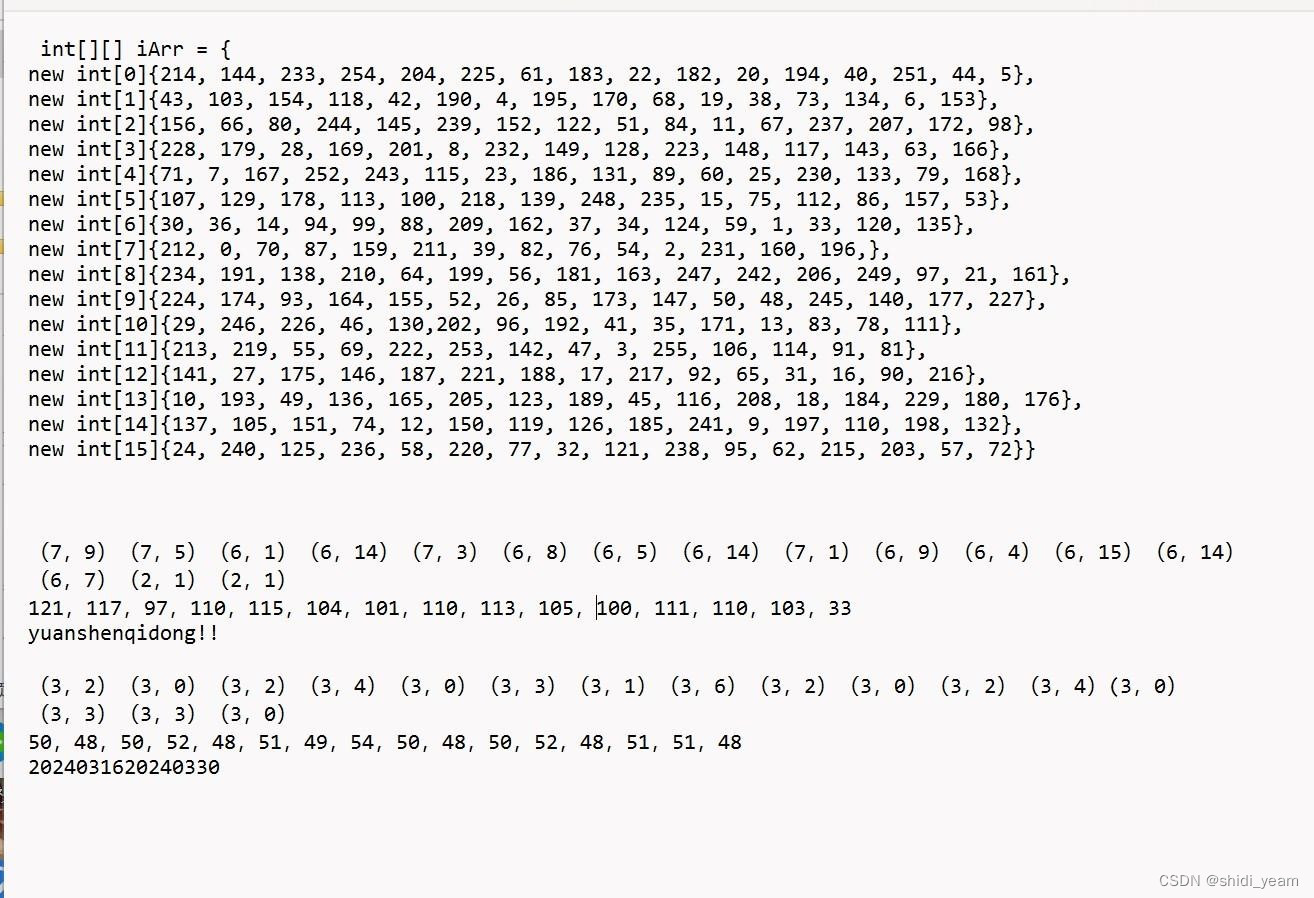
然后再看到 CheckFlag 类
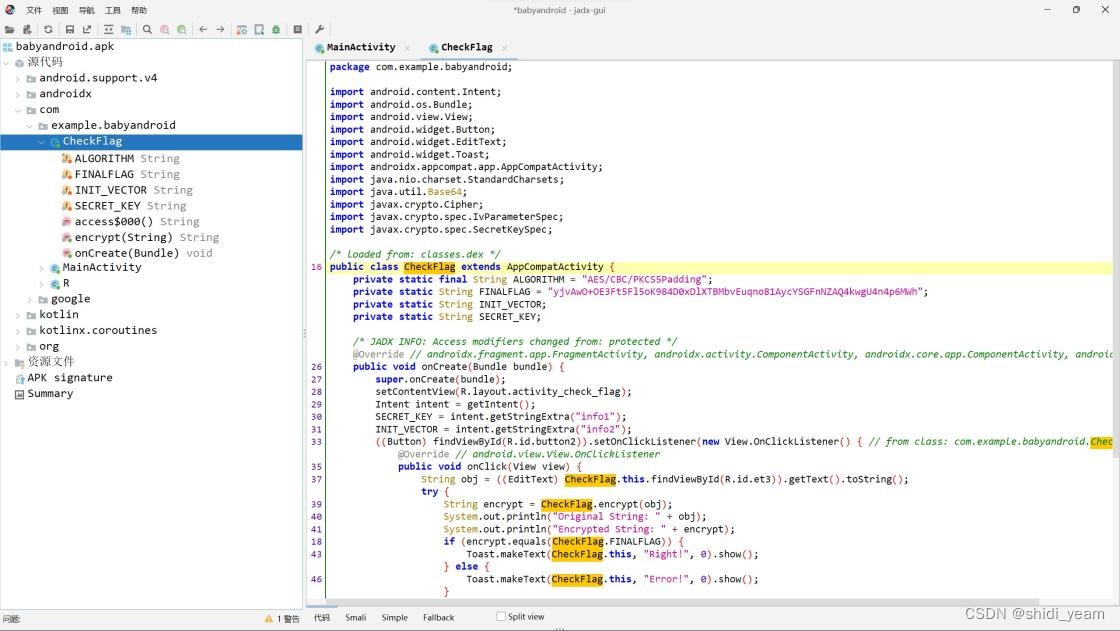
这里的函数逻辑很清晰,就是将正确的密码作为 AES 加密的偏移量,刚好 16
位,用户名作为密钥,然后进行 AES 加密,CBC 的,在网上找个工具梭一下,
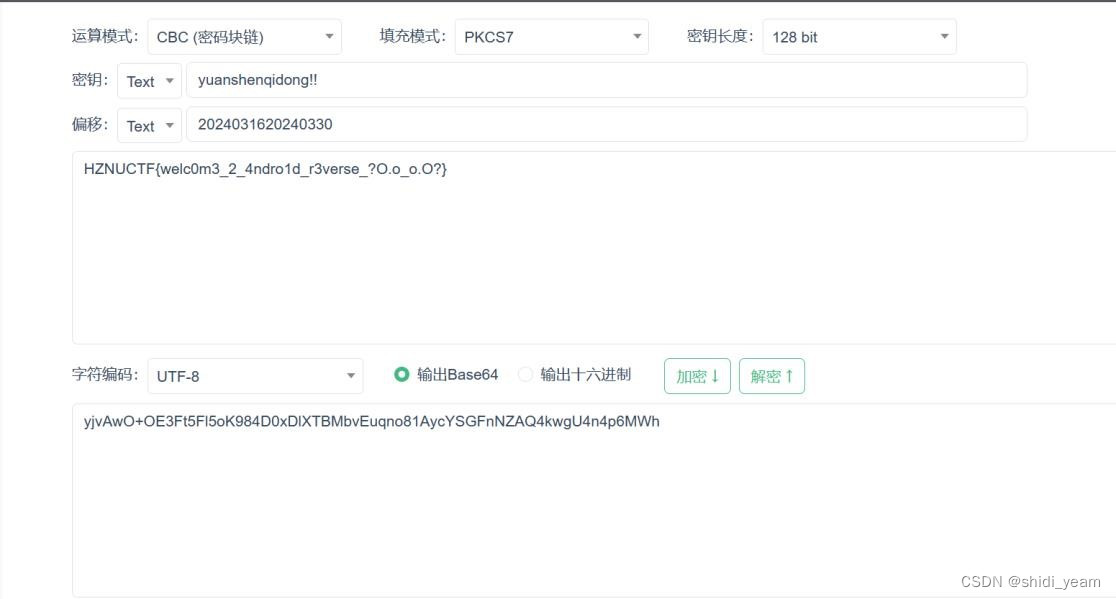
拿到flag
HZNUCTF{welc0m3_2_4ndro1d_r3verse_?O.o_o.O?}
4.运动的elf
拿到附件,解压缩,查壳,没有壳,但一看是.elf,并且看他题目名称是,运动的elf,估计是动调.elf文件了,还是一样,先查壳,
没有壳,64bit的。然后放到虚拟机里跑一下,看看回显,
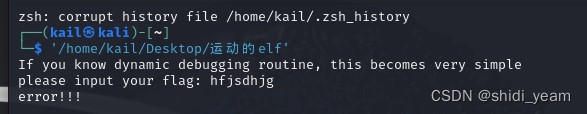
好了,看来基本确定是要动调.elf文件了。先丢到ida-64里分析,分析结束,汇编页面显示直接就是main函数,那么F5就好了,然后得到伪代码,c++写的,看的头疼
int __fastcall main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rdx
char *v4; // rax
__int64 v5; // rax
__int64 v7; // rax
char *v8; // rax
int v9; // eax
bool v11; // bl
__int64 v12; // rax
int i; // [rsp+10h] [rbp-130h]
int j; // [rsp+14h] [rbp-12Ch]
int k; // [rsp+18h] [rbp-128h]
char v17[32]; // [rsp+20h] [rbp-120h] BYREF
char v18[32]; // [rsp+40h] [rbp-100h] BYREF
char v19[32]; // [rsp+60h] [rbp-E0h] BYREF
char v20[32]; // [rsp+80h] [rbp-C0h] BYREF
char v21[32]; // [rsp+A0h] [rbp-A0h] BYREF
char v22[32]; // [rsp+C0h] [rbp-80h] BYREF
char v23[32]; // [rsp+E0h] [rbp-60h] BYREF
char v24[40]; // [rsp+100h] [rbp-40h] BYREF
unsigned __int64 v25; // [rsp+128h] [rbp-18h]
v25 = __readfsqword(0x28u);
std::string::basic_string(v17, argv, envp);
std::string::basic_string(v18, argv, v3);
puts("If you know dynamic debugging routine, this becomes very simpl
printf("please input your flag: ");
std::operator>><char>(&std::cin, v17);
for ( i = 0; i <= 7; ++i )
{
v4 = (char *)std::string::operator[](v17, i);
std::string::operator+=(v18, (unsigned int)*v4);
}
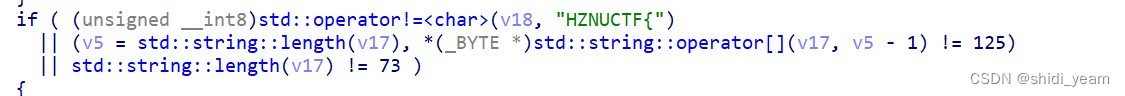
if ( (unsigned __int8)std::operator!=<char>(v18, "HZNUCTF{")
|| (v5 = std::string::length(v17), *(_BYTE *)std::string::operator
|| std::string::length(v17) != 73 )
{
v7 = std::operator<<<std::char_traits<char>>(&std::cout, "error!!!
std::ostream::operator<<(v7, &std::endl<char,std::char_traits<char
}
else
{
std::string::operator=(v18, &unk_A00C);
for ( j = 8; j < (unsigned __int64)(std::string::length(v17) - 1);
{
v8 = (char *)std::string::operator[](v17, j);
std::string::operator+=(v18, (unsigned int)*v8);
}
StoH[abi:cxx11](v19);
std::string::operator=(&h_pwd[abi:cxx11], v19);
std::string::~string(v19);
std::string::basic_string(v24, &h_pwd[abi:cxx11]);
HtoB(v20, v24);
std::string::operator=(&b_pwd[abi:cxx11], v20);
std::string::~string(v20);
std::string::~string(v24);
l = std::string::length(&b_pwd[abi:cxx11]);
for ( ::k = 0; (l + 1 + ::k) % 512 != 448; ++::k )
;
std::to_string((std::__cxx11 *)v24, l);
DtoB(v21, v24);
std::string::~string(v24);
while ( (std::string::length(v21) & 0x3F) != 0 )
{
std::operator+<char>(v22, 48LL, v21);
std::string::operator=(v21, v22);
std::string::~string(v22);
}
std::string::operator+=(&b_pwd[abi:cxx11], 49LL);
v9 = l + ::k + 65;
if ( v9 < 0 )
v9 = l + ::k + 576;
n = v9 >> 9;
while ( ::k-- )
std::string::operator+=(&b_pwd[abi:cxx11], 48LL);
std::string::operator+=(&b_pwd[abi:cxx11], v21);
std::string::basic_string(v24, &v[abi:cxx11]);
HtoB(v23, v24);
std::string::operator=(&v[abi:cxx11], v23);
std::string::~string(v23);
std::string::~string(v24);
for ( k = 0; k < n; ++k )
{
cf[abi:cxx11](v22, (unsigned int)(k << 9));
std::string::basic_string(v23, &v[abi:cxx11]);
Xor(v24, v23, v22);
std::string::operator=(&v[abi:cxx11], v24);
std::string::~string(v24);
std::string::~string(v23);
std::string::~string(v22);
}
std::string::basic_string(v24, v18);
v11 = (unsigned int)func1(v24) != 0;
std::string::~string(v24);
if ( v11 )
v12 = std::operator<<<std::char_traits<char>>(&std::cout, "right
else
v12 = std::operator<<<std::char_traits<char>>(&std::cout, "error
std::ostream::operator<<(v12, &std::endl<char,std::char_traits<cha
std::string::~string(v21);
}
