放到ida
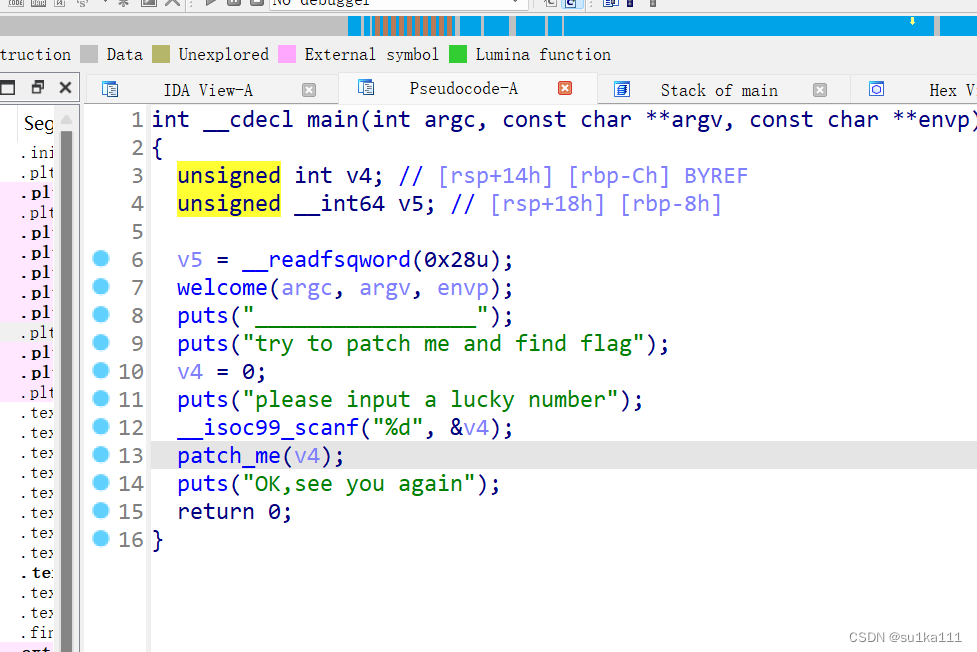
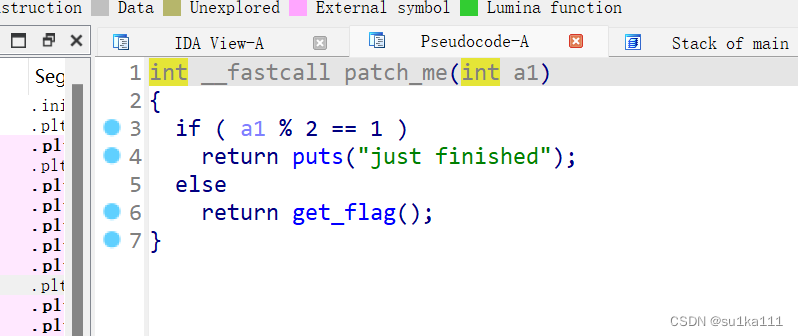
可以看出执行顺序是4,5,1
unsigned __int64 get_flag()
{
unsigned int v0; // eax
int i; // [rsp+4h] [rbp-3Ch]
int j; // [rsp+8h] [rbp-38h]
__int64 s; // [rsp+10h] [rbp-30h] BYREF
char v5; // [rsp+18h] [rbp-28h]
unsigned __int64 v6; // [rsp+38h] [rbp-8h]
v6 = __readfsqword(0x28u);
v0 = time(0LL);
srand(v0);
for ( i = 0; i <= 4; ++i )
{
switch ( rand() % 200 )
{
case 1:
puts("OK, it's flag:");
memset(&s, 0, 0x28uLL);
strcat((char *)&s, f1);
strcat((char *)&s, &f2);
printf("%s", (const char *)&s);
break;
case 2:
printf("Solar not like you");
break;
case 3:
printf("Solar want a girlfriend");