std::string::~string(v18);
std::string::~string(v17);
return 0;
}
既然说如果会远程调试的话就会很简单,那么我们直接找到最后输出的地方,看到如果v11的值是1的话,那就输出正确,然后我们在跟踪v11的值是从哪来的,看到是fun1函数传回来的值,跟进,
__int64 __fastcall func1(__int64 a1, __int64 a2, __int64 a3)
{
__int64 v3; // rdx
_BYTE *v4; // rax
int v6; // [rsp+18h] [rbp-D8h]
int v7; // [rsp+1Ch] [rbp-D4h]
int i; // [rsp+20h] [rbp-D0h]
int j; // [rsp+24h] [rbp-CCh]
int k; // [rsp+28h] [rbp-C8h]
char v11[32]; // [rsp+30h] [rbp-C0h] BYREF
char v12[32]; // [rsp+50h] [rbp-A0h] BYREF
char v13[32]; // [rsp+70h] [rbp-80h] BYREF
char v14[32]; // [rsp+90h] [rbp-60h] BYREF
char v15[40]; // [rsp+B0h] [rbp-40h] BYREF
unsigned __int64 v16; // [rsp+D8h] [rbp-18h]
v16 = __readfsqword(0x28u);
std::string::basic_string(v11, a2, a3);
std::string::basic_string(v12, a2, v3);
v6 = 1;
v7 = 1;
std::string::basic_string(v15, &v[abi:cxx11]);
BtoH(v13, v15);
std::string::operator=(&v[abi:cxx11], v13);
std::string::~string(v13);
std::string::~string(v15);
for ( i = 0; i < (unsigned __int64)std::string::length(&v[abi:cxx11]
{
v4 = (_BYTE *)std::string::operator[](a1, i);
std::string::operator+=(v11, (unsigned int)(char)(*v4 ^ 5));
std::string::operator+=(v11, "#");
}
std::string::basic_string(v15, &v[abi:cxx11]);
std::string::basic_string(v13, v11);
Xor(v14, v13, v15);
std::string::operator=(v11, v14);
std::string::~string(v14);
std::string::~string(v13);
std::string::~string(v15);
std::string::basic_string(v14, &v[abi:cxx11]);
std::string::basic_string(v13, a1);
Xor(v15, v13, v14);
std::string::operator=(v12, v15);
std::string::~string(v15);
std::string::~string(v13);
std::string::~string(v14);
for ( j = 0; j < (unsigned __int64)std::string::length(&v[abi:cxx11]
{
if ( *(_BYTE *)std::string::operator[](v12, j) != 48 )
{
v7 = 0;
break;
}
}
for ( k = 0; k < (unsigned __int64)std::string::length(&v[abi:cxx11]
{
if ( *(_BYTE *)std::string::operator[](v11, k) != 48 )
{
v6 = 0;
break;
}
}
std::string::~string(v12);
std::string::~string(v11);
return v7 ^ (unsigned int)v6;
}可是呢我们还是就只看到了一个异或,以及一个二进制转十进制的数,并没有我们想象的,最后如果输入正确,程序会自己跑,输出正确的flag。那么我们还是继续分析main函数吧,可以看到,主函数要求我们输入的flag一定是73位的,并且有长度检测,以及flag格式是HZNUCTF{},那么这么计算下来,中间的内容就是64位,
一时间还真没什么头绪,那么就shitf+F12看看有没有什么有用的字符串引用,
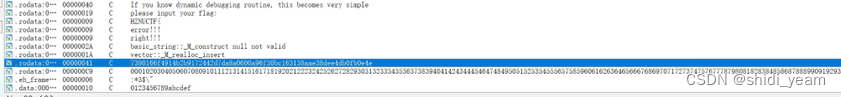
可以看到这个字符串很可疑,恰好 是64位的,那么我们不妨试试,输进来看看。因为一般提示如果会动态调试这题会很简单的话,除了刚才提到的会直接输出flag,还有一种可能 就是flag会在程序内存中,没输出罢了,那么我们就开始远程调试,
先连接一下,然后再在ida里找到进程选项,输入虚拟机的ip地址以及密码,就可以进行远程调试了,就把断点下在提示输入flag的地方即可,然后F8步过,输入我们预设好的字符串,因为中间函数循环有点多,我们再下一个断点在最后if语句判断的地方,然后F9运行,直接略过中间冗杂的循环,这个时候我们再来查看内存,其实一开始我在做的时候还是没有发现什么有用的字符串,然后我就用了findcrypto的插件,

就发现了一个非常可疑的字符串,正好也是64位,然后就提交试一试,还过了,
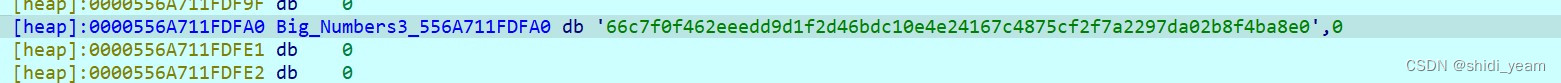
那么就得到了flag,
HZNUCTF{66c7f0f462eeedd9d1f2d46bdc10e4e24167c4875cf2f7a2297da02 b8f4ba8e0}
5.TupEAx
拿到附件,下载,解压缩,查壳,是32bit的,直接脱壳,然后丢到ida-32里分析,分析结束,找到main函数,直接F5得到伪代码,
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
char v4; // [esp+0h] [ebp-1B8h]
char v5; // [esp+0h] [ebp-1B8h]
int m; // [esp+D0h] [ebp-E8h]
int k; // [esp+DCh] [ebp-DCh]
int j; // [esp+E8h] [ebp-D0h]
int v9[4]; // [esp+F4h] [ebp-C4h] BYREF
int i; // [esp+104h] [ebp-B4h]
int z; // [esp+110h] [ebp-A8h]
char flag[4]; // [esp+11Ch] [ebp-9Ch] BYREF
int v13[7]; // [esp+120h] [ebp-98h] BYREF
char v14; // [esp+13Ch] [ebp-7Ch]
char v15[44]; // [esp+148h] [ebp-70h]
int key[6]; // [esp+174h] [ebp-44h] BYREF
char v17[31]; // [esp+18Ch] [ebp-2Ch]
char v18[4]; // [esp+1ABh] [ebp-Dh] BYREF
__CheckForDebuggerJustMyCode(&unk_F3C003);
v17[0] = 0x4A;
v17[1] = 0x9C;
v17[2] = 0x16;
v17[3] = 0xE3; //
//
v17[4] = 0xE9;
v17[5] = 0x90;
v17[6] = 0xB1;
v17[7] = 0x49; //
//
v17[8] = 0x54;
v17[9] = 0xA1;
v17[10] = 0x82;
v17[11] = 0x9E; //
//
v17[12] = 0x3E;
v17[13] = 0x3F;
v17[14] = 0xC4;
v17[15] = 0xAE; //
//
v17[16] = 0xC;
v17[17] = 0x81;
v17[18] = 0x20;
v17[19] = 0x5F; //
//
v17[20] = 0x40;
v17[21] = 0xCE;
v17[22] = 0x51;
v17[23] = 0xAE; //
//
v17[24] = 0x3B;
v17[25] = 0x52;
v17[26] = 0x9B;
v17[27] = 0xB0; //
//
v17[28] = 0xAA;
v17[29] = 0xC1;
v17[30] = 0xF5;
strcpy(v18, "S");
key[0] = 2;
key[1] = 0;
key[2] = 2;
key[3] = 4;
*(_DWORD *)flag = 0;
memset(v13, 0, sizeof(v13));
v14 = 0;
print("please input your flag: ", v4);
scanf("%32s", (char)flag);
z = 0;
for ( i = 0; i < 32; i += 8 )
{
v9[0] = *(_DWORD *)&flag[i];
v9[1] = v13[i / 4u];
tea((int)v9, (int)key);
for ( j = 0; j < 2; ++j )
{
for ( k = 0; k < 4; ++k )
{
v15[z] = v9[j];
v9[j] = (unsigned int)v9[j] >> 8;
++z;
}
}
}
for ( m = 0; m < 32; ++m )
{
if ( v17[m] != v15[m] )
{
print("error!!!\n", v5);
return 0;
}
}
print(aRight, v5);
return 0;
}这里已经对函数名和一些变量名进行了修改。我们分析代码,就是一个tea算法,但是在最后进行了一个小端排序,我们在解密的时候需要逆一下,同时 tea算法中的v13,其实就是我们输入进来的flag,只是ida分析的时候没做好罢了,那么就可以写脚本了。这里借用官方脚本
#include<stdio.h>
#include<stdint.h>
void decrypt(uint32_t* v, uint32_t* k)
{
uint32_t v0 = v[0], v1 = v[1];
uint32_t delta = 0xd33b470;
uint32_t sum = 32 * delta;
for (int i = 0; i < 32; i++) {
v1 -= ((v0 << 4) + k[2]) ^ (v0 + sum) ^ ((v0 >> 5) + k[3]);
v0 -= ((v1 << 4) + k[0]) ^ (v1 + sum) ^ ((v1 >> 5) + k[1]);
sum -= delta;
}
v[0] = v0;
v[1] = v1;
}
int main() {
int8_t result[33] = {
0x4a, 0x9c, 0x16, 0xe3, 0xe9, 0x90, 0xb1, 0x49, 0x54, 0xa1,
0x82, 0x9e, 0x3e, 0x3f, 0xc4, 0xae, 0x0c, 0x81, 0x20, 0x5f,
0x40, 0xce, 0x51, 0xae, 0x3b, 0x52, 0x9b, 0xb0, 0xaa, 0xc1,
0xf5, 0x53, };
uint32_t k[4] = { 2,0,2,4 };
for (int i = 0; i < 32; i += 8) {
uint32_t v[2] = { *(uint32_t*)&result[i], *(uint32_t*)&result[i + 4] };
decrypt(v, k);
for (int j = 0; j < 2; j++)
{
for (int k = 0; k < 4; k++)//小端序存储
{
printf("%c", v[j] & 0xff);
v[j] >>= 8;
}
}
}
return 0;
}得到flag:
HZNUCTF{EnjOy_th1s_cuP_0f_t3@@@}
6.ezpy
下载附件,解压缩,很明显就是一个pyc逆向,先用pyinstxtractor.py反编译,得到.py文件,然后用pycdc,就可以得到如下,
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
def IV(begin, end):
Unsupported opcode: JUMP_BACKWARD
x = float('inf')
mat = [
0 [ 0, 9, 1, x, x, x, x, x, x, x, x, x, x, x, x, x],
1 [ 1, 0, x, 1, x, x, x, x, 0, x, x, x, x, x, x, x],
2 [ 1, x, 0, x, 1, x, x, x, x, x, x, x, x, x, x, x],
3 [ x, 1, x, 0, x, 1, x, x, x, x, x, x, x, x, x, x],
4 [ x, x, 1, x, 0, x, 1, x, x, x, x, x, x, x, x, x],
5 [ x, x, x, 1, x, 0, x, 1, x, x, x, x, x, x, x, x],
6 [ x, x, x, x, 1, x, 0, x, 1, x, x, x, x, x, x, x],
7 [ x, x, x, x, x, 1, x, 0, 9, 1, x, x, x, x, x, x],
8 [ x, 1, x, x, x, x, 1, 9, 0, x, x, x, x, x, x, 50],
9 [ x, x, x, x, x, x, x, 1, x, 0, 1, x, x, x, x, x],
10 [ x, x, x, x, x, x, x, x, x, 1, 0, 1, x, x, x, x],
11 [ x, x, x, x, x, x, x, x, x, x, 1, 0, 1, x, x, x],
12 [ x, x, x, x, x, x, x, x, x, x, x, 1, 0, 1, x, x],
13 [ x, x, x, x, x, x, x, x, x, x, x, x, 1, 0, 1, x],
14 [ x, x, x, x, x, x, x, x, x, x, x, x, x, 1, 0, 1],
15 [ x, x, x, x, x, x, x, x, 50, x, x, x, x, x, 1,0]
]
n = len(mat)
parent = []
collected = []
distTo = mat[begin]
path = []
# WARNING: Decompyle incomplete
def Key():
Unsupported opcode: JUMP_BACKWARD
key1 = [ 55, 53, 55, 49, 53, 54, 55, 53] 75715675;9;=9::9
key2 = [ 59, 57, 59, 61, 57, 58, 58, 57]
key = ''
# WARNING: Decompyle incomplete
def encrypt(key, plaintext, iv = (None,)):
cipher = AES.new(key, AES.MODE_CBC, iv = iv) if iv else AES.new(key, AES.MODE_CBC)
ciphertext = cipher.encrypt(pad(plaintext, AES.block_size))
return ciphertext
def main():
flag = b'68fcb549ee313b964d5eea2d3dedea23e87e4e89a675ff46698ed29b191ffe19f5bac00e0eb5dedcc8be847356d93eb8'
print('please input your flag: ', end = '')
message = input()
plaintext = message.encode('utf-8')
key = Key().encode('utf-8')
iv = IV(0, 15).encode('utf-8')
ciphertext = encrypt(key, plaintext, iv)
if ciphertext.hex().encode('utf-8') == flag:
print('Right!!!')