break;
case 4:
s = 0x7F666F6067756369LL;
v5 = 0;
strcat(&f2, (const char *)&s);
break;
case 5:
for ( j = 0; j <= 7; ++j )
{
if ( j % 2 == 1 )
*(&f2 + j) -= 2;
else
--*(&f2 + j);
}
break;
default:
puts("emmm,you can't find flag 23333");
break;
}
}
return __readfsqword(0x28u) ^ v6;
}写脚本
flag="GXY{do_not_"
f2=[0x7F,0x66,0x6F,0x60,0x67,0x75,0x63,0x69][::-1] #小端序的问题,所以要逆序一下
for j in range(8):
if j%2==1 :
s=chr(f2[j]-2)
else:
s=chr(f2[j]-1)
flag+=s
print (flag)
jadx 1.4.4安装:Release 1.4.4 · skylot/jadx · GitHub
使用教程:jadx-gui-1.4.4 反编译工具使用教程 - 莫贞俊晗 - 博客园 (cnblogs.com)
放到jadx里,找到主函数
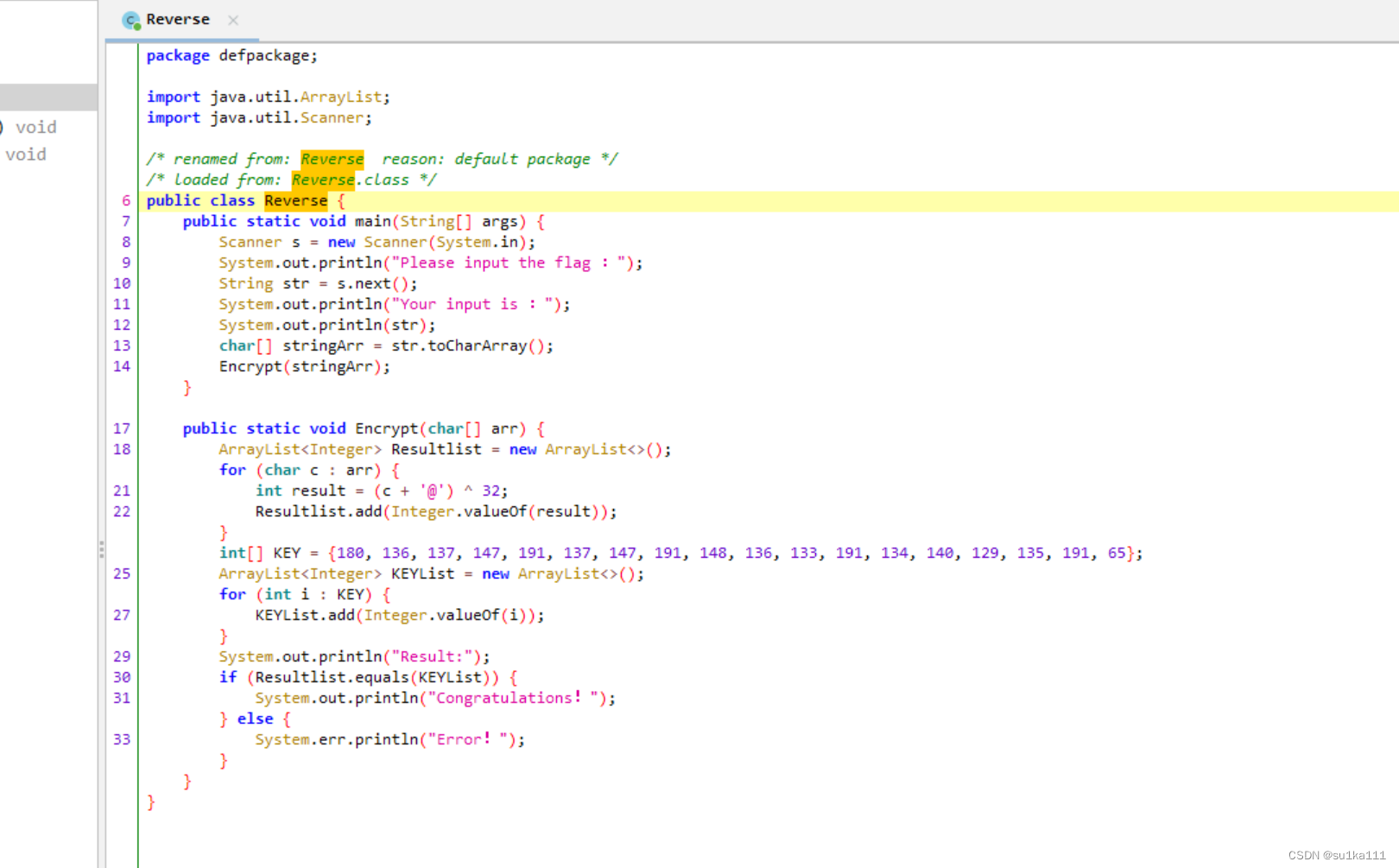
这里有两步,第一步:是在主函数main上输入flag,再调用Encrypt来进行加密