return None
None('error!!!')
main()
很明显。KEY函数不完整,那就只能看字节码了
ezpy.pyc (Python 3.11)
[Code]
File Name: ezpy.py
Object Name: <module>
Qualified Name: <module>
Arg Count: 0
Pos Only Arg Count: 0
KW Only Arg Count: 0
Stack Size: 2
Flags: 0x00000000
[Names]
'Crypto.Cipher'
'AES'
'Crypto.Util.Padding'
'pad'
'IV'
'Key'
'encrypt'
'main'
[Locals+Names]
[Constants]
0
(
'AES'
)
(
'pad'
)
[Code]
File Name: ezpy.py
Object Name: IV
Qualified Name: IV
Arg Count: 2
Pos Only Arg Count: 0
KW Only Arg Count: 0
Stack Size: 31
Flags: 0x00000003 (CO_OPTIMIZED | CO_NEWLOCALS)
[Names]
'float'
'len'
'range'
'append'
'reverse'
'hex'
[Locals+Names]
'begin'
'end'
'x'
'mat'
'n'
'parent'
'collected'
'distTo'
'path'
'i'
'min_n'
'v'
'e'
'iv'
[Constants]
None
'inf'
0
9
1
50
True
False
-1
''
2
[Disassembly]
0 RESUME 0
2 LOAD_GLOBAL 1: NULL + float
14 LOAD_CONST 1: 'inf'
16 PRECALL 1
20 CALL 1
30 STORE_FAST 2: x
32 LOAD_CONST 2: 0
34 LOAD_CONST 3: 9
36 LOAD_CONST 4: 1
38 LOAD_FAST 2: x
40 LOAD_FAST 2: x
42 LOAD_FAST 2: x
44 LOAD_FAST 2: x
46 LOAD_FAST 2: x
48 LOAD_FAST 2: x
50 LOAD_FAST 2: x
52 LOAD_FAST 2: x
54 LOAD_FAST 2: x
56 LOAD_FAST 2: x
58 LOAD_FAST 2: x
60 LOAD_FAST 2: x
62 LOAD_FAST 2: x
64 BUILD_LIST 16
66 LOAD_CONST 4: 1
68 LOAD_CONST 2: 0
70 LOAD_FAST 2: x
72 LOAD_CONST 4: 1
74 LOAD_FAST 2: x
76 LOAD_FAST 2: x
78 LOAD_FAST 2: x
80 LOAD_FAST 2: x
82 LOAD_CONST 2: 0
84 LOAD_FAST 2: x
86 LOAD_FAST 2: x
88 LOAD_FAST 2: x
90 LOAD_FAST 2: x
92 LOAD_FAST 2: x
94 LOAD_FAST 2: x
96 LOAD_FAST 2: x
98 BUILD_LIST 16
100 LOAD_CONST 4: 1
102 LOAD_FAST 2: x
104 LOAD_CONST 2: 0
106 LOAD_FAST 2: x
108 LOAD_CONST 4: 1
110 LOAD_FAST 2: x
112 LOAD_FAST 2: x
114 LOAD_FAST 2: x
116 LOAD_FAST 2: x
118 LOAD_FAST 2: x
120 LOAD_FAST 2: x
122 LOAD_FAST 2: x
124 LOAD_FAST 2: x
126 LOAD_FAST 2: x
128 LOAD_FAST 2: x
130 LOAD_FAST 2: x
132 BUILD_LIST 16
134 LOAD_FAST 2: x
136 LOAD_CONST 4: 1
138 LOAD_FAST 2: x
140 LOAD_CONST 2: 0
142 LOAD_FAST 2: x
144 LOAD_CONST 4: 1
146 LOAD_FAST 2: x
148 LOAD_FAST 2: x
150 LOAD_FAST 2: x
152 LOAD_FAST 2: x
154 LOAD_FAST 2: x
156 LOAD_FAST 2: x
158 LOAD_FAST 2: x
160 LOAD_FAST 2: x
162 LOAD_FAST 2: x
164 LOAD_FAST 2: x
166 BUILD_LIST 16
168 LOAD_FAST 2: x
170 LOAD_FAST 2: x
172 LOAD_CONST 4: 1
174 LOAD_FAST 2: x
176 LOAD_CONST 2: 0
178 LOAD_FAST 2: x
180 LOAD_CONST 4: 1
182 LOAD_FAST 2: x
184 LOAD_FAST 2: x
186 LOAD_FAST 2: x
188 LOAD_FAST 2: x
190 LOAD_FAST 2: x
192 LOAD_FAST 2: x
194 LOAD_FAST 2: x
196 LOAD_FAST 2: x
198 LOAD_FAST 2: x
200 BUILD_LIST 16
202 LOAD_FAST 2: x
204 LOAD_FAST 2: x
206 LOAD_FAST 2: x
208 LOAD_CONST 4: 1
210 LOAD_FAST 2: x
212 LOAD_CONST 2: 0
214 LOAD_FAST 2: x
216 LOAD_CONST 4: 1
218 LOAD_FAST 2: x
220 LOAD_FAST 2: x
222 LOAD_FAST 2: x
224 LOAD_FAST 2: x
226 LOAD_FAST 2: x
228 LOAD_FAST 2: x
230 LOAD_FAST 2: x
232 LOAD_FAST 2: x
234 BUILD_LIST 16
236 LOAD_FAST 2: x
238 LOAD_FAST 2: x
240 LOAD_FAST 2: x
242 LOAD_FAST 2: x
244 LOAD_CONST 4: 1
246 LOAD_FAST 2: x
248 LOAD_CONST 2: 0
250 LOAD_FAST 2: x
252 LOAD_CONST 4: 1
254 LOAD_FAST 2: x
256 LOAD_FAST 2: x
258 LOAD_FAST 2: x
260 LOAD_FAST 2: x
262 LOAD_FAST 2: x
264 LOAD_FAST 2: x
266 LOAD_FAST 2: x
268 BUILD_LIST 16
270 LOAD_FAST 2: x
272 LOAD_FAST 2: x
274 LOAD_FAST 2: x
276 LOAD_FAST 2: x
278 LOAD_FAST 2: x
280 LOAD_CONST 4: 1
282 LOAD_FAST 2: x
284 LOAD_CONST 2: 0
286 LOAD_CONST 3: 9
288 LOAD_CONST 4: 1
290 LOAD_FAST 2: x
292 LOAD_FAST 2: x
294 LOAD_FAST 2: x
296 LOAD_FAST 2: x
298 LOAD_FAST 2: x
300 LOAD_FAST 2: x
302 BUILD_LIST 16
304 LOAD_FAST 2: x
306 LOAD_CONST 4: 1
308 LOAD_FAST 2: x
310 LOAD_FAST 2: x
312 LOAD_FAST 2: x
314 LOAD_FAST 2: x
316 LOAD_CONST 4: 1
318 LOAD_CONST 3: 9
320 LOAD_CONST 2: 0
322 LOAD_FAST 2: x
324 LOAD_FAST 2: x
326 LOAD_FAST 2: x
328 LOAD_FAST 2: x
330 LOAD_FAST 2: x
332 LOAD_FAST 2: x
334 LOAD_CONST 5: 50
336 BUILD_LIST 16
338 LOAD_FAST 2: x
340 LOAD_FAST 2: x
342 LOAD_FAST 2: x
344 LOAD_FAST 2: x
346 LOAD_FAST 2: x
348 LOAD_FAST 2: x
350 LOAD_FAST 2: x
352 LOAD_CONST 4: 1
354 LOAD_FAST 2: x
356 LOAD_CONST 2: 0
358 LOAD_CONST 4: 1
360 LOAD_FAST 2: x
362 LOAD_FAST 2: x
364 LOAD_FAST 2: x
366 LOAD_FAST 2: x
368 LOAD_FAST 2: x
370 BUILD_LIST 16
372 LOAD_FAST 2: x
374 LOAD_FAST 2: x
376 LOAD_FAST 2: x
378 LOAD_FAST 2: x
380 LOAD_FAST 2: x
382 LOAD_FAST 2: x
384 LOAD_FAST 2: x
386 LOAD_FAST 2: x
388 LOAD_FAST 2: x
390 LOAD_CONST 4: 1
392 LOAD_CONST 2: 0
394 LOAD_CONST 4: 1
396 LOAD_FAST 2: x
398 LOAD_FAST 2: x
400 LOAD_FAST 2: x
402 LOAD_FAST 2: x
404 BUILD_LIST 16
406 LOAD_FAST 2: x