public static void main(String[] args) {
Scanner s = new Scanner(System.in);
System.out.println("Please input the flag );
String str = s.next();
System.out.println("Your input is );
System.out.println(str);
char[] stringArr = str.toCharArray();
Encrypt(stringArr);
}
第二步就是通过逆向Encrypt函数来获取flag
public static void Encrypt(char[] arr) {
ArrayList<Integer> Resultlist = new ArrayList<>();
for (int i = 0; i < arr.length; i++) {
int result = arr[i] + 64 ^ 0x20;
Resultlist.add(Integer.valueOf(result));
}
int[] KEY = {
180, 136, 137, 147, 191, 137, 147, 191, 148, 136,
133, 191, 134, 140, 129, 135, 191, 65 };
ArrayList<Integer> KEYList = new ArrayList<>();
for (int j = 0; j < KEY.length; j++)
KEYList.add(Integer.valueOf(KEY[j]));
System.out.println("Result:");
if (Resultlist.equals(KEYList)) {
System.out.println("Congratulations);
} else {
System.err.println("Error);
}
}
这题很好理解,就是输入的每个字符都加上64 ^ 0x20
for (int i = 0; i < arr.length; i++)
int result = arr[i] + 64 ^ 0x20;
然后再和KEY进行比较,相等就是我们要求的flag了
if (Resultlist.equals(KEYList))
System.out.println("Congratulations);
这里放上Python的求解代码:
key = [ 180, 136, 137, 147, 191, 137, 147, 191, 148, 136, 133, 191, 134, 140, 129, 135, 191, 65 ]
flag = ""
for i in range(0,len(key)):
for x in range(0,1024): # 这里通过暴力破解来获取flag
temp = x + 64 ^ 0x20 # 每个字符都加上固定的64 ^ 0x20
if temp == key[i]: # 如果相等就表示这是我们要的flag字符