408 LOAD_FAST 2: x
410 LOAD_FAST 2: x
412 LOAD_FAST 2: x
414 LOAD_FAST 2: x
416 LOAD_FAST 2: x
418 LOAD_FAST 2: x
420 LOAD_FAST 2: x
422 LOAD_FAST 2: x
424 LOAD_FAST 2: x
426 LOAD_CONST 4: 1
428 LOAD_CONST 2: 0
430 LOAD_CONST 4: 1
432 LOAD_FAST 2: x
434 LOAD_FAST 2: x
436 LOAD_FAST 2: x
438 BUILD_LIST 16
440 LOAD_FAST 2: x
442 LOAD_FAST 2: x
444 LOAD_FAST 2: x
446 LOAD_FAST 2: x
448 LOAD_FAST 2: x
450 LOAD_FAST 2: x
452 LOAD_FAST 2: x
454 LOAD_FAST 2: x
456 LOAD_FAST 2: x
458 LOAD_FAST 2: x
460 LOAD_FAST 2: x
462 LOAD_CONST 4: 1
464 LOAD_CONST 2: 0
466 LOAD_CONST 4: 1
468 LOAD_FAST 2: x
470 LOAD_FAST 2: x
472 BUILD_LIST 16
474 LOAD_FAST 2: x
476 LOAD_FAST 2: x
478 LOAD_FAST 2: x
480 LOAD_FAST 2: x
482 LOAD_FAST 2: x
484 LOAD_FAST 2: x
486 LOAD_FAST 2: x
488 LOAD_FAST 2: x
490 LOAD_FAST 2: x
492 LOAD_FAST 2: x
494 LOAD_FAST 2: x
496 LOAD_FAST 2: x
498 LOAD_CONST 4: 1
500 LOAD_CONST 2: 0
502 LOAD_CONST 4: 1
504 LOAD_FAST 2: x
506 BUILD_LIST 16
508 LOAD_FAST 2: x
510 LOAD_FAST 2: x
512 LOAD_FAST 2: x
514 LOAD_FAST 2: x
516 LOAD_FAST 2: x
518 LOAD_FAST 2: x
520 LOAD_FAST 2: x
522 LOAD_FAST 2: x
524 LOAD_FAST 2: x
526 LOAD_FAST 2: x
528 LOAD_FAST 2: x
530 LOAD_FAST 2: x
532 LOAD_FAST 2: x
534 LOAD_CONST 4: 1
536 LOAD_CONST 2: 0
538 LOAD_CONST 4: 1
540 BUILD_LIST 16
542 LOAD_FAST 2: x
544 LOAD_FAST 2: x
546 LOAD_FAST 2: x
548 LOAD_FAST 2: x
550 LOAD_FAST 2: x
552 LOAD_FAST 2: x
554 LOAD_FAST 2: x
556 LOAD_FAST 2: x
558 LOAD_CONST 5: 50
560 LOAD_FAST 2: x
562 LOAD_FAST 2: x
564 LOAD_FAST 2: x
566 LOAD_FAST 2: x
568 LOAD_FAST 2: x
570 LOAD_CONST 4: 1
572 LOAD_CONST 2: 0
574 BUILD_LIST 16
576 BUILD_LIST 16
578 STORE_FAST 3: mat
580 LOAD_GLOBAL 3: NULL + len
592 LOAD_FAST 3: mat
594 PRECALL 1
598 CALL 1
608 STORE_FAST 4: n
610 BUILD_LIST 0
612 STORE_FAST 5: parent
614 BUILD_LIST 0
616 STORE_FAST 6: collected
618 LOAD_FAST 3: mat
620 LOAD_FAST 0: begin
622 BINARY_SUBSCR
632 STORE_FAST 7: distTo
634 BUILD_LIST 0
636 STORE_FAST 8: path
638 LOAD_GLOBAL 5: NULL + range
650 LOAD_CONST 2: 0
652 LOAD_FAST 4: n
654 PRECALL 2
658 CALL 2
668 GET_ITER
670 FOR_ITER 72 (to 816)
672 STORE_FAST 9: i
674 LOAD_FAST 9: i
676 LOAD_FAST 0: begin
678 COMPARE_OP 2 (==)
684 POP_JUMP_FORWARD_IF_FALSE 22 (to 730)
686 LOAD_FAST 6: collected
688 LOAD_METHOD 3: append
710 LOAD_CONST 6: True
712 PRECALL 1
716 CALL 1
726 POP_TOP
728 JUMP_FORWARD 21 (to 772)
730 LOAD_FAST 6: collected
732 LOAD_METHOD 3: append
754 LOAD_CONST 7: False
756 PRECALL 1
760 CALL 1
770 POP_TOP
772 LOAD_FAST 5: parent
774 LOAD_METHOD 3: append
796 LOAD_CONST 8: -1
798 PRECALL 1
802 CALL 1
812 POP_TOP
814 JUMP_BACKWARD 73 (to 670)
816 NOP
818 LOAD_FAST 6: collected
820 LOAD_FAST 1: end
822 BINARY_SUBSCR
832 LOAD_CONST 6: True
834 COMPARE_OP 2 (==)
840 POP_JUMP_FORWARD_IF_FALSE 1 (to 844)
842 JUMP_FORWARD 156 (to 1156)
844 LOAD_FAST 2: x
846 STORE_FAST 10: min_n
848 LOAD_GLOBAL 5: NULL + range
860 LOAD_CONST 2: 0
862 LOAD_FAST 4: n
864 PRECALL 2
868 CALL 2
878 GET_ITER
880 FOR_ITER 36 (to 954)
882 STORE_FAST 9: i
884 LOAD_FAST 6: collected
886 LOAD_FAST 9: i
888 BINARY_SUBSCR
898 LOAD_CONST 7: False
900 COMPARE_OP 2 (==)
906 POP_JUMP_FORWARD_IF_FALSE 22 (to 952)
908 LOAD_FAST 7: distTo
910 LOAD_FAST 9: i
912 BINARY_SUBSCR
922 LOAD_FAST 10: min_n
924 COMPARE_OP 0 (<)
930 POP_JUMP_FORWARD_IF_FALSE 10 (to 952)
932 LOAD_FAST 7: distTo
934 LOAD_FAST 9: i
936 BINARY_SUBSCR
946 STORE_FAST 10: min_n
948 LOAD_FAST 9: i
950 STORE_FAST 11: v
952 JUMP_BACKWARD 37 (to 880)
954 LOAD_CONST 6: True
956 LOAD_FAST 6: collected
958 LOAD_FAST 11: v
960 STORE_SUBSCR
964 LOAD_GLOBAL 5: NULL + range
976 LOAD_CONST 2: 0
978 LOAD_FAST 4: n
980 PRECALL 2
984 CALL 2
994 GET_ITER
996 FOR_ITER 78 (to 1154)
998 STORE_FAST 9: i
1000 LOAD_FAST 6: collected
1002 LOAD_FAST 9: i
1004 BINARY_SUBSCR
1014 LOAD_CONST 7: False
1016 COMPARE_OP 2 (==)
1022 POP_JUMP_FORWARD_IF_FALSE 64 (to 1152)
1024 LOAD_FAST 7: distTo
1026 LOAD_FAST 11: v
1028 BINARY_SUBSCR
1038 LOAD_FAST 3: mat
1040 LOAD_FAST 11: v
1042 BINARY_SUBSCR
1052 LOAD_FAST 9: i
1054 BINARY_SUBSCR
1064 BINARY_OP 0 (+)
1068 LOAD_FAST 7: distTo
1070 LOAD_FAST 9: i
1072 BINARY_SUBSCR
1082 COMPARE_OP 0 (<)
1088 POP_JUMP_FORWARD_IF_FALSE 31 (to 1152)
1090 LOAD_FAST 11: v
1092 LOAD_FAST 5: parent
1094 LOAD_FAST 9: i
1096 STORE_SUBSCR
1100 LOAD_FAST 7: distTo
1102 LOAD_FAST 11: v
1104 BINARY_SUBSCR
1114 LOAD_FAST 3: mat
1116 LOAD_FAST 11: v
1118 BINARY_SUBSCR
1128 LOAD_FAST 9: i
1130 BINARY_SUBSCR
1140 BINARY_OP 0 (+)
1144 LOAD_FAST 7: distTo
1146 LOAD_FAST 9: i
1148 STORE_SUBSCR
1152 JUMP_BACKWARD 79 (to 996)
1154 JUMP_BACKWARD 169 (to 818)
1156 LOAD_FAST 1: end
1158 STORE_FAST 12: e
1160 LOAD_FAST 12: e
1162 LOAD_CONST 8: -1
1164 COMPARE_OP 3 (!=)
1170 POP_JUMP_FORWARD_IF_FALSE 35 (to 1242)
1172 LOAD_FAST 8: path
1174 LOAD_METHOD 3: append
1196 LOAD_FAST 12: e
1198 PRECALL 1
1202 CALL 1
1212 POP_TOP
1214 LOAD_FAST 5: parent
1216 LOAD_FAST 12: e
1218 BINARY_SUBSCR
1228 STORE_FAST 12: e
1230 LOAD_FAST 12: e
1232 LOAD_CONST 8: -1
1234 COMPARE_OP 3 (!=)
1240 POP_JUMP_BACKWARD_IF_TRUE 35 (to 1172)
1242 LOAD_FAST 8: path
1244 LOAD_METHOD 3: append
1266 LOAD_FAST 0: begin
1268 PRECALL 1
1272 CALL 1
1282 POP_TOP
1284 LOAD_FAST 8: path
1286 LOAD_METHOD 4: reverse
1308 PRECALL 0
1312 CALL 0
1322 POP_TOP
1324 LOAD_CONST 9: ''
1326 STORE_FAST 13: iv
1328 LOAD_GLOBAL 5: NULL + range
1340 LOAD_GLOBAL 3: NULL + len
1352 LOAD_FAST 8: path
1354 PRECALL 1
1358 CALL 1
1368 PRECALL 1
1372 CALL 1
1382 GET_ITER
1384 FOR_ITER 34 (to 1454)
1386 STORE_FAST 9: i
1388 LOAD_FAST 13: iv
1390 LOAD_GLOBAL 11: NULL + hex
1402 LOAD_FAST 8: path
1404 LOAD_FAST 9: i
1406 BINARY_SUBSCR
1416 PRECALL 1
1420 CALL 1
1430 LOAD_CONST 10: 2
1432 LOAD_CONST 0: None
1434 BUILD_SLICE 2
1436 BINARY_SUBSCR
1446 BINARY_OP 13 (+=)
1450 STORE_FAST 13: iv
1452 JUMP_BACKWARD 35 (to 1384)
1454 LOAD_FAST 13: iv
1456 RETURN_VALUE
[Code]
File Name: ezpy.py
Object Name: Key
Qualified Name: Key
Arg Count: 0
Pos Only Arg Count: 0
KW Only Arg Count: 0
Stack Size: 6
Flags: 0x00000003 (CO_OPTIMIZED | CO_NEWLOCALS)
[Names]
'range'
'len'
'chr'
[Locals+Names]
'key1'
'key2'
'key'
'i'
[Constants]
None
(
55
53
55
49
53
54
55
53
)
(
59
57
59
61
57
58
58
57
)
''
5
9
[Disassembly]
0 RESUME 0
2 BUILD_LIST 0
4 LOAD_CONST 1: (55, 53, 55, 49, 53, 54, 55, 53)
6 LIST_EXTEND 1
8 STORE_FAST 0: key1
10 BUILD_LIST 0
12 LOAD_CONST 2: (59, 57, 59, 61, 57, 58, 58, 57)
14 LIST_EXTEND 1
16 STORE_FAST 1: key2
18 LOAD_CONST 3: ''
20 STORE_FAST 2: key
22 LOAD_GLOBAL 1: NULL + range
34 LOAD_GLOBAL 3: NULL + len
46 LOAD_FAST 0: key1
48 PRECALL 1
52 CALL 1
62 PRECALL 1
66 CALL 1
76 GET_ITER
78 FOR_ITER 29 (to 138)
80 STORE_FAST 3: i
82 LOAD_FAST 2: key
84 LOAD_GLOBAL 5: NULL + chr
96 LOAD_FAST 0: key1
98 LOAD_FAST 3: i
100 BINARY_SUBSCR
110 LOAD_CONST 4: 5
112 BINARY_OP 12 (^)
116 PRECALL 1
120 CALL 1
130 BINARY_OP 13 (+=)
134 STORE_FAST 2: key
136 JUMP_BACKWARD 30 (to 78)
138 LOAD_GLOBAL 1: NULL + range
150 LOAD_GLOBAL 3: NULL + len
162 LOAD_FAST 1: key2
164 PRECALL 1
168 CALL 1
178 PRECALL 1
182 CALL 1
192 GET_ITER
194 FOR_ITER 29 (to 254)
196 STORE_FAST 3: i
198 LOAD_FAST 2: key
200 LOAD_GLOBAL 5: NULL + chr
212 LOAD_FAST 1: key2
214 LOAD_FAST 3: i
216 BINARY_SUBSCR
226 LOAD_CONST 5: 9
228 BINARY_OP 12 (^)
232 PRECALL 1
236 CALL 1
246 BINARY_OP 13 (+=)
250 STORE_FAST 2: key
252 JUMP_BACKWARD 30 (to 194)
254 LOAD_FAST 2: key
256 RETURN_VALUE
None
[Code]
File Name: ezpy.py
Object Name: encrypt
Qualified Name: encrypt
Arg Count: 3
Pos Only Arg Count: 0
KW Only Arg Count: 0
Stack Size: 6
Flags: 0x00000003 (CO_OPTIMIZED | CO_NEWLOCALS)
[Names]
'AES'
'new'
'MODE_CBC'
'encrypt'
'pad'
'block_size'
[Locals+Names]
'key'
'plaintext'
'iv'
'cipher'
'ciphertext'
[Constants]
None
(
'iv'
)
[Disassembly]
0 RESUME 0
2 LOAD_FAST 2: iv
4 POP_JUMP_FORWARD_IF_FALSE 33 (to 72)
6 LOAD_GLOBAL 1: NULL + AES
18 LOAD_ATTR 1: new
28 LOAD_FAST 0: key
30 LOAD_GLOBAL 0: AES
42 LOAD_ATTR 2: MODE_CBC
52 LOAD_FAST 2: iv
54 KW_NAMES 1: ('iv',)
56 PRECALL 3
60 CALL 3
70 JUMP_FORWARD 30 (to 132)
72 LOAD_GLOBAL 1: NULL + AES
84 LOAD_ATTR 1: new
94 LOAD_FAST 0: key
96 LOAD_GLOBAL 0: AES
108 LOAD_ATTR 2: MODE_CBC
118 PRECALL 2
122 CALL 2
132 STORE_FAST 3: cipher
134 LOAD_FAST 3: cipher
136 LOAD_METHOD 3: encrypt
158 LOAD_GLOBAL 9: NULL + pad
170 LOAD_FAST 1: plaintext
172 LOAD_GLOBAL 0: AES
184 LOAD_ATTR 5: block_size
194 PRECALL 2
198 CALL 2
208 PRECALL 1
212 CALL 1
222 STORE_FAST 4: ciphertext
224 LOAD_FAST 4: ciphertext
226 RETURN_VALUE
[Code]
File Name: ezpy.py
Object Name: main
Qualified Name: main
Arg Count: 0
Pos Only Arg Count: 0
KW Only Arg Count: 0
Stack Size: 5
Flags: 0x00000003 (CO_OPTIMIZED | CO_NEWLOCALS)
[Names]
'print'
'input'
'encode'
'Key'
'IV'
'encrypt'
'hex'
[Locals+Names]
'flag'
'message'
'plaintext'
'key'
'iv'
'ciphertext'
[Constants]
None
b'68fcb549ee313b964d5eea2d3dedea23e87e4e89a675ff46698ed29b191ffe19f5bac00e0eb5dedcc8be847356d93eb8'
'please input your flag: '
''
(
'end'
)
'utf-8'
0
15
'Right!!!'