flag = flag + chr(x)
break
print("flag{"+flag+"}")
#flag{This_is_the_flag_!}放到ida
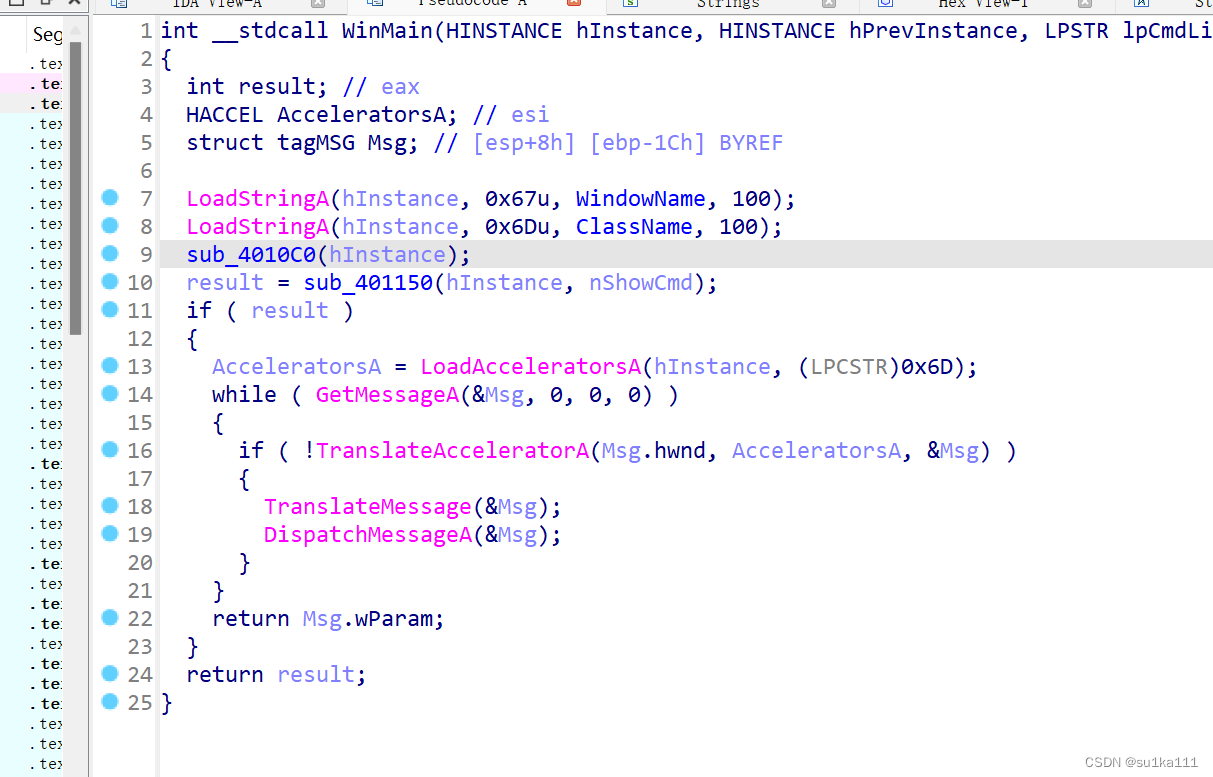
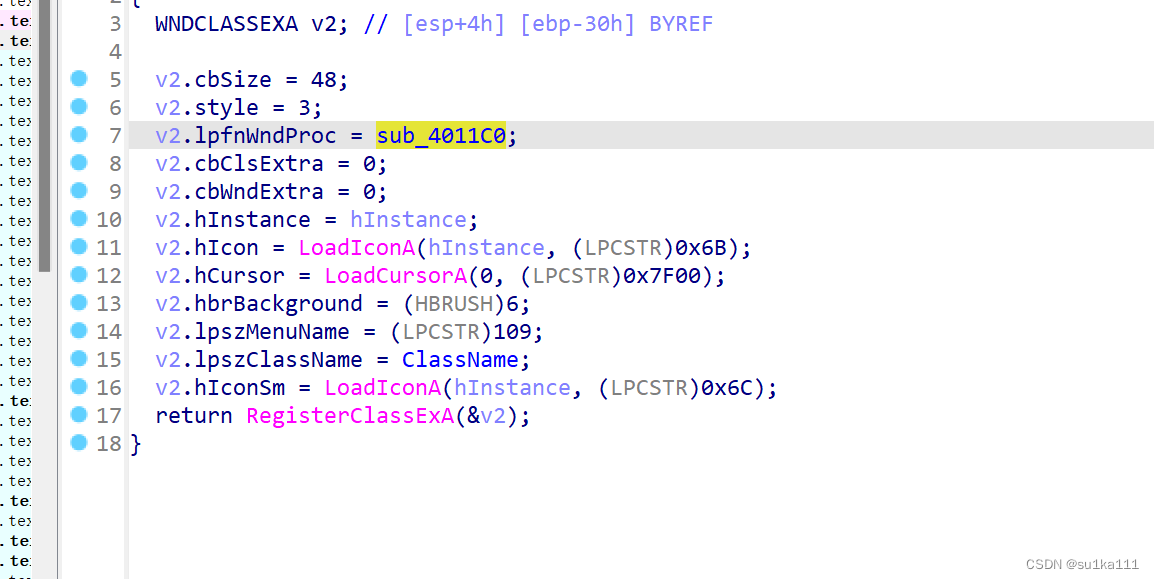
进各个函数看一下
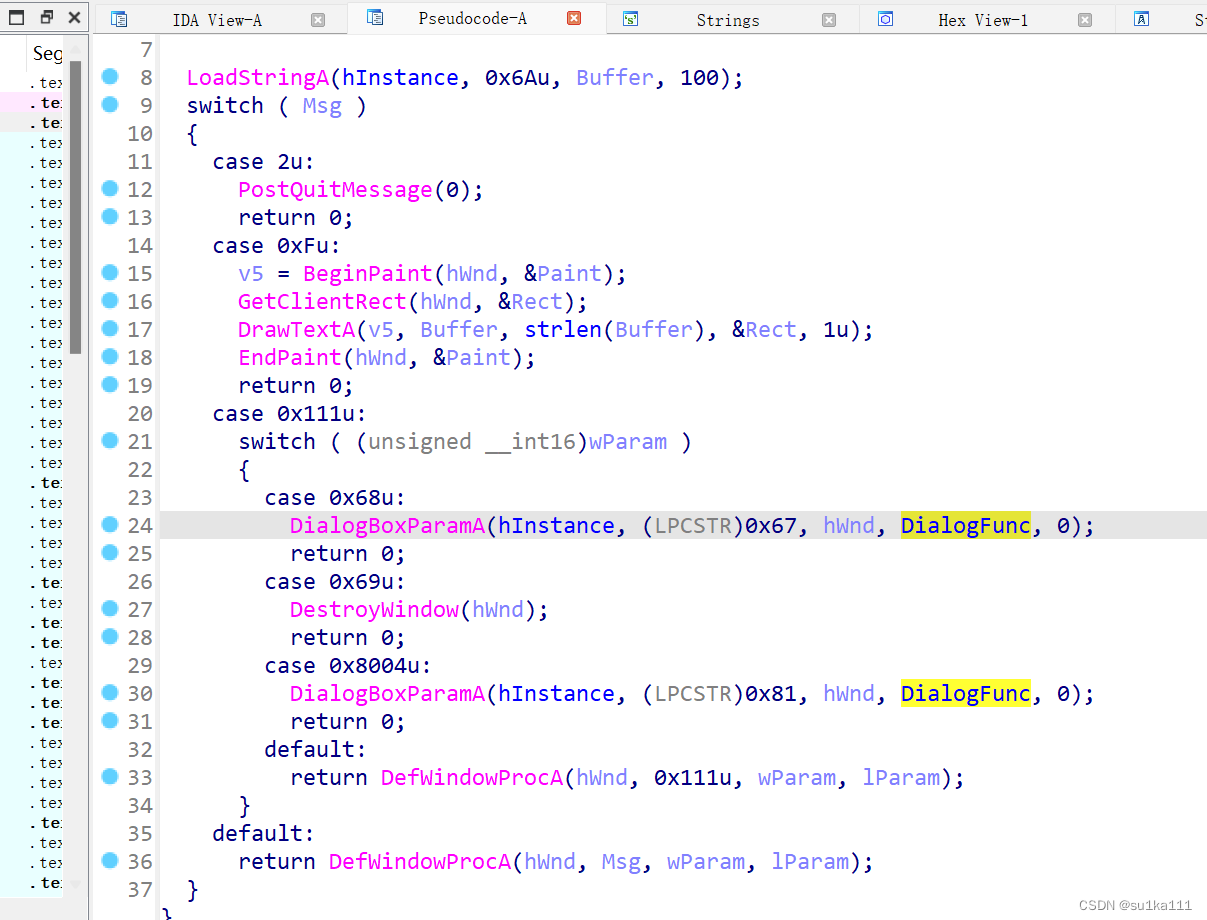
找到flag
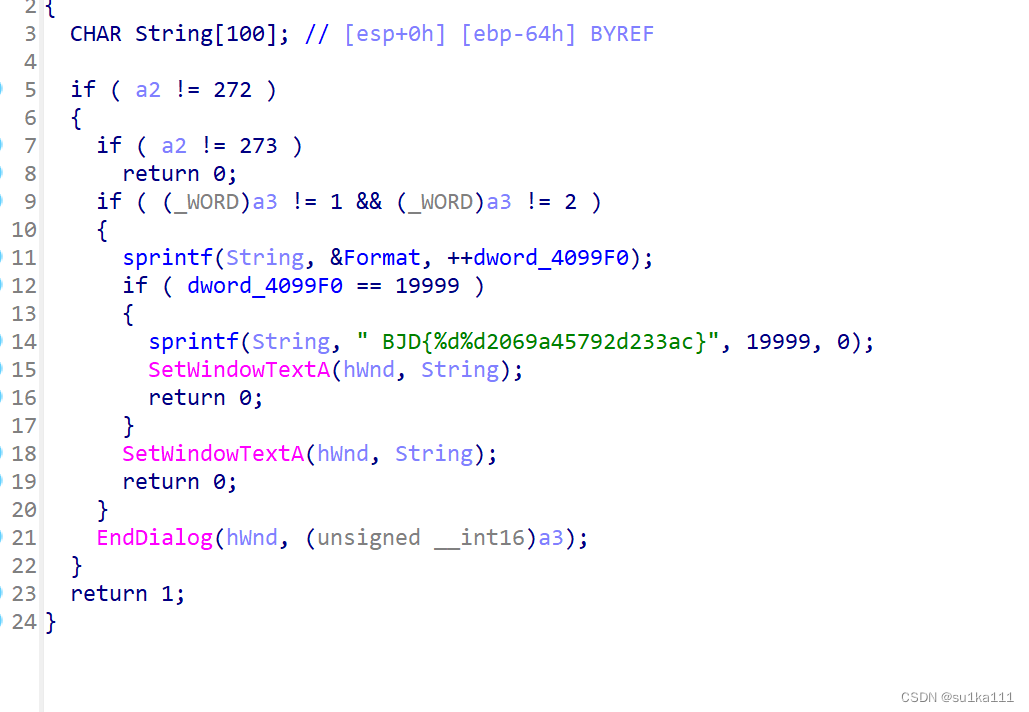
放到jadx找主函数,写个脚本
str=['d','d','2','9','4','0','c','0','4','4','6','2','b','4','d','d','7','c','4','5','0','5','2','8','8','3','5','c','c','a','1','5']
str[2]=chr(ord(str[2])+ord(str[3])-50)
str[4]=chr( ord(str[2])+ord(str[5])-0x30 )
str[30]=chr( ord(str[0x1f])+ord(str[9])-0x30)
str[14]=chr( ord(str[27])+ord(str[28])-97 )
for i in range(16):
x=str[0x1f-i]
str[0x1f-i]=str[i]
str[i]=x
for i in str:
print (i,end="")