'error!!!'
[Disassembly]
0 RESUME 0
2 LOAD_CONST 1: b'68fcb549ee313b964d5eea2d3dedea23e87e4e89a675ff46698ed29b191ffe19f5bac00e0eb5dedcc8be847356d93eb8'
4 STORE_FAST 0: flag
6 LOAD_GLOBAL 1: NULL + print
18 LOAD_CONST 2: 'please input your flag: '
20 LOAD_CONST 3: ''
22 KW_NAMES 4: ('end',)
24 PRECALL 2
28 CALL 2
38 POP_TOP
40 LOAD_GLOBAL 3: NULL + input
52 PRECALL 0
56 CALL 0
66 STORE_FAST 1: message
68 LOAD_FAST 1: message
70 LOAD_METHOD 2: encode
92 LOAD_CONST 5: 'utf-8'
94 PRECALL 1
98 CALL 1
108 STORE_FAST 2: plaintext
110 LOAD_GLOBAL 7: NULL + Key
122 PRECALL 0
126 CALL 0
136 LOAD_METHOD 2: encode
158 LOAD_CONST 5: 'utf-8'
160 PRECALL 1
164 CALL 1
174 STORE_FAST 3: key
176 LOAD_GLOBAL 9: NULL + IV
188 LOAD_CONST 6: 0
190 LOAD_CONST 7: 15
192 PRECALL 2
196 CALL 2
206 LOAD_METHOD 2: encode
228 LOAD_CONST 5: 'utf-8'
230 PRECALL 1
234 CALL 1
244 STORE_FAST 4: iv
246 LOAD_GLOBAL 11: NULL + encrypt
258 LOAD_FAST 3: key
260 LOAD_FAST 2: plaintext
262 LOAD_FAST 4: iv
264 PRECALL 3
268 CALL 3
278 STORE_FAST 5: ciphertext
280 LOAD_FAST 5: ciphertext
282 LOAD_METHOD 6: hex
304 PRECALL 0
308 CALL 0
318 LOAD_METHOD 2: encode
340 LOAD_CONST 5: 'utf-8'
342 PRECALL 1
346 CALL 1
356 LOAD_FAST 0: flag
358 COMPARE_OP 2 (==)
364 POP_JUMP_FORWARD_IF_FALSE 17 (to 400)
366 LOAD_GLOBAL 1: NULL + print
378 LOAD_CONST 8: 'Right!!!'
380 PRECALL 1
384 CALL 1
394 POP_TOP
396 LOAD_CONST 0: None