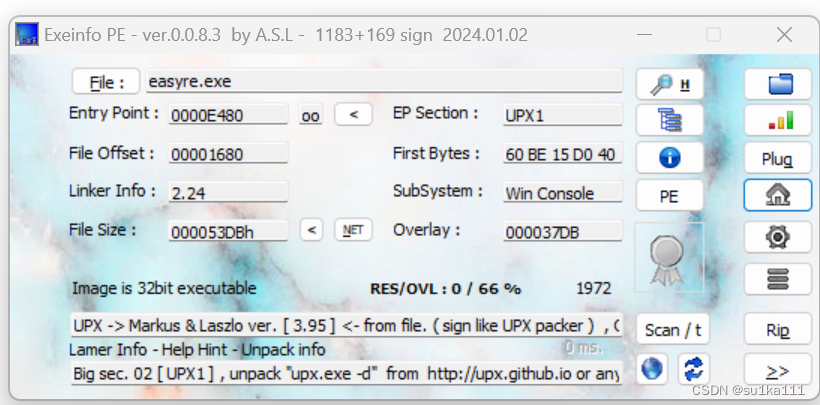
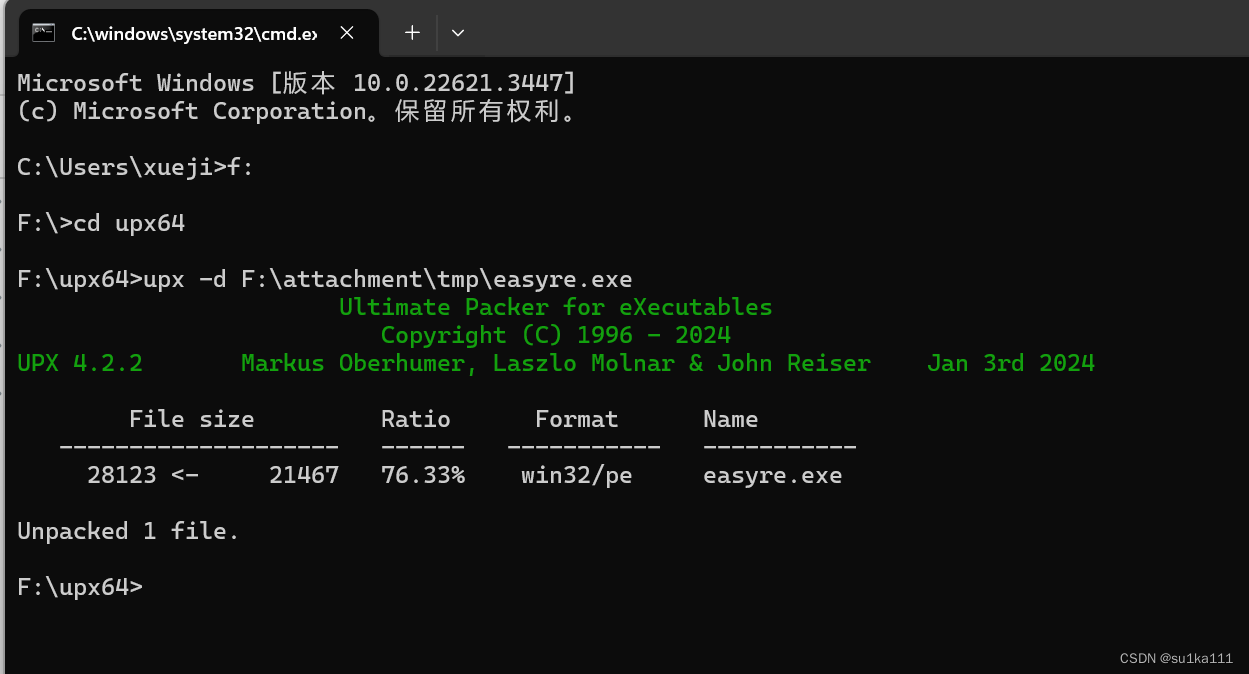
查下壳,有upx壳
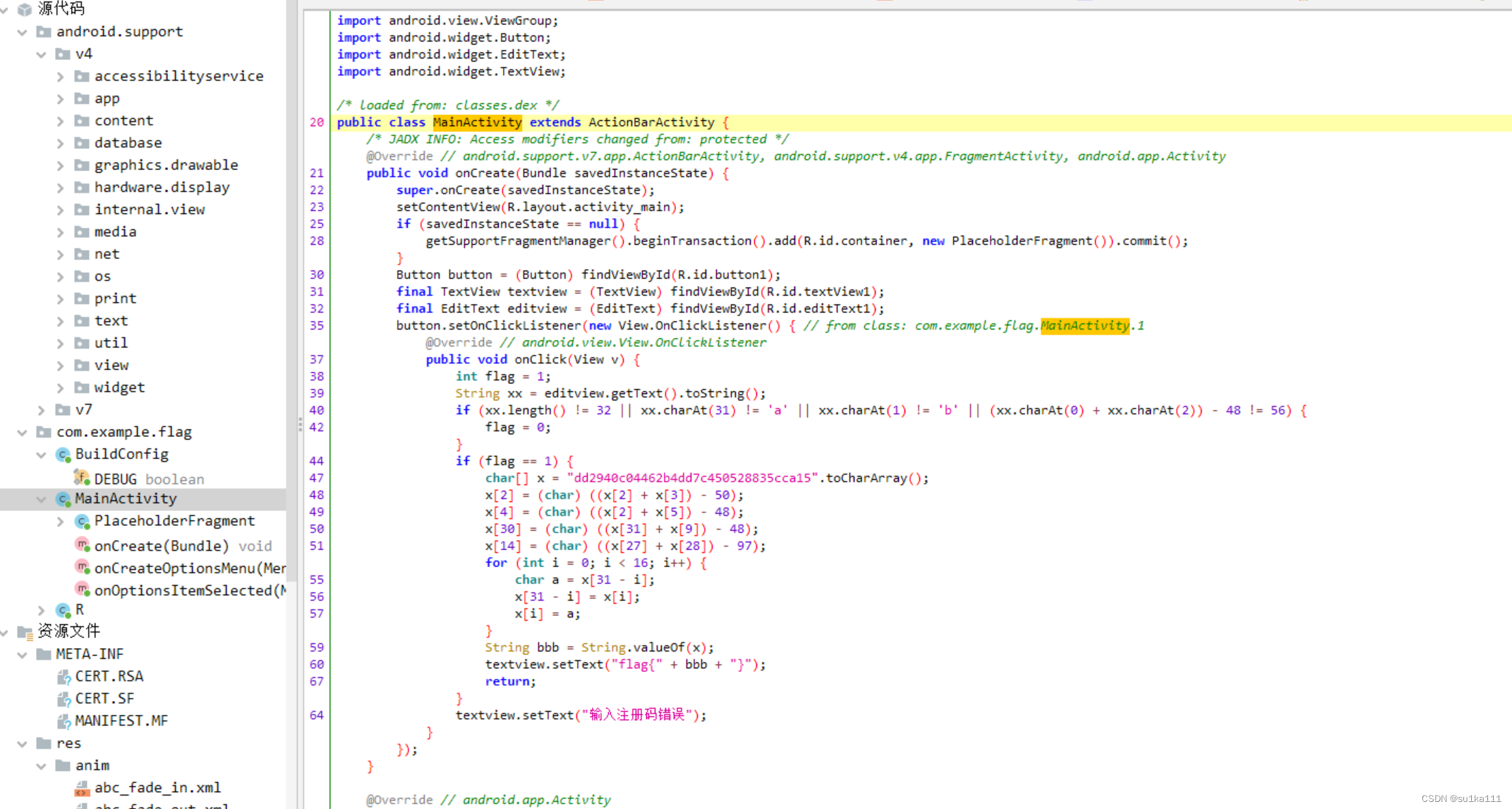
找到主函数,
从for循环了解到flag长度应该是12,将flag的ASCII值作为下标取值,与v4数组比较。很简单,只需要利用v4数组在_data_start__中找位置,就是我们flag的值
int __cdecl main(int argc, const char **argv, const char **envp)
{
_BYTE v4[12]; // [esp+12h] [ebp-2Eh] BYREF
_DWORD v5[3]; // [esp+1Eh] [ebp-22h]
_BYTE v6[5]; // [esp+2Ah] [ebp-16h] BYREF
int v7; // [esp+2Fh] [ebp-11h]
int v8; // [esp+33h] [ebp-Dh]
int v9; // [esp+37h] [ebp-9h]
char v10; // [esp+3Bh] [ebp-5h]
int i; // [esp+3Ch] [ebp-4h]
__main();
qmemcpy(v4, "*F'\"N,\"(I?+@", sizeof(v4));
printf("Please input:");
scanf("%s", v6);