398 RETURN_VALUE
400 LOAD_GLOBAL 1: NULL + print
412 LOAD_CONST 9: 'error!!!'
414 PRECALL 1
418 CALL 1
428 POP_TOP
430 LOAD_CONST 0: None
432 RETURN_VALUE
(
None
)
[Disassembly]
0 RESUME 0
2 LOAD_CONST 0: 0
4 LOAD_CONST 1: ('AES',)
6 IMPORT_NAME 0: Crypto.Cipher
8 IMPORT_FROM 1: AES
10 STORE_NAME 1: AES
12 POP_TOP
14 LOAD_CONST 0: 0
16 LOAD_CONST 2: ('pad',)
18 IMPORT_NAME 2: Crypto.Util.Padding
20 IMPORT_FROM 3: pad
22 STORE_NAME 3: pad
24 POP_TOP
26 LOAD_CONST 3: <CODE> IV
28 MAKE_FUNCTION 0
30 STORE_NAME 4: IV
32 LOAD_CONST 4: <CODE> Key
34 MAKE_FUNCTION 0
36 STORE_NAME 5: Key
38 LOAD_CONST 8: (None,)
40 LOAD_CONST 6: <CODE> encrypt
42 MAKE_FUNCTION 1
44 STORE_NAME 6: encrypt
46 LOAD_CONST 7: <CODE> main
48 MAKE_FUNCTION 0
50 STORE_NAME 7: main
52 PUSH_NULL
54 LOAD_NAME 7: main
56 PRECALL 0
60 CALL 0
70 POP_TOP
72 LOAD_CONST 5: None
74 RETURN_VALUE借用官方wp的完整代码
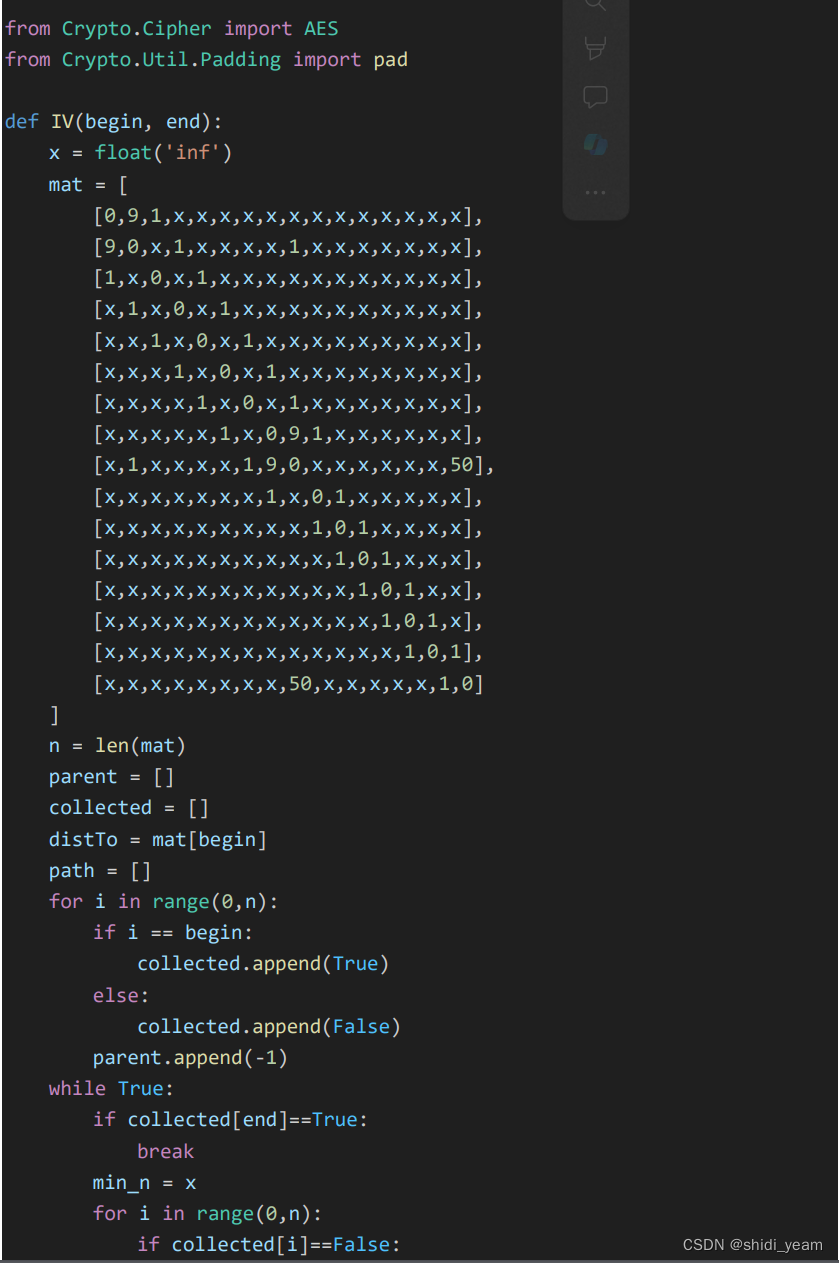
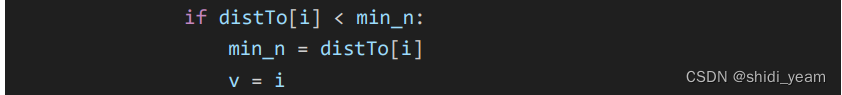
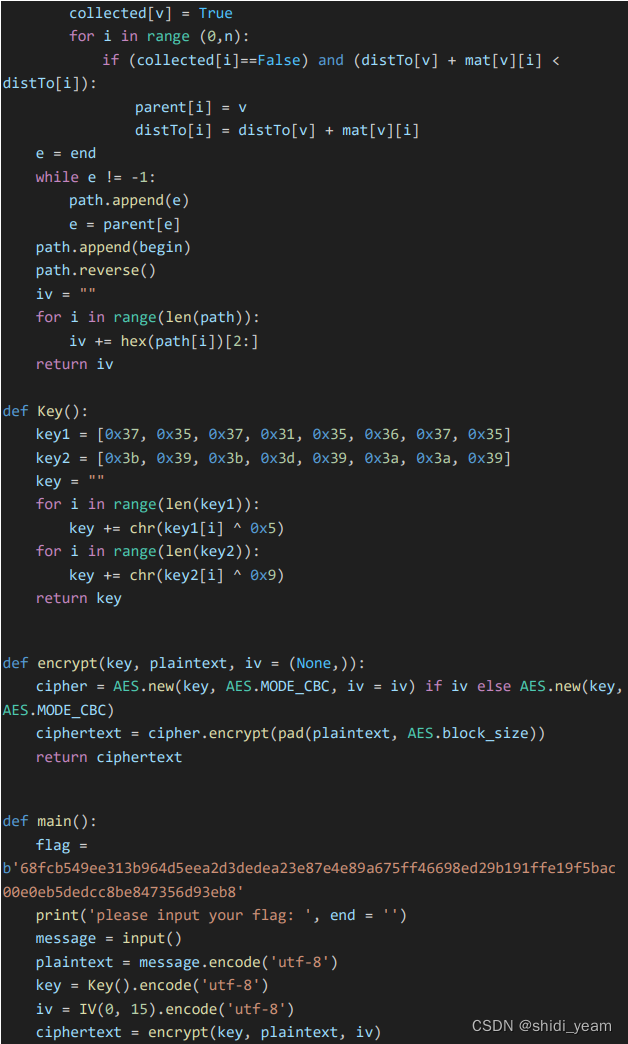
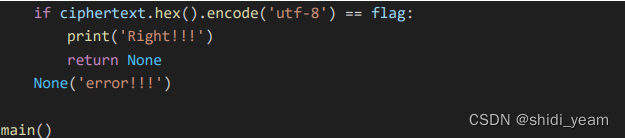
然后分析逻辑,就是一个AES加密,然后key需要经过一个异或,IV就是通过 dijkstra 算法 求得的最短路径
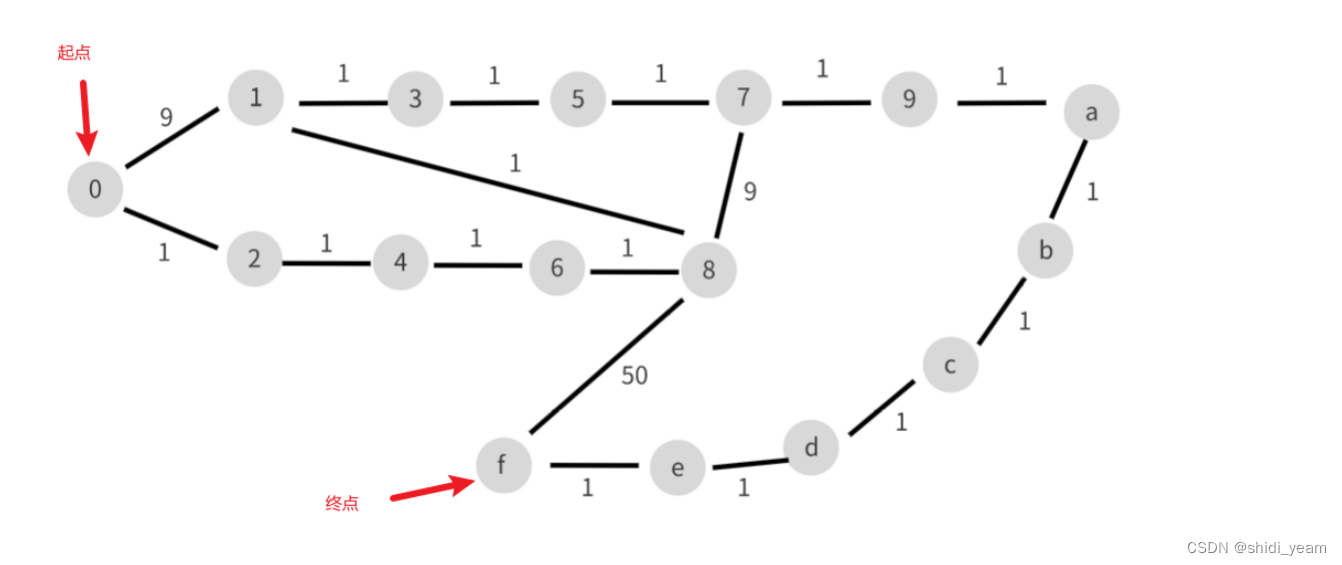
也可以直接解,这是官方wp中的图,肢解也不难,去网上找个脚本,换一下矩阵就好了,
最短路径:0246813579abcdef
key = 2024032020240330
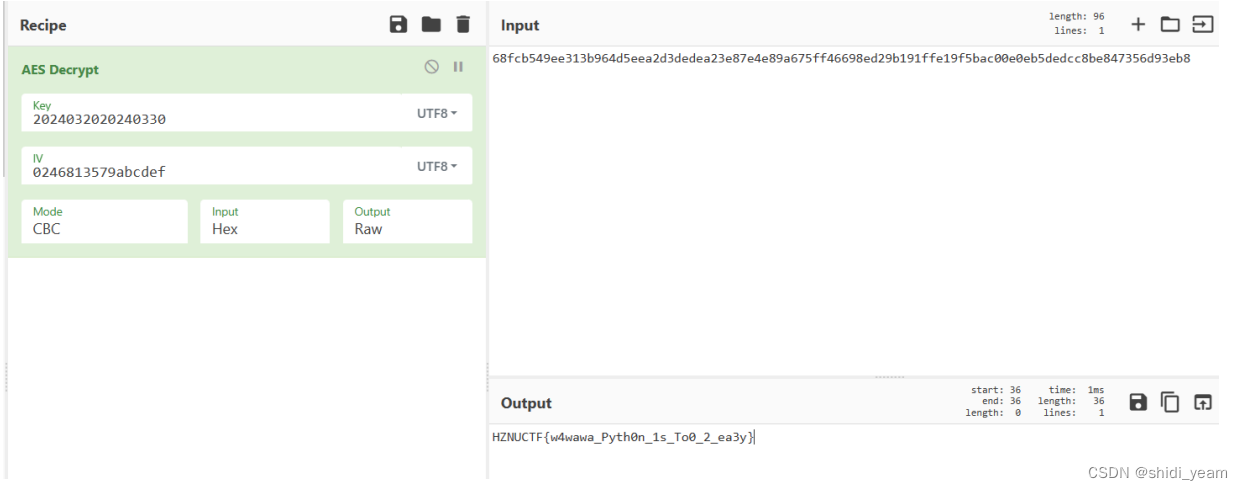
HZNUCTF{w4wawa_Pyth0n_1s_To0_2_ea3y}























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