if ( v6[0] != 65 || v6[1] != 67 || v6[2] != 84 || v6[3] != 70 || v6[4] != 123 || v10 != 125 )
return 0;
v5[0] = v7;
v5[1] = v8;
v5[2] = v9;
for ( i = 0; i <= 11; ++i )
{
if ( v4[i] != _data_start__[*((char *)v5 + i) - 1] )
return 0;
}
printf("You are correct!");
return 0;
}
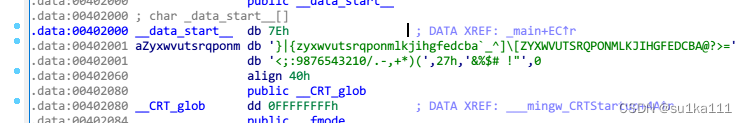
v4 = [42,70,39,34,78,44,34,40,73,63,43,64]
model = r"}|{zyxwvutsrqponmlkjihgfedcba`_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)(" + chr(0x27) + r'&%$# !"'
pos = []
for i in v4:
pos.append(model.find(chr(i))+1)
s = [chr(x + 1) for x in pos]
flag = ''.join(s)
print ('flag{'+flag+'}')
#flag{U9X_1S_W6@T?}
Python解包及反编译: PyInstaller Extractor+uncompyle6 - 知乎 (zhihu.com)
把.pyc文件变成py文件
有了程序
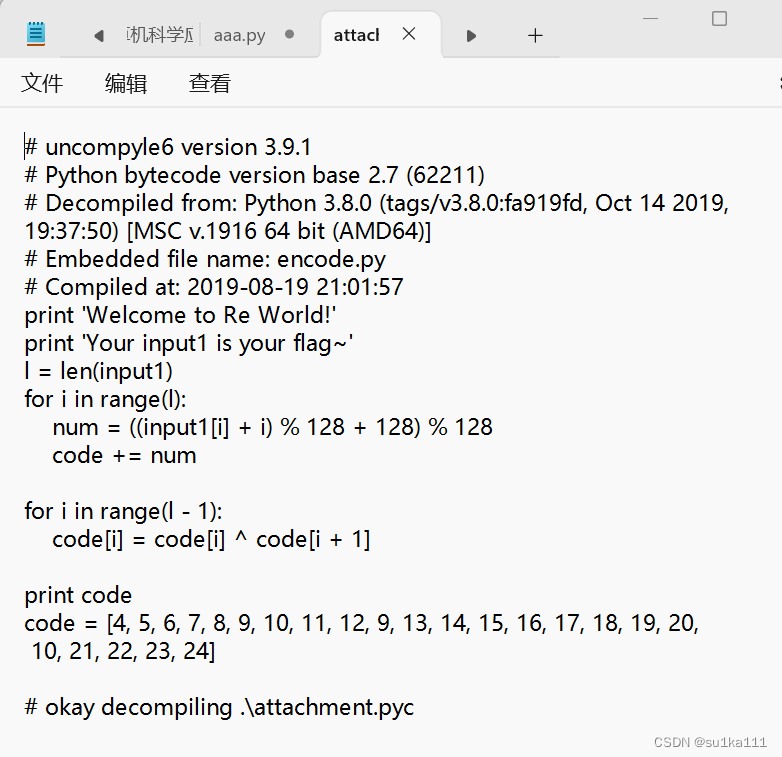
code = ['\x1f','\x12','\x1d','(','0','4','\x01','\x06','\x14','4',',','\x1b','U','?','o','6','*',':','\x01','D',';','%','\x13']
flag = ''
for i in range(len(code)-2,-1, - 1):
code[i] = chr(ord(code[i]) ^ ord(code[i + 1]))
for i in range (len(code)):
num = chr((ord(code[i]) - i)%128)
flag +=num
print(flag)
https://buuoj.cn/challenges#findit
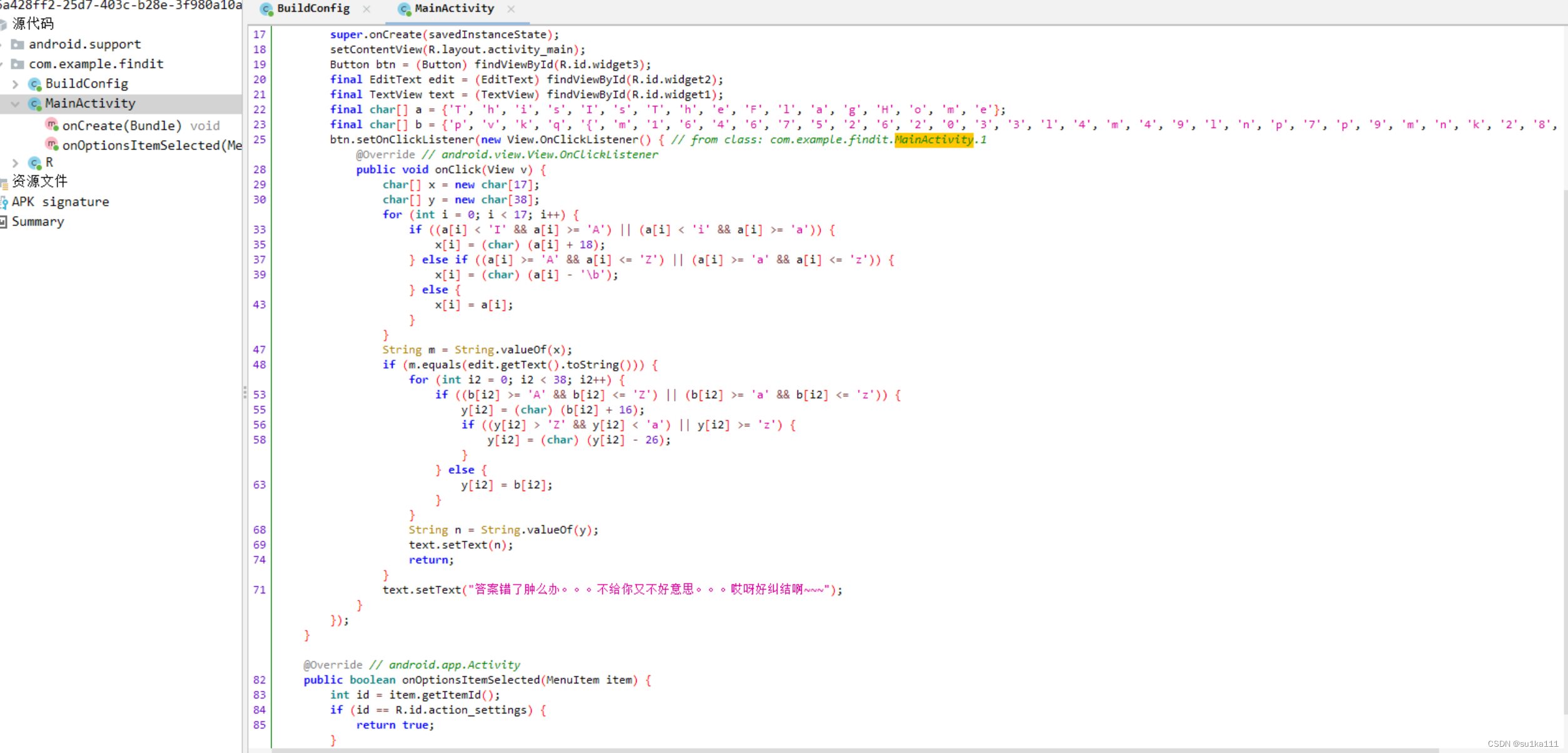
看第二串字符
仔细观察pvkq,发现f——>p移10位,l——>v移10位,a——>k移10位,g——>q移10位,
所以这我们还需要将得到的字符串进行一次凯撒加密
flag{c164675262033b4c49bdf7f9cda28a75}




















 357
357

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








